Third Coming GOST 28147-89 or Russian Roulette
Until the mid-60s of the last century, in the era of arithmometers and slide rules, cryptographic systems were developed by engineers. Then the role of mathematicians was reduced to cryptanalysis and the introduction of hidden backdoors into algorithms.
With the advent of computers, mathematicians fully occupied the topic of cryptography, a digital representation of their patrimony data.
But progress does not stand still, quantum calculators and quantum data transfer appeared, and there the data are not represented as numbers, but as quantum states, this means the arrival of physicists in the topic of information processing.
')
While real quantum computations are in the region of the “transcendental distance”, but this does not mean that they are preparing for them early, it is quite possible that it is already too late. But better late than never.
In the meantime, mathematicians are poorly versed in the intricacies of programming, they invent something, and then the programmer must implement it in program code, which is not always possible to do effectively.
An example of this approach is the Grasshopper symmetric encryption algorithm; it is impossible to implement it effectively in the x86-64 software codes.
Let's do the opposite and see what happens ...
The programmer, who knows how the processor works, will develop the algorithm most effectively implemented on modern processors, and the physicist will tell you how to make it resistant to quantum cryptanalysis methods.
Cryptographers, as in the good old days, let them do their main work - the cryptanalysis of the resulting solution.
We will act cautiously, according to the principle of "The best is the enemy of the good," we take as a basis the "good" - GOST 28147-89. Then, following the medical principle “Do no harm”, we will strengthen it with the methods of multi-threaded calculations.
What it means to "strengthen" was stated in the article "Multi-threaded cryptographic algorithms ," which was specifically done:
- Increased the key size to 256 bytes.
- Increased data block size to 256 bytes.
- Improved statistical parameters of ciphertext.
Increasing the size of the key and data block is reduced to an increase in the calculated and algorithmic complexity of cryptanalysis. The requirement of maximum compliance of the ciphertext with the random sequence parameters was previously secondary, but at present it is already unacceptable.
Statistical characteristics of ciphertext in the post-quantum era become the main parameters determining cryptographic resistance.
Any violations of chance are hidden patterns that cryptographers can reduce to linear functions. And linear functions of any complexity are opened by quantum methods. Therefore, the statistics were focused on the development of a multi-threaded encryption algorithm based on GOST 28147-89.
The following has been done:
- The nonlinear tetrad substitution operation is replaced by a nonlinear permutation byte operation in the data block. A total of 16 fixed permutations are used.
- A nonlinear operation of inverting groups of bits is introduced in the linear cyclic shift transform.
- The Feistel network is modified into a ring network of its own production with preservation of the basic transformations GOST 28147-89. This is done to eliminate the reversibility of the transformation.
- Entering keys is made in the form of a reversible cryptographic transformation of permutation of bits.
Converting a bit permutation splits a 256-byte block into pieces of arbitrary length (according to the key information) and swaps them also depending on the key information. The keys in this transformation do not affect the contents of the data block (they do not change the number of zeros and units), they only mix the data block with an “external” influence.
How to analyze this conversion is not clear. There is no mathematical apparatus for analyzing arbitrary permutations in binary blocks performed on arbitrary fragments of this block ...
The modified Feistel network operates in the mode of irreversible gamming. This ensures that even knowing the keys and a certain sequence of gamma blocks it is impossible to calculate the values of gamma blocks outside of this known sequence of blocks.
To calculate gamma block values outside of a known sequence, it is required to perform a calculation from the starting point of gamming.
Practical implementation
While all this was a "fairy tale" and good wishes, it is time to turn them into a "true story", and this is how it looks:
This is a typical result of NIST tests of new crypto-transformation based on GOST 28147-89. The results of tests on any random keys and initial fillings always fit into the statistical parameters of a random sequence.
To reduce testing time, a simplified method was used. First, an experiment was conducted on a hundred blocks one million bits long in a gamut of 24 megabytes long (the first half of the gamut is used).
In the case of an unsuccessful experiment (falling out of the range of permissible proportions), the same gamma, already in full, was tested on blocks of two million bits in length. For such experiments, all test launches were successful (in a series of 100 experiments).
It is clear that tests with a block of two million bits in length should also sometimes lead to falling out of the range of proportions, but due to limitations on the number of experiments, there were no such cases.
These statistical parameters of the gamut are much better than the gamma produced by classical GOST, it often contains keys that the NIST tests do not pass in principle. The AES cipher in similar experiments is not much different from the traditional GOST.
The statistical parameters obtained in experiments on the norms of the 8-byte block cipher for a block cipher with a block size of 256 bytes are fantastic.
This is the same as, for example, throwing a coin 12 times and receiving an equal loss of "eagle" and "nutlets", to demand that the cube, also thrown 12 times, fall on each face twice a time ...
This is theoretically possible only with very high differential entropy between adjacent blocks and characterizes the level of complexity of the block cipher.
And the most interesting, these parameters are obtained with one round of conversion. There are no other block ciphers satisfying the requirements of randomness when using just one round.
The maximum cryptographic power of this cipher is already achieved in 16 rounds, but for the current level of cryptanalysis it is clearly redundant.
Now about the speed

This is a screenshot of the implementation of multi-threaded crypto-transformation based on GOST 28147-89 in the FastSecurityBoxes program, the testing was carried out according to the procedure described in the article “The Second Coming of GOST”.
As can be seen in the screenshot, the copy speed has reached the limit for test SSDs and is 453 MBytes / sec. when the processor is only 6 percent.
Theoretically, in tests of pure cryptography, the encryption speed for the gamming mode is 12 GBytes / sec. for one physical core of the processor (Skylake models and above) operating at a frequency of 3 GHz and above.
The encryption speed is no longer determined by the frequency of the processor, but by the bandwidth of the RAM of the computing system.
Russian Roulette, 2017 and its future application
Recently, with the help of the FSB, we began to receive ciphers with sonorous names, such as “Magma”, “Grasshopper”, and we will continue this tradition.
We will call this block cipher "Russian Roulette" .
Why "Russian", I hope everyone understands. A "roulette", because the cipher is built on the rotations (ring shifts) of binary sequences. Such shifts there are only explicitly 192 pieces per round.
By the way, the Russian officers who played Russian Roulette were crazy, but far from foolish. They thoroughly cleaned their revolvers, and knew physics well, and therefore kept the revolver while rotating the drum horizontally ...
A drum with one / five of the six bullets becomes unbalanced, and always strive to stand up empty chamber in front of the barrel.
So it was just an accident that the drum was jamming from different specks / hairs, getting to the empty chamber was “pseudo-random” and had a strict, predictable result.
Previously, when introducing a parallel implementation method to GOST 28147-89, I had to fully describe it, since it was officially certified by the FSB.
Now the situation is different, no official status is expected. Therefore, there will be no detailed description of the “Russian Roulette” algorithm, this is a kind of copyright protection. If it becomes interesting to become professionals, let them turn to their colleagues, - reverse programmers. That's who will have to break his head ...
In short, the Russian Roulette algorithm will be proprietary and this is coming soon: Russian Roulette, 2017 .
The encryption algorithm, closed from research, is of course nonsense, since there is no confidence in the encryption reliability.
