How to protect corporate storage from encryption viruses with snapshots
Encryption viruses have been shaking the IT market for years with the consequences of their clandestine work. Hiding behind the link in the email or in the JavaScript code on the page of the website, they silently install on the working computers or servers and begin to silently encrypt all the information. After the end of encryption, some simply delete the encryption key, others require a ransom, but not all users who pay it receive an encryption key. How can you deal with them? The most important means of struggle is to be prepared for the worst.
Trying to protect yourself from viruses and other hacker attacks only by means of antivirus and firewalls, it's like hanging locks on the door, put an alarm / video surveillance and count on the fact that there is no one who can bypass it. As practice shows, even the most complex locks, the most intelligent protection systems can be circumvented. You need to have a “Plan B” and be prepared for the worst. The only solution is to be able to quickly and securely recover data. Using the NetApp solutions as an example, consider these possibilities.
')
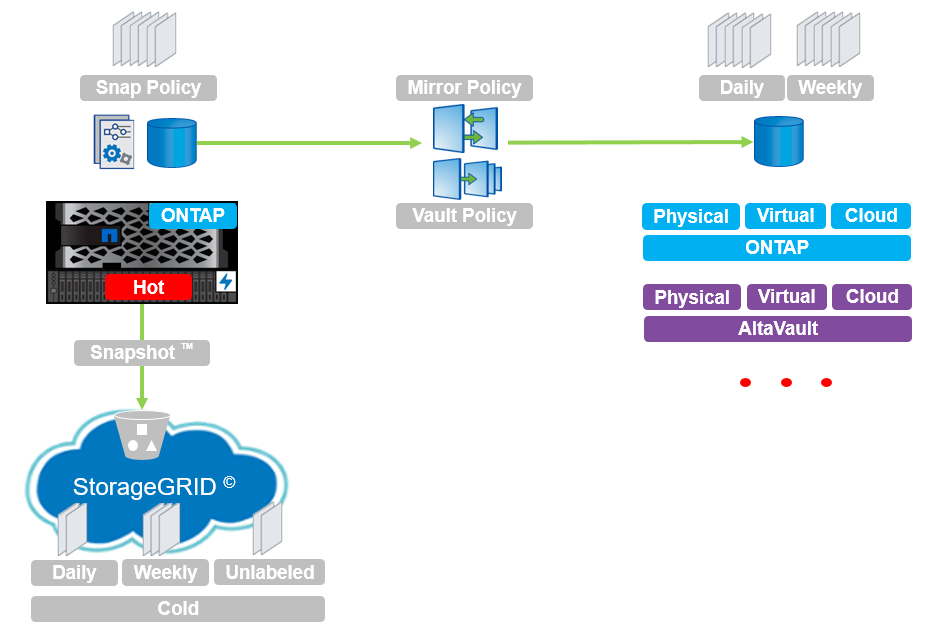
They not only have multiple integrations with a variety of backup software, antivirus systems, and other infrastructure systems, but also provide high availability for NAS (NFS, CIFS / SMB) and SAN (iSCSI, FC, FCoE). Unified storage allows for transparent data migration between the nodes of the cluster, which can consist of 24 nodes, and also allows you to use all the nodes at the same time to service the NAS and SAN to improve performance. Thus, you can completely abandon the vulnerable Windows Server vulnerabilities - not to buy licenses and not build clusters for high availability, because all the functionality is already available in NetApp ONTAP, including integration with AD, file and folder security settings, Access Based Enumeration, and all the usual MMC Management Console
Both in the largest organizations and in small firms, working files are placed on a shared file storage so that everyone can use them. The centralization of storage provides the convenience for several people to work together on the same files, but it also imposes the responsibility to protect such information. Naturally, in order to combat encryption viruses, it is necessary to perform regular backups using the 3-2-1 scheme. Backups are important to keep separate from the main system.
