Gigabit GOST VPN. Tss diamond
VPN channel is a necessity for almost all companies that have remote branches or just remote employees. For the organization of these channels there is a rather large number of technologies and protocols (IPSec, GRE. L2TP, etc.), which are supported by most modern equipment. However, there is a certain category of organizations that are forced (and are forced) to use solutions supporting domestic cryptoalgorithms - GOST VPN . At the same time, implementing this GOST on Linux-like systems is not difficult. However, obtaining the certificate of the FSB (as a means of CIPP) is almost impossible for foreign solutions (Cisco, Check Point , Fortinet , etc.). In this regard, the choice of equipment is sharply narrowed. So far in such cases, the following options have been considered:
However, at the moment it is very difficult to find a solution that would support Gigabit GOST VPN . There are various "tricky" ways to get around this problem, for example, to put several devices on each side and using balancing to increase the overall bandwidth using several VPN tunnels.
S-terra example:
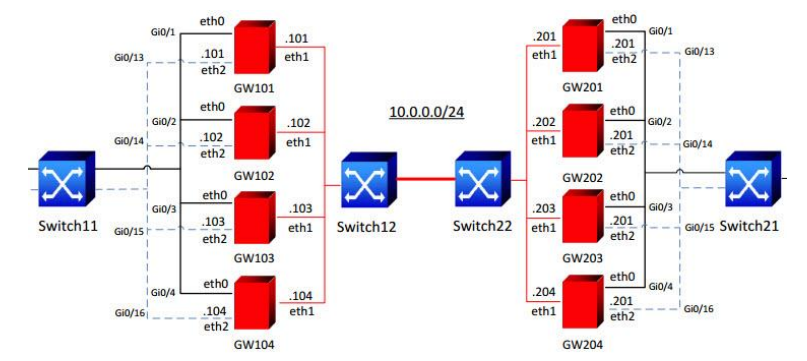
Not always this solution is applicable and not always "affordable". In search of a compromise, we learned about the existence of another very interesting solution - TSS Diamond . TSS Company announces the possibility of its hardware to organize a VPN channel with bandwidth even more than Gigabit . And this is from one piece of iron, without aggregation ... We decided not to believe the marketing materials and test everything ourselves. For this, the vendor has kindly provided us with two “hardware” for the test - Diamond VPN / FW Enterprise 5111 .

