JaCarta Authentication Server and JaCarta WebPass for OTP Authentication in Linux SSH
In this article we will talk about the main stages of setting up authentication in Linux SSH to replace password authentication with one-time passwords - this article describes the authentication scenario in an SSH connection session to Linux OS using one-time passwords using a JaCarta WebPass device .

JaCarta WebPass developed by Aladdin RD is a USB token with “OTP on board” for two-factor user authentication when accessing protected information resources using a one-time password or a reusable password token stored in memory.
The scenario proposed in the article implies the use of the RADIUS server to verify the authenticity of the entered one-time code, as well as the OTP value verification system. As an OTP key management system, we will use the JaCarta Authentication Server (JAS) also developed by Aladdin RD.
')
The user, when an SSH connection is established, will enter an OTP value instead of a password at the authentication stage. The PAM module will send the transmitted value to the RADIUS Server, which will check it and allow or deny authentication.
This instruction is configured for the following operating system versions:
For Windows Server, you need to create a domain, add the NPS role. To do this, follow the tips below.
Open the snap-in to add the NPS role.
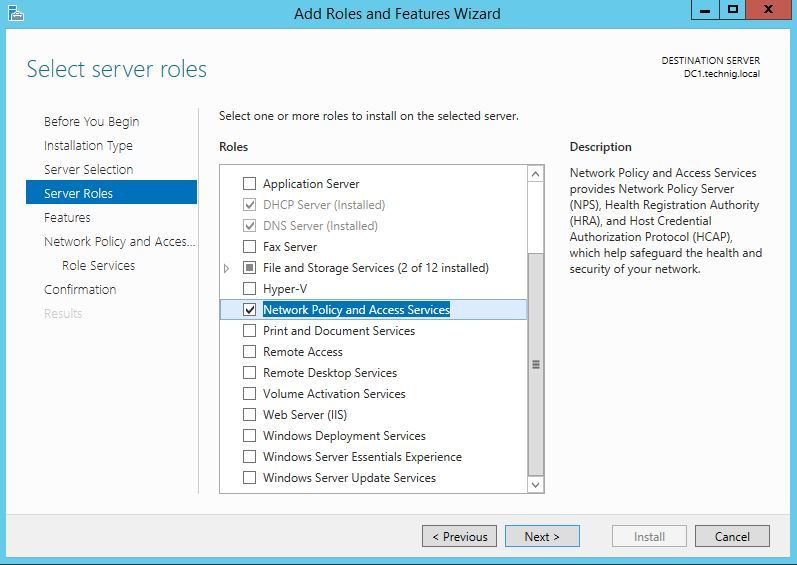
When selecting services and components, select Network Policy Server.
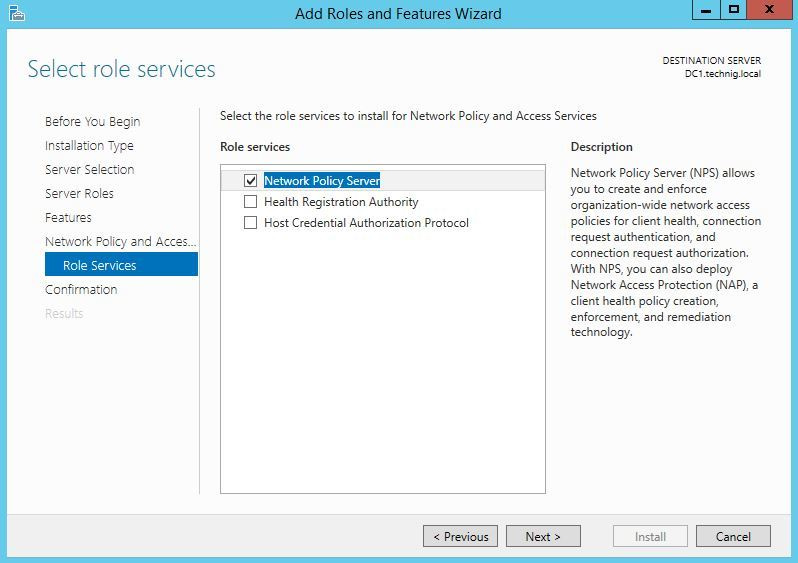
After that, you will see the NPS equipment available.