But Russian Roulette is not an encryption system, we do not need a float with a regulator. Let me be the first to throw a stone at someone who says that this is a cipher, this is not an encryption system, the knight's move is made with a slight movement of the hand, and the algorithm is turned into a high-speed system of hashing and error correction, because first of all you need to take care of data integrity ...
The self-made Feistel cyclic network ideally meets the requirements of the “turbo code” for correcting errors, I did not do it on purpose, “he came” ...
Standard feedback gamma is converted to a hash function, if the keys are associated with previously processed data ...
Well, the fact that as a result, the data will also be reliably protected from viewing and modification - so sorry, a side effect of the system of hashing and error correction.
While the cryptographic “engine” of this future system is presented, it can be evaluated on test scales in terms of statistics and cryptographic resistance.
In the future, what Krylov failed to do was to be done. With the help of Russian roulette, we will bind the three members of his fable into the “cart” of responsible archiving, the “swan” of privacy, the “cancer” of authenticity and the “pike” of reliability. In this case, make them pull the "cart" at a breakneck pace ...
Difficult task, but solvable.
Practical implementation of crypto functions
The Russian Roulette algorithm is built into the demo version of the FastSecurityBoxes program in a partially cropped form. So far, for testing, only the basic transform operating in the gamming mode has been implemented. One round is used, this is enough for reliable passing of the NIST tests and cryptographic strength at the level of 2256 * 8 (the brute force direct attack option).
Keys are recalculated after issuing 64 kilobytes of gamma.
The algorithm itself is implemented on AVX commands using YMM registers, so this algorithm can effectively work only on the latest Intel processors (Skylake and higher).
On AMD processors, even the newest ones, the Russian Roulette algorithm will work slowly, since operations using YMM registers are implemented in them by firmware and not by hardware.
So that in the future, the FastSecurityBoxes program was required for practical work, it has a “payload” as a function of creating backup copies of logical disks (of course, recovery of disks is also there).
The choice of the applied task is determined on the one hand by the relevance of the topic, and on the other hand by the clarity of the result. Creating backup copies of the disks was naturally “sharpened” for high-speed SSD drives, which already today on the NVMe interface can work at a speed of 2-3 Gigabytes per second. At such speeds, nobody has yet been able to encrypt data, but now this is already a reality.
In addition to the new, yet exotic multi-threading algorithm, FastSecurityBoxes implements encryption according to the classical GOST 28147-89 in 8 parallel threads (for old processors) and 16 parallel threads (for skyleyka and above). These parallel encryption methods are certified by the FSB.
Encryption in 8 and 16 streams is included in the program for a substantive comparison of the results so that the difference could be felt ...
Apparently I confused readers with the terms "multi-threaded" and "parallel", so I will explain.
The parallel implementation method GOST 28147-89 is a certified FSB method. Parallelism involves the implementation of standard cryptographic procedures simultaneously on 4-8-16 independent physical devices. In this case, encryption keys, replacement blocks are the same everywhere, but the input and output data are different. Acceleration of work is achieved due to the simultaneous operation of several independent physical devices.
The term “independent physical device” as applied to a processor is a conventional concept, in reality, the processor has a set of registers on which the same transformations are performed simultaneously (with one processor command). But for simplicity of understanding, we will consider them independent physical devices operating strictly parallel and synchronous.
The multithreaded method implemented in the “Russian Roulette” algorithm differs significantly from the parallel one, here are its main differences:
1. There is a single block round converter.
2. The block length (so far) is 256 bytes and can be scaled.
3. Block fragments (two bytes each) are processed in independent streams.
4. Combining fragments produced in an additional transformation.
The multithreaded method allows you to increase the size of key data and the size of the input data block. Moreover, a change in any of the 2048 bits of the input block leads to a guaranteed change in all 2048 output bits after ten rounds of conversion.
Now the cipher contains 128 threads, when the processor with the AVX-512 command set appears, it will be possible to increase the number of threads to 512 (the data block will be 1 KB in size) and increase the speed twice.
In the meantime, the bottom line ..
The speed is 12 Gbytes per second for a processor with a frequency of 3 GHz, there is nothing to compare. The speed of the implementation of the algorithm “Russian Roulette” in the gamming mode “incomparable”. It is the fastest known pseudo-random sequence generator that meets the requirements of NIST tests.
The mathematical complexity of the cryptanalysis of the basic transformation “Russian Roulette” is determined by the dimension of the key, in our case it is equal to 2256 * 8.
The algorithmic complexity of cryptanalysis taking into account the known hacking methods for the basic Russian Roulette transformation is at least not less than the parent transformation of GOST 28147-89.
I will not overload the article with information about this new algorithm, while let the interested parties check what was said in the test program.
Download FastSecurityBoxes program here .
For testing, it provides the function of issuing a "clean" gamma. In this mode, test pseudorandom files are created for transformations in accordance with GOST 28147-89 and Russian Roulette.
PS
The FastSecurityBoxes program (Forced Secretive Images if in Russian) will soon turn into a responsible archiving program suitable for mass use, and then, I hope, into a full-featured commercial product. Accordingly, it is interesting to compare it with the commercial market backup luminaries in terms of copy speed and processor load.
The speed parameters of FastSecurityBoxes have already been cited in the article “The Second Coming of GOST”, let's see as an example what Acronis can do in the same modes of operation, on the same hardware platform.
Here's how it creates a sector dump without encryption and compression:
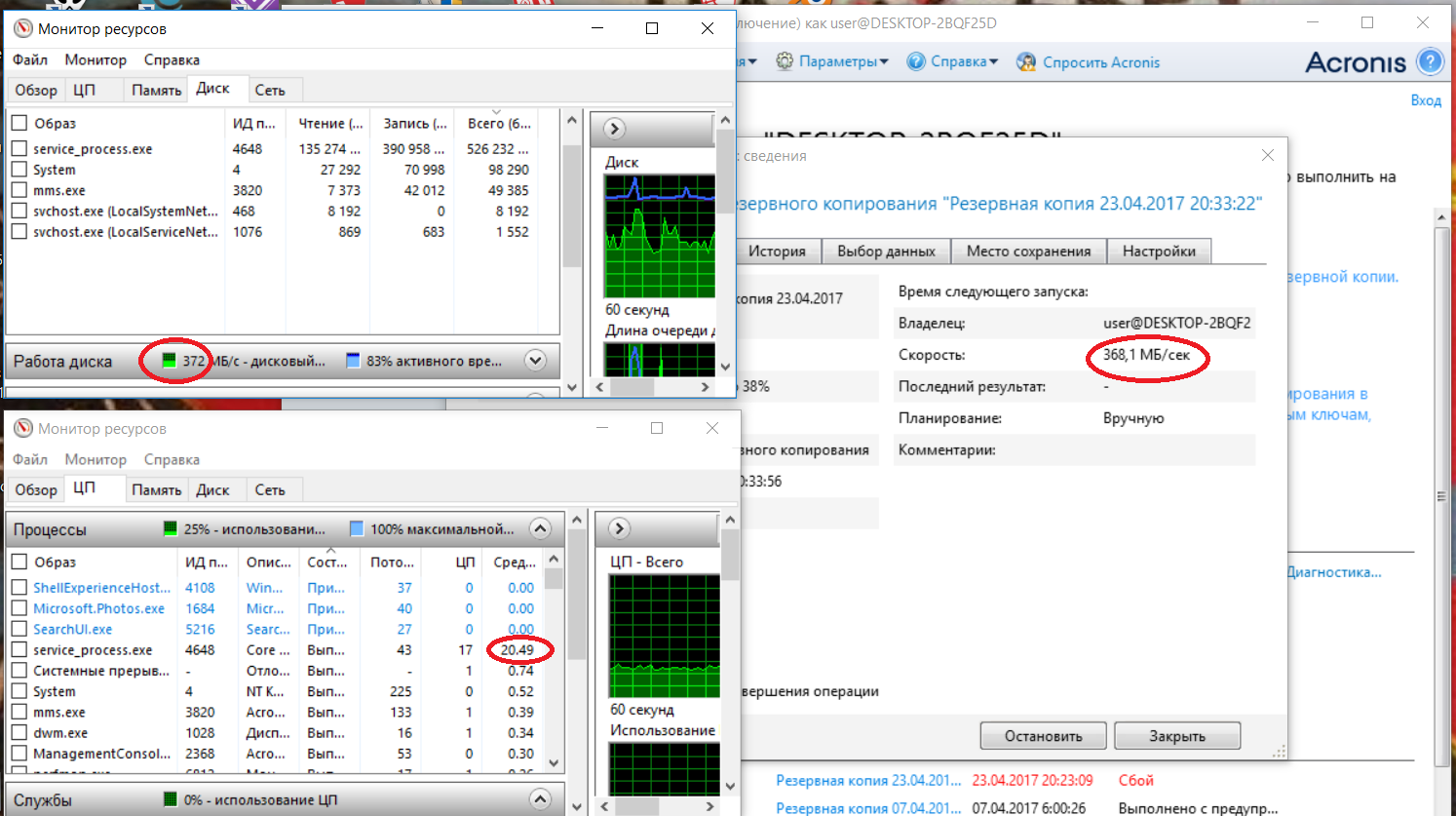
The program performs sector-by-sector copying at a speed of 368 MB / s ... Apparently, synchronous single-threaded I / O with cycles of waiting for the end of an I / O operation is used. Otherwise, do not explain too much CPU usage on I / O operations, which is 20%. Clearly outdated solution from the past millennium.
