Who is Mr. Hacker?

Colleagues and friends! I am pleased to announce the launch of a new, 11th penetration testing laboratory: Test Lab v. eleven!
The laboratory is a copy of the real corporate network of the company, which contains typical vulnerabilities and configuration errors, and anyone can take part. Currently, more than 17,000 people are registered in the laboratory!
The main focus in our laboratories is realistic and interconnected assignments. Attacking, getting access to this or that machine, can use it as a springboard for promotion within the network.
')
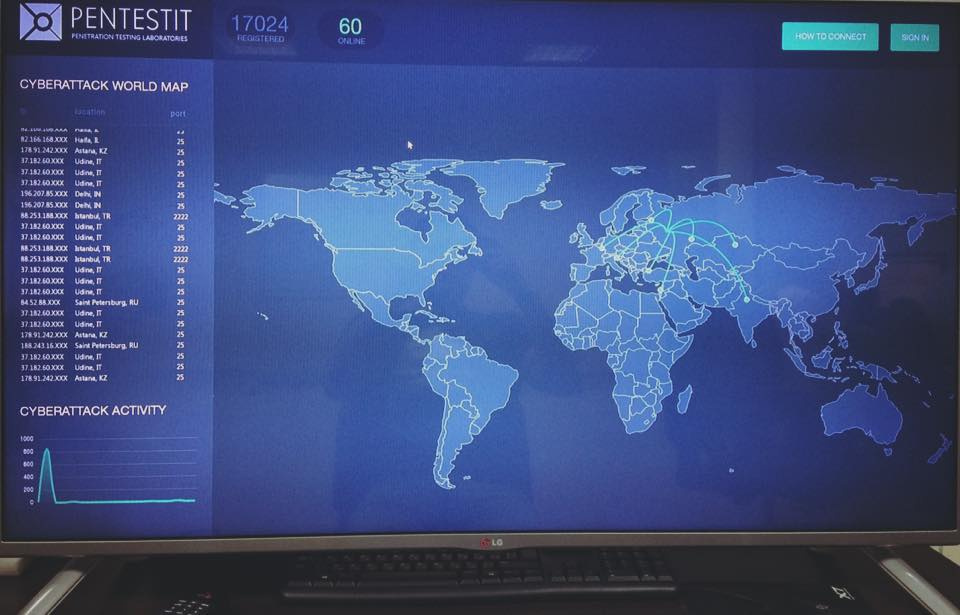
The new lab contains the following vulnerable resources and services:
- company website;
- Post service;
- CRM system;
- AD;
- AWP based on Win;
- secondary servers and services;
- AWP and services of technical personnel;
- access control systems;
- protective equipment.
Pledged attack vectors:
- OWASP TOP-10;
- MiTM;
- Public vulns;
- Security policy vulns;
- Auth bypass;
- Privilege escalation;
- circumvention of protective equipment;
- misconfiguration and more.
Attack scenario:
Laboratory participants need to explore the perimeter of a virtual company, detect vulnerabilities, and secure entry points to the corporate network. Using previously attacked machines as a bridgehead to move through the network, identifying new targets for attack, until you gain control over all the machines on the network!
Dare!
Source: https://habr.com/ru/post/332062/
All Articles