Getsploit: search and download exploits on an aggregated database
When I thought about the further development vector of Vulners , I paid attention to our older brothers - the Exploit-DB database. One of the main utilities in their arsenal is searchsploit . This is a console utility that allows you to search for exploits by user search queries and immediately get their source codes. It is the basic part of Kali Linux and operates on exploit data from the Exploit-DB database. What is the most "delicious" that the utility can work with a local database and you can always take it with you. So why are we worse? We collected in Vulners not only a collection of exploits from Exploit-DB, but also Packet Storm, 0day.today, Seebug, Zero Science Lab and many others. Well, let's invent a new bike with preference and poetess.
We look more attentively at searchsploit
And we see inside the bash script 711 lines long. He downloads a copy of the data from the public repository exploit-database and is already searching for it. But where is the Google-style syntax and other delights of modern search? Alas, in their approach there were both pluses and minuses. The advantages are that they are able to find exploits by applicability criteria. Cons - rather poor functionality for inaccurate search. At this point, the idea of integrating with him was dropped and the decision to write your fork became dominant.
What should getsploit do?
Let's start with the fact that we define functionality.
- Search for exploits throughout the Vulners collection using Full Text Search and Lucene
- Saving exploit source codes to disk
- Offline search with local database
- Cross-platform and minimum dependencies
- Be open source
Let there be code
As a result, the utility was implemented in Python with compatibility from Python 2.6 to Python 3.6. I tried to keep the main keys identical with searchsploit in order to not have to get used again.
isox$ git clone https://github.com/vulnersCom/getsploit isox$ cd getsploit isox$ ./getsploit.py -h usage: Exploit search and download utility [-h] [-t] [-j] [-m] [-c COUNT] [-l] [-u] [query [query ...]] positional arguments: query Exploit search query. See https://vulners.com/help for the detailed manual. optional arguments: -h, --help show this help message and exit -t, --title Search JUST the exploit title (Default is description and source code). -j, --json Show result in JSON format. -m, --mirror Mirror (aka copies) search result exploit files to the subdirectory with your search query name. -c COUNT, --count COUNT Search limit. Default 10. -l, --local Perform search in the local database instead of searching online. -u, --update Update getsploit.db database. Will be downloaded in the script path. The main search mechanics are based on the Vulners API. This way you will always get up-to-date data at the “here and now”. Well, let's look for wordpress exploits?
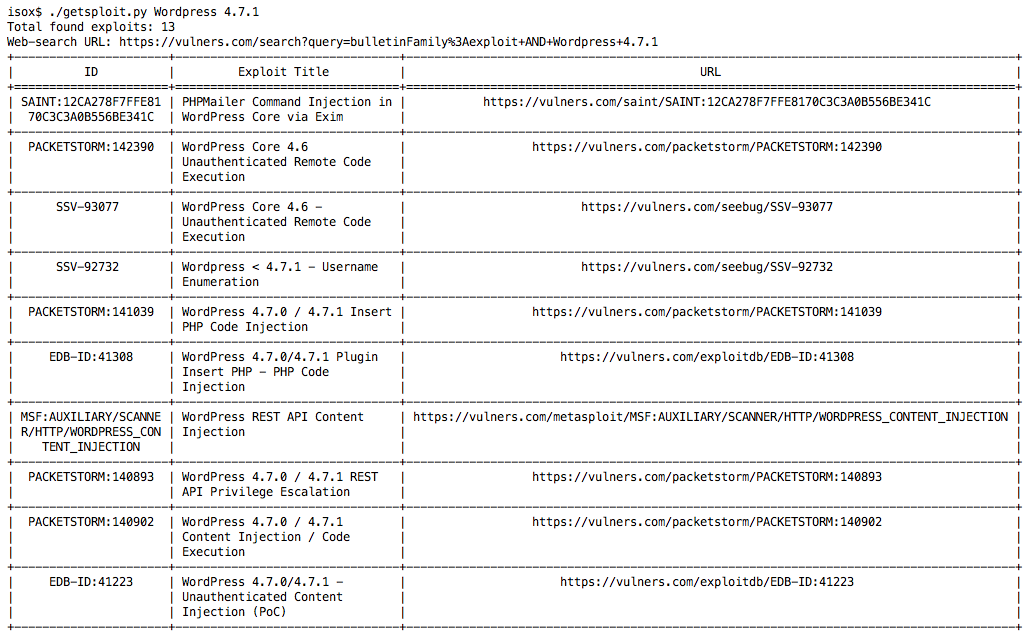
Pretty good, huh? Now let's try to limit us only to the Packet Storm collection. The syntax of expressions completely coincides with the search line of the site and can be peeped on the help page.