On the same hardware configuration, the FastSecurityBoxes test program provided a dumping speed of 450 MB / s. with a processor load of 6 percent.
Here is what Acronis issues on sector copying (without compression) with dump encryption according to GOST 28147-89:
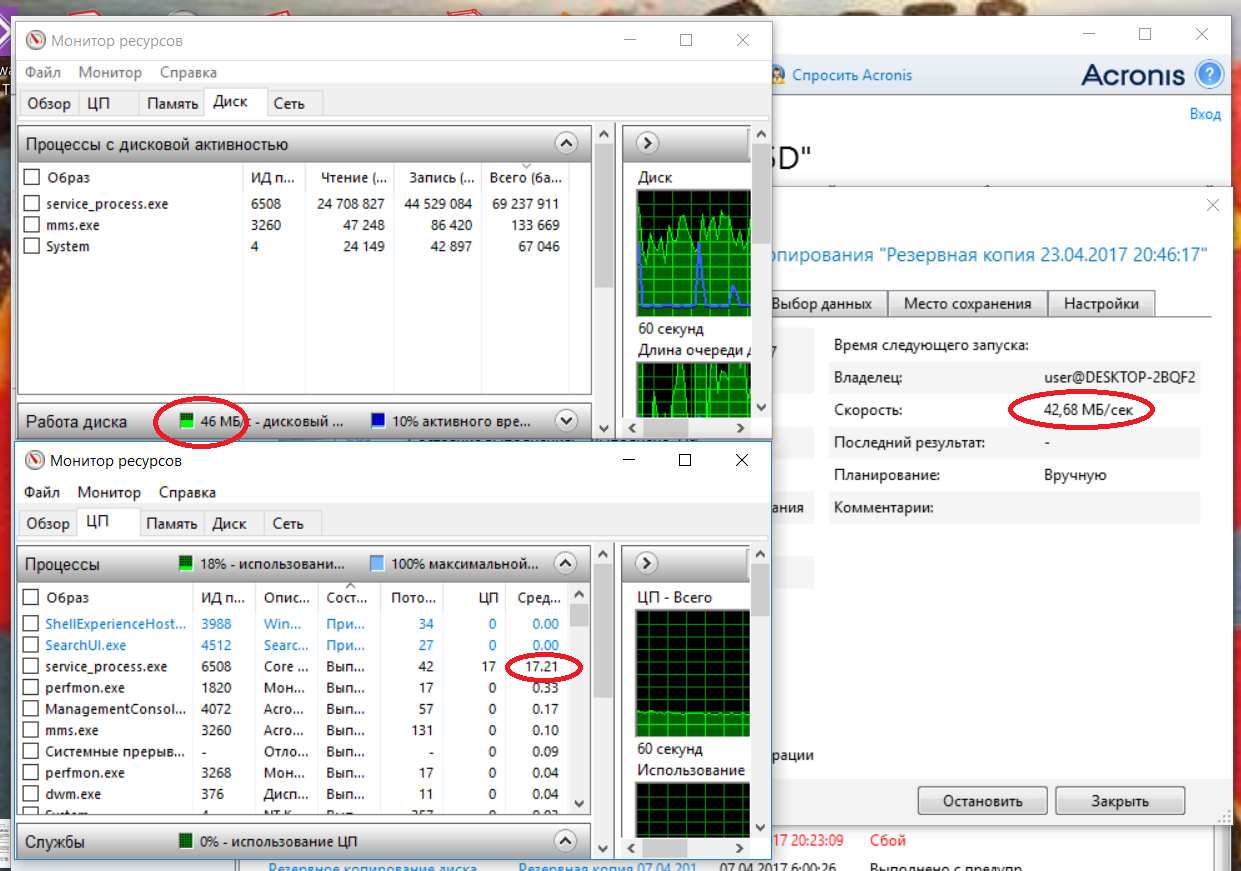
The speed dropped almost ten times, to 42 MB / s. using 17 percent of the processor's computing resources, FastSecurityBoxes provided 330 MB / sec in this mode, while using 10 percent of the computing resources, I think comments are superfluous ...
And the conclusion is obvious, Acronis uses an outdated classical implementation of GOST 28147-89 on the RON registers of the processor, therefore, such a low speed.
This is what Acronis does with encryption dump using the most “lightweight” AES-128 algorithm, again without compression. This algorithm for cryptographic resistance is worse than GOST 28147-89, but its implementation is the fastest due to the reduced number of rounds.