Then we quickly put together a simple circuit for the test:
')
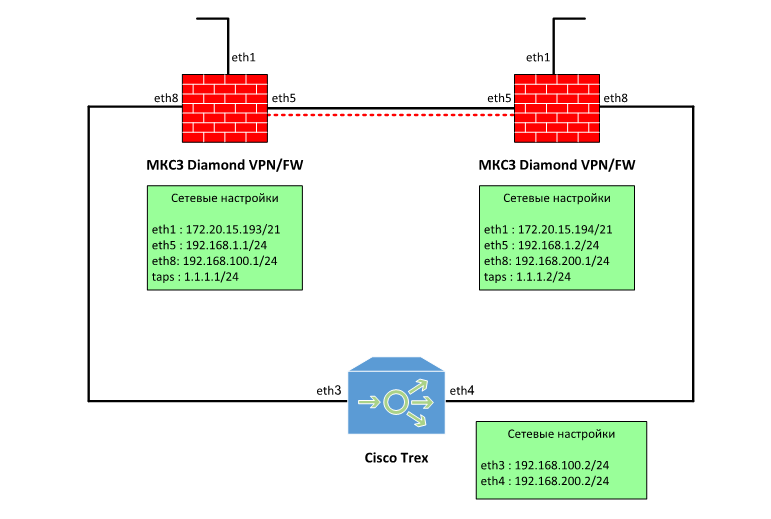
Those. Two devices are connected directly to each other (optical links). To test the throughput of the VPN tunnel, Cisco Trex was used .
Briefly describe the setup procedure. All