How the vulnerability of the payment system revealed credit card information
Recently I decided to check the sites of payment systems for vulnerabilities (ua, ru). Found the top of this kind of services, on a set of which xss, csrf and other popular vulnerabilities were discovered. There were companies that promptly eliminated vulnerabilities, thanked and agreed to cooperate, there were that silently fixed, and the most embarrassing moment - companies that did not believe in the danger of the problem, I tried to prove to them the opposite, that they were serious, offered to show their vulnerability. test account, they said they would fix it, but still have not fixed it.
There is one payment system on which there was a vulnerability, which allows to obtain critical information about the user, his password, credit card and so on. The bug was very easily reproduced, although withdrawing funds from hacked accounts was difficult for several reasons, I’ll tell you about them under the cut.
The company's website https://www.plategka.com , this is 7900 alexarank in Ukraine. I usually do not spend a lot of time on each site, because it is not yet known how the owner treats vulnerabilities on his site, maybe he will ignore the vulnerability and my time will be wasted. If I found the first standing vulnerability on the site, then I immediately reproach her, look at the owner's reaction, and if he is positive about such events and wants me to cooperate further with him, then I continue my searches.
')
The first thing I did was check the subdomains and directories in my dictionary, the following subdomains were identified
In general, brutal gave nothing.
Next, the output was viewed on google Dorks, alas, the search was not successful, and the only thing that was found was an article by Gorodnya on Habré about how he found vulnerability on plategka, and how he was paid a lot of money - only $ 8.
The next step, it was decided to test the functionality of the personal account, the csrf bugs could not be reproduced due to confirmation with a password to change the data, there were also xss filters.
The only thing that was discovered is self xss in confirming the form with a password, the danger of such bugs is minimal, so you had to look for something else and more serious.
One thing that I noticed is the pay2me service. His job is to process credit card data, which I thought was an interesting subject to study.
I used to run into news with this service , but did not pay much attention to them. Instructions for creating:
I created my link https://www.plategka.com/gateway/pay2me/qwqwqw/ .

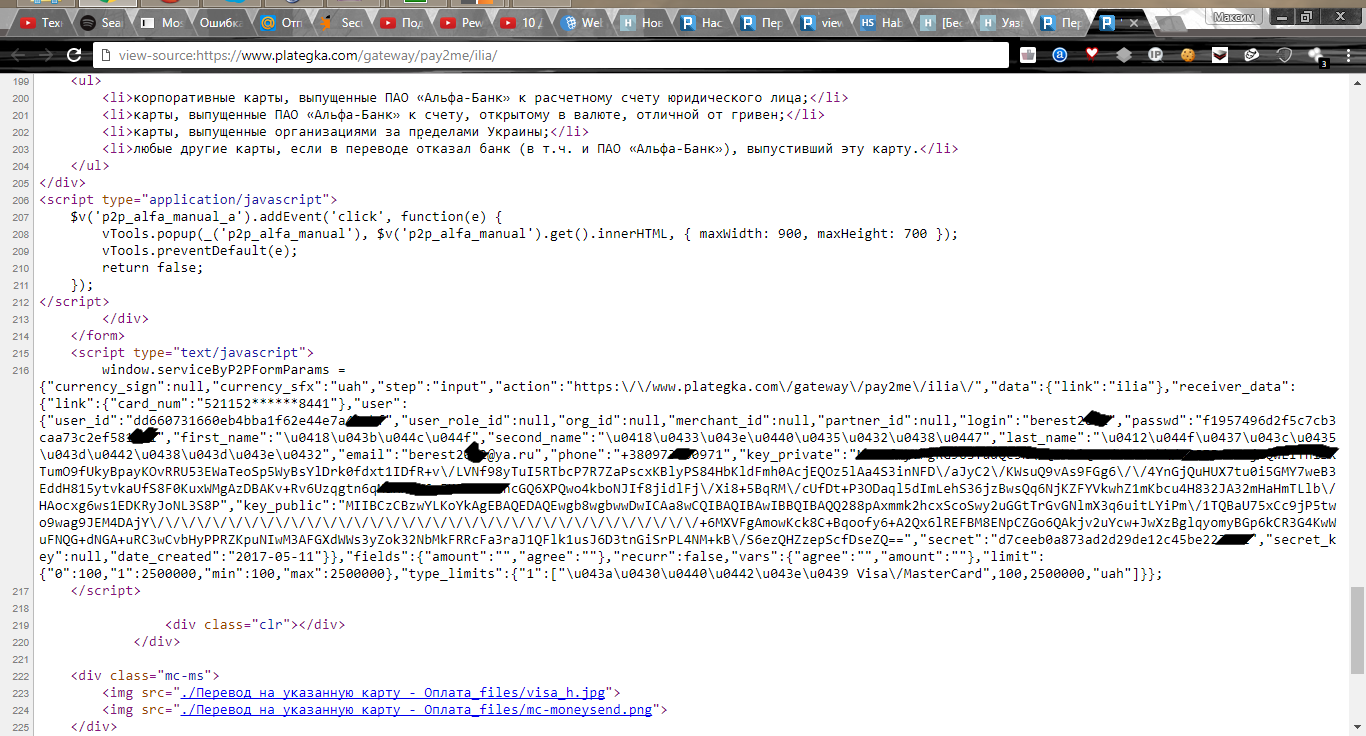
Map data was hidden, xss vulnerabilities were missing. Attention attracted the answer burp. In the source code of the page with payment in javascript, the user login, md5 hash of his password, name, email and phone number were issued:
(This data is taken from the url https://www.plategka.com/gateway/pay2me/ilia/ ).
The vulnerability was found, but one of my references for the proof will not be enough, it was decided to find other similar links.
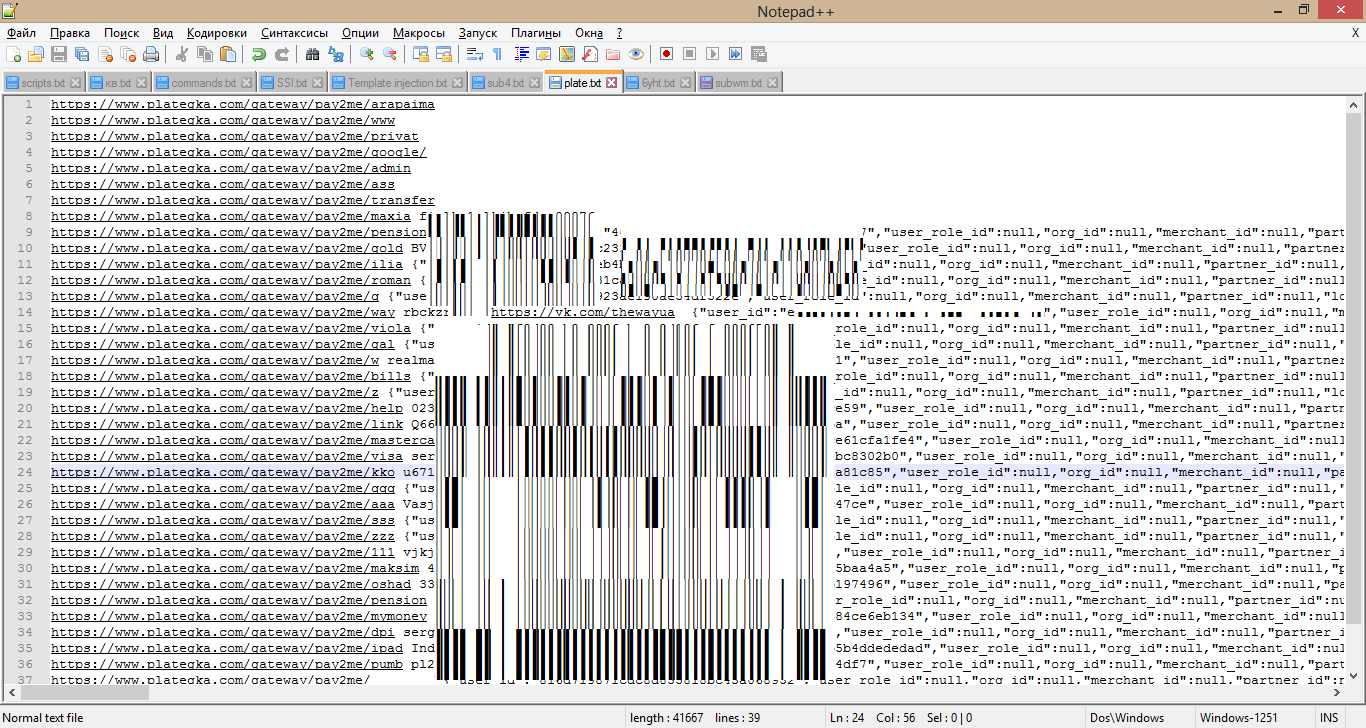
There have been attempts to find them using dorks of the type site: plategka.com inurl: pay2me /, issued only one link . I knew that there should be much more links, because the service is very popular.
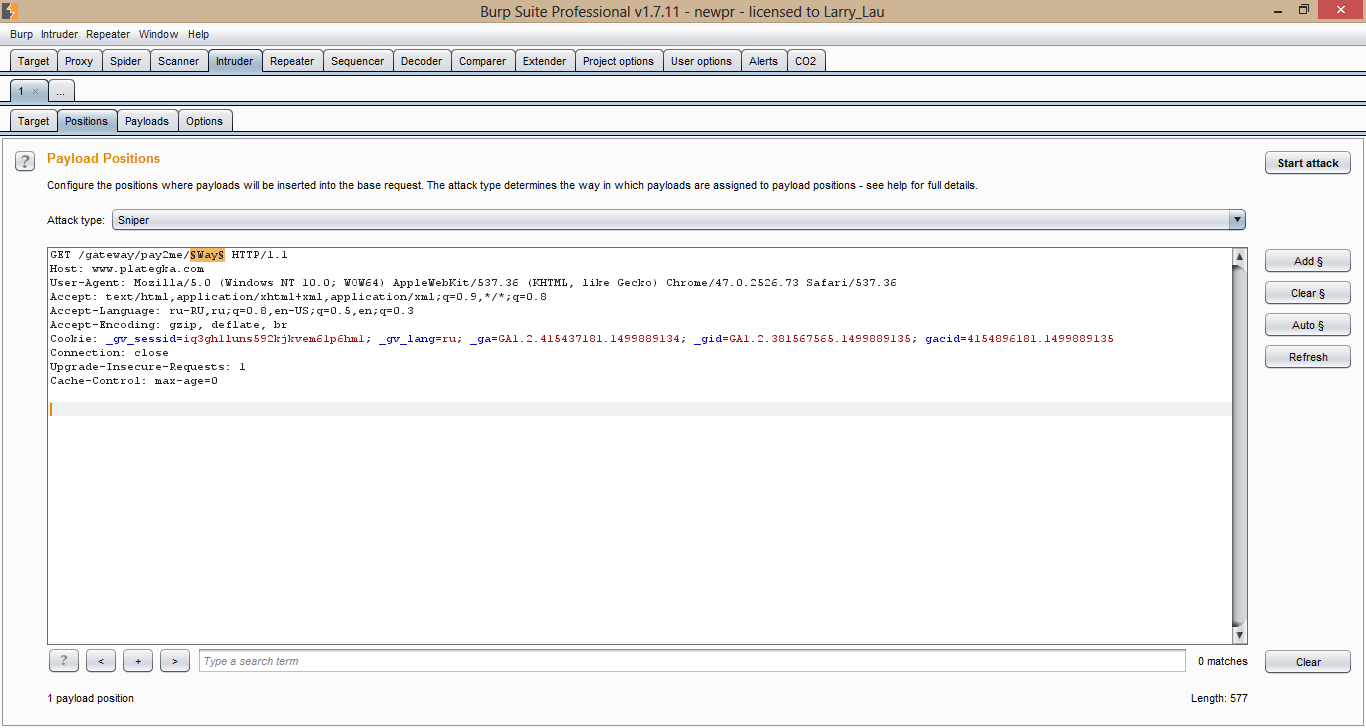
The last chance to get the cherished links was the brute force in the intruder, more than 100,000 popular English words were downloaded and search started.