NetApp FAS / ONTAP storage systems have in their arsenal snapshots that do not affect performance and replication based on these snapshots, which allow you to integrate NetApp storage systems with NASA and SAN technologies with a wide range of backup systems :
Let's take a closer look at one of these backup systems, Veeam Backup & Replication, which has gained trust and respect due to the ease and simplicity of the management interface. But these are not all the advantages of this product, which not only knows how to manage snapshots and replicas between NetApp FAS, ONTAP Select, ONTAP Cloud and AltaVault. It also allows data storage systems to clone data on one of the sites for testing performance and recoverability from such backups. Cloning as well as snapshots on the NetApp FAS / ONTAP system is a very convenient technology that also does not affect performance and at the initial moment of taking a snapshot does not take up any storage space. In addition, creation takes less than a second, regardless of the size of the data being cloned.
But a full recovery, firstly, can be quite long, and secondly, backups can be performed not every 15 minutes, thus increasing the RPO. And here it becomes clear how important a part of backups are snapshots, which can be performed much more often than backups from NAS or SAN storage and, accordingly, restore such data much faster from snapshots, thus significantly reducing the RPO value. And here it becomes clear how important it is that such snapshots function like a clock, do not inhibit the operation of the entire repository, do not have architectural problems for deletion and consolidation. At the same time, snapshots are not a replacement for backup, but an important addition to a complete backup strategy. So the procedure for creating snapshots can be done often enough to capture the most recent changes to your information.
Snapshots are not a complete copy of the data, only the difference of new data at the block level, a kind of reverse incremental backup that more efficiently uses storage space, rather than a full backup. But still this space is used, the more changes, the more information gets into the snapshot. A customized schedule for auto-deleting old snapshots will allow more efficient use of storage resources and not eat up all the available space on expensive NAS storage. A backup, will store a much longer time copy of older versions of information.
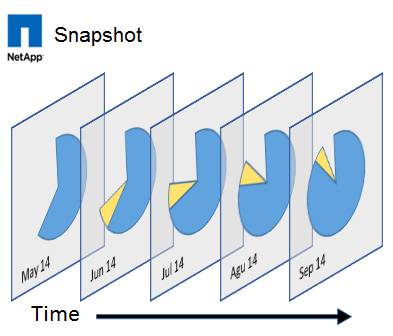
NetApp ONTAP snapshots are equally effective in both NAS and SAN environments, are equally architecturally designed, have the same interface, configuration, removal and recovery speed, which allows you to more quickly roll back in case of data corruption.
Separately, it is worth noting the technology FabricPool , which allows to transparently shift snapshots and cold data from SSD drives to slow disks in the object storage, which will make it possible to actively and often use such an important technology of snapshoting on expensive storage media.
There is a separate document on how to deal with encryption viruses using NetApp TR4572 systems .
Many have already come across various implementations of snapshots and already know in practice how snapshots should not work:
ONTAP snapshots for NetApp storage do not work this way . They were first implemented in the ONTAP operating system, as part of the WAFL file system in 1993, as we see, these technologies have been tested by time. By the way, the word Snapshot itself is a registered trademark of NetApp, and the snapshot technology is patented. To study the question of how WAFL snapshots work, you can download for free the test period a virtual machine with an ONTAP repository image, which can be requested from the Distributor or the Integrator.
mysupport.netapp.com/NOW/cgi-bin/software/?product=ONTAP+Select&platform=Deploy+Install
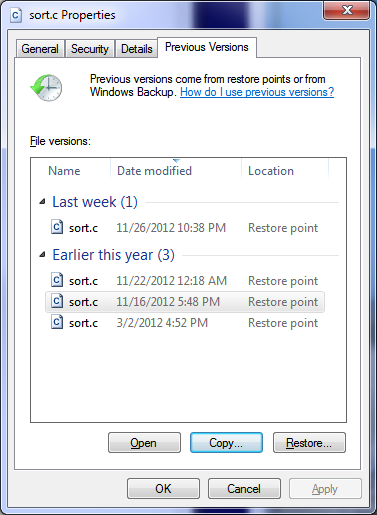
Integration of storage snapshots with operating systems will allow you to remove the routine from the storage administrator to recover individual files. So that users themselves can restore their files from snapshots directly from their Windows computer using standard OS tools.
