Security Week 27: ExPetr = BlackEnergy, more than 90% of sites are insecure, in RCE-vulnerability closed in Linux
 The sinister ExPetr, which knocked several very respectable institutions, continues to offer surprises . Our analysts from the GReAT team discovered his relationship with the eraser, who attacked Ukrainian power plants a couple of years ago as part of the BlackEnergy campaign.
The sinister ExPetr, which knocked several very respectable institutions, continues to offer surprises . Our analysts from the GReAT team discovered his relationship with the eraser, who attacked Ukrainian power plants a couple of years ago as part of the BlackEnergy campaign.Of course, there is no obvious use of pieces of code in ExPetr, the authors tried not to burn. But programmer's handwriting is not so easy to disguise.
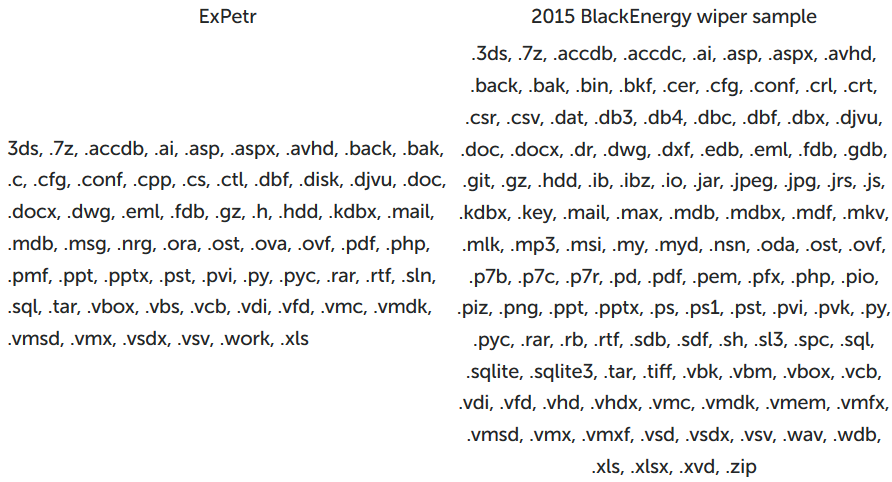
First, analysts compared lists of extensions of encrypted files. At first glance, it is not very similar - BlackEnergy worked with a much wider variety of files - but if you look closely, there is still a similarity. There are many types of extensions, and from them it is possible to collect an infinite number of different lists, and here there are obvious intersections in composition and formatting.
')
The second characteristic feature is the format for storing the list of extensions. Both here and there extensions are separated by a dot. In itself, this does not prove anything, but it gave rise to dig deeper.
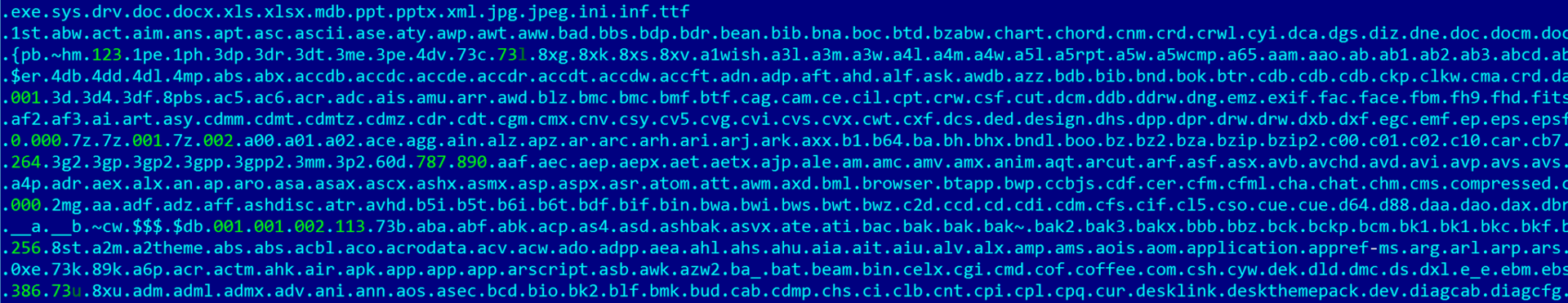
Some more similar code sections were found using automatic comparison. So, in the search code of files with extensions from the list in both samples, the use of the string comparison function wcscmp to check whether the file name is equal to the current directory symbol '.' Was found. Again, nothing out of the ordinary, but it went into a box of signs.