It turned out to find about 40 links, about half of the passwords were found
I went to a couple of accounts to check whether cvv2 and other card data is encrypted.
On the first account I found 3 valid cards:

The second was 20:
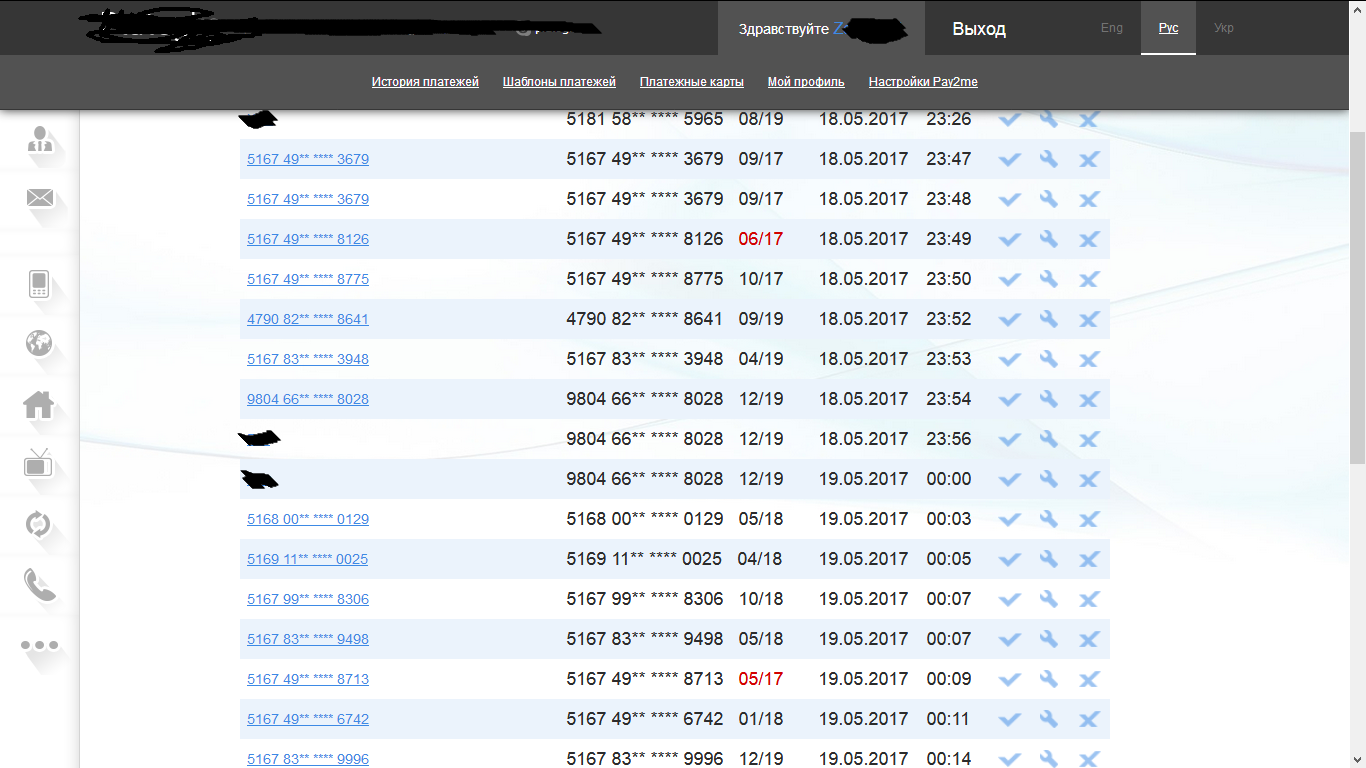
cvv in your account is hidden, information is disclosed only about 10 digits of the card number and its expiration date . To cash out cards, you can, for example, replenish webmoney, or another electronic wallet. But in order to do this, you will have to enter the cvv2 code in the payment confirmation, even if the card has been verified.