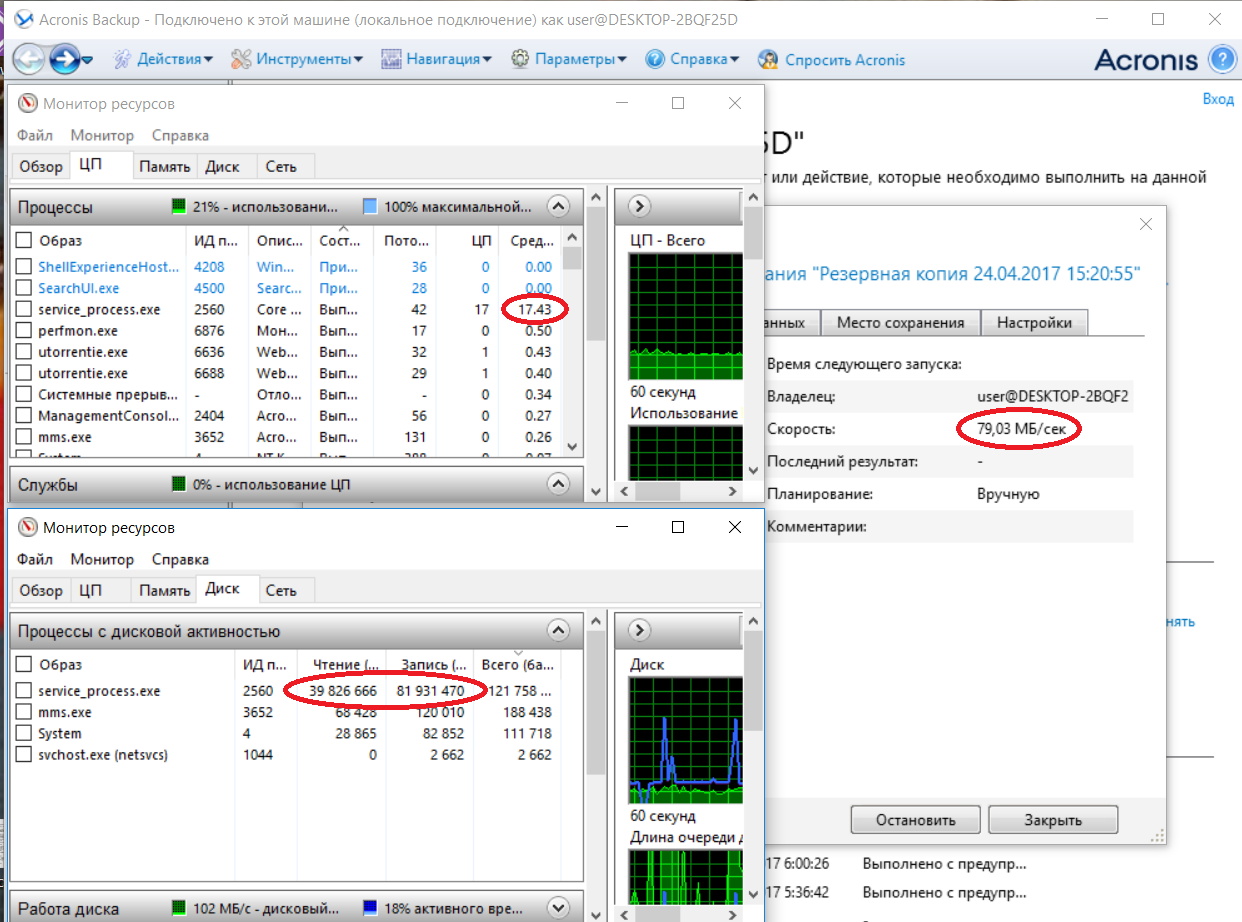
The speed has increased up to 80 MB / s, but still it is catastrophically low, BitLocker provided in this mode a speed of about 360 MB / s. Obviously, outdated crypto-library without the support of Intel hardware crypto accelerator is used.
How does all this look pale against the backdrop of modern technology ...
With the advent of computers, mathematicians fully occupied the topic of cryptography, a digital representation of their patrimony data.
But progress does not stand still, quantum calculators and quantum data transfer appeared, and there the data are not represented as numbers, but as quantum states, this means the arrival of physicists in the topic of information processing.
')
While real quantum computations are in the region of the “transcendental distance”, but this does not mean that they are preparing for them early, it is quite possible that it is already too late. But better late than never.
In the meantime, mathematicians are poorly versed in the intricacies of programming, they invent something, and then the programmer must implement it in program code, which is not always possible to do effectively.
An example of this approach is the Grasshopper symmetric encryption algorithm; it is impossible to implement it effectively in the x86-64 software codes.
Let's do the opposite and see what happens ...
The programmer, who knows how the processor works, will develop the algorithm most effectively implemented on modern processors, and the physicist will tell you how to make it resistant to quantum cryptanalysis methods.
Cryptographers, as in the good old days, let them do their main work - the cryptanalysis of the resulting solution.
We will act cautiously, according to the principle of "The best is the enemy of the good," we take as a basis the "good" - GOST 28147-89. Then, following the medical principle “Do no harm”, we will strengthen it with the methods of multi-threaded calculations.
What it means to "strengthen" was stated in the article "Multi-threaded cryptographic algorithms ," which was specifically done:
- Increased the key size to 256 bytes.
- Increased data block size to 256 bytes.
- Improved statistical parameters of ciphertext.
Increasing the size of the key and data block is reduced to an increase in the calculated and algorithmic complexity of cryptanalysis. The requirement of maximum compliance of the ciphertext with the random sequence parameters was previously secondary, but at present it is already unacceptable.
Statistical characteristics of ciphertext in the post-quantum era become the main parameters determining cryptographic resistance.
Any violations of chance are hidden patterns that cryptographers can reduce to linear functions. And linear functions of any complexity are opened by quantum methods. Therefore, the statistics were focused on the development of a multi-threaded encryption algorithm based on GOST 28147-89.
The following has been done:
- The nonlinear tetrad substitution operation is replaced by a nonlinear permutation byte operation in the data block. A total of 16 fixed permutations are used.
- A nonlinear operation of inverting groups of bits is introduced in the linear cyclic shift transform.
- The Feistel network is modified into a ring network of its own production with preservation of the basic transformations GOST 28147-89. This is done to eliminate the reversibility of the transformation.
- Entering keys is made in the form of a reversible cryptographic transformation of permutation of bits.
Converting a bit permutation splits a 256-byte block into pieces of arbitrary length (according to the key information) and swaps them also depending on the key information. The keys in this transformation do not affect the contents of the data block (they do not change the number of zeros and units), they only mix the data block with an “external” influence.
How to analyze this conversion is not clear. There is no mathematical apparatus for analyzing arbitrary permutations in binary blocks performed on arbitrary fragments of this block ...
The modified Feistel network operates in the mode of irreversible gamming. This ensures that even knowing the keys and a certain sequence of gamma blocks it is impossible to calculate the values of gamma blocks outside of this known sequence of blocks.
To calculate gamma block values outside of a known sequence, it is required to perform a calculation from the starting point of gamming.
