The balance between security devices in proxy mode and the impact on network performance
The almost exponential growth over the past decade of cyber attacks on various types of applications has reinforced the need for an improved network perimeter security infrastructure that can check and block all types of traffic. Next-generation security device manufacturers (NGFW) understand the need for deep inspection (deep inspection) and have moved beyond the transport layer firewall to the application level for web, email, file transfer, etc.

')
The next big problem that such security devices face is the quality of inspections as the volume of encrypted traffic increases. To ensure that security devices catch all traffic, including encrypted traffic, they must be implemented in proxy mode when performing intrusion prevention tasks. Implementing a proxy for security purposes usually involves reduced performance and latency.
The effectiveness of security checks for encrypted traffic is undeniable. Nevertheless, history has shown that any in-line security device that introduces significant delays is either reserved or out-of-band moves after a certain time. Here we discuss the proxy implementation, the overhead that they add to the network, test scripts that can help detect such performance effects, as well as tips and tricks for a better proxy implementation.
What is a proxy?
Simply put, a proxy is a computer or device that mediates between two systems, such as:
- hosts on a secure network and the Internet;
- Internet clients and servers in a private network.
A proxy terminates any connection initiated by the client and opens a new connection between itself and the server. This helps the proxy to achieve multiple goals as an intermediary, such as client authentication, load balancing between multiple servers, faster responses through caching mechanisms, and most importantly, security by checking traffic.

Here we focus on the security devices and the effects of enabling the proxy mode on them.
Security proxies
In order to achieve security objectives, a security device needs to track all sessions, analyze each downloaded file, detect any malicious activity and prevent threats from entering protected targets. Now that most Internet traffic is encrypted, security devices are required to be deployed in proxy mode to effectively inspect all of this encrypted traffic. This has to be paid for with performance — several operations are listed below that affect the performance of security devices in proxy mode, but are needed for security tasks:
- Opening of two separate connections for each incoming connection: one from the initiator of the connection to the proxy, and the other from the proxy to the addressee;
- Interception of encrypted SSL traffic and decryption of all payloads, checking all traffic, re-encryption and sending to the addressee;
- Based on the check - block / report on any suspicious traffic, while ensuring the unimpeded passage of legitimate traffic.
The impact of enabling proxy on performance
The deep inspection functionality makes the security devices in proxy mode the main bottleneck (the so-called bottleneck) and can lead to a decrease in the performance of the entire network.
Because of the strong SSL ciphers and large key sizes, the proxy can affect performance, even if the network is running at 10% of maximum capacity.
The performance degradation in most cases is accompanied by errors caused by packet re-request, session delay (session delay), session failure (TCP Retries and Timeouts), and transaction errors (Packet Drop).
Tests demonstrating the effect of enabling proxies
To make the proxy firewall (FW) more reliable and efficient when handling these bottlenecks, you need to test and verify them before deployment. The following shows the serious delays that occur when the proxy mode is enabled on security devices.
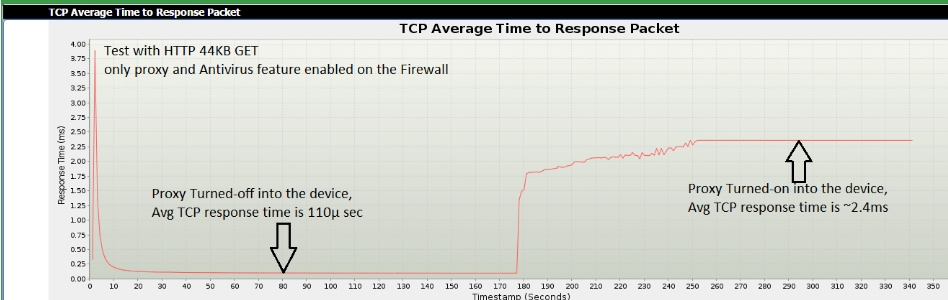
Scenario 1 : Proxy without SSL. HTTP GET with a 200OK response with a page size of 44 KB. For the test, IXIA BreakingPoint is used to simulate HTTP clients and servers with a security device in the middle. The goal of the test is to reach the maximum number of unique TCP / HTTP sessions per second. To understand the impact of proxy performance, proxy mode and inspection were enabled at the time of testing.
Observation 1 : The average TCP response time (response), when the device works without and with proxy mode, differs by more than 22 times.
Observation 2 : The average duration of a TCP session is increased by 225 times, if you compare the mode of the device without and with a proxy.