configuration is done via an intuitive web-based interface. In this case, the first gateway acts as a VPN server, the second - as a VPN client.
Server Tuning
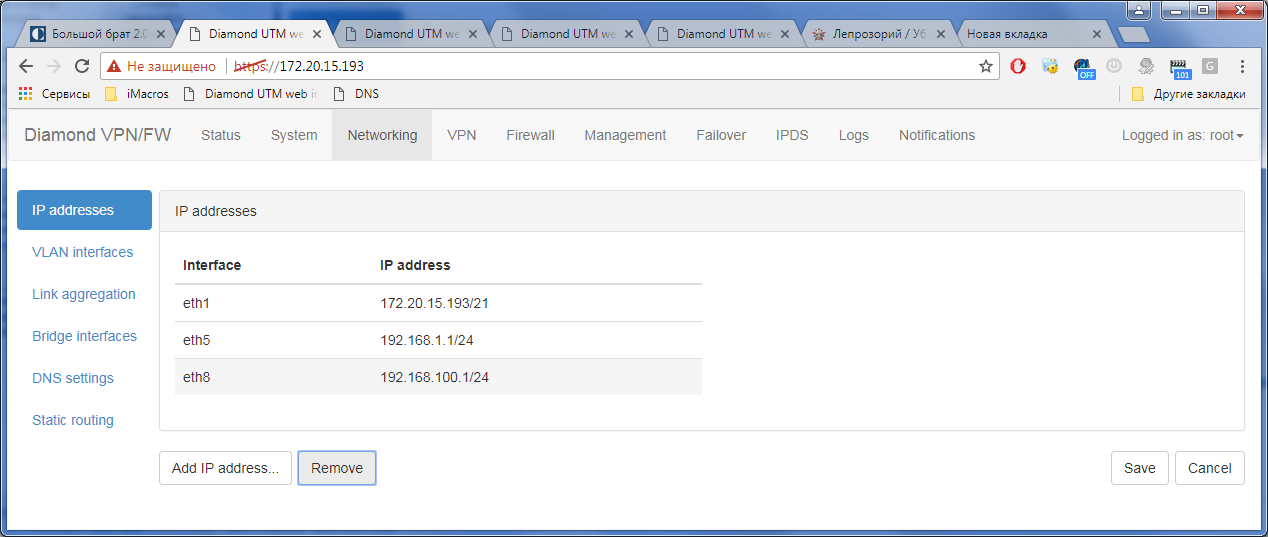
1) Configure network interfaces:
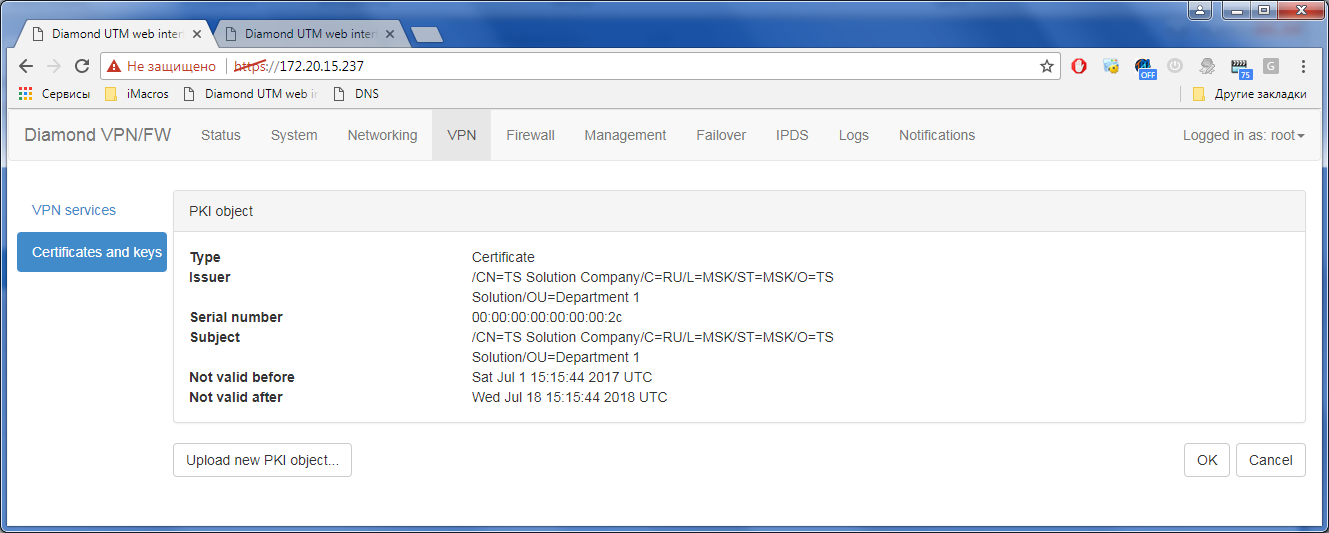