Simply deleting old snapshots that are already in the repository and configured in a well-established backup strategy is a significant waste of resources. After all, snapshots can be used to replicate them on the second, third, etc. storage systems. Firstly, there are already snapshots, why not to use them, secondly, it is much more profitable to transfer the delta than the entire data set each time; in the third, snapshots work like reverse incremental backups. Those. do not require time for “gluing into full backup”, in the fourth, ONTAP snapshots are like reverse incremental backups, but they do not require gluing or consolidation either before recovery, during replication, or during recovery, as is the case with traditional incremental backup or reverse incremental backup. But there is no magic, snapshots when replicating data are still read out from the target system changes to be sent to the remote system, this generates additional read operations during the replica, but it is much better compared to a full backup, which every time re-reads everything data entirely.
The Write Once Read Man or WORM technology, also known by other commercial names, for example, NetApp SnapLock, built on the basis of snapshots, allows you to block data for a long time from changes, including from users of the storage system with elevated privileges. So you can store firmware, configuration from a variety of devices, such as switches, routers, and more. Files of this kind are rarely changed at all during the life of the device, and WORM-supported storage is a safe place to put important infrastructure settings files that are not exactly infected, they cannot be changed, but they can be read. This property can be used to load configurations and firmware for key components of your infrastructure.
And of course, the ability to check files on the storage side will not be superfluous either . NetApp FAS / ONTAP systems integrate with a wide list of anti-virus systems that will perform corporate data checking on NAS storage. The most well-known anti-virus scanning systems are supported:
As it was said earlier, snapshots store a block delta in themselves - the difference between their previous state and the current one, that is, relevant. And the more changes are made to the actual data, the more it takes snapshot. In addition, it is worth mentioning about the technology of compression and data deduplication, which allow you to compress the original data, saving storage space. So some data is not compressed. For example, a photo, video or audio data, and what data is not pressed yet? Correctly, encrypted files. So imagine you set up a snapshot schedule, you have deduplication and compression. Snapshots are removed, and older ones are deleted, data is compressed, space consumption is quite measured and stable. And suddenly the snapshots start to take up much, much more space than before, and deduplication and compression are no longer effective. These are indicators of silent and malicious work of the ciphering virus: your data, firstly, changes dramatically (snapshots grow in size compared to how they were before), secondly, dedup and compression stopped producing results (it means that incompressible information, for example, the originals of the files are replaced by encrypted versions). These two indirect indicators lead to irrational consumption of storage space, and you can notice this on the graph of space consumption in the monitoring interface of NetApp, which suddenly began to grow geometrically upwards.

Fpolicy and ONTAP directory-security API are mechanisms that allow you to analyze a file, and depending on the configured policies, allow or not allow, write it, or work with it for the SMB / CIFS protocol. File analysis can be performed on the basis of a file extension (Fpolicy built-in ONTAP functionality) or by content, then you need specialized software using these two mechanisms.
The free product Cleondis SnapGuard Light Edition (SGLE) is designed not only to detect on the CIFS / SMB ball, but also to recover from encryption viruses using snapshots on the NetApp ONTAP platform . SGLE is able to recognize patterns of malicious encryption viruses that begin to encrypt your files and stop clients who are infected from further harm and are fully compatible with existing anti-virus systems.
Prolion DataAnalyzer-light free product provides the ability to detect encryption viruses on the NetApp ONTAP platform with SMB / CIFS ball .
Varonis is a very powerful industrial solution that not only can track encryption, disconnect infected users from the NAS (CIFS / SMB), but also find and recover those files that were encrypted.
The WannaCry / Petya viruses exploit a vulnerability in the SMB1 protocol on Windows machines, this vulnerability is not found in NetApp ONTAP systems. But once on Windows, the virus can encrypt files located on the NAS storage, so it is recommended to configure snapshots on a schedule. NetApp recommends disabling SMB1 and upgrading to newer versions of SMB v2 or v3 protocols on client-side Windows workstation to avoid infection.
Newer versions of the virus can disable VSS shadowing on Windows hosts, but since the snapshot schedule on the NAS NetApp storage is configured, turned on and off on the storage itself, turned off VSS will not affect the operation of snapshots.
Ps. Also note the document describing ONTAP security settings to enhance security (Security Hardening Guide for NetApp ONTAP 9) .