Practical implementation
While all this was a "fairy tale" and good wishes, it is time to turn them into a "true story", and this is how it looks:
First, the main statistical parameters:
------------------------------------------------------------------------------ RESULTS FOR THE UNIFORMITY OF P-VALUES AND THE PROPORTION OF PASSING SEQUENCES ------------------------------------------------------------------------------ generator is <dump.test> ------------------------------------------------------------------------------ C1 C2 C3 C4 C5 C6 C7 C8 C9 C10 P-VALUE PROPORTION STATISTICAL TEST ------------------------------------------------------------------------------ 6 12 15 10 9 14 4 5 11 14 0.122325 100/100 Frequency 5 6 15 12 11 13 9 9 11 9 0.494392 98/100 BlockFrequency 5 12 12 14 10 7 11 10 9 10 0.739918 100/100 CumulativeSums 6 9 14 11 10 13 8 7 14 8 0.574903 100/100 CumulativeSums 11 10 7 10 6 9 20 8 11 8 0.137282 100/100 Runs 12 11 6 8 12 12 10 13 6 10 0.759756 100/100 LongestRun 10 12 7 7 9 14 13 8 12 8 0.739918 98/100 Rank 16 10 9 5 8 10 7 12 10 13 0.455937 99/100 FFT 7 15 8 10 6 14 10 9 11 10 0.616305 100/100 NonOverlappingTemplate 9 10 10 11 13 9 6 11 8 13 0.897763 99/100 NonOverlappingTemplate 6 11 8 12 9 11 12 13 9 9 0.897763 100/100 NonOverlappingTemplate 8 6 5 12 10 12 9 16 12 10 0.401199 98/100 NonOverlappingTemplate 10 8 5 8 12 15 6 13 15 8 0.236810 100/100 NonOverlappingTemplate 11 9 6 12 6 8 13 7 12 16 0.350485 98/100 NonOverlappingTemplate 10 6 7 9 11 8 7 13 15 14 0.437274 97/100 NonOverlappingTemplate 8 6 7 17 13 12 11 9 8 9 0.366918 100/100 NonOverlappingTemplate 10 7 9 9 10 11 5 12 17 10 0.437274 99/100 NonOverlappingTemplate 7 8 13 7 17 6 8 11 6 17 0.055361 98/100 NonOverlappingTemplate 13 12 5 11 16 7 9 8 8 11 0.401199 99/100 NonOverlappingTemplate 12 8 10 8 14 5 7 13 13 10 0.534146 100/100 NonOverlappingTemplate 13 5 14 9 13 6 8 9 11 12 0.474986 99/100 NonOverlappingTemplate 11 9 9 10 11 7 7 15 11 10 0.851383 97/100 NonOverlappingTemplate 15 9 8 12 9 10 7 11 8 11 0.834308 98/100 NonOverlappingTemplate 10 13 6 10 13 7 8 11 10 12 0.816537 99/100 NonOverlappingTemplate 9 8 13 7 12 16 10 9 6 10 0.534146 98/100 NonOverlappingTemplate 14 14 7 13 6 8 10 6 10 12 0.437274 99/100 NonOverlappingTemplate 14 7 17 12 6 11 6 13 6 8 0.122325 98/100 NonOverlappingTemplate 13 8 10 5 12 11 9 6 10 16 0.383827 99/100 NonOverlappingTemplate 7 14 8 6 16 13 13 7 7 9 0.224821 97/100 NonOverlappingTemplate 9 10 11 13 7 9 10 15 9 7 0.779188 98/100 NonOverlappingTemplate 13 11 12 8 13 12 7 11 7 6 0.678686 99/100 NonOverlappingTemplate 8 13 12 4 9 10 8 16 13 7 0.262249 98/100 NonOverlappingTemplate 8 8 7 13 13 7 12 7 11 14 0.595549 99/100 NonOverlappingTemplate 15 13 12 5 10 7 7 9 13 9 0.419021 99/100 NonOverlappingTemplate 6 10 18 15 6 12 9 7 9 8 0.122325 100/100 NonOverlappingTemplate 11 12 10 10 8 9 7 11 10 12 0.983453 99/100 NonOverlappingTemplate 11 8 12 9 10 7 15 11 9 8 0.834308 100/100 NonOverlappingTemplate 12 7 10 6 10 13 4 10 18 10 0.129620 99/100 NonOverlappingTemplate 17 11 11 13 10 4 9 9 10 6 0.249284 98/100 NonOverlappingTemplate 9 7 14 16 12 10 9 7 7 9 0.474986 100/100 NonOverlappingTemplate 13 6 8 13 13 10 12 11 5 9 0.554420 100/100 NonOverlappingTemplate 8 12 11 8 12 14 8 11 8 8 0.867692 99/100 NonOverlappingTemplate 12 13 11 6 11 9 8 9 12 9 0.897763 99/100 NonOverlappingTemplate 10 10 13 10 5 8 10 8 10 16 0.554420 99/100 NonOverlappingTemplate 6 8 7 11 8 7 13 12 10 18 0.213309 100/100 NonOverlappingTemplate 12 9 12 9 11 6 11 11 12 7 0.897763 97/100 NonOverlappingTemplate 12 11 11 9 6 6 10 7 10 18 0.262249 99/100 NonOverlappingTemplate 6 9 12 8 7 13 10 12 11 12 0.816537 100/100 NonOverlappingTemplate 9 8 11 15 4 8 16 5 11 13 0.115387 100/100 NonOverlappingTemplate 12 6 8 14 7 16 9 10 8 10 0.437274 98/100 NonOverlappingTemplate 14 10 10 7 5 14 8 11 8 13 0.494392 98/100 NonOverlappingTemplate 14 6 7 11 10 10 14 9 7 12 0.616305 98/100 NonOverlappingTemplate 10 9 13 12 11 7 12 10 5 11 0.798139 100/100 NonOverlappingTemplate 17 10 15 7 9 8 6 12 11 5 0.145326 98/100 NonOverlappingTemplate 13 10 9 7 6 18 14 11 6 6 0.096578 97/100 NonOverlappingTemplate 11 8 7 10 7 13 15 12 7 10 0.637119 99/100 NonOverlappingTemplate 9 7 12 7 16 8 13 8 10 10 0.574903 97/100 NonOverlappingTemplate 9 12 14 13 4 8 7 11 11 11 0.514124 99/100 NonOverlappingTemplate 9 8 6 3 11 10 17 16 11 9 0.071177 100/100 NonOverlappingTemplate 6 11 9 12 14 9 5 13 11 10 0.595549 100/100 NonOverlappingTemplate 8 11 14 11 12 9 8 8 11 8 0.911413 99/100 NonOverlappingTemplate 15 10 10 10 5 9 10 12 9 10 0.779188 99/100 NonOverlappingTemplate 13 11 12 11 8 9 9 10 9 8 0.978072 99/100 NonOverlappingTemplate 9 12 11 8 11 9 9 11 13 7 0.955835 99/100 NonOverlappingTemplate 14 13 11 14 4 10 10 8 8 8 0.437274 99/100 NonOverlappingTemplate 10 9 17 15 9 6 12 11 4 7 0.115387 99/100 NonOverlappingTemplate 8 8 15 10 9 9 11 10 10 10 0.935716 99/100 NonOverlappingTemplate 8 8 13 11 10 3 9 7 14 17 0.115387 100/100 NonOverlappingTemplate 10 8 10 8 6 13 9 15 10 11 0.739918 99/100 NonOverlappingTemplate 10 11 8 5 8 5 13 11 12 17 0.202268 99/100 NonOverlappingTemplate 12 8 19 6 16 8 6 7 10 8 0.042808 96/100 NonOverlappingTemplate 3 11 12 13 6 7 16 12 11 9 0.162606 100/100 NonOverlappingTemplate 15 11 7 10 12 8 8 5 14 10 0.455937 98/100 NonOverlappingTemplate 5 11 12 10 11 13 13 12 8 5 0.514124 100/100 NonOverlappingTemplate 12 9 10 4 10 7 7 14 14 13 0.350485 99/100 NonOverlappingTemplate 10 7 11 15 10 6 11 9 12 9 0.759756 99/100 NonOverlappingTemplate 9 17 6 13 6 13 10 12 5 9 0.162606 100/100 NonOverlappingTemplate 11 10 4 13 7 7 15 17 10 6 0.080519 97/100 