2) Adding certificates (install new PKI ...):
result:
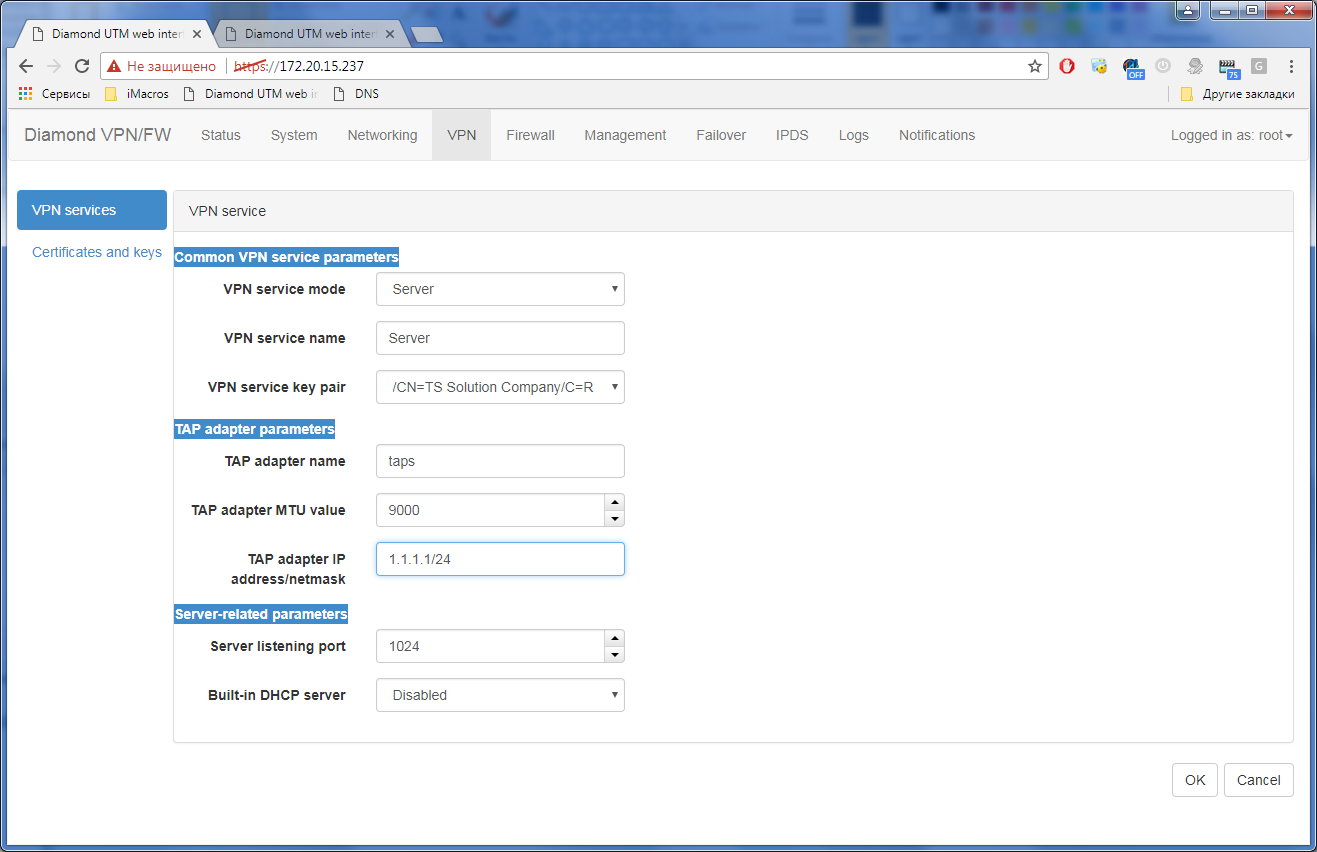
3) VPN connection settings:
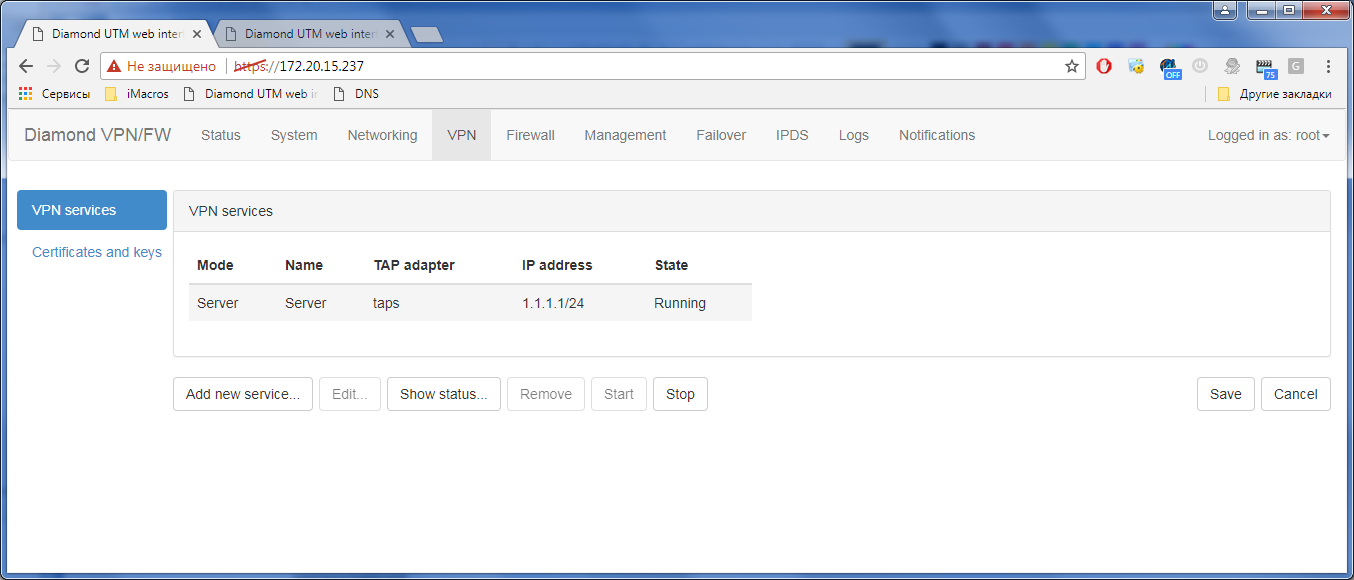
The status must be in the status of Running
4) Now you need to register the route in order to “wrap” the traffic in the VPN tunnel:

Client setup
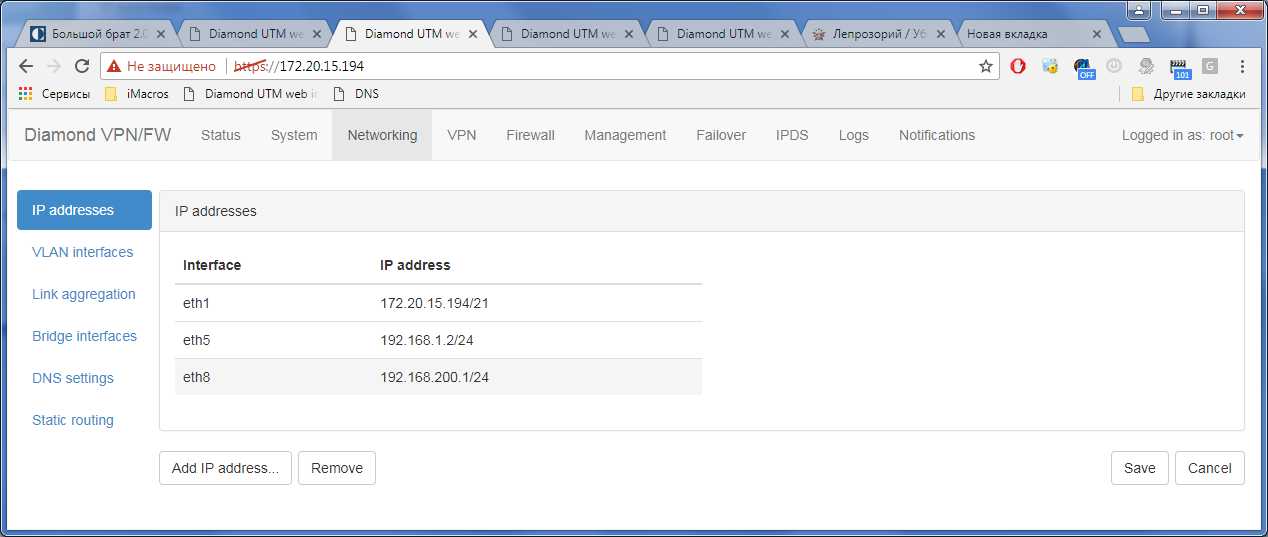
1) Configure network interfaces:
2) Add a certificate:
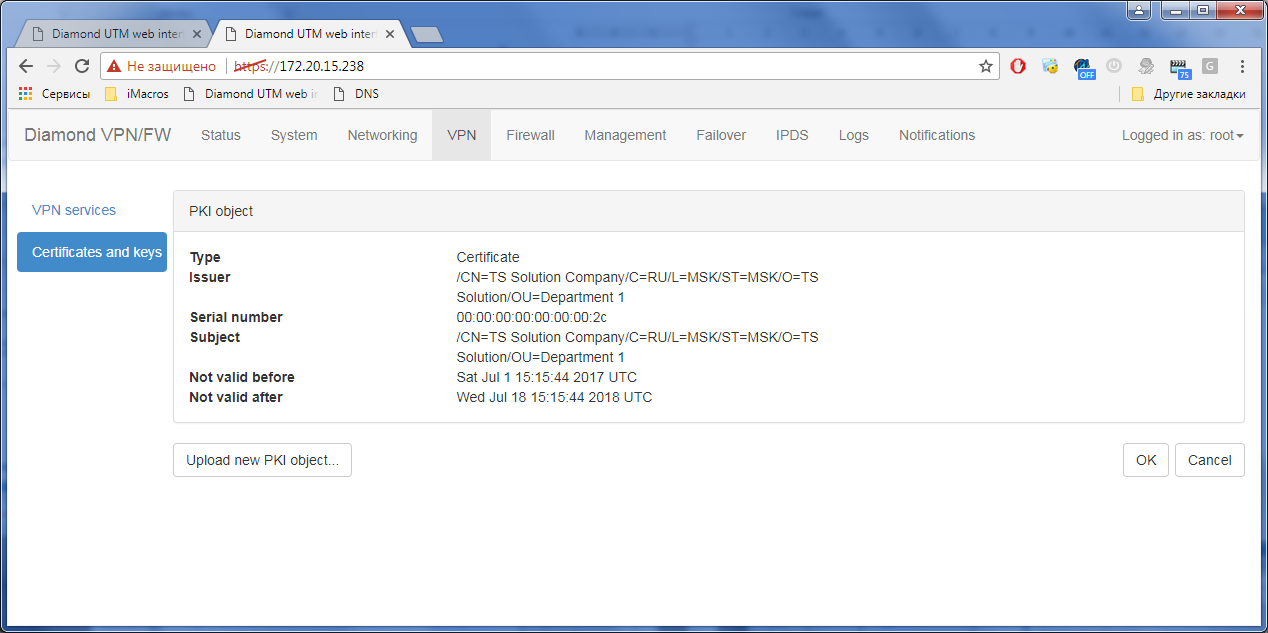
3) VPN connection settings:

We check that the status is Running:
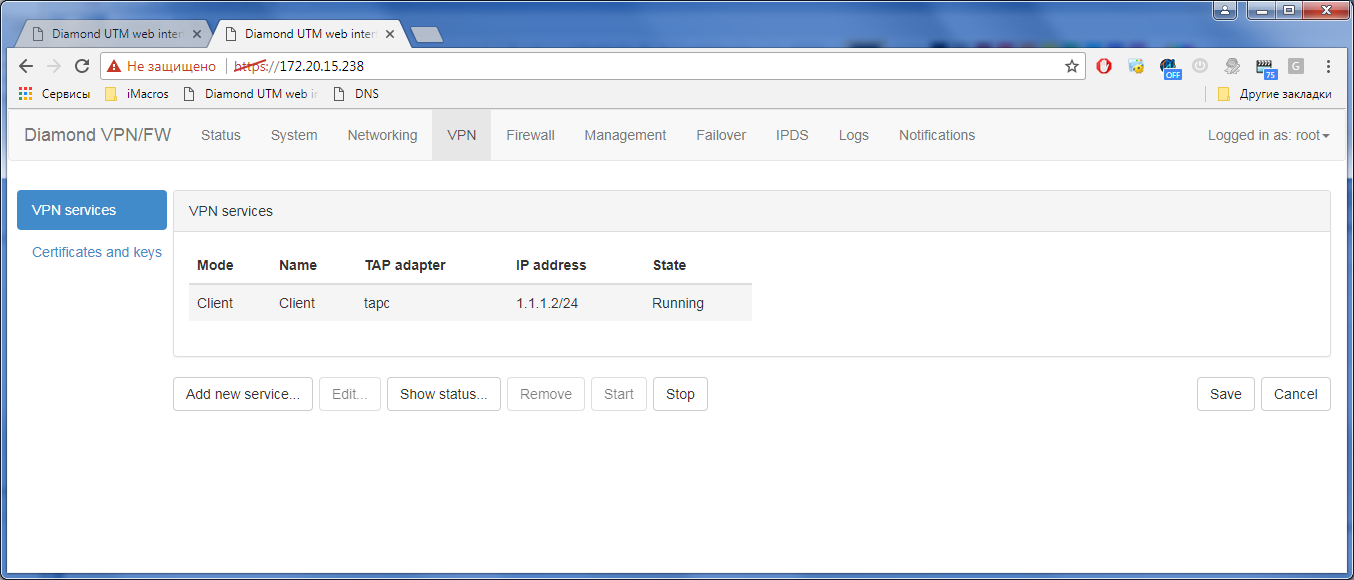
4) “Wrap” traffic using a static route:
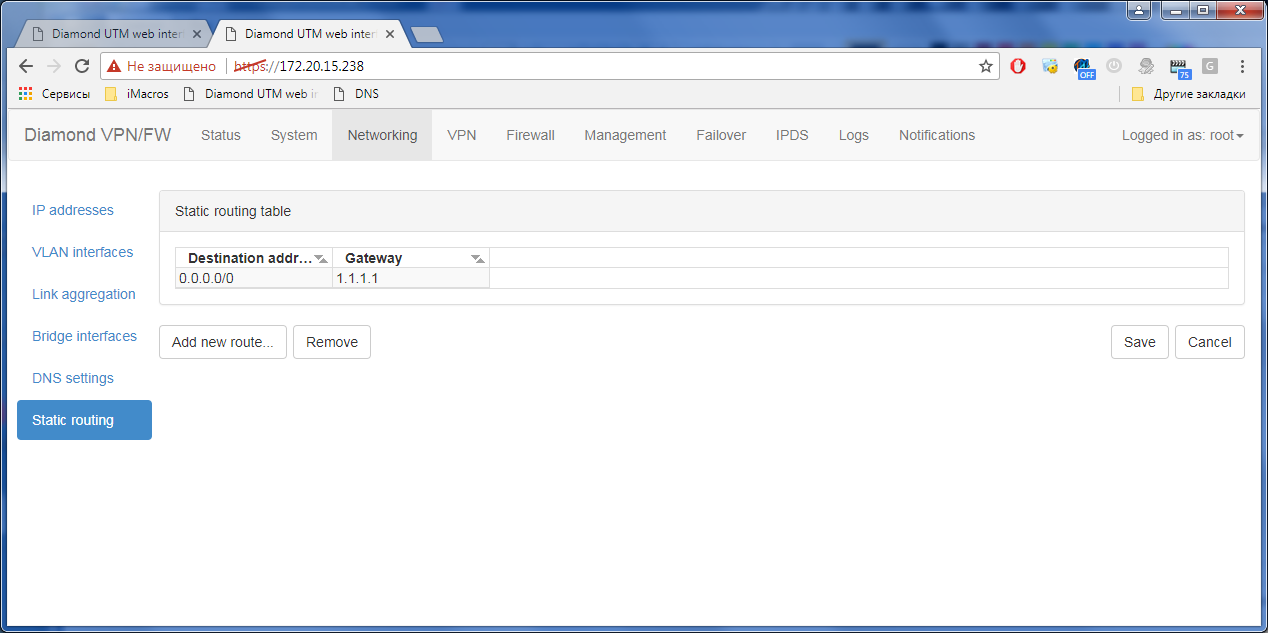
After that, in the event log you can find a log about a successful VPN connection:
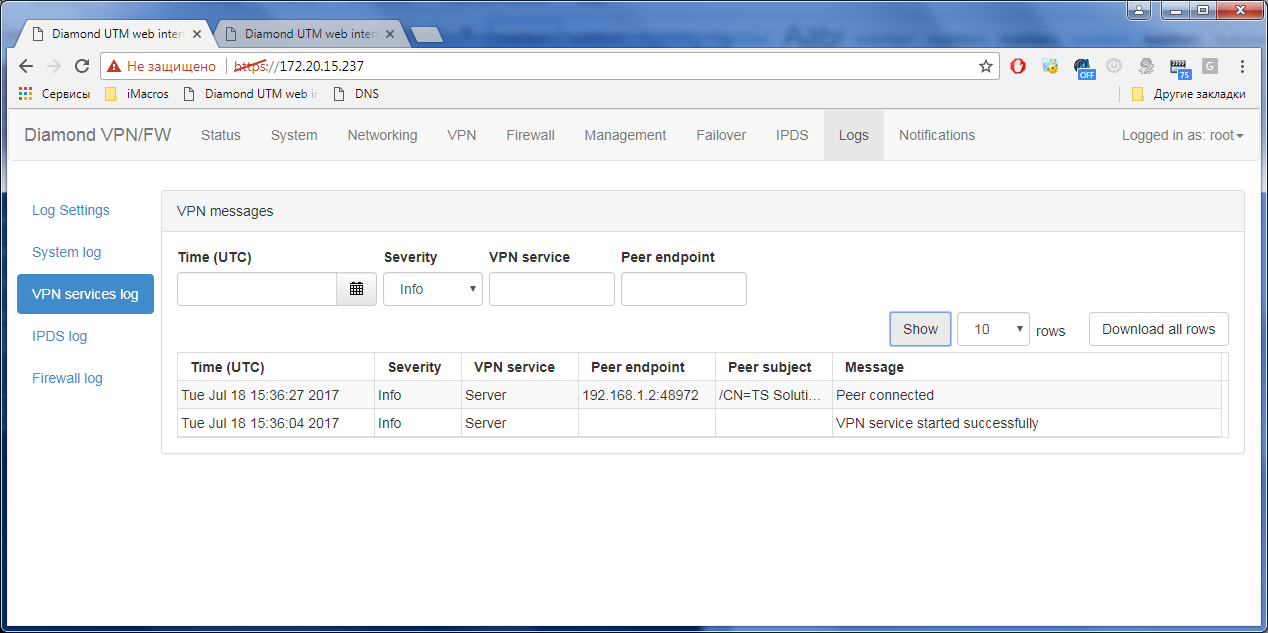
As mentioned earlier, Cisco Trex was used to test the throughput of the VPN tunnel. They were tested both in small and large packages, and in duplex, i.e. immediately in two directions ( upload / download ). Here are some results:
1) Packet 64 bytes