On the server side, you must perform the following steps:
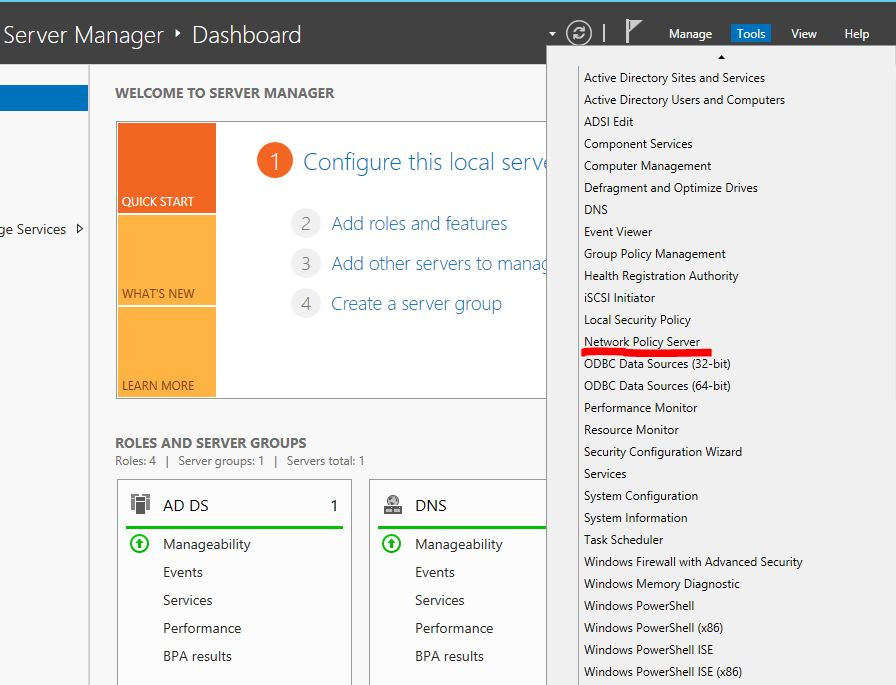
In the snap-in menu, select NPS - RADIUS Clients and Servers - RADIUS Clients, then right-click to open the context menu and click New.
Enter the client's settings for connecting to the RADIUS server: the name displayed in the snap-in, the address or name of the client, the shared secret for the client and server (you need to think of it).