In connection with the mass infection of data by viruses such as RansomWare, Megatrade, the official distributor of NetApp in Ukraine launches a campaign for its existing and future customers on:
In conclusion, it is worth noting that snapshots are not a replacement, but an important part of a backup strategy, which allows you to more quickly, more often back up data and restore it faster. WAFL snapshots are the basis for cloning, SnapLock and data replication to a backup storage system, do not slow down the system, do not require consolidation and bonding, and are an effective means of backing up data. Enterprise-class storage systems NetApp FAS / ONTAP have multiple technologies and integration that allow you to be prepared for the worst. Well, in the context of the latest events, the technologies discussed above also become very relevant for protecting your information from various malware threats.
Translation to English:
How to protect your corporate storage system against ransomware
I ask to send messages on errors in the text to the LAN . Comments, additions and questions on the article on the contrary, please in the comments.
Trying to protect yourself from viruses and other hacker attacks only by means of antivirus and firewalls, it's like hanging locks on the door, put an alarm / video surveillance and count on the fact that there is no one who can bypass it. As practice shows, even the most complex locks, the most intelligent protection systems can be circumvented. You need to have a “Plan B” and be prepared for the worst. The only solution is to be able to quickly and securely recover data. Using the NetApp solutions as an example, consider these possibilities.

')
NetApp FAS / ONTAP Storage Systems
They not only have multiple integrations with a variety of backup software, antivirus systems, and other infrastructure systems, but also provide high availability for NAS (NFS, CIFS / SMB) and SAN (iSCSI, FC, FCoE). Unified storage allows for transparent data migration between the nodes of the cluster, which can consist of 24 nodes, and also allows you to use all the nodes at the same time to service the NAS and SAN to improve performance. Thus, you can completely abandon the vulnerable Windows Server vulnerabilities - not to buy licenses and not build clusters for high availability, because all the functionality is already available in NetApp ONTAP, including integration with AD, file and folder security settings, Access Based Enumeration, and all the usual MMC Management Console
Backup
Both in the largest organizations and in small firms, working files are placed on a shared file storage so that everyone can use them. The centralization of storage provides the convenience for several people to work together on the same files, but it also imposes the responsibility to protect such information. Naturally, in order to combat encryption viruses, it is necessary to perform regular backups using the 3-2-1 scheme. Backups are important to keep separate from the main system.
NetApp FAS / ONTAP storage systems have in their arsenal snapshots that do not affect performance and replication based on these snapshots, which allow you to integrate NetApp storage systems with NASA and SAN technologies with a wide range of backup systems :
- Veeam Backup & Replication
- CommVault Simpana
- NetApp SnapManager / SnapCenter.
- NetApp SnapCreator (free framework)
- Veritas netbackup
- Veritas BackupExec
- Syncsort
- Acronis
- IBM Spectrum Protect (Tivoli)
- EMC Networker
- HP Data Protector
- Cleondris DM
- Catalog ECX / DPX
- Arcserve UDP
- Other
Let's take a closer look at one of these backup systems, Veeam Backup & Replication, which has gained trust and respect due to the ease and simplicity of the management interface. But these are not all the advantages of this product, which not only knows how to manage snapshots and replicas between NetApp FAS, ONTAP Select, ONTAP Cloud and AltaVault. It also allows data storage systems to clone data on one of the sites for testing performance and recoverability from such backups. Cloning as well as snapshots on the NetApp FAS / ONTAP system is a very convenient technology that also does not affect performance and at the initial moment of taking a snapshot does not take up any storage space. In addition, creation takes less than a second, regardless of the size of the data being cloned.
Snapshots for salvation
But a full recovery, firstly, can be quite long, and secondly, backups can be performed not every 15 minutes, thus increasing the RPO. And here it becomes clear how important a part of backups are snapshots, which can be performed much more often than backups from NAS or SAN storage and, accordingly, restore such data much faster from snapshots, thus significantly reducing the RPO value. And here it becomes clear how important it is that such snapshots function like a clock, do not inhibit the operation of the entire repository, do not have architectural problems for deletion and consolidation. At the same time, snapshots are not a replacement for backup, but an important addition to a complete backup strategy. So the procedure for creating snapshots can be done often enough to capture the most recent changes to your information.
Snapshots are not a complete copy of the data, only the difference of new data at the block level, a kind of reverse incremental backup that more efficiently uses storage space, rather than a full backup. But still this space is used, the more changes, the more information gets into the snapshot. A customized schedule for auto-deleting old snapshots will allow more efficient use of storage resources and not eat up all the available space on expensive NAS storage. A backup, will store a much longer time copy of older versions of information.

