Was there a hacking of "Gosuslug"? Yandex Hypothesis
On Thursday, the network reported that a potentially dangerous code was found on the website of the State Services, and today we want to share with you the results of our own investigation and once again remind you of the importance of using Content Security Policy.

The first threat reports mentioned the introduction of fragments with an iframe on the site’s pages, loading data from at least 15 questionable domains. Our analysts quickly began to study the code of the site pages to protect users by using our existing mechanism to prevent such threats. We will tell about the mechanism a little lower, but the main thing here is in the other - the found code fragments were well known to us.
')
If you are familiar with the development of extensions for popular browsers, then you know that the authors have not so many ways to earn money on their own creations. Paid extensions almost do not occur, and as a result, the majority of attempts to make money is built around the fact that they simply embed advertising in the code of the pages visited by users. To do this, there are whole affiliate programs that offer authors of extensions to embed code that their extensions must embed in all pages visited by the user. Usually, the embedded fragment is engaged in showing additional, often not very high-quality advertising, but, generally speaking, technologically it allows for something more dangerous. At gosuslugi.ru there were code snippets, which in such extensions can be used to collect statistics or display ads.
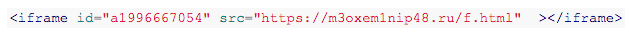
Such fragments fall into the page code on the client side if it has an extension installed. And here the question arises: “how then did this code end up on the server side?” And we have a hypothesis.
We believe that the appearance of this code on the pages of gosuslugi.ru is not associated with a hacking, targeted attack. It is more likely that the administrator who edited the contents of these pages had a similar extension installed. It injected the extraneous code into the document when it was loaded onto the client side, and it appeared on the server after the employee had saved his changes. One more fact speaks in favor of this version. We carefully monitored all the found fragments, and none of them began to upload any content - the authors of the code hardly expected that they would get access to the users of the public services portal. But this does not mean that there was no threat - they could begin to do it at any time, as soon as they understood, on the pages of which site their code appeared.
And now about the protection mechanism. The order of percentage of Yandex users has a similar problem with extraneous content in the pages visited. And that's a lot. Therefore, we have long and actively been fighting with such a threat. First of all, we protect users of Yandex. Browser with the help of a mechanism that prevents the loading of data from identified questionable addresses. Information about new threats quickly gets into the SafeBrowsing database, which is available to the Browser, Search and our other services using a special API . This allows us to quickly stop the spread of epidemics without having to release an update for the application itself.
Fortunately, in the case of state services, Yandex users for the most part have already been protected: 15 of the found fragments out of 16 have already been entered into the SafeBrowsing database even before the situation with the site as part of the usual process of searching for threats.
And something else. Having a shield on the client side is good, but you should not forget about protection on the service side too. We recommend that all major services working with private user data implement Content Security Policy support. This will block the download of third-party content and protect your users. Yandex services have long used CSP to prevent the downloading of unauthorized code.

The first threat reports mentioned the introduction of fragments with an iframe on the site’s pages, loading data from at least 15 questionable domains. Our analysts quickly began to study the code of the site pages to protect users by using our existing mechanism to prevent such threats. We will tell about the mechanism a little lower, but the main thing here is in the other - the found code fragments were well known to us.
')
If you are familiar with the development of extensions for popular browsers, then you know that the authors have not so many ways to earn money on their own creations. Paid extensions almost do not occur, and as a result, the majority of attempts to make money is built around the fact that they simply embed advertising in the code of the pages visited by users. To do this, there are whole affiliate programs that offer authors of extensions to embed code that their extensions must embed in all pages visited by the user. Usually, the embedded fragment is engaged in showing additional, often not very high-quality advertising, but, generally speaking, technologically it allows for something more dangerous. At gosuslugi.ru there were code snippets, which in such extensions can be used to collect statistics or display ads.

Such fragments fall into the page code on the client side if it has an extension installed. And here the question arises: “how then did this code end up on the server side?” And we have a hypothesis.
We believe that the appearance of this code on the pages of gosuslugi.ru is not associated with a hacking, targeted attack. It is more likely that the administrator who edited the contents of these pages had a similar extension installed. It injected the extraneous code into the document when it was loaded onto the client side, and it appeared on the server after the employee had saved his changes. One more fact speaks in favor of this version. We carefully monitored all the found fragments, and none of them began to upload any content - the authors of the code hardly expected that they would get access to the users of the public services portal. But this does not mean that there was no threat - they could begin to do it at any time, as soon as they understood, on the pages of which site their code appeared.
And now about the protection mechanism. The order of percentage of Yandex users has a similar problem with extraneous content in the pages visited. And that's a lot. Therefore, we have long and actively been fighting with such a threat. First of all, we protect users of Yandex. Browser with the help of a mechanism that prevents the loading of data from identified questionable addresses. Information about new threats quickly gets into the SafeBrowsing database, which is available to the Browser, Search and our other services using a special API . This allows us to quickly stop the spread of epidemics without having to release an update for the application itself.
Fortunately, in the case of state services, Yandex users for the most part have already been protected: 15 of the found fragments out of 16 have already been entered into the SafeBrowsing database even before the situation with the site as part of the usual process of searching for threats.
And something else. Having a shield on the client side is good, but you should not forget about protection on the service side too. We recommend that all major services working with private user data implement Content Security Policy support. This will block the download of third-party content and protect your users. Yandex services have long used CSP to prevent the downloading of unauthorized code.
Source: https://habr.com/ru/post/333404/
All Articles