Create a domain user whose name will be used for authentication on a Linux server.
To initialize JaCarta WebPass, you need to open the Web Pass Tool application, which is included in the JaCarta Single Client software. You can download software via the link https://www.aladdin-rd.ru/support/downloads/jacarta/ .
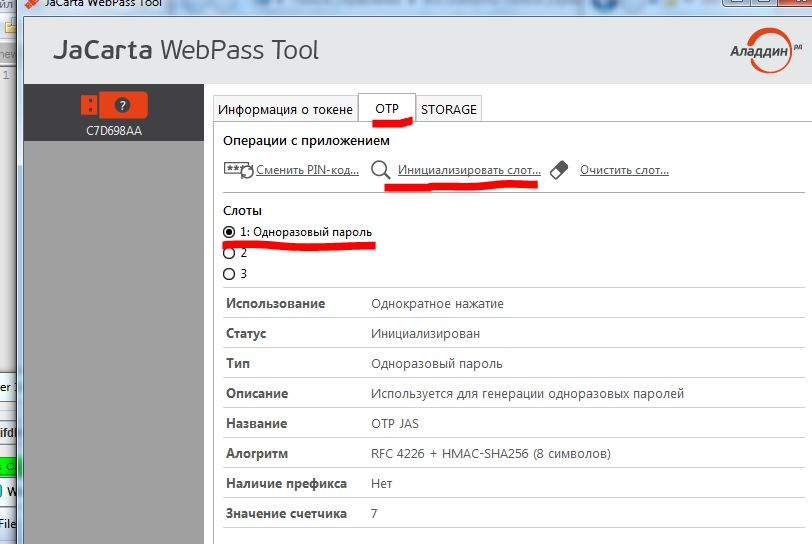
Open the JaCarta WebPass Tool application, select the OTP tab.
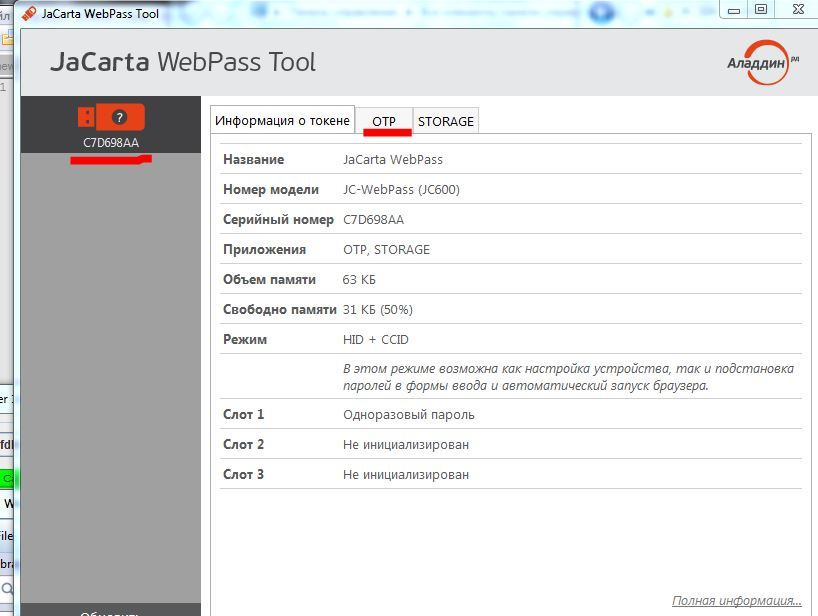
Select the slot to initialize, then click the Initialize item in the menu.
