Fighting viruses and infrastructure, or disabling SMB v1

In connection with the recent outbreak of the WannaCry cipher operator that exploits the SMB v1 vulnerability, there are again tips on disabling this protocol. Moreover, Microsoft strongly recommended disabling the first version of SMB back in September 2016. But such a shutdown can lead to unexpected consequences, even curiosities: I personally came across a company where, after the fight against SMB, the Sonos wireless speakers stopped playing.
Especially to minimize the likelihood of “shot in the foot,” I want to remind you of the features of SMB and consider in detail what the ill-considered disabling of its old versions threatens.
SMB (Server Message Block) is a network protocol for remote access to files and printers. It is used when connecting resources via \ servername \ sharename. The protocol initially worked on top of NetBIOS using UDP ports 137, 138 and TCP 137, 139. With the release of Windows 2000, it started working directly using TCP port 445. SMB is also used to log into the Active Directory domain and work in it.
In addition to remote access to resources, the protocol is also used for interprocessor communication via “named flows” - named pipes . The process is accessed via the path \. \ Pipe \ name.
The first version of the protocol, also known as CIFS (Common Internet File System), was created in the 1980s, but the second version appeared only with Windows Vista, in 2006. The third version of the protocol came out with Windows 8. In parallel with Microsoft, the protocol was created and updated in its open source implementation of Samba .
In each new version of the protocol, various improvements were added to increase the speed, security and support for new functions. But at the same time, support for old protocols remained for compatibility. Of course, in the old versions there were enough vulnerabilities, one of which is used by WannaCry .
| Version | operating system | Added, compared with the previous version |
| SMB 2.0 | Windows Vista / 2008 | The number of protocol commands has changed from 100+ to 19 |
| The possibility of "pipeline" work - sending additional requests before receiving a response to the previous | ||
| Support for symbolic links | ||
| Signature of HMAC SHA256 messages instead of MD5 | ||
| Increase cache and write \ read blocks | ||
| SMB 2.1 | Windows 7 / 2008R2 | Performance improvement |
| Support for higher MTU value | ||
| BranchCache support - a mechanism that caches requests to the global network on a local network | ||
| SMB 3.0 | Windows 8/2012 | Ability to build a transparent, failover cluster with load distribution |
| Direct Memory Access (RDMA) support | ||
| Control via Powershell cmdlets | ||
| VSS support | ||
| AES – CMAC Signature | ||
| AES – CCM Encryption | ||
| Ability to use network folders to store HyperV virtual machines | ||
| Ability to use network folders to store Microsoft SQL databases | ||
| SMB 3.02 | Windows 8.1 / 2012R2 | Security and speed improvements |
| Automatic cluster balancing | ||
| SMB 3.1.1 | Windows 10/2016 | AES – GCM encryption support |
| Integrity check prior to authentication using the SHA512 hash | ||
| Mandatory secure "negotiations" when working with SMB 2.x clients and above |
Considered conditionally affected
It is quite easy to look at the currently used protocol version; we use the Get – SmbConnection cmdlet for this:

Displays the cmdlet with open network resources on servers with different versions of Windows.
From the output, you can see that a client that supports all versions of the protocol uses the highest possible version supported by the server to connect. Of course, if the client supports only the old version of the protocol, and it will be disabled on the server, the connection will not be established. You can enable or disable support for old versions in modern Windows systems using the Set – SmbServerConfiguration cmdlet , and see the status as follows:
Get–SmbServerConfiguration | Select EnableSMB1Protocol, EnableSMB2Protocol 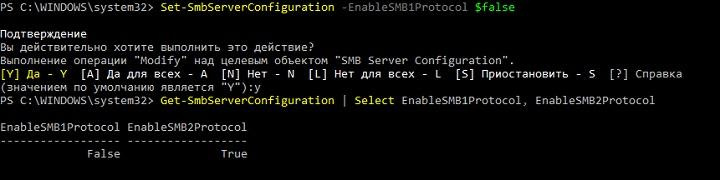
Disable SMBv1 on a server running Windows 2012 R2.
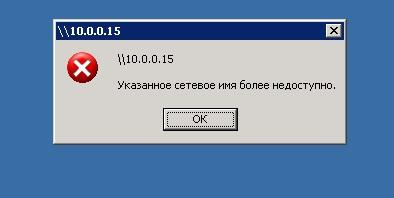
Result when connecting with Windows 2003.
Thus, if you disable the old, vulnerable protocol, you can lose the network performance with old clients. In addition to Windows XP and 2003, SMB v1 is also used in a number of software and hardware solutions (for example, NAS on GNU \ Linux, using the old version of samba).
| Manufacturer | Product | Comment |
| Barracuda | SSL VPN | |
| Web Security Gateway backups | ||
| Canon | Scan to a network share | |
| Cisco | WSA / WSAv | |
| Waas | Versions 5.0 and higher | |
| F5 | RDP client gateway | |
| Microsoft Exchange Proxy | ||
| Forcepoint (Raytheon) | "Some Products" | |
| HPE | ArcSight Legacy Unified Connector | Older versions |
| Ibm | Netserver | Version V7R2 and later |
| QRadar Vulnerability Manager | Versions 7.2.x and later | |
| Lexmark | Multifunction scan for network resource | Firmware eSF 2.x and eSF 3.x firmware |
| Linux Kernel | CIFS client | 2.5.42 to 3.5.x |
| Mcafee | Web gateway | |
| Microsoft | Windows | XP / 2003 and older |
| MYOB | Accountants | |
| Netapp | ONTAP | Versions up to 9.1 |
| NetGear | ReadyNAS | |
| Oracle | Solaris | 11.3 and older |
| Pulse secure | PCS | 8.1R9 / 8.2R4 and older |
| Pps | 5.1R9 / 5.3R4 and older | |
| QNAP | All storage devices | Firmware older than 4.1 |
| Redhat | Rhel | Versions 7.2 |
| Ricoh | Multifunction scan for network resource | In addition to a number of models |
| RSA | Authentication Manager Server | |
| Samba | Samba | Older than 3.5 |
| Sonos | Wireless speakers | |
| Sophos | Sophos UTM | |
| Sophos xg firewall | ||
| Sophos Web Appliance | ||
| Suse | SLES | 11 and older |
| Synology | Diskstation manager | Only management |
| Thomson reuters | CS Professional Suite | |
| Tