PHDays HackBattle: breaking one by one

In May, the HackBattle competition was held for the first time at the conference on practical information security Positive Hack Days VII. On the first day of PHDays, visitors could take part in qualifying competitions, and two participants who completed the most tasks in the shortest time reached the final of HackBattle, which took place on the second day of the conference on the main stage. In this article, we will describe how the competition took place, and we will also offer everyone to try their hand at the tasks that were used in the competition.
Selection
Since the final of the competition was to take place on the main stage under conditions of limited time, as well as under the close supervision of a professional public, we needed people who did not give up on the fact that thousands of eyes were fixed on them and would be able to solve the problem in adequate time.
To find such hackers, we decided to use the format of qualifying competitions based on CTF type tasks, but with a time limit of 25 minutes. For the selection of 9 tasks were prepared, ranked by level of complexity. At the same time, we tried to select such tasks, the scenarios of which are encountered in the course of real pentest.
')
Each guest of the conference had the opportunity to once participate in the qualifying competition, after registering. It was possible to participate only from workstations provided by the organizers. The first visitor who wished to take part in the competition appeared literally in the first minutes of the forum, and the total number of hackers who participated in the selection of HackBattle was 97 people!

The final
The state of affairs in the selection table changed throughout the first day of the conference, and only in the evening there were two participants entrenched there who reached the final. They became Vlad “vos” Roskov and Omar “Beched” Ganiev.
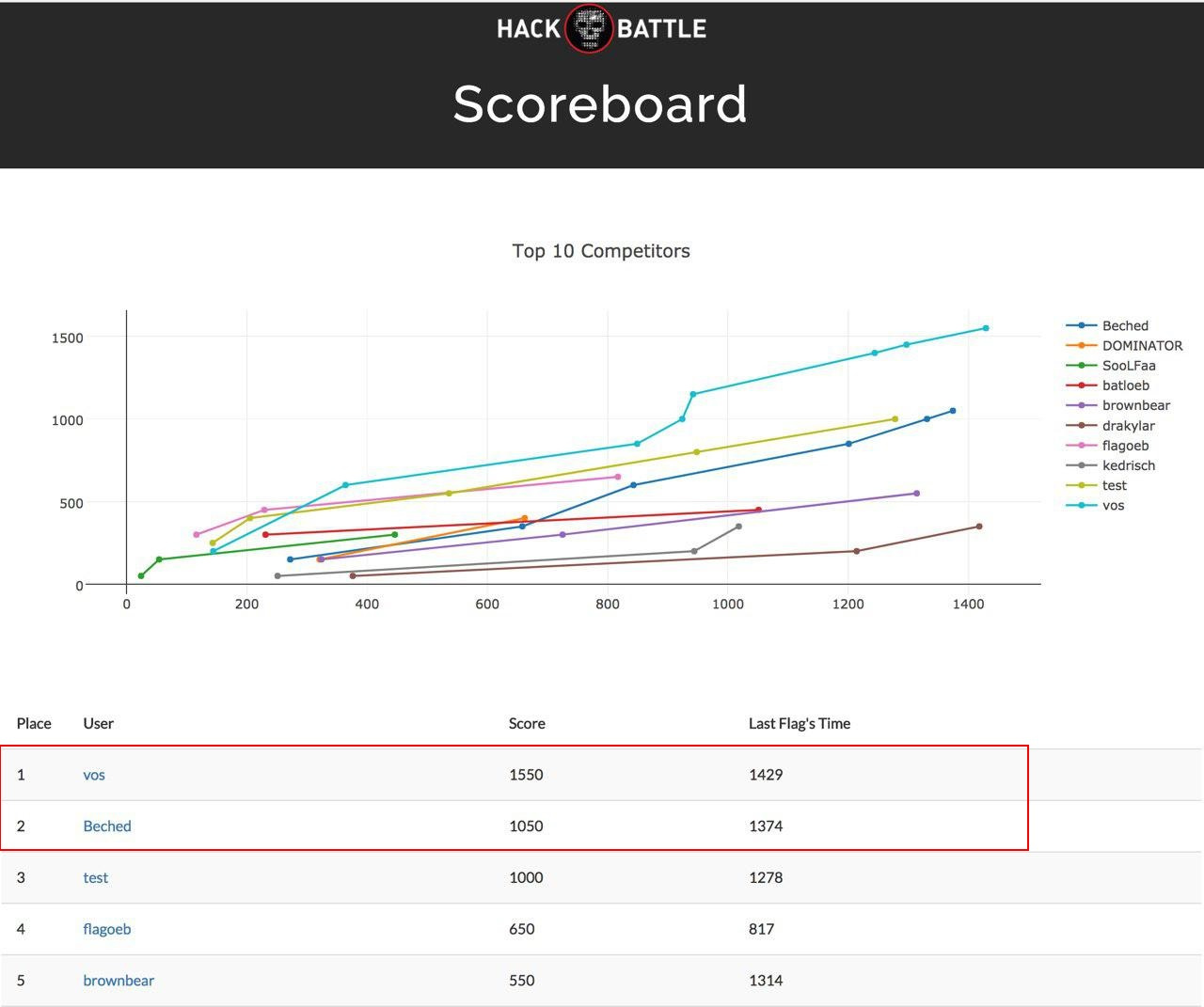
The final took place on the second day, on the main stage of PHDays. Everything that happens on the monitors of the two hackers finalists was broadcast on a big screen, with professional comments from information security experts:

The finalists were asked to attack the same infrastructure. According to legend, it was the security department of a fictional city:
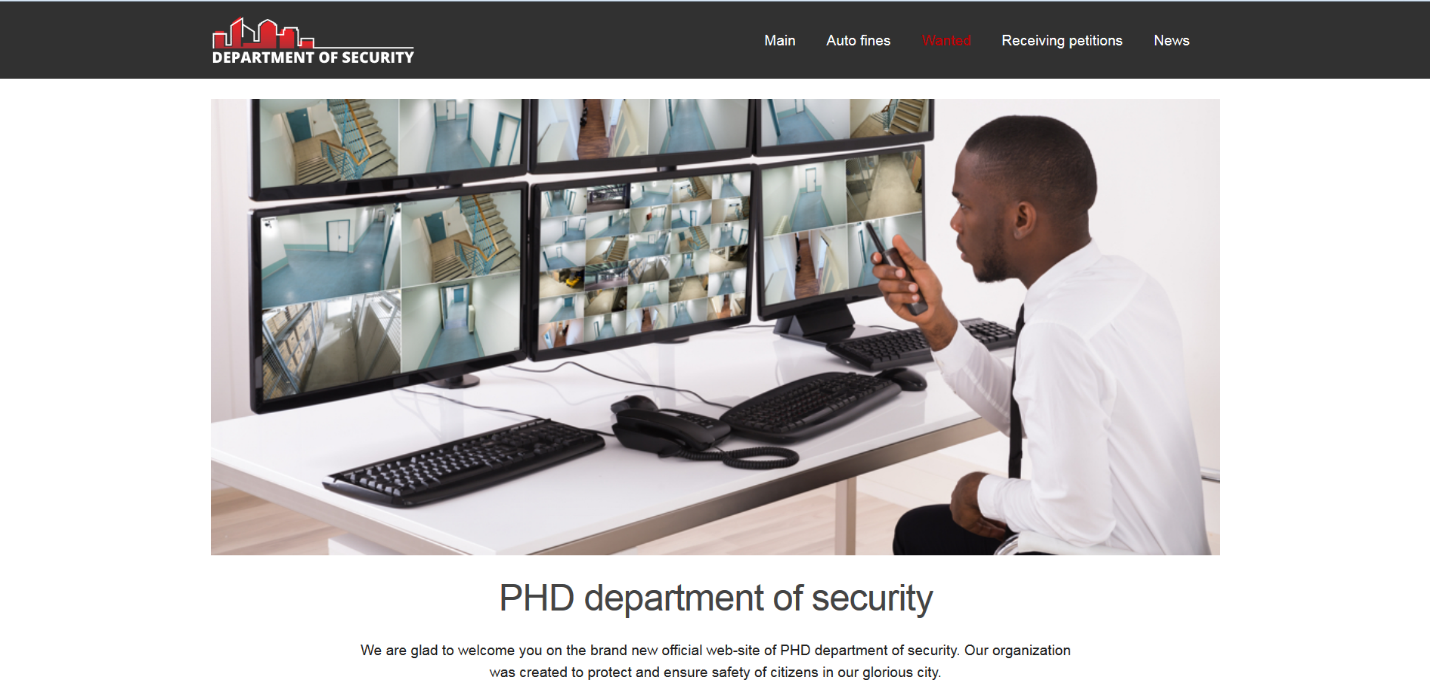
The task consisted of three stages: the first two had to attack the web application in order to first get into the application administration panel, and then be able to execute commands with the web server rights. At the third stage, it was necessary to elevate privileges to root and launch a bash script. According to the legend of the game, he activated the siren in the department building. Separately, it is worth noting that the passage of the task was not linear, each stage could be overcome in several ways, which our finalists showed.
The battle was hot, until the last moment it was unclear exactly who will come to the finish line first! The full version of the final can be viewed at www.phdays.com/broadcast/ , May 24, part 2 mix stream from 2:00:00. If you do not want to know the winner ahead of time, then do not read further until you look at the record.

The winner was Vlad “vos” Roskov ! After the contest, we took a small interview from the finalists to share their impressions of HackBattle.
Vlad “vos” Roskov :
“ I love the hack battles one on one, the guys came up with a cool format for the show with the final battle on the stage. Respect for diverse task. Bechedu is also a respectable, worthy rival :)
This time there was only one duel, in which the top 2 were selected according to the number of decisions for the first day - it would be cool next time to build a tournament grid and do all the battles one-on-one . ”
Omar “Beched” Ganiyev :
“ I have already had the opportunity to compete in a similar format in a more modest setting - at the RuCTF conference. In general, this is the most exciting format for viewers and a very interesting format for participants. The difficulty for the organizers is to hold a competition without flaws in the infrastructure, and most importantly, to make tasks such that they are really solved in a short time (10–30 minutes). The result is a dynamic competition for speed, which demonstrates the audience’s approaches to solving problems.
The authors of HackBattle just managed to maintain such a balance and make tasks that are solved in different ways and allow participants to choose their own path.
Another plus for the participants is that the competition takes very little time, so you can warm up and get distracted at the conference. I’m happy to take part again and recommend to think about scaling battles into tournament format - so that not only two people can fight in the final. A similar competition Rapid Fire was conducted by ForAllSecure . ”
Tasks for the contest: try it yourself
The tasks for the selection and the final can be downloaded in the OVA format:
http://static.ptsecurity.com/phdays/2017/hackbattle/creds.txt - access to virtual machines
static.ptsecurity.com/phdays/2017/hackbattle/1.ova
static.ptsecurity.com/phdays/2017/hackbattle/2.ova
static.ptsecurity.com/phdays/2017/hackbattle/3.ova
static.ptsecurity.com/phdays/2017/hackbattle/4.ova
static.ptsecurity.com/phdays/2017/hackbattle/5.ova
static.ptsecurity.com/phdays/2017/hackbattle/6.ova
static.ptsecurity.com/phdays/2017/hackbattle/7.ova
static.ptsecurity.com/phdays/2017/hackbattle/8.ova
static.ptsecurity.com/phdays/2017/hackbattle/9.ova
static.ptsecurity.com/phdays/2017/hackbattle/FINAL.ova
Tasks vary greatly in complexity. An analysis of one of them (No. 3 by reference), for the solution of which a modest 100 points were relied upon, can be found below. Of course, this spoiler should not be read to anyone who wants to try to solve this problem on their own.
Review task number 3
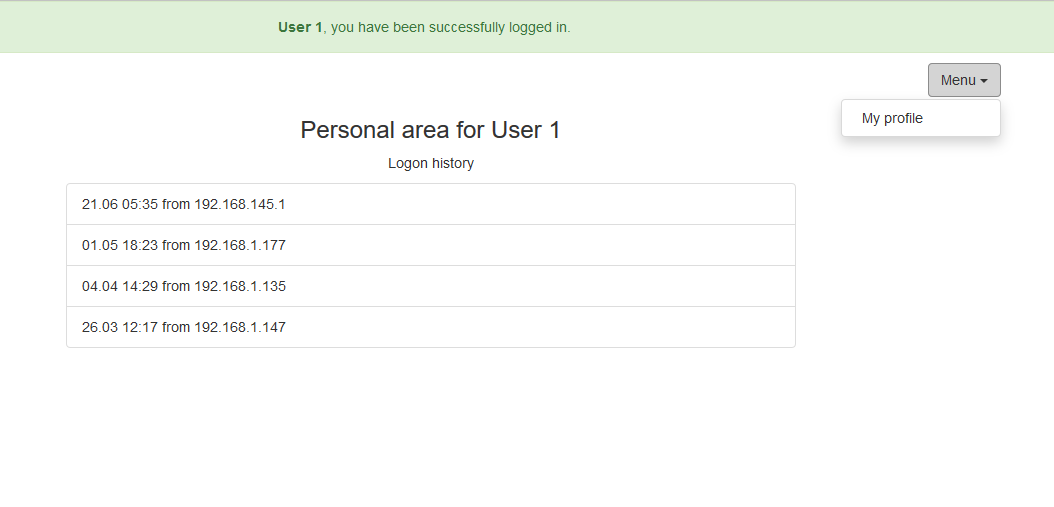
When clicking on the link, the participant saw a web application with a welcome message “ User 1 , you have been successfully logged in.”:
When you click on the link “My profile”, the User 1 profile page opens:
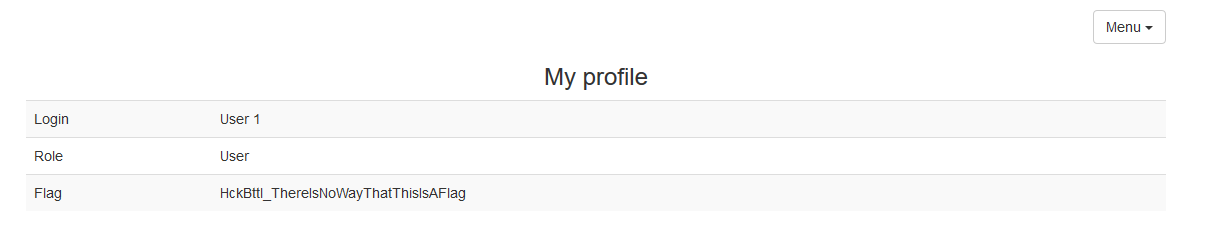
The message in the Flag line unequivocally said that the flag is not here.