The first thing we can do is to enter a random cvv2 code, for example 111. Often we will be redirected to enter otp from the bank, and then the payment does not work because of an invalid cvv2.

We can also roll in cvv2, but then again we may be faced with entering a code from a bank, which is hard to get around.
If we have a date and a partial card number, then a regular phishing attack can force the user to tell about his card number (we received an email , phone number , name , I could even get several links to user pages on social networks), even a regular letter like: “You have won a cash prize, to receive it you need to send us your card number” may work, the action does not require the provision of critical confidential data.
To pick up cvv2, you can use some kind of online store, only 1000 requests and we picked up the code ( here's an article about it ). Of course, some stores make a redirect to enter otp from a bank, but many “foreign” stores immediately write off money without the need for a redirect.
The vulnerability was reported almost immediately after the brute force, complete with the data on the vulnerability and sent the user base, which were promptly frozen, and the bug was quickly eliminated.
For the vulnerability they paid only $ 100, they said that in order to get more, I have to find out all the credit card details from my account.
Chronology:
July 13 at 5:00 pm - the report has been sent.
13.07 - the vulnerability is fixed.
July 20 - $ 100 reward paid.
24.07 - the article was agreed with those of plategka.com.
Conclusion from the article: Despite the stated passage of PCI DSS, I would recommend sites to periodically check for vulnerabilities, and for customers to get virtual cards for use on the Internet.
PS:If you need a security audit, write here . Also, if you are interested in monitoring new articles, you can subscribe to vk / twitter / telegram, links below.
Previous article .
There is one payment system on which there was a vulnerability, which allows to obtain critical information about the user, his password, credit card and so on. The bug was very easily reproduced, although withdrawing funds from hacked accounts was difficult for several reasons, I’ll tell you about them under the cut.
The company's website https://www.plategka.com , this is 7900 alexarank in Ukraine. I usually do not spend a lot of time on each site, because it is not yet known how the owner treats vulnerabilities on his site, maybe he will ignore the vulnerability and my time will be wasted. If I found the first standing vulnerability on the site, then I immediately reproach her, look at the owner's reaction, and if he is positive about such events and wants me to cooperate further with him, then I continue my searches.
')
The first thing I did was check the subdomains and directories in my dictionary, the following subdomains were identified
mail.plategka.com
test.plategka.comIn general, brutal gave nothing.
Next, the output was viewed on google Dorks, alas, the search was not successful, and the only thing that was found was an article by Gorodnya on Habré about how he found vulnerability on plategka, and how he was paid a lot of money - only $ 8.
The next step, it was decided to test the functionality of the personal account, the csrf bugs could not be reproduced due to confirmation with a password to change the data, there were also xss filters.
The only thing that was discovered is self xss in confirming the form with a password, the danger of such bugs is minimal, so you had to look for something else and more serious.
One thing that I noticed is the pay2me service. His job is to process credit card data, which I thought was an interesting subject to study.
I used to run into news with this service , but did not pay much attention to them. Instructions for creating:
In your account there is a corresponding tab - “Pay2me settings”. To create a unique link, you must enter its name, 16-digit card number and press the "Add" button.
I created my link https://www.plategka.com/gateway/pay2me/qwqwqw/ .