The researchers found several more lines present in both ExPetr and the sample from BlackEnergy:
- exe / r / f
- ComSpec
- InitiateSystemShutdown.
Nothing unusual at all, you say. True, but from these non-proving coincidences, GReAT made up the rule for YARA, and this is what became clear after its application to our huge collection of malicious samples. Each individual condition of this rule works on very many files, but the rule entirely catches only two of them - ExPetr and BlackEnergy. Not a proof, but a very convincing argument in favor of the kinship of these samples.
Most sites on the Internet do not support security technology.
News Research Browser vendors regularly report on the introduction of new technologies, each of which is supposed to block off oxygen to sneaky hackers and protect ordinary users. And things are still there: attacks via websites, phishing, theft of cookies still flourish, as if nothing is happening. And all they like, goose water.
And the reason, meanwhile, is obvious - many fashion technologies that appear in browsers almost every month require support on the side of sites. And traditionally, everything is bad - the admin will not wake up until his site is hacked and thousands of its visitors spread the Trojan-banker or something worse. Judging by the results of the Mozilla Foundation study, there are as many as 93.45% of such irresponsible admins.
They got this figure as follows: they took the top million sites from the Alexa rating, and checked the support of information security technologies, like CSP, CORS and HPKP. The results, to put it mildly, did not make happy - 9 out of 10 sites received the lowest rating (F), that is, by and large, the administration of popular sites is not interested in user safety.
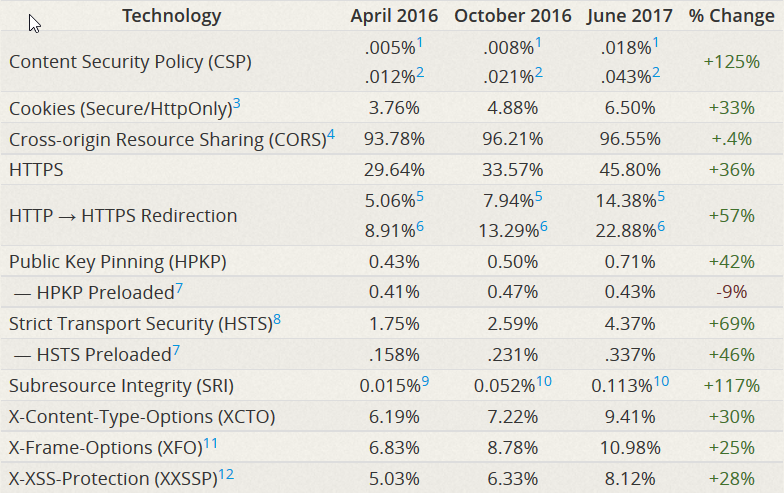
However, there is a barely noticeable positive trend: in comparison with last year’s survey, F-sites decreased by 2.8%. That is, some more than 34 years (while maintaining the same dynamics), and the web will become safe!
Linux closed RCE bug
News From Canonical they report that they have patched a vulnerability in Ubuntu that allowed them to crash the system or force it to execute code using a constructed DNS response. The problem lay in systemd-resolved, the system DNS resolver in Ubunt and several other distributions.
At least it's good that the DNS-record does not exploit this hole, you need to send a resolver TCP packet to the resolver, during the processing of which the daemon flattens the buffer to such a small size that the data from the DNS-answer falls outside its borders.
Although Canonical gave the bug a high degree of threat, the situation does not look very scary. To exploit this vulnerability, it is necessary to force the system to access a malicious DNS server, which is success in itself. But it is present in Ubuntu since June 2015 (in systemd, starting with version 223). And due to the fact that systemd also comes with Debian, Fedora and openSUSE distributions, the bug is worth looking for there. However, Fedora has already patched .

Antiquities
Family "Ieronim"
Resident non-dangerous viruses are recorded in .COM-files (except COMMAND.COM) when they are loaded into memory. Depending on their version, viruses are introduced either at the end or at the beginning of the file. About once an hour, text like “Mulier pulchra est janua diaboli, via iniquitatis, scorpionis percussio. St. Ieronim. In addition to this, contain the string "comcommand". Intercept int 8, 21h.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 32.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/332646/
All Articles