NonOverlappingTemplate 13 11 15 7 9 8 11 10 4 12 0.437274 100/100 NonOverlappingTemplate 9 13 10 10 4 9 13 11 13 8 0.637119 100/100 NonOverlappingTemplate 14 7 6 7 8 10 11 10 14 13 0.534146 100/100 NonOverlappingTemplate 11 13 10 6 10 11 11 7 12 9 0.897763 99/100 NonOverlappingTemplate 7 15 8 10 6 14 10 9 11 10 0.616305 100/100 NonOverlappingTemplate 11 9 9 6 13 10 8 7 12 15 0.637119 98/100 NonOverlappingTemplate 16 13 7 9 8 8 14 3 8 14 0.096578 99/100 NonOverlappingTemplate 7 9 9 14 6 9 11 15 6 14 0.334538 100/100 NonOverlappingTemplate 14 8 13 12 12 11 5 8 5 12 0.383827 99/100 NonOverlappingTemplate 12 6 11 5 11 13 11 11 9 11 0.739918 100/100 NonOverlappingTemplate 13 10 7 10 1 3 13 16 14 13 0.009535 98/100 NonOverlappingTemplate 6 6 15 10 13 6 3 16 16 9 0.015598 99/100 NonOverlappingTemplate 12 17 13 11 6 8 9 6 11 7 0.275709 100/100 NonOverlappingTemplate 11 10 7 8 13 8 12 15 8 8 0.699313 100/100 NonOverlappingTemplate 13 9 15 11 9 7 16 4 6 10 0.145326 99/100 NonOverlappingTemplate 6 13 14 8 6 9 12 10 14 8 0.474986 100/100 NonOverlappingTemplate 13 13 15 9 9 8 9 5 10 9 0.574903 100/100 NonOverlappingTemplate 13 10 16 7 6 9 13 7 8 11 0.401199 99/100 NonOverlappingTemplate 6 14 12 10 12 10 9 8 8 11 0.834308 100/100 NonOverlappingTemplate 14 13 6 8 10 5 15 10 7 12 0.289667 99/100 NonOverlappingTemplate 9 6 11 14 14 8 6 12 10 10 0.595549 100/100 NonOverlappingTemplate 12 13 12 13 9 12 6 3 9 11 0.366918 99/100 NonOverlappingTemplate 7 11 7 12 6 10 10 8 12 17 0.383827 100/100 NonOverlappingTemplate 11 8 9 11 18 7 9 5 9 13 0.236810 99/100 NonOverlappingTemplate 12 11 12 9 12 3 7 10 15 9 0.366918 100/100 NonOverlappingTemplate 15 8 8 8 10 11 9 11 8 12 0.851383 97/100 NonOverlappingTemplate 10 13 9 7 10 11 10 12 10 8 0.971699 100/100 NonOverlappingTemplate 10 9 10 12 11 9 15 6 12 6 0.657933 99/100 NonOverlappingTemplate 13 15 10 11 15 6 8 7 7 8 0.334538 100/100 NonOverlappingTemplate 7 13 16 7 9 9 11 6 14 8 0.334538 99/100 NonOverlappingTemplate 9 4 11 9 13 9 7 12 11 15 0.455937 100/100 NonOverlappingTemplate 16 7 12 7 9 12 13 7 6 11 0.366918 97/100 NonOverlappingTemplate 13 15 12 8 6 8 9 7 10 12 0.574903 98/100 NonOverlappingTemplate 10 8 14 9 14 5 14 10 8 8 0.474986 99/100 NonOverlappingTemplate 10 12 9 6 9 14 14 9 7 10 0.699313 99/100 NonOverlappingTemplate 11 7 7 9 13 4 13 13 17 6 0.096578 99/100 NonOverlappingTemplate 14 9 8 8 10 7 11 13 12 8 0.816537 98/100 NonOverlappingTemplate 8 8 8 8 13 8 11 14 14 8 0.678686 99/100 NonOverlappingTemplate 14 10 13 11 8 9 11 9 8 7 0.867692 98/100 NonOverlappingTemplate 10 8 11 12 8 12 15 11 5 8 0.616305 97/100 NonOverlappingTemplate 10 13 7 10 10 12 9 10 13 6 0.851383 99/100 NonOverlappingTemplate 10 11 10 8 7 8 11 9 15 11 0.867692 99/100 NonOverlappingTemplate 11 10 8 15 9 4 8 9 16 10 0.289667 98/100 NonOverlappingTemplate 8 18 10 8 11 10 9 7 12 7 0.383827 98/100 NonOverlappingTemplate 4 21 14 10 10 7 6 8 9 11 0.015598 100/100 NonOverlappingTemplate 10 7 9 10 8 9 11 16 10 10 0.816537 99/100 NonOverlappingTemplate 7 11 18 9 5 9 7 10 7 17 0.051942 100/100 NonOverlappingTemplate 16 9 11 6 8 6 7 13 11 13 0.334538 98/100 NonOverlappingTemplate 4 11 9 17 9 8 10 11 10 11 0.401199 100/100 NonOverlappingTemplate 10 5 18 15 13 9 11 9 6 4 0.037566 98/100 NonOverlappingTemplate 12 6 13 13 10 12 9 10 4 11 0.534146 99/100 NonOverlappingTemplate 13 8 9 5 4 15 13 13 8 12 0.181557 100/100 NonOverlappingTemplate 17 9 9 7 9 14 8 12 9 6 0.334538 97/100 NonOverlappingTemplate 7 11 14 5 9 15 10 10 14 5 0.224821 100/100 NonOverlappingTemplate 12 9 15 9 10 7 10 10 8 10 0.883171 99/100 NonOverlappingTemplate 10 13 8 7 8 6 12 10 17 9 0.383827 98/100 NonOverlappingTemplate 6 15 9 15 5 10 13 9 5 13 0.137282 100/100 NonOverlappingTemplate 11 12 8 9 8 15 10 10 7 10 0.851383 99/100 NonOverlappingTemplate 7 9 8 6 7 17 13 11 11 11 0.350485 100/100 NonOverlappingTemplate 13 7 8 12 10 9 8 10 7 16 0.574903 97/100 NonOverlappingTemplate 12 6 9 9 6 10 11 14 12 11 0.739918 100/100 NonOverlappingTemplate 8 10 16 12 9 5 11 10 7 12 0.494392 100/100 NonOverlappingTemplate 10 8 13 7 6 9 12 6 16 13 0.319084 99/100 NonOverlappingTemplate 9 14 12 9 6 5 10 10 10 15 0.455937 99/100 NonOverlappingTemplate 14 7 9 15 12 7 9 4 9 14 0.224821 99/100 NonOverlappingTemplate 11 13 11 6 12 7 14 10 9 7 0.678686 100/100 NonOverlappingTemplate 15 5 9 6 6 8 13 7 10 21 0.007160 98/100 NonOverlappingTemplate 10 12 12 6 9 7 13 11 6 14 0.574903 100/100 NonOverlappingTemplate 14 8 14 7 10 13 9 4 10 11 0.419021 98/100 NonOverlappingTemplate 7 8 12 8 6 12 14 11 9 13 0.657933 98/100 NonOverlappingTemplate 10 13 13 10 9 8 6 7 12 12 0.779188 99/100 NonOverlappingTemplate 9 13 9 8 11 14 7 9 9 11 0.883171 100/100 NonOverlappingTemplate 14 4 6 17 9 11 9 9 11 10 0.202268 99/100 NonOverlappingTemplate 9 9 11 7 10 13 11 13 6 11 0.851383 99/100 NonOverlappingTemplate 10 11 6 7 18 11 10 7 16 4 0.045675 99/100 NonOverlappingTemplate 7 7 8 15 9 8 11 13 7 15 0.383827 99/100 NonOverlappingTemplate 7 14 12 11 5 11 11 12 6 11 0.554420 99/100 NonOverlappingTemplate 11 13 10 6 10 12 10 7 12 9 0.883171 99/100 NonOverlappingTemplate 6 7 7 10 9 17 12 14 5 13 0.129620 99/100 OverlappingTemplate 8 15 14 11 9 9 11 9 7 7 0.657933 98/100 Universal 20 8 8 8 9 5 7 10 15 10 0.045675 99/100 ApproximateEntropy 4 6 4 9 3 10 10 7 7 6 0.350485 66/66 RandomExcursions 11 10 5 2 6 9 6 3 6 8 0.148094 64/66 RandomExcursions 7 13 3 5 7 5 6 6 11 3 0.066882 66/66 RandomExcursions 3 9 5 8 12 7 7 5 4 6 0.275709 66/66 RandomExcursions 11 7 8 7 9 6 4 3 8 3 0.275709 63/66 RandomExcursions 7 6 15 5 9 3 5 2 4 10 0.006196 66/66 RandomExcursions 3 6 4 12 7 7 6 6 9 6 0.350485 66/66 