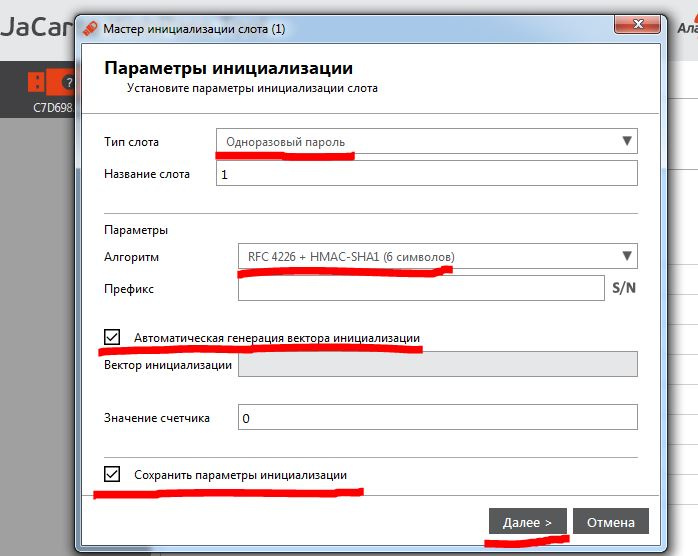
In the settings, specify the One-time password, the first mechanism from the drop-down list, check Save initialization parameters and click Next.
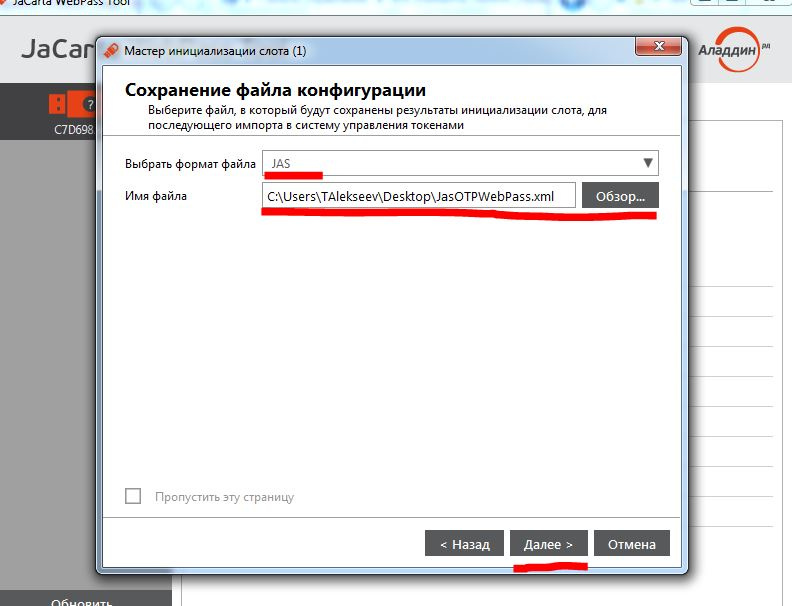
Select the format of the JAS file and the path to the folder where the initialization file will be saved. This file is required to connect the key to JAS.
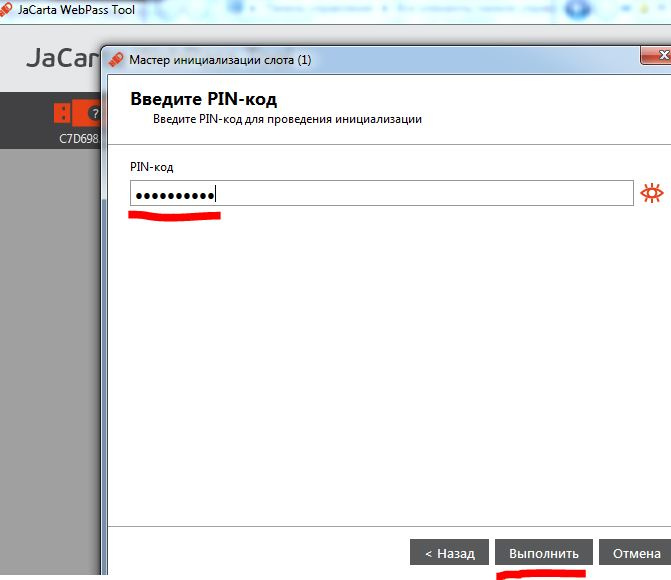
Enter the PIN for the key and click Next.