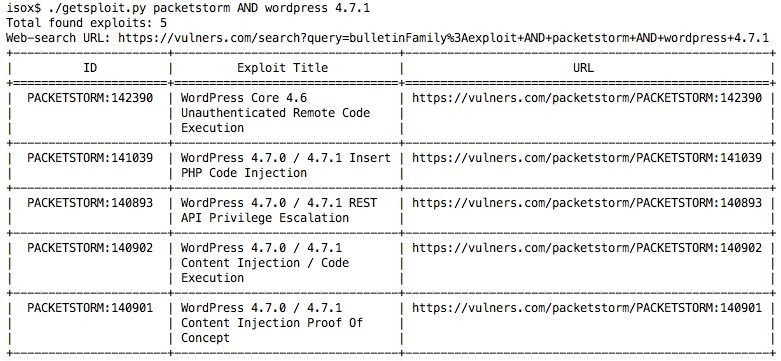
So, the exploits we need are found. Now they need to be saved for later use. To do this, use the "-m" key. After this, the utility will create a folder with your search and load the exploits there.
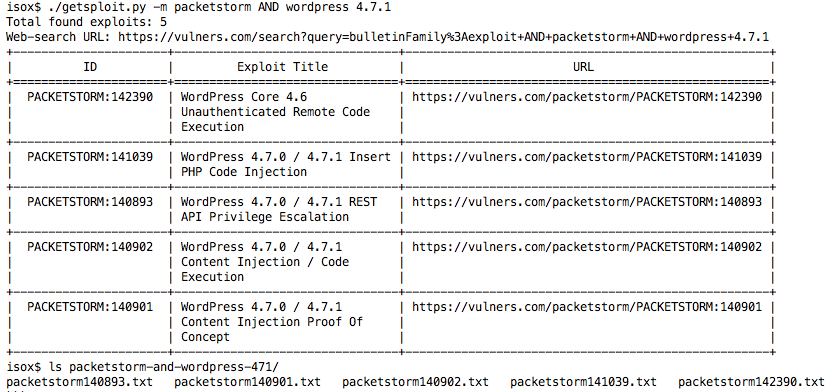
But what to do if we do not have an online connection to the Internet? Remember this while it is still available and make "--update"!
isox$ ./getsploit.py --update Downloading getsploit database archive. Please wait, it may take time. Usually around 5-10 minutes. 219686398/219686398 [100.00%] Unpacking database. Database download complete. Now you may search exploits using --local key './getsploit.py -l wordpress 4.7' With this query, getsploit downloads a SQLite database with the entire collection of exploits. This is about 594 megabytes of data at the time of this writing.
Please note that if you have Python compiled without sqlite3 support (which is rare in principle), then the local database, alas, will not work.
Here we had to sacrifice compatibility for the sake of speed and full text search capabilities with the FTS4 SQLite module.
But everything is not so bad, the majority of Python builds come with the sqlite3 module by default. Let's try to find exploits locally?
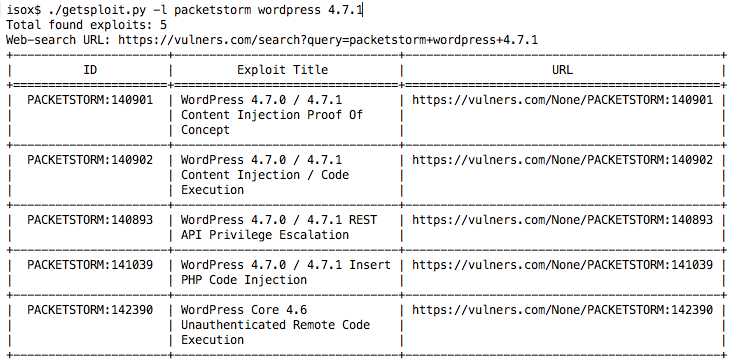
Fine! Now you can take with you the entire collection of exploits with Vulners and use it offline without registration and SMS.
And of course, the source codes are on our GitHub .
Pull-requests are extremely welcome.
')
Source: https://habr.com/ru/post/333808/
All Articles