RandomExcursions 8 2 9 5 8 9 2 11 5 7 0.110952 66/66 RandomExcursions 8 2 6 8 8 7 8 6 7 6 0.772760 65/66 RandomExcursionsVariant 7 5 8 3 5 10 5 6 11 6 0.378138 65/66 RandomExcursionsVariant 4 10 5 4 8 9 3 9 10 4 0.178278 65/66 RandomExcursionsVariant 7 7 3 4 9 10 8 6 6 6 0.602458 66/66 RandomExcursionsVariant 4 5 6 9 7 4 6 9 10 6 0.602458 66/66 RandomExcursionsVariant 8 2 7 6 7 6 8 9 8 5 0.671779 65/66 RandomExcursionsVariant 6 5 7 3 5 9 7 10 6 8 0.637119 65/66 RandomExcursionsVariant 6 5 7 4 5 8 8 8 9 6 0.862344 66/66 RandomExcursionsVariant 9 8 6 8 12 4 2 4 8 5 0.134686 64/66 RandomExcursionsVariant 8 6 5 5 8 6 7 7 7 7 0.985035 65/66 RandomExcursionsVariant 6 6 6 7 5 5 9 8 8 6 0.949602 65/66 RandomExcursionsVariant 5 8 6 7 5 2 13 4 5 11 0.048716 66/66 RandomExcursionsVariant 5 6 7 7 2 5 9 11 9 5 0.299251 66/66 RandomExcursionsVariant 6 6 5 3 5 6 13 7 7 8 0.275709 66/66 RandomExcursionsVariant 7 3 5 5 5 10 8 8 6 9 0.568055 65/66 RandomExcursionsVariant 5 5 6 1 9 7 11 8 9 5 0.178278 66/66 RandomExcursionsVariant 5 3 6 3 6 7 11 5 11 9 0.148094 66/66 RandomExcursionsVariant 5 4 2 4 8 12 4 7 11 9 0.043745 65/66 RandomExcursionsVariant 11 13 8 9 5 10 13 14 9 8 0.637119 100/100 Serial 11 13 5 9 11 14 8 8 9 12 0.678686 100/100 Serial 9 8 12 14 6 9 10 8 11 13 0.779188 98/100 LinearComplexity - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - The minimum pass rate for each statistical test with the exception of the random excursion (variant) test is approximately = 96 for a sample size = 100 binary sequences. The minimum pass rate for the random excursion (variant) test is approximately = 62 for a sample size = 66 binary sequences. For further guidelines construct a probability table using the MAPLE program provided in the addendum section of the documentation. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - This is a typical result of NIST tests of new crypto-transformation based on GOST 28147-89. The results of tests on any random keys and initial fillings always fit into the statistical parameters of a random sequence.
To reduce testing time, a simplified method was used. First, an experiment was conducted on a hundred blocks one million bits long in a gamut of 24 megabytes long (the first half of the gamut is used).
In the case of an unsuccessful experiment (falling out of the range of permissible proportions), the same gamma, already in full, was tested on blocks of two million bits in length. For such experiments, all test launches were successful (in a series of 100 experiments).
It is clear that tests with a block of two million bits in length should also sometimes lead to falling out of the range of proportions, but due to limitations on the number of experiments, there were no such cases.
These statistical parameters of the gamut are much better than the gamma produced by classical GOST, it often contains keys that the NIST tests do not pass in principle. The AES cipher in similar experiments is not much different from the traditional GOST.
The statistical parameters obtained in experiments on the norms of the 8-byte block cipher for a block cipher with a block size of 256 bytes are fantastic.
This is the same as, for example, throwing a coin 12 times and receiving an equal loss of "eagle" and "nutlets", to demand that the cube, also thrown 12 times, fall on each face twice a time ...
This is theoretically possible only with very high differential entropy between adjacent blocks and characterizes the level of complexity of the block cipher.
And the most interesting, these parameters are obtained with one round of conversion. There are no other block ciphers satisfying the requirements of randomness when using just one round.
The maximum cryptographic power of this cipher is already achieved in 16 rounds, but for the current level of cryptanalysis it is clearly redundant.
Now about the speed

This is a screenshot of the implementation of multi-threaded crypto-transformation based on GOST 28147-89 in the FastSecurityBoxes program, the testing was carried out according to the procedure described in the article “The Second Coming of GOST”.
As can be seen in the screenshot, the copy speed has reached the limit for test SSDs and is 453 MBytes / sec. when the processor is only 6 percent.
Theoretically, in tests of pure cryptography, the encryption speed for the gamming mode is 12 GBytes / sec. for one physical core of the processor (Skylake models and above) operating at a frequency of 3 GHz and above.
The encryption speed is no longer determined by the frequency of the processor, but by the bandwidth of the RAM of the computing system.
Russian Roulette, 2017 and its future application
Recently, with the help of the FSB, we began to receive ciphers with sonorous names, such as “Magma”, “Grasshopper”, and we will continue this tradition.
We will call this block cipher "Russian Roulette" .
Why "Russian", I hope everyone understands. A "roulette", because the cipher is built on the rotations (ring shifts) of binary sequences. Such shifts there are only explicitly 192 pieces per round.
By the way, the Russian officers who played Russian Roulette were crazy, but far from foolish. They thoroughly cleaned their revolvers, and knew physics well, and therefore kept the revolver while rotating the drum horizontally ...
A drum with one / five of the six bullets becomes unbalanced, and always strive to stand up empty chamber in front of the barrel.
So it was just an accident that the drum was jamming from different specks / hairs, getting to the empty chamber was “pseudo-random” and had a strict, predictable result.