On the JAS side, follow the steps below.
Add an OTP device to the system, bind the user to the device. To do this, open the JAS snap-in.
In the snap-in, select Import key media.
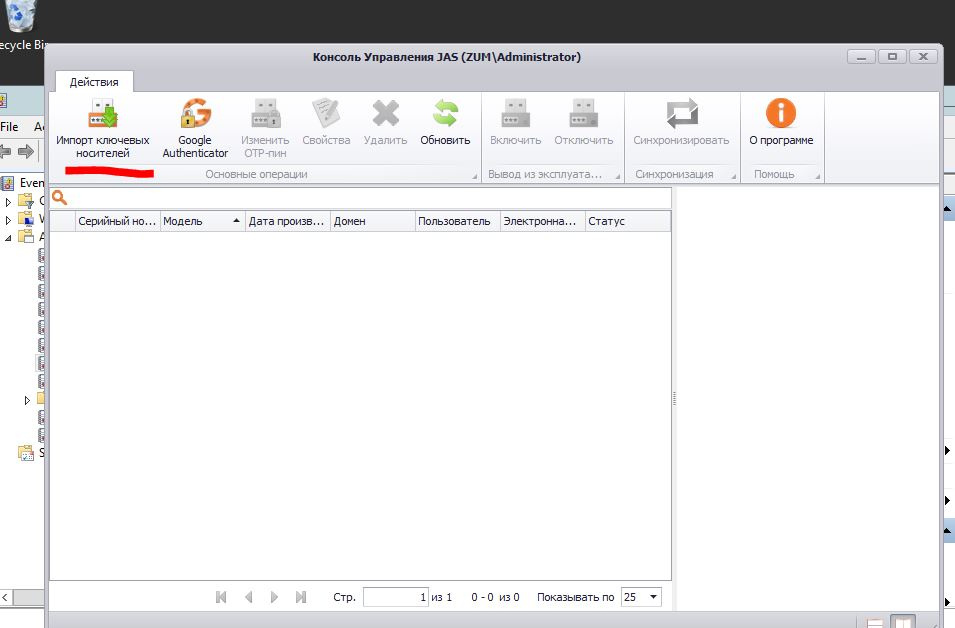
Specify the path to the file with JaCarta WebPass initialization data (the file can be obtained during slot initialization in the Web Pass Tool application, which is included in the JaCarta Single Client software. You can download the software at https://www.aladdin-rd.ru / support / downloads / jacarta / ).

