Evolution of web application attacks

Attacks on web applications open wide opportunities for attackers: this is the theft of critical information or sensitive information; violation of business logic for financial gain; Also, a successful web application attack may be a precursor to hacking the company's corporate network. In this article I will talk about the evolution of web application attacks.
OWASP TOP 10
Classic vulnerabilities are currently represented by the OWASP TOP 10 list:
- A1 Code Implementation
- A2 Incorrect authentication and session management
- A3 Crossite scripting
- A4 Insecure Direct Object Links
- A5 Unsafe Configuration
- A6 Leaked sensitive data
- A7 Lack of access control to the functional level
- A8 Cross-Site Request Forgery
- A9 Using components with known vulnerabilities
- A10 Unvalidated Redirects
Attacks on web applications are applicable to this list, but not all are common everywhere and occur every day.
A good example of identifying a particular vulnerability is the unofficial HackerOne disclosure timeline: http://h1.nobbd.de/index.php . As we can see, SQL injections, client-side attacks, etc. prevail.
Types of attacks
There are two types of attacks: non-targeted and targeted. Non-target "hit the squares", and implement one or two attack vectors, do not always implement the target of the attack. As a rule, they are distinguished by primitiveness. We see such attacks every day, presented as exploiting a particular vulnerability, trying to gain access to critical files, etc.
Targeted attacks are distinguished by a multitude of vectors, high professionalism of the attackers and effectiveness. Such accounts for approximately 5% of the total number of attacks, but in terms of effectiveness they are much higher than non-targeted ones.
Non-target attacks, as a rule, are automated and are performed using various exploitation systems: from vulnerability scanners to self-written scripts and utilities. They differ, as a rule, by several signs (User-Agent, application vector, IP range). For example, an attempt to identify /uploadify/uploadify.php - vulnerabilities in the MODX module.
Statistics of untargeted attacks is as follows:
Most popular attacks:
- Attempts to detect SQL Injection: - 85%.
- Attempts to identify access to critical folders and files: - 7%.
- Attempts to use known (sensational) exploits - 5%.
- Attempts to implement the identification of Cross-Site Scripting - 3%.
This concerned automated systems. If the site is attacked by an attacker, a knowledgeable web application and its vulnerable components - the attack becomes more targeted and effective.
Evolution of attacks
The evolution of attacks on web applications can be viewed from several angles:
- the complexity of web applications - as a consequence, more opportunities for errors;
- the complexity of the architecture - as a consequence, more possibilities of error;
- popularization of “kulkhackery” - as a result, there is more material in open access, more attacks;
- apparent impunity.
I will leave the ethical framework out of this article and want to talk about the technical side.
The emergence of new vectors due to the use of new technologies or the identification of vulnerabilities in the old. Also, some of the vulnerabilities may be "overboard" and not used for many years, such as the External External XML: the first mentions are dated 2002 , the specified vectors are 2009 , mass exploitation began from 2011-2012 almost everywhere, for example phpmyadmin . XXE vulnerabilities were found (as part of the BugBounty program) on Yandex, Vkontakte, Uber and many other resources.
Another important factor in the development of attack vectors are embedded protective equipment. We installed a vulnerable web application, specifying the type of vulnerability and protecting the web application with the protection service: http://vulns.pentestit.ru .
http://vulns.pentestit.ru/wp-content/plugins/kittycatfish/base.css.php?kc_ad=31&ver=2.0" Vulnerable parameter kc_ad. Attackers first of all try to reveal the presence of an injection using the quotation mark symbol, a classic of the genre: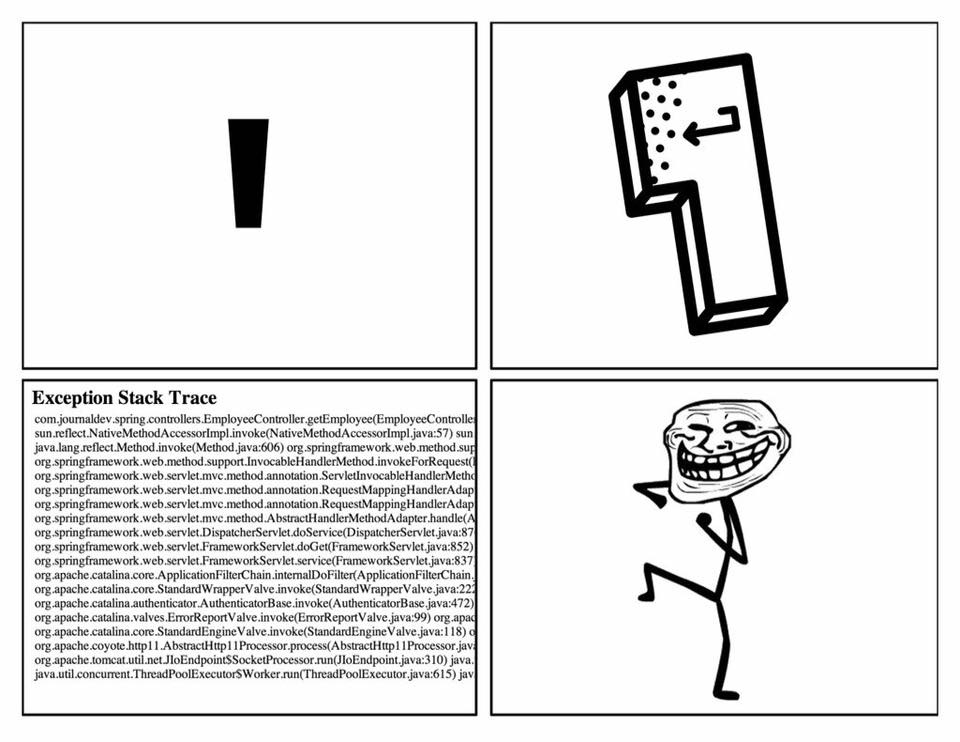
Vulnerability is present on the site, but it will not be possible to perform it immediately, therefore, the attackers use data tamping techniques to attempt to circumvent protective equipment:
http://vulns.pentestit.ru/wp-content/plugins/kittycatfish-2.2/base.css.php?kc_ad=16+group%0aby%0a1%0aUNIO%6e%0aSELEC%74%0achar%0a(107,99,95,97,100,95,99,115,115),(selec%74%0acolumn_name%0afro%6d%0a`%69nformation%5fschem%61`.columns%0awher%65%0atable_name=0x746c5f746f6b656e%0alimit%0a0,1) Such circumvention techniques also do not allow for the exploitation of a vulnerability, so attackers begin to use increasingly sophisticated evasion techniques (which I wrote about in this article: Web application security tools bypassing SQL injection operations .

This translates to the following queries:
http://vulns.pentestit.ru/wp-content/plugins/kittycatfish-2.2/kittycatfish.js.php Parameter kc_ad=%27%2F%2A%2A%2FanD%2F%2A%2A%2F3083%2F%2A%2A%2FbEtWEEN%2F%2A%2A%2F3083%2F%2A%2A%2FanD%2F%2A%2A%2F3083--%2F%2A%2A%2FiGqe&ver=2.0 Thus, it can be noted that at the moment practically all known vulnerabilities are being exploited, adjusted for the introduction of protection mechanisms in the development of applications, and for the applied protective equipment. Also, this is due to the large number of tools for carrying out attacks on web applications.
Protection measures
As a test of our skills in circumventing the protective features of a web application, we offer everyone the opportunity to test their strength on a test bench (and even get a reward for successfully operating the attack vector).
')
Source: https://habr.com/ru/post/334054/
All Articles