The critical vulnerability of the BIND authentication mechanism allows you to steal and modify DNS server records
A critical vulnerability has been discovered in the popular BIND DNS server. Its operation allows an attacker to obtain the correct signature for arbitrary data and use this signature to make changes to it or to receive a list of all DNS server records (dns zone transfer attack).
What is the problem
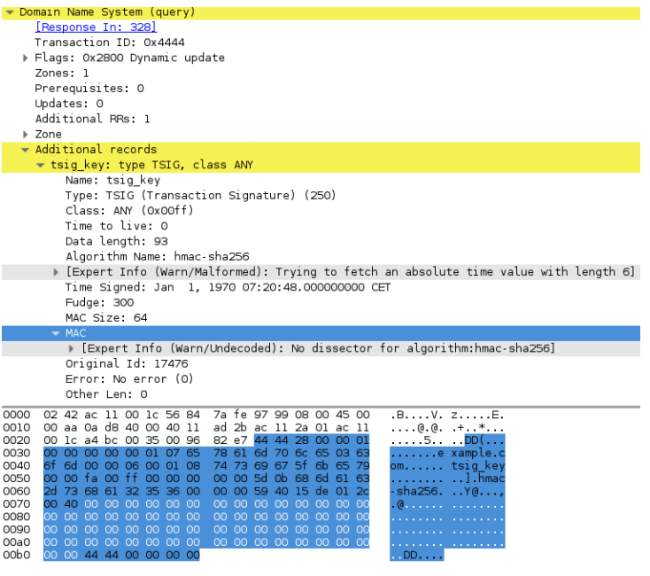
Vulnerability CVE-2017-3143 found in the implementation of the authentication protocol for BIND DNS called TSIG. Also, the TSIG protocol is used by a number of other DNS services like PowerDNS, NSD and Knot DNS.
')
Researchers at Synacktiv discovered an error in processing TSIG records, allowing an attacker who knows the name of the key to overcome the protection mechanism for zone update, alert and transfer operations.
If you send a TSIG-digest of the wrong length (more than what should be when the hashing algorithm is used), the server, instead of a blank signature, will return data from an attacker's request with the correct signature. As a result, the attacker is able to obtain the correct signature for arbitrary fake data and overcome TSIG authentication. Vulnerability can be used by hackers to modify data or gain access to a file with DNS zones.
According to RFC 2845, the response digest is computed from three fields from the query:
- A digest (MAC) from the request, along with a length field;
- records from the request (update), but without a TSIG record;
- TSIG recording itself, but without a digest.
Thus, the exploitation of a vulnerability occurs in several stages:
- The attacker sends a DNS query with zone updates and an SOA record, where instead of a digest it places the RR data of records that he intends to insert into the server database. For example, writing a TXT to one of the server-controlled zones with the text “Injected”. The length of such a digest must be greater than that implied by the hashing algorithm used, for example, with a length of more than 32 bytes for the HMAC-SHA256 algorithm.
- The server, instead of responding with a blank MAC (digest) field in the TSIG record, returns data from the attacker, including a request with zone updates and a TXT record signed by the server's secret key.
- Using the received signature, the attacker sends the same request with updating zones as in step 1, but additional records, instead of the TSIG MAC field, are in the Zones section after the SOA record, and the MAC field now contains the correct digest from step 2. For operation , the value of the Time Signed TSIG field must be the same, so that the vulnerable server uses the same data when checking the signature.
- The server, after successfully verifying the request sent, applies the data to the database, which you can learn from the log:
14-Jun-2017 07:48:55.003 client 172.17.42.1#50445/key tsig_key: updating zone 'example.com/IN': adding an RR at 'i.can.inject.records.in.the.zone.example.com' TXT "injected" According to information published by researchers, the presence of a vulnerability has been confirmed for the following versions of BIND:
- BIND 9.9.10
- BIND 9.10.5
- BIND 9.11.1
According to the company ISC, under the license of which the BIND software is distributed, the following versions are also vulnerable:
- from 9.4.0 to 9.8.8
- from 9.9.0 to 9.9.10P1
- from 9.10.0 to 9.10.5P1
- from 9.11.0 to 9.11.1P1
- 9.9.3S1 to 9.9.10S2
- from 9.10.5S1 to 9.10.5S2
Representatives of Synaktiv in their material also presented the PoC-exploit code for this vulnerability.
How to protect
ISC specialists have published a patch to eliminate the described security error. In addition, the experts of Positive Technologies created a signature for IDS Suricata, which allows detecting and preventing attempts to exploit the CVE-2017-3143 vulnerability over the network, in the archive also an example of traffic during the exploitation of this vulnerability:
Also, to detect vulnerabilities, our specialists recommend using specialized tools such as the monitoring system of security and compliance with the standards of MaxPatrol 8 .
Source: https://habr.com/ru/post/332880/
All Articles