If successful, click Next.

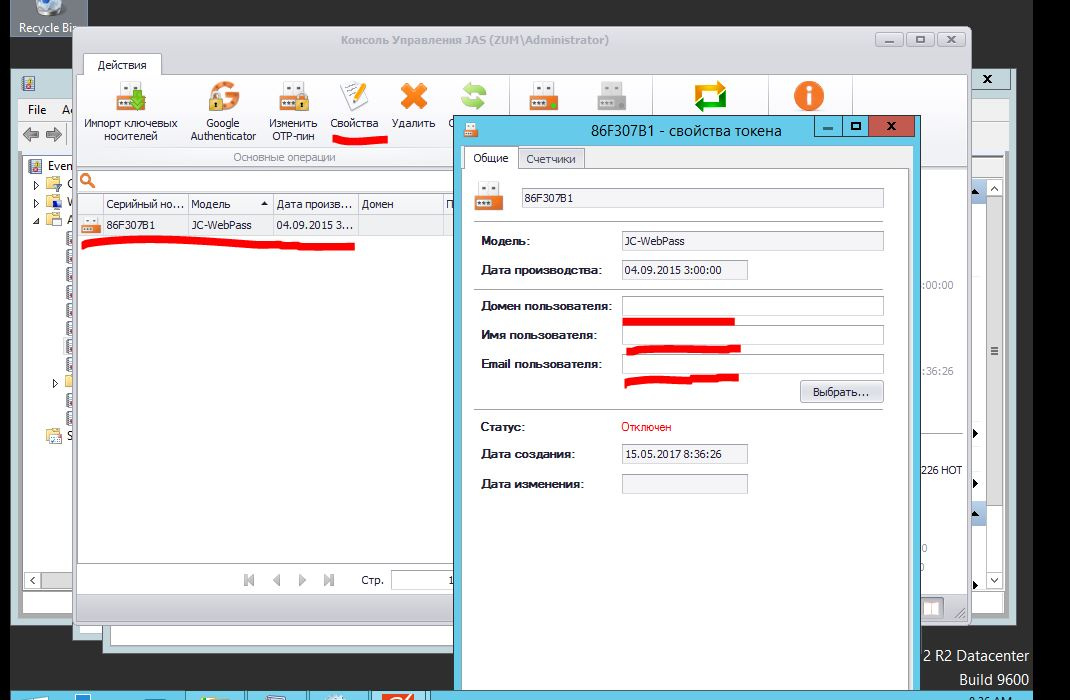
Select the added key, click Properties in the menu. To bind to the user, specify the name and email address for the domain user.
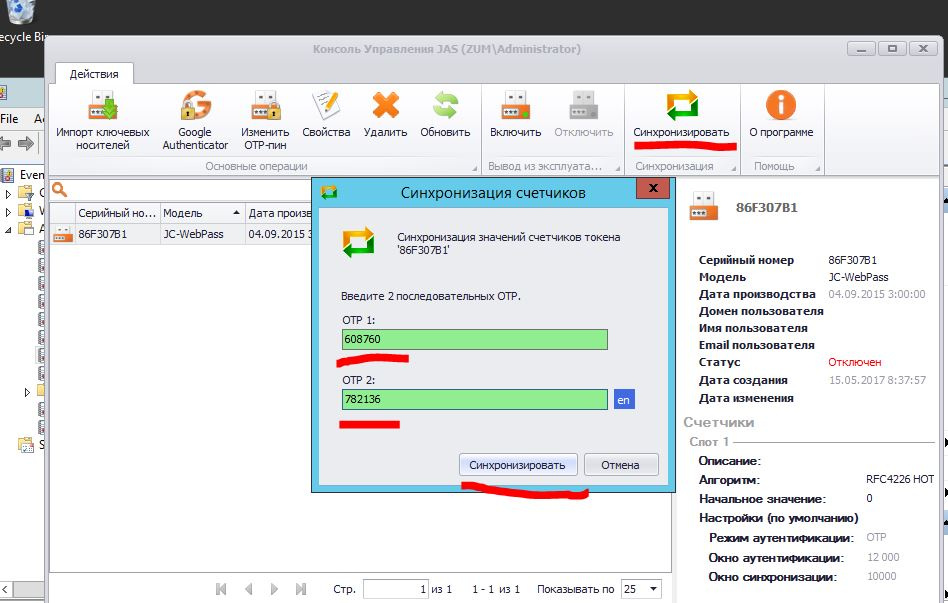
Before activating, you should synchronize the device, to do this, click Sync in the menu, point to the OTP 1 window and click on the JaCarta WebPass device button, then repeat with the OTP 2 window.
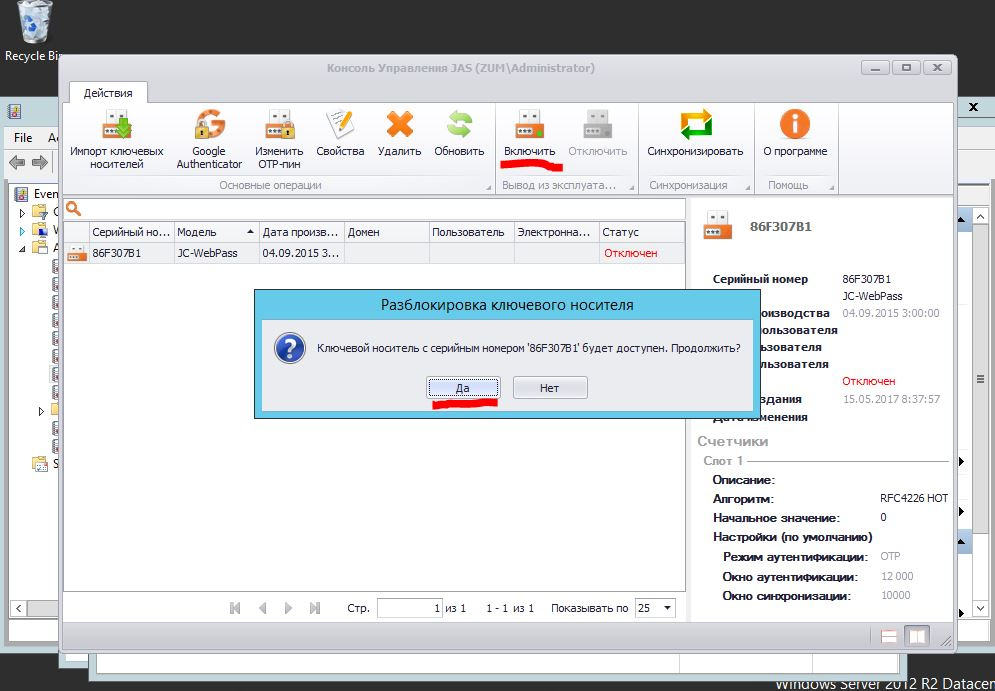
To activate, select Enable.
On the Linux server side, all operations must be performed as root.
Add values for your RADIUS server, IP address, or server name, shared secret to the /etc/pam_radius_auth.conf file.
