Security Week 26: ExPetr is not an extortionist, Intel PT allows you to bypass PatchGuard, in the Malware Protection Engine again RCE
 Mimicry is extremely common in the animal world. To make it easier to hide from predators, or vice versa, it is easier to sneak up to prey undetected, animals, reptiles, birds and insects acquire a color similar to the surrounding terrain. There is mimicry and under the objects, and, finally, under the animals of other species - more dangerous, or less tasty.
Mimicry is extremely common in the animal world. To make it easier to hide from predators, or vice versa, it is easier to sneak up to prey undetected, animals, reptiles, birds and insects acquire a color similar to the surrounding terrain. There is mimicry and under the objects, and, finally, under the animals of other species - more dangerous, or less tasty.In a similar way, the new extortioner ExPetr, which seems to be Petya, and not quite it, comes in. Spreading like a plague, it caused a rustling in 150 countries. One of the distribution vectors, but not the only one, is a sweet couple of EternalBlue and DoublePulsar, from which many have not bothered to patch after WannaCry.
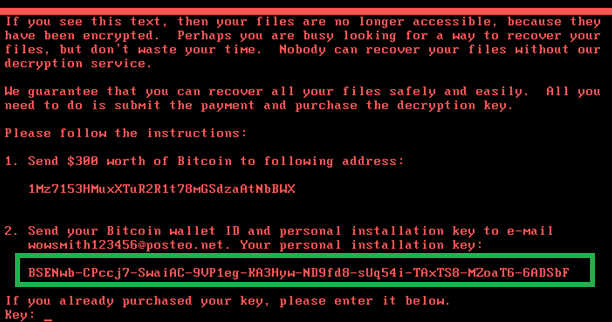
So, what I mean. On closer examination, it turned out that ExPetr is no extortionist, and the most natural data eraser . Restoring encrypted data is not provided and is impossible.
')
Good old Petya generated an identifier for each victim that should have been sent to the extortioners after paying the ransom. It was from him that the fraudsters calculated the key that was returned to the victim so that she could recover her files. And ExPetr shows the victim an identifier, that's just obviously useless - just a random set of numbers. Nobody was going to decipher anything initially.
Then a reasonable question arises, why was it necessary to fuss and demand disguise as a relatively peaceful Petya? Perhaps this is not a particularly tricky attempt to hide the fact that behind the new epidemic there are not simple guys from Rana who are trying to earn extra money on a freebie exploit, but someone who is much more malicious and does not need money. True, the ExPetr authors still earned some money.
A way to bypass Windows 10 kernel security has been developed.
News Research As you know, Windows 10 has acquired a number of good, suitable protective functions. One of them, PatchGuard, has worn out rootkits almost at the root. But the guys from CyberArk argue that the wait is not long, as they have already invented a way to run code without a code in the Windows 10 kernel space.
 The problem lies in the remarkable technology of Intel PT (Processor Trace), which allows security products to track the flow of commands executed by the processor to instantly determine a possible attack. The idea is great, but CyberArk could use PT to run its code in kernel space. They, of course, reported it all to Microsoft, but received an answer that all this is nonsense, since admin rights are needed to exploit the vulnerability. And if so, then it is no longer a vulnerability, because the admin is already allowed everything on the machine, and if the attacker has become such - light the carcasses, drain the water.
The problem lies in the remarkable technology of Intel PT (Processor Trace), which allows security products to track the flow of commands executed by the processor to instantly determine a possible attack. The idea is great, but CyberArk could use PT to run its code in kernel space. They, of course, reported it all to Microsoft, but received an answer that all this is nonsense, since admin rights are needed to exploit the vulnerability. And if so, then it is no longer a vulnerability, because the admin is already allowed everything on the machine, and if the attacker has become such - light the carcasses, drain the water.And yet this is not entirely true. Even a Trojan with admin rights can be detected and destroyed. But the CyberArk exploit allows you to execute the code completely unnoticed by any security systems. It is possible that something like some bad guys have been using for a long time, only to catch them will be very, very difficult.
Malware Protection Engine found RCE again
News Researchers from Google Project Zero, it seems, liked to dissect the protective engine from Microsoft. For the third time in recent months, a vulnerability has been found in it that allows arbitrary code to be run remotely.
The problem lies in the x86-emulator, in which MsMpEng runs untrusted PE files. It turned out that Microsoft developers left one of the emulator API calls to hang out, not accidentally, but “for a number of reasons”. Sly Tevis Ormandy from Project Zero was able to use it in an elaborately coarse file, which, if scanned in the emulator, causes memory corruption, which, according to Microsoft, allows "to run code, install programs, change data, create new accounts".
A typical attack scenario looks approximately the same as last time with the vulnerabilities of MsMpEng: the victim visits a site that pushes a tricky file to him, or receives this file by mail or via instant messenger. MsMpEng automatically scans it, and those who do not need to manage the system.
Let me remind you that the leaky MsMpEng is contained in Microsoft Endpoint Protection, Microsoft Forefront Endpoint Protection, Windows Defender and Microsoft Intune Endpoint Protection, but the vulnerability is present only in the 32-bit version of the engine.

Antiquities
"Astra-498, -510, -521"
Resident non-dangerous viruses. The SYS files of the current directory hit each time the DOS function is called FindFirst. They are written to the end of files for which only the address of the interrupt routine is changed (interrupt). Their TSR-copy is recorded in the vector table at addresses 0020: xxxx. Intercepted int21h.
They contain the text “(5)” and, depending on the version of the virus, one of the lines: “© AsTrA, 1990, JPN”, “(C) AsTrA, 1990”, “© AsTrA, JPN”. The phrases “I like cold flavor!”, “I like fragrant smell of flower!” Or “I like a flower's smell!” Are displayed.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 26.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/332050/
All Articles