Scenario 2 : Similar to the scenario described above, except that the HTTP-GET 44KB page is now encrypted with a TLS1.1 session.
Observation 1 : with encrypted traffic, in proxy mode, a TCP response time increases by 20 times. [Note. In general, the TCP response time is higher for encrypted traffic due to the delay that a proxy contributes to, which spends more resources processing this traffic].

Observation 2 : The average duration of a TCP session increases by a staggering 400 times.

Tips for implementing an effective proxy
1. Choosing the right manufacturer
Hardware and software is constantly optimized for better proxy processing. The so-called “unloading” (offloading) and methods for allocating allocated resources increase the efficiency of the proxy mode in security devices. Customers should be aware of this and compare the characteristics of security devices in proxy mode, as one of the criteria for selecting a manufacturer.
2. Choosing the right ciphers and encryption methods when possible
The choice of ciphers that a client or server uses cannot always be monitored by security specialists, but they should ensure, where possible, that the encrypted traffic uses the most efficient ciphers that provide better performance without compromising security (for example, ECDHE-ECDSA 256 -bit for the exchange of public keys).
3. Use different levels of encryption on secure and non-secure sides
Proxy, according to the design, should work with two separate compounds. A secure side connection, which usually opens between a proxy server and the end host, may provide lower TLS encryption, since it is located behind the security devices / perimeter. The user can choose lower encryption or no encryption on the secure side. This will increase the efficiency of one of the two connections and, therefore, improve the overall performance of the security device in proxy mode.

findings
The two tests described here demonstrate the extreme impact of proxy mode on security devices. On the other hand, the increased safety performance of in-line devices in proxy mode reduces security risks. Organizations no longer want to increase security risks, even if it means better performance, so we see a large introduction of proxy mode in security devices. When we implement proxies in security infrastructures, effective and efficient deployment and better security appliance characteristics will help reduce the impact of proxies on network performance and, accordingly, business performance.
The study is based on Amritam Putatunda and Rakesh Kumar.
Additional resources:
https://www.ixiacom.com/
https://www.ixiacom.com/products/breakingpoint
https://www.ixiacom.com/products/breakingpoint-ve
https://www.ixiacom.com/products/breakingpoint-aws

')
The next big problem that such security devices face is the quality of inspections as the volume of encrypted traffic increases. To ensure that security devices catch all traffic, including encrypted traffic, they must be implemented in proxy mode when performing intrusion prevention tasks. Implementing a proxy for security purposes usually involves reduced performance and latency.
The effectiveness of security checks for encrypted traffic is undeniable. Nevertheless, history has shown that any in-line security device that introduces significant delays is either reserved or out-of-band moves after a certain time. Here we discuss the proxy implementation, the overhead that they add to the network, test scripts that can help detect such performance effects, as well as tips and tricks for a better proxy implementation.
What is a proxy?
Simply put, a proxy is a computer or device that mediates between two systems, such as:
- hosts on a secure network and the Internet;
- Internet clients and servers in a private network.
A proxy terminates any connection initiated by the client and opens a new connection between itself and the server. This helps the proxy to achieve multiple goals as an intermediary, such as client authentication, load balancing between multiple servers, faster responses through caching mechanisms, and most importantly, security by checking traffic.