The profile link was “/ profile / 1”, if you try to follow the link “/ profile / 2”, then the User 2 profile was displayed:
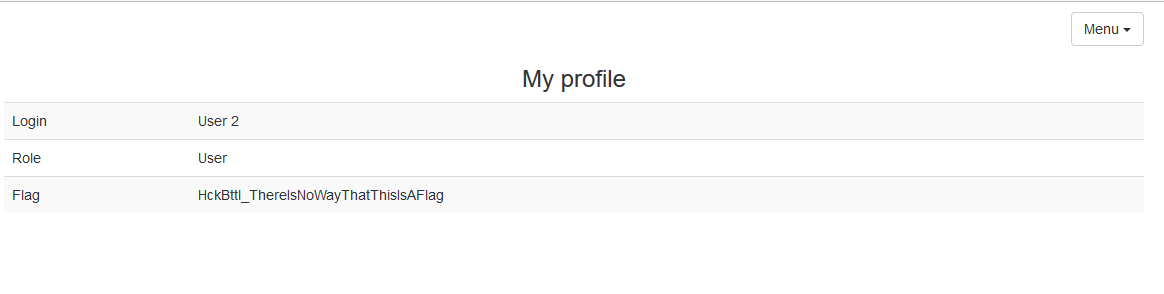
Unfortunately, there was no flag here either, but it is obvious that there is an IDOR vulnerability. Let's iterate over the first 100 id using Burp Intruder:
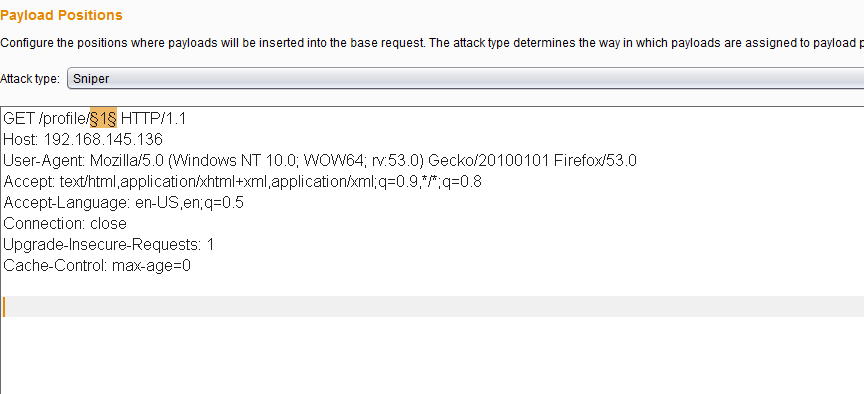
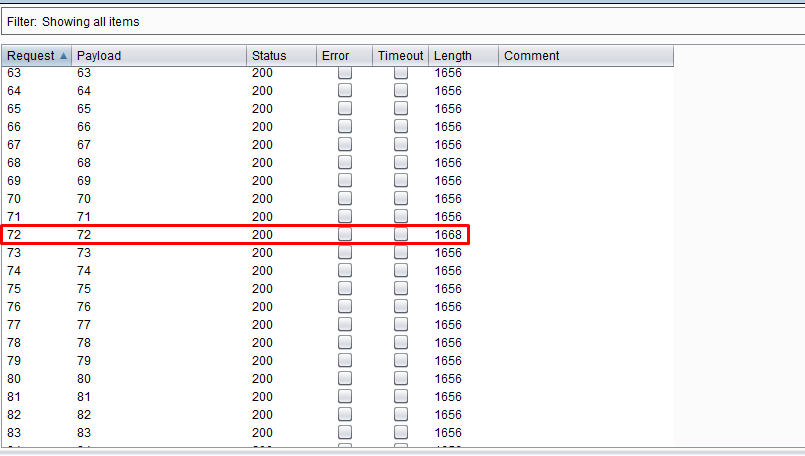
On id 72 we see an anomaly in the Length column, go:
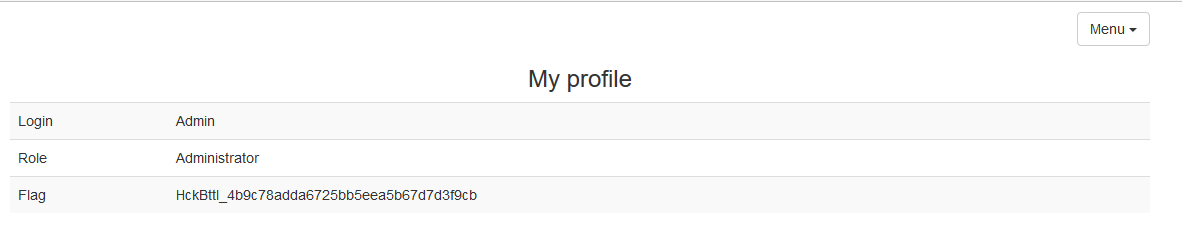
This is what you need! And the flag now looks quite realistic.
Authors: Alexander Morozov, Anatoly Ivanov, Anna Vekhteva, Positive Technologies
Source: https://habr.com/ru/post/332492/
All Articles