SAN Wednesday
NetApp ONTAP snapshots are equally effective in both NAS and SAN environments, are equally architecturally designed, have the same interface, configuration, removal and recovery speed, which allows you to more quickly roll back in case of data corruption.
Snapshots and NetApp FabricPool Technology
Separately, it is worth noting the technology FabricPool , which allows to transparently shift snapshots and cold data from SSD drives to slow disks in the object storage, which will make it possible to actively and often use such an important technology of snapshoting on expensive storage media.
There is a separate document on how to deal with encryption viruses using NetApp TR4572 systems .
How snapshots should not work
Many have already come across various implementations of snapshots and already know in practice how snapshots should not work:
- they should not increase the load on the disk subsystem simply from having a snapshot;
- they should not increase the load simply from a larger number of snapshots;
- they should not be slowly created and deleted and this process should not affect the performance of the disk subsystem;
- they should not be deleted so as to damage the master data;
- it shouldn’t be any difference to how much data, everything should work quickly, instantly and without the slightest possibility to damage information due to the deletion or consolidation of the snapshot.
ONTAP snapshots for NetApp storage do not work this way . They were first implemented in the ONTAP operating system, as part of the WAFL file system in 1993, as we see, these technologies have been tested by time. By the way, the word Snapshot itself is a registered trademark of NetApp, and the snapshot technology is patented. To study the question of how WAFL snapshots work, you can download for free the test period a virtual machine with an ONTAP repository image, which can be requested from the Distributor or the Integrator.
mysupport.netapp.com/NOW/cgi-bin/software/?product=ONTAP+Select&platform=Deploy+Install
Recovery Automation
Integration of storage snapshots with operating systems will allow you to remove the routine from the storage administrator to recover individual files. So that users themselves can restore their files from snapshots directly from their Windows computer using standard OS tools.

Snapshot Replication
Simply deleting old snapshots that are already in the repository and configured in a well-established backup strategy is a significant waste of resources. After all, snapshots can be used to replicate them on the second, third, etc. storage systems. Firstly, there are already snapshots, why not to use them, secondly, it is much more profitable to transfer the delta than the entire data set each time; in the third, snapshots work like reverse incremental backups. Those. do not require time for “gluing into full backup”, in the fourth, ONTAP snapshots are like reverse incremental backups, but they do not require gluing or consolidation either before recovery, during replication, or during recovery, as is the case with traditional incremental backup or reverse incremental backup. But there is no magic, snapshots when replicating data are still read out from the target system changes to be sent to the remote system, this generates additional read operations during the replica, but it is much better compared to a full backup, which every time re-reads everything data entirely.
Worm
The Write Once Read Man or WORM technology, also known by other commercial names, for example, NetApp SnapLock, built on the basis of snapshots, allows you to block data for a long time from changes, including from users of the storage system with elevated privileges. So you can store firmware, configuration from a variety of devices, such as switches, routers, and more. Files of this kind are rarely changed at all during the life of the device, and WORM-supported storage is a safe place to put important infrastructure settings files that are not exactly infected, they cannot be changed, but they can be read. This property can be used to load configurations and firmware for key components of your infrastructure.
NAS Antivirus Protection
And of course, the ability to check files on the storage side will not be superfluous either . NetApp FAS / ONTAP systems integrate with a wide list of anti-virus systems that will perform corporate data checking on NAS storage. The most well-known anti-virus scanning systems are supported:
- Symantec
- Trend micro
- Computer associates
- Mcafee
- Sophos
- Kaspersky
Snapshots as an indicator of infection RansomWare
As it was said earlier, snapshots store a block delta in themselves - the difference between their previous state and the current one, that is, relevant. And the more changes are made to the actual data, the more it takes snapshot. In addition, it is worth mentioning about the technology of compression and data deduplication, which allow you to compress the original data, saving storage space. So some data is not compressed. For example, a photo, video or audio data, and what data is not pressed yet? Correctly, encrypted files. So imagine you set up a snapshot schedule, you have deduplication and compression. Snapshots are removed, and older ones are deleted, data is compressed, space consumption is quite measured and stable. And suddenly the snapshots start to take up much, much more space than before, and deduplication and compression are no longer effective. These are indicators of silent and malicious work of the ciphering virus: your data, firstly, changes dramatically (snapshots grow in size compared to how they were before), secondly, dedup and compression stopped producing results (it means that incompressible information, for example, the originals of the files are replaced by encrypted versions). These two indirect indicators lead to irrational consumption of storage space, and you can notice this on the graph of space consumption in the monitoring interface of NetApp, which suddenly began to grow geometrically upwards.