In the /etc/pam.d/sshd file, add the line auth sufficient pam_radius_auth.so over include common-auth, as shown below.
Create a local user with the name corresponding to the user in AD.
For verification, we use the Microsoft Windows 7 operating system with the PUTTY client installed in SSH.
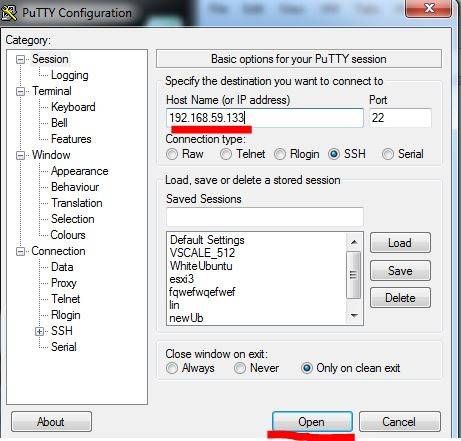
Let's open Putty and we will specify the address of the machine interesting us on Linux.
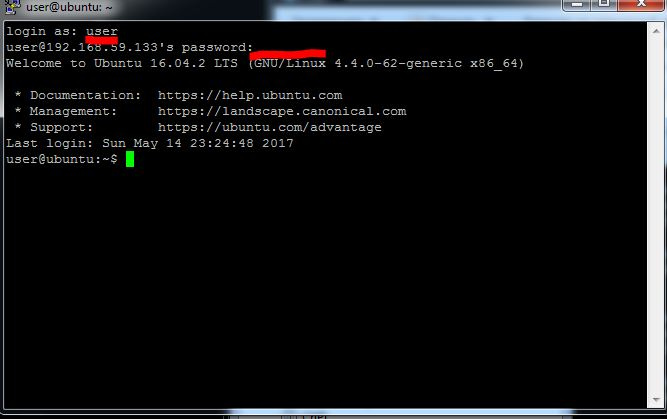
Enter your username, Enter, then click on the JaCarta WebPass device button, Enter.
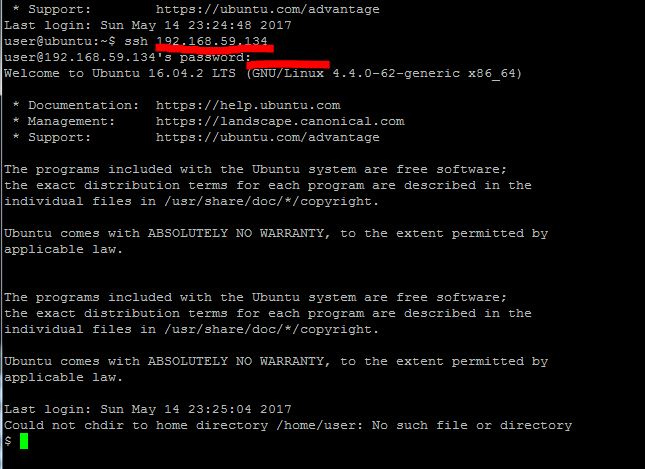
Next, enter the command SSH [Servername2], Enter, press the button on the device, Enter.

