Security Week 29: How to crack ICO, RCE-bug in tens of millions of installations, Nukebot went to the people
 Hacking a one-page Wordpress website and stealing $ 7.7 million is no longer the scenario of an illiterate movie about hackers, but an accomplished reality. Technology! Still noticed the ICO craze? It's like an IPO when the company first issues its shares and sells them through the exchange. Only not shares, but tokens, not through a stock exchange, but directly, and, most often, for cryptocurrency.
Hacking a one-page Wordpress website and stealing $ 7.7 million is no longer the scenario of an illiterate movie about hackers, but an accomplished reality. Technology! Still noticed the ICO craze? It's like an IPO when the company first issues its shares and sells them through the exchange. Only not shares, but tokens, not through a stock exchange, but directly, and, most often, for cryptocurrency.Is this all for? It is very easy for cryptoinvestors to get expensive bitcoins and ethers that are poised, and it is very easy to invest them in a hyip startup. Took, and translated to the desired address, no hassle with the stock exchange and brokers. Fast, easy, safe.
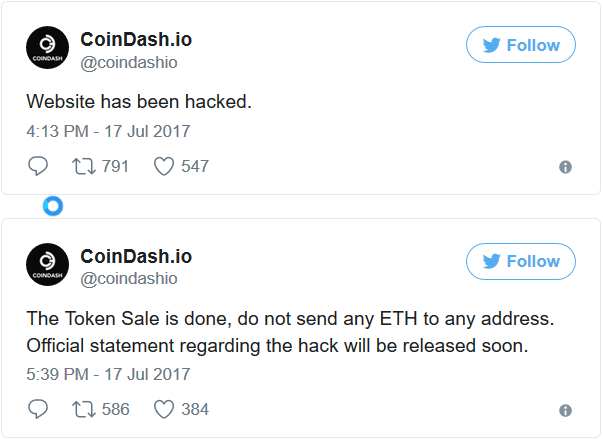
Unknown hackers also appreciated the convenience of the ICO and decided to participate. Found talented guys CoinDash, who ICO using the site on Wordpress, broke it, changed the ethereum-address for investment - and they sit, count the wallowing millions. The first victims were 2,000 investors, who lost 37,000 broadcasts (at that time, $ 209 for each broadcast).
')
Even after CoinDash announced this dirty hack, investors continued to send air to the left address and send it already worth more than $ 10 million. The company decided to issue its tokens to the victims of hackers, so investors should not suffer, only the company itself.
Tens of millions of software installations and IoT devices contain a critical RCE vulnerability.
 News Research News from the world of the Internet of things is very monotonous, but the trend is quite apocalyptic - the farther into the forest, the more holes. And all because when a security researcher has nothing to do, he takes the first available IoT device, finds vulnerability there in half an hour, estimates the number of copies sold, and here you are, the scenario of the next routerkalipsis in all specialized publications!
News Research News from the world of the Internet of things is very monotonous, but the trend is quite apocalyptic - the farther into the forest, the more holes. And all because when a security researcher has nothing to do, he takes the first available IoT device, finds vulnerability there in half an hour, estimates the number of copies sold, and here you are, the scenario of the next routerkalipsis in all specialized publications!Somehow, Senrio did something like that and studied a cool security camera from Axis Communications. They quickly learned to call a buffer overflow through the 80th port and intercept the video stream without re-authentication, reboot the camera, and pause recording. Vulnerability dubbed Devil's Ivy.
After that, they found out that the same software is in other 248 models of the Axis Communications line, and this bug, of course, is also there. They scanned the Internet using Shodun - found 14,700 vulnerable cameras online (it is clear that most of these cameras are sitting behind firewalls).
Then another link of this chain came to light: the fact is that the leaky component, the gSOAP library, is used very much where, including in the products of Microsoft, IBM, Xerox and Adobe. This does not mean that all products using gSOAP are vulnerable, but definitely the problem is very large. This is where the tens of millions declared in the news came from. From these very approximate numbers it does not get scary, but if suddenly any self-propelled Trojan worm using this hole appears, it will not seem to be enough.
Numerous Nukebot modifications found
News Research At the end of March this year, the author of the Trojan-banker Nukebot laid out his source code in the darknet . Unfortunately, such actions are not uncommon, the motives are usually not clear, and the consequences are extremely unpleasant. The guys, who are eager for easy money, who are unable to write such a thing themselves, or buy a darkvar subscription on a darknet, use such charity. and flood the Internet with slightly modified Trojans.
And now - a month and a half has passed, and our analysts have already found a bunch of samples. True, most of them are essentially inoperable - even the management server is not registered in the code. Whether this is a test sample, or part of the vonnabi-hackers did not manage to build the botnet's command infrastructure (and encrypt the code). However, about 5% of the samples are quite working, and probably bring money to their masters.

By the way, researchers from IBM conducted a small investigation and put forward a version of why the author published the Nukebot sources. It turns out that he tried to organize sales of the Trojan without his checking by the site administration on the darknet. After this case was stopped, he ewed elsewhere under a different name, and was, after all, banned everywhere. Since no one bought from him, he decided to just distribute the code. All this lack of professionalism doesn’t really fit in with the quite good technical level of Nukebot, but there’s no point in guessing.

Antiquities
"Sunday-1631"
Very dangerous - it deletes files when they are launched for execution. On Sunday, it says “Today is SunDay! Why do you work so hard? All work and no play Come on! Let's go out and have some fun! ”
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 35.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/333882/
All Articles