Solution of the promo task from BI.ZONE CTF

On May 31, BI.ZONE announced the news about the “CTFzone presidential election” . And already on June 1st, a BI.ZONE publication appeared on Habrahabr announcing the election of the president of the CTFzone , in which, like last year , the Easter Bishop is hidden. If you take a closer look at the text of the publication, you will notice that in the sentence “ Good luck with the elections!” There is a link leading to a web page containing a QR code:

QR scanner issued a message:
try_h4rd3r_try_h4rd3r_try_h4rd3r_try_h4rd3r_try_h4rd3r_try_h4rd3r_try_h4rd3r_try_h4rd3r_try_h4rd3r_try_h4rd3r
The first thing that came to mind is to find the user try_h4rd3r on twitter. The second attempt of “try hard” was that we tried to break the large original QR code into several small ones:
')




But all attempts were in vain. It was decided to download the promo_task.png file and explore in Hexed.it. The line attracted a lot of attention:
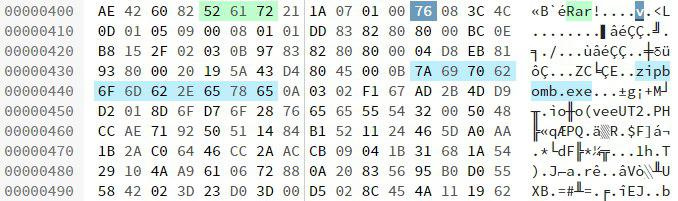
Thus, having changed the extension to
.7z , we get an archive, which we can open with 32-bit 7-Zip. The contents of the archive: zipbomb.exe is a real ZIP bomb . "Cutting the red wire" and changing the extension to .zip, we get an archive containing the file "-" of 38.1 GB in size (40,959,016,020 bytes). It was clear right away that such a file could not be read at once. It was decided to write a simple Python script that would read it in parts. def read_in_chunks(file_object, chunk_size=1024): while True: data = file_object.read(chunk_size) if not data: break yield data The result of the work was a lot of lines containing zeros, among which it was hard to find something special. Then the script was modified by a simple check:
def read_in_chunks(file_object, chunk_size=1024): while True: data = file_object.read(chunk_size) if not data: break yield data f = open('-') for piece in read_in_chunks(f): if piece.count("0") < 1023: print(piece) The result of the script:

We see the line: @ cc77af5382e431dc_bot and first of all we drive in the name of the bot in Telegram. We get the bot instructions and the task:
Selecting Base64 encoding, we decode and get:
Further, sending the result to the bot
/solve <> you can get the flag . However, today you only get this: "Sorry all flags are gone . "Good luck to everyone at CTFzone presidential election!
Thanks tugric tammio for team work on the task. If they answer you in the comments - they can be trusted.
Source: https://habr.com/ru/post/332930/
All Articles