2) Packet 594 bytes

3) Packet 1500 bytes
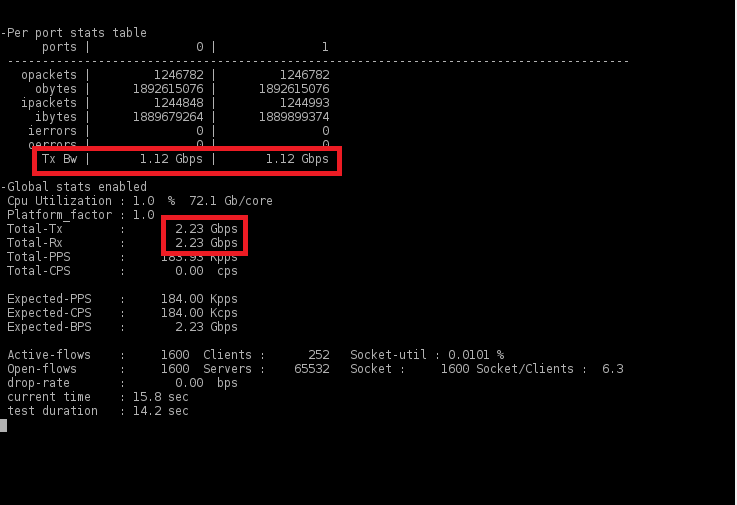
4) Packet 9000 bytes
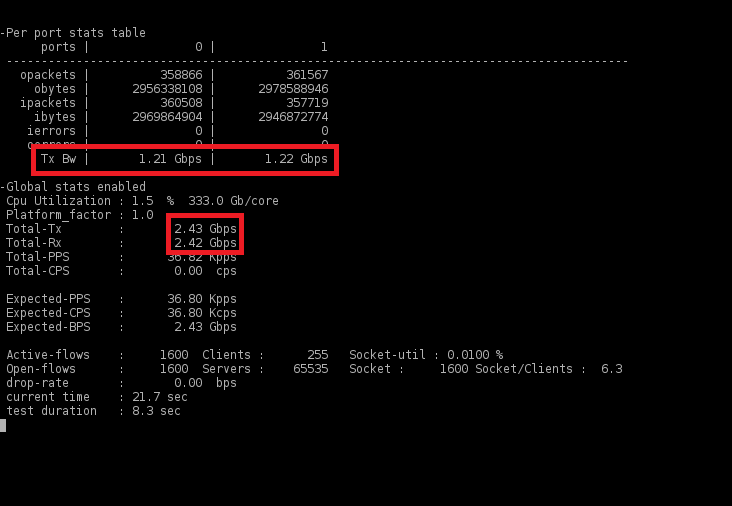
In this case, all tests were performed for L3 VPN . For L2 VPN there will be about the same options.
What is written in datasheet on this piece of iron? There are the following parameters:
VPN throughput - 2.6 Gbps
The basic throughput of ME in the basic configuration - 7.5 Gb / s
In general, if we consider our synthetic tests, the parameters converge (in terms of VPN). In addition, these devices have the function of IPS , but this is a topic for a separate article.
Naturally, when choosing a device with GOST VPN, the first interesting question is the availability of certificates. TSS Diamond devices have the following certificates of conformity:
The cryptographic subsystem of the DCrypt product has a certificate of conformity in class - 1 2 3.
In our subjective opinion, this equipment is well suited for solving the task of organizing a GOST VPN tunnel with high bandwidth (for example, for communication between two data centers ). All declared functions are performed. I don’t see any reason to demand something more from this device (except VPN). In addition, the TSS Dimond lineup also has smaller “smaller” models that are suitable for small and medium-sized branches ( Diamond VPN / FW 1101, 2111, 3101, 4101, 4105 ). The youngest model 1101 on tests gives at least 100 Mbit GOST VPN (1500 packages).
If you have additional questions about TSS Diamond, feel free to contact us .
PS If there is no equipment (or software) known to you in the list of GOST VPN organization solutions, please write this in the comments.
- S-terra
- APKS Continent
- Ideco MagPro GOST-VPN
- Vipnet
- Outpost
However, at the moment it is very difficult to find a solution that would support Gigabit GOST VPN . There are various "tricky" ways to get around this problem, for example, to put several devices on each side and using balancing to increase the overall bandwidth using several VPN tunnels.
S-terra example:
Not always this solution is applicable and not always "affordable". In search of a compromise, we learned about the existence of another very interesting solution - TSS Diamond . TSS Company announces the possibility of its hardware to organize a VPN channel with bandwidth even more than Gigabit . And this is from one piece of iron, without aggregation ... We decided not to believe the marketing materials and test everything ourselves. For this, the vendor has kindly provided us with two “hardware” for the test - Diamond VPN / FW Enterprise 5111 .
Then we quickly put together a simple circuit for the test:
')
Those. Two devices are connected directly to each other (optical links). To test the throughput of the VPN tunnel, Cisco Trex was used .
Customization
Briefly describe the setup procedure. All configuration is done via an intuitive web-based interface. In this case, the first gateway acts as a VPN server, the second - as a VPN client.
Server Tuning
1) Configure network interfaces:

2) Adding certificates (install new PKI ...):

result:

3) VPN connection settings:

The status must be in the status of Running

4) Now you need to register the route in order to “wrap” the traffic in the VPN tunnel:

Client setup
1) Configure network interfaces:

2) Add a certificate:

3) VPN connection settings:

We check that the status is Running:

4) “Wrap” traffic using a static route:

After that, in the event log you can find a log about a successful VPN connection:

Bandwidth test
As mentioned earlier, Cisco Trex was used to test the throughput of the VPN tunnel. They were tested both in small and large packages, and in duplex, i.e. immediately in two directions ( upload / download ). Here are some results:
1) Packet 64 bytes

2) Packet 594 bytes

3) Packet 1500 bytes

4) Packet 9000 bytes

In this case, all tests were performed for L3 VPN . For L2 VPN there will be about the same options.
What is written in datasheet on this piece of iron? There are the following parameters:
VPN throughput - 2.6 Gbps
The basic throughput of ME in the basic configuration - 7.5 Gb / s
In general, if we consider our synthetic tests, the parameters converge (in terms of VPN). In addition, these devices have the function of IPS , but this is a topic for a separate article.
Certification
Naturally, when choosing a device with GOST VPN, the first interesting question is the availability of certificates. TSS Diamond devices have the following certificates of conformity:
- "Means of computing. Protection against unauthorized access to information. Indicators of security against unauthorized access to information ”(State Technical Commission of Russia, 1992) - 3 classes of security;
- "Protection against unauthorized access to information. Part 1. Software of information security tools. Classification by the level of control over the absence of undeclared capabilities "(State Technical Commission of Russia, 1999) - by level 2 of control
- as well as documents:
- “Requirements for intrusion detection systems” (FSTEC of Russia, 2011);
- “The security profile of intrusion detection systems of network level of the fourth class of protection. IT.SOV.S4.PZ ”(FSTEC of Russia, 2012);
- "Requirements for firewalls" (FSTEC of Russia, 2016);
- “Profile of protection of firewalls of type“ A ”of the fourth class of protection IT.ME.A4.PZ (FSTEC of Russia, 2016)”;
- • “Profile of protection of firewalls of type“ B ”of the fourth class of protection IT. ME.B4. PZ (FSTEC of Russia, 2016)”;
- “Profile of protection of firewalls of type“ B ”of the fourth class of protection IT.ME.V4.PZ (FSTEC of Russia, 2016)”.
The cryptographic subsystem of the DCrypt product has a certificate of conformity in class - 1 2 3.
findings
In our subjective opinion, this equipment is well suited for solving the task of organizing a GOST VPN tunnel with high bandwidth (for example, for communication between two data centers ). All declared functions are performed. I don’t see any reason to demand something more from this device (except VPN). In addition, the TSS Dimond lineup also has smaller “smaller” models that are suitable for small and medium-sized branches ( Diamond VPN / FW 1101, 2111, 3101, 4101, 4105 ). The youngest model 1101 on tests gives at least 100 Mbit GOST VPN (1500 packages).
If you have additional questions about TSS Diamond, feel free to contact us .
PS If there is no equipment (or software) known to you in the list of GOST VPN organization solutions, please write this in the comments.
Source: https://habr.com/ru/post/334534/
All Articles