Map data was hidden, xss vulnerabilities were missing. Attention attracted the answer burp. In the source code of the page with payment in javascript, the user login, md5 hash of his password, name, email and phone number were issued:
{“user_id”:”dd660731660eb4bba1f62e44e7″,”user_role_id”:null,”org_id”:null,”merchant_id”:null,”partner_id”:null,”login”:”berest****”,”passwd”:”f1957496d2f5c7cb3caa73c2e*******”,”first_name”:”\u0418\u043b\u044c\u044f”,”second_name”:”\u0418\u0433\u043e\u0440\u0435\u0432\u0438\u0447″,”last_name”:”\u0412\u044f\u0437\u043c\u0435\u043d\u0442\u0438\u043d\u043e\u0432″,”email”:”berest****@ya.ru”,”phone”:”+38097360″,”key_private”:”inNFD\/aJyC2\/KWsuQ9vAs9FGg6\/\/4YnGjQuHUX7tu0i5GMY7weB3EddH815ytvkaUfS8F0KuxWMgAzDBAKv+Rv6Uzqgtn6qMaHH8N6v5KFWFeeRncGQ6XPQwo4kboNJIf8jidlFj\/Xi8+5BqRM\/cUfDt+P3ODaql5dImLehS36jzBwsQq6NjKZFYVkwhZ1mKbcu4H832JA32mHaHmTLlb\/HAocxg6ws1EDKRyJoNL3S8P”,”key_public”:”/\/\/\/\/\/\/\/\/\/\/\/\/\/\/\/\/\/\/+6MXVFgAmowKck8C+Bqoofy6+A2Qx6lREFBM8ENpCZGo6QAkjv2uYcw+JwXzBglqyomyBGp6kCR3G4KwWuFNQG+dNGA+uRC3wCvbHyPPRZKpuNIwM3AFGXdWWs3yZok32NbMkFRRcFa3raJ1QFlk1usJ6D3tnGiSrPL4NM+kB\/S6ezQHZzepScfD”,”secret”:”d7ceeb0a873ad2d29de12c45b******”,”secret_key”:null,”date_created”:”2017-05-11″} (This data is taken from the url https://www.plategka.com/gateway/pay2me/ilia/ ).

The vulnerability was found, but one of my references for the proof will not be enough, it was decided to find other similar links.
There have been attempts to find them using dorks of the type site: plategka.com inurl: pay2me /, issued only one link . I knew that there should be much more links, because the service is very popular.
The last chance to get the cherished links was the brute force in the intruder, more than 100,000 popular English words were downloaded and search started.

It turned out to find about 40 links, about half of the passwords were found

I went to a couple of accounts to check whether cvv2 and other card data is encrypted.
On the first account I found 3 valid cards:

The second was 20:

cvv in your account is hidden, information is disclosed only about 10 digits of the card number and its expiration date . To cash out cards, you can, for example, replenish webmoney, or another electronic wallet. But in order to do this, you will have to enter the cvv2 code in the payment confirmation, even if the card has been verified.
The first thing we can do is to enter a random cvv2 code, for example 111. Often we will be redirected to enter otp from the bank, and then the payment does not work because of an invalid cvv2.

We can also roll in cvv2, but then again we may be faced with entering a code from a bank, which is hard to get around.
If we have a date and a partial card number, then a regular phishing attack can force the user to tell about his card number (we received an email , phone number , name , I could even get several links to user pages on social networks), even a regular letter like: “You have won a cash prize, to receive it you need to send us your card number” may work, the action does not require the provision of critical confidential data.
To pick up cvv2, you can use some kind of online store, only 1000 requests and we picked up the code ( here's an article about it ). Of course, some stores make a redirect to enter otp from a bank, but many “foreign” stores immediately write off money without the need for a redirect.
The vulnerability was reported almost immediately after the brute force, complete with the data on the vulnerability and sent the user base, which were promptly frozen, and the bug was quickly eliminated.
For the vulnerability they paid only $ 100, they said that in order to get more, I have to find out all the credit card details from my account.
Chronology:
July 13 at 5:00 pm - the report has been sent.
13.07 - the vulnerability is fixed.
July 20 - $ 100 reward paid.
24.07 - the article was agreed with those of plategka.com.
Conclusion from the article: Despite the stated passage of PCI DSS, I would recommend sites to periodically check for vulnerabilities, and for customers to get virtual cards for use on the Internet.
PS:
Previous article .
Source: https://habr.com/ru/post/333930/
All Articles