File Screening Fpolicy
Fpolicy and ONTAP directory-security API are mechanisms that allow you to analyze a file, and depending on the configured policies, allow or not allow, write it, or work with it for the SMB / CIFS protocol. File analysis can be performed on the basis of a file extension (Fpolicy built-in ONTAP functionality) or by content, then you need specialized software using these two mechanisms.
Free Cleondis SnapGuard Light Edition
The free product Cleondis SnapGuard Light Edition (SGLE) is designed not only to detect on the CIFS / SMB ball, but also to recover from encryption viruses using snapshots on the NetApp ONTAP platform . SGLE is able to recognize patterns of malicious encryption viruses that begin to encrypt your files and stop clients who are infected from further harm and are fully compatible with existing anti-virus systems.
Free Prolion DataAnalyzer-light
Prolion DataAnalyzer-light free product provides the ability to detect encryption viruses on the NetApp ONTAP platform with SMB / CIFS ball .
Varonis
Varonis is a very powerful industrial solution that not only can track encryption, disconnect infected users from the NAS (CIFS / SMB), but also find and recover those files that were encrypted.
SMB1 and WannaCry / Petya
The WannaCry / Petya viruses exploit a vulnerability in the SMB1 protocol on Windows machines, this vulnerability is not found in NetApp ONTAP systems. But once on Windows, the virus can encrypt files located on the NAS storage, so it is recommended to configure snapshots on a schedule. NetApp recommends disabling SMB1 and upgrading to newer versions of SMB v2 or v3 protocols on client-side Windows workstation to avoid infection.
Newer versions of the virus can disable VSS shadowing on Windows hosts, but since the snapshot schedule on the NAS NetApp storage is configured, turned on and off on the storage itself, turned off VSS will not affect the operation of snapshots.
Turn off SMB1 and SMB2
Open Powershall as administrator and insert the following lines.
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB1 -Type DWORD -Value 0 -Force Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB2 -Type DWORD -Value 0 -Force netsh advfirewall firewall add rule dir=in action=block protocol=TCP localport=445 name="Block_TCP-445" netsh advfirewall firewall add rule dir=in action=block protocol=TCP localport=135 name="Block_TCP-135" netsh advfirewall firewall add rule dir=in action=block protocol=TCP localport=139 name="Block_TCP-139" Ps. Also note the document describing ONTAP security settings to enhance security (Security Hardening Guide for NetApp ONTAP 9) .
In connection with the mass infection of data by viruses such as RansomWare, Megatrade, the official distributor of NetApp in Ukraine launches a campaign for its existing and future customers on:
- configuring ONTAP snapshots for NAS, SnapRestore, Virtual Storage Console
- installing free RansomWare infection monitoring software for ONTAP (CIFS / SMB)
- setting up ONTAP integration with antivirus systems for CIFS / SMB
- learning how to use ONTAP snapshots with SAN access
Conclusion
In conclusion, it is worth noting that snapshots are not a replacement, but an important part of a backup strategy, which allows you to more quickly, more often back up data and restore it faster. WAFL snapshots are the basis for cloning, SnapLock and data replication to a backup storage system, do not slow down the system, do not require consolidation and bonding, and are an effective means of backing up data. Enterprise-class storage systems NetApp FAS / ONTAP have multiple technologies and integration that allow you to be prepared for the worst. Well, in the context of the latest events, the technologies discussed above also become very relevant for protecting your information from various malware threats.
Translation to English:
How to protect your corporate storage system against ransomware
I ask to send messages on errors in the text to the LAN . Comments, additions and questions on the article on the contrary, please in the comments.
Source: https://habr.com/ru/post/332098/
All Articles