Previously, when introducing a parallel implementation method to GOST 28147-89, I had to fully describe it, since it was officially certified by the FSB.
Now the situation is different, no official status is expected. Therefore, there will be no detailed description of the “Russian Roulette” algorithm, this is a kind of copyright protection. If it becomes interesting to become professionals, let them turn to their colleagues, - reverse programmers. That's who will have to break his head ...
In short, the Russian Roulette algorithm will be proprietary and this is coming soon: Russian Roulette, 2017 .
The encryption algorithm, closed from research, is of course nonsense, since there is no confidence in the encryption reliability.
But Russian Roulette is not an encryption system, we do not need a float with a regulator. Let me be the first to throw a stone at someone who says that this is a cipher, this is not an encryption system, the knight's move is made with a slight movement of the hand, and the algorithm is turned into a high-speed system of hashing and error correction, because first of all you need to take care of data integrity ...
The self-made Feistel cyclic network ideally meets the requirements of the “turbo code” for correcting errors, I did not do it on purpose, “he came” ...
Standard feedback gamma is converted to a hash function, if the keys are associated with previously processed data ...
Well, the fact that as a result, the data will also be reliably protected from viewing and modification - so sorry, a side effect of the system of hashing and error correction.
While the cryptographic “engine” of this future system is presented, it can be evaluated on test scales in terms of statistics and cryptographic resistance.
In the future, what Krylov failed to do was to be done. With the help of Russian roulette, we will bind the three members of his fable into the “cart” of responsible archiving, the “swan” of privacy, the “cancer” of authenticity and the “pike” of reliability. In this case, make them pull the "cart" at a breakneck pace ...
Difficult task, but solvable.
Practical implementation of crypto functions
The Russian Roulette algorithm is built into the demo version of the FastSecurityBoxes program in a partially cropped form. So far, for testing, only the basic transform operating in the gamming mode has been implemented. One round is used, this is enough for reliable passing of the NIST tests and cryptographic strength at the level of 2256 * 8 (the brute force direct attack option).
Keys are recalculated after issuing 64 kilobytes of gamma.
The algorithm itself is implemented on AVX commands using YMM registers, so this algorithm can effectively work only on the latest Intel processors (Skylake and higher).
On AMD processors, even the newest ones, the Russian Roulette algorithm will work slowly, since operations using YMM registers are implemented in them by firmware and not by hardware.
So that in the future, the FastSecurityBoxes program was required for practical work, it has a “payload” as a function of creating backup copies of logical disks (of course, recovery of disks is also there).
The choice of the applied task is determined on the one hand by the relevance of the topic, and on the other hand by the clarity of the result. Creating backup copies of the disks was naturally “sharpened” for high-speed SSD drives, which already today on the NVMe interface can work at a speed of 2-3 Gigabytes per second. At such speeds, nobody has yet been able to encrypt data, but now this is already a reality.
In addition to the new, yet exotic multi-threading algorithm, FastSecurityBoxes implements encryption according to the classical GOST 28147-89 in 8 parallel threads (for old processors) and 16 parallel threads (for skyleyka and above). These parallel encryption methods are certified by the FSB.
Encryption in 8 and 16 streams is included in the program for a substantive comparison of the results so that the difference could be felt ...
Apparently I confused readers with the terms "multi-threaded" and "parallel", so I will explain.
The parallel implementation method GOST 28147-89 is a certified FSB method. Parallelism involves the implementation of standard cryptographic procedures simultaneously on 4-8-16 independent physical devices. In this case, encryption keys, replacement blocks are the same everywhere, but the input and output data are different. Acceleration of work is achieved due to the simultaneous operation of several independent physical devices.
The term “independent physical device” as applied to a processor is a conventional concept, in reality, the processor has a set of registers on which the same transformations are performed simultaneously (with one processor command). But for simplicity of understanding, we will consider them independent physical devices operating strictly parallel and synchronous.
The multithreaded method implemented in the “Russian Roulette” algorithm differs significantly from the parallel one, here are its main differences:
1. There is a single block round converter.
2. The block length (so far) is 256 bytes and can be scaled.
3. Block fragments (two bytes each) are processed in independent streams.
4. Combining fragments produced in an additional transformation.
The multithreaded method allows you to increase the size of key data and the size of the input data block. Moreover, a change in any of the 2048 bits of the input block leads to a guaranteed change in all 2048 output bits after ten rounds of conversion.
Now the cipher contains 128 threads, when the processor with the AVX-512 command set appears, it will be possible to increase the number of threads to 512 (the data block will be 1 KB in size) and increase the speed twice.
In the meantime, the bottom line ..
The speed is 12 Gbytes per second for a processor with a frequency of 3 GHz, there is nothing to compare. The speed of the implementation of the algorithm “Russian Roulette” in the gamming mode “incomparable”. It is the fastest known pseudo-random sequence generator that meets the requirements of NIST tests.
The mathematical complexity of the cryptanalysis of the basic transformation “Russian Roulette” is determined by the dimension of the key, in our case it is equal to 2256 * 8.
The algorithmic complexity of cryptanalysis taking into account the known hacking methods for the basic Russian Roulette transformation is at least not less than the parent transformation of GOST 28147-89.
I will not overload the article with information about this new algorithm, while let the interested parties check what was said in the test program.
Download FastSecurityBoxes program here .
For testing, it provides the function of issuing a "clean" gamma. In this mode, test pseudorandom files are created for transformations in accordance with GOST 28147-89 and Russian Roulette.
PS
The FastSecurityBoxes program (Forced Secretive Images if in Russian) will soon turn into a responsible archiving program suitable for mass use, and then, I hope, into a full-featured commercial product. Accordingly, it is interesting to compare it with the commercial market backup luminaries in terms of copy speed and processor load.
The speed parameters of FastSecurityBoxes have already been cited in the article “The Second Coming of GOST”, let's see as an example what Acronis can do in the same modes of operation, on the same hardware platform.
Here's how it creates a sector dump without encryption and compression:

The program performs sector-by-sector copying at a speed of 368 MB / s ... Apparently, synchronous single-threaded I / O with cycles of waiting for the end of an I / O operation is used. Otherwise, do not explain too much CPU usage on I / O operations, which is 20%. Clearly outdated solution from the past millennium.
On the same hardware configuration, the FastSecurityBoxes test program provided a dumping speed of 450 MB / s. with a processor load of 6 percent.
Here is what Acronis issues on sector copying (without compression) with dump encryption according to GOST 28147-89:

The speed dropped almost ten times, to 42 MB / s. using 17 percent of the processor's computing resources, FastSecurityBoxes provided 330 MB / sec in this mode, while using 10 percent of the computing resources, I think comments are superfluous ...
And the conclusion is obvious, Acronis uses an outdated classical implementation of GOST 28147-89 on the RON registers of the processor, therefore, such a low speed.
This is what Acronis does with encryption dump using the most “lightweight” AES-128 algorithm, again without compression. This algorithm for cryptographic resistance is worse than GOST 28147-89, but its implementation is the fastest due to the reduced number of rounds.

The speed has increased up to 80 MB / s, but still it is catastrophically low, BitLocker provided in this mode a speed of about 360 MB / s. Obviously, outdated crypto-library without the support of Intel hardware crypto accelerator is used.
How does all this look pale against the backdrop of modern technology ...
Source: https://habr.com/ru/post/331960/
All Articles