Here we focus on the security devices and the effects of enabling the proxy mode on them.
Security proxies
In order to achieve security objectives, a security device needs to track all sessions, analyze each downloaded file, detect any malicious activity and prevent threats from entering protected targets. Now that most Internet traffic is encrypted, security devices are required to be deployed in proxy mode to effectively inspect all of this encrypted traffic. This has to be paid for with performance — several operations are listed below that affect the performance of security devices in proxy mode, but are needed for security tasks:
- Opening of two separate connections for each incoming connection: one from the initiator of the connection to the proxy, and the other from the proxy to the addressee;
- Interception of encrypted SSL traffic and decryption of all payloads, checking all traffic, re-encryption and sending to the addressee;
- Based on the check - block / report on any suspicious traffic, while ensuring the unimpeded passage of legitimate traffic.
The impact of enabling proxy on performance
The deep inspection functionality makes the security devices in proxy mode the main bottleneck (the so-called bottleneck) and can lead to a decrease in the performance of the entire network.
Because of the strong SSL ciphers and large key sizes, the proxy can affect performance, even if the network is running at 10% of maximum capacity.
The performance degradation in most cases is accompanied by errors caused by packet re-request, session delay (session delay), session failure (TCP Retries and Timeouts), and transaction errors (Packet Drop).
Tests demonstrating the effect of enabling proxies
To make the proxy firewall (FW) more reliable and efficient when handling these bottlenecks, you need to test and verify them before deployment. The following shows the serious delays that occur when the proxy mode is enabled on security devices.
Scenario 1 : Proxy without SSL. HTTP GET with a 200OK response with a page size of 44 KB. For the test, IXIA BreakingPoint is used to simulate HTTP clients and servers with a security device in the middle. The goal of the test is to reach the maximum number of unique TCP / HTTP sessions per second. To understand the impact of proxy performance, proxy mode and inspection were enabled at the time of testing.
Observation 1 : The average TCP response time (response), when the device works without and with proxy mode, differs by more than 22 times.

Observation 2 : The average duration of a TCP session is increased by 225 times, if you compare the mode of the device without and with a proxy.

Scenario 2 : Similar to the scenario described above, except that the HTTP-GET 44KB page is now encrypted with a TLS1.1 session.
Observation 1 : with encrypted traffic, in proxy mode, a TCP response time increases by 20 times. [Note. In general, the TCP response time is higher for encrypted traffic due to the delay that a proxy contributes to, which spends more resources processing this traffic].

Observation 2 : The average duration of a TCP session increases by a staggering 400 times.

Tips for implementing an effective proxy
1. Choosing the right manufacturer
Hardware and software is constantly optimized for better proxy processing. The so-called “unloading” (offloading) and methods for allocating allocated resources increase the efficiency of the proxy mode in security devices. Customers should be aware of this and compare the characteristics of security devices in proxy mode, as one of the criteria for selecting a manufacturer.
2. Choosing the right ciphers and encryption methods when possible
The choice of ciphers that a client or server uses cannot always be monitored by security specialists, but they should ensure, where possible, that the encrypted traffic uses the most efficient ciphers that provide better performance without compromising security (for example, ECDHE-ECDSA 256 -bit for the exchange of public keys).
3. Use different levels of encryption on secure and non-secure sides
Proxy, according to the design, should work with two separate compounds. A secure side connection, which usually opens between a proxy server and the end host, may provide lower TLS encryption, since it is located behind the security devices / perimeter. The user can choose lower encryption or no encryption on the secure side. This will increase the efficiency of one of the two connections and, therefore, improve the overall performance of the security device in proxy mode.

findings
The two tests described here demonstrate the extreme impact of proxy mode on security devices. On the other hand, the increased safety performance of in-line devices in proxy mode reduces security risks. Organizations no longer want to increase security risks, even if it means better performance, so we see a large introduction of proxy mode in security devices. When we implement proxies in security infrastructures, effective and efficient deployment and better security appliance characteristics will help reduce the impact of proxies on network performance and, accordingly, business performance.
The study is based on Amritam Putatunda and Rakesh Kumar.
Additional resources:
https://www.ixiacom.com/
https://www.ixiacom.com/products/breakingpoint
https://www.ixiacom.com/products/breakingpoint-ve
https://www.ixiacom.com/products/breakingpoint-aws
Source: https://habr.com/ru/post/333360/
All Articles