JaCarta WebPass developed by Aladdin RD is a USB token with “OTP on board” for two-factor user authentication when accessing protected information resources using a one-time password or a reusable password token stored in memory.
The scenario proposed in the article implies the use of the RADIUS server to verify the authenticity of the entered one-time code, as well as the OTP value verification system. As an OTP key management system, we will use the JaCarta Authentication Server (JAS) also developed by Aladdin RD.
')
The user, when an SSH connection is established, will enter an OTP value instead of a password at the authentication stage. The PAM module will send the transmitted value to the RADIUS Server, which will check it and allow or deny authentication.
Used to demonstrate the environment
This instruction is configured for the following operating system versions:
- Microsoft Windows Server 2012;
- Ubuntu Server 16;
- Microsoft Windows 7.
Environmental requirements
For Windows Server, you need to create a domain, add the NPS role. To do this, follow the tips below.
Open the snap-in to add the NPS role.

When selecting services and components, select Network Policy Server.

After that, you will see the NPS equipment available.

Setup on the RADIUS server side
On the server side, you must perform the following steps:
- add client radius with IP address or Linux server name;
- Select the NPS snap-in on the server.

In the snap-in menu, select NPS - RADIUS Clients and Servers - RADIUS Clients, then right-click to open the context menu and click New.

Enter the client's settings for connecting to the RADIUS server: the name displayed in the snap-in, the address or name of the client, the shared secret for the client and server (you need to think of it).

Create a domain user whose name will be used for authentication on a Linux server.
Preparing JaCarta WebPass
To initialize JaCarta WebPass, you need to open the Web Pass Tool application, which is included in the JaCarta Single Client software. You can download software via the link https://www.aladdin-rd.ru/support/downloads/jacarta/ .
Open the JaCarta WebPass Tool application, select the OTP tab.

Select the slot to initialize, then click the Initialize item in the menu.

In the settings, specify the One-time password, the first mechanism from the drop-down list, check Save initialization parameters and click Next.

Select the format of the JAS file and the path to the folder where the initialization file will be saved. This file is required to connect the key to JAS.

Enter the PIN for the key and click Next.

Setup on the JAS side
On the JAS side, follow the steps below.
Add an OTP device to the system, bind the user to the device. To do this, open the JAS snap-in.
In the snap-in, select Import key media.

Specify the path to the file with JaCarta WebPass initialization data (the file can be obtained during slot initialization in the Web Pass Tool application, which is included in the JaCarta Single Client software. You can download the software at https://www.aladdin-rd.ru / support / downloads / jacarta / ).

If successful, click Next.

Select the added key, click Properties in the menu. To bind to the user, specify the name and email address for the domain user.

Before activating, you should synchronize the device, to do this, click Sync in the menu, point to the OTP 1 window and click on the JaCarta WebPass device button, then repeat with the OTP 2 window.

To activate, select Enable.

Setup on the Linux Server side
On the Linux server side, all operations must be performed as root.
# sudo -i # apt-get install libpam-radius-auth Add values for your RADIUS server, IP address, or server name, shared secret to the /etc/pam_radius_auth.conf file.
# nano /etc/pam_radius_auth.conf # The timeout field controls how many seconds the module waits before # deciding that the server has failed to respond. # # server[:port] shared_secret timeout (s) [SERVER IP] [ ] 3 In the /etc/pam.d/sshd file, add the line auth sufficient pam_radius_auth.so over include common-auth, as shown below.
# nano /etc/pam.d/sshd # PAM configuration for the Secure Shell service # Standard Un*x authentication. auth sufficient pam_radius_auth.so @include common-auth # Disallow non-root logins when /etc/nologin exists. Create a local user with the name corresponding to the user in AD.
Solution Verification
For verification, we use the Microsoft Windows 7 operating system with the PUTTY client installed in SSH.
Let's open Putty and we will specify the address of the machine interesting us on Linux.
Enter your username, Enter, then click on the JaCarta WebPass device button, Enter.
Next, enter the command SSH [Servername2], Enter, press the button on the device, Enter.
Source: https://habr.com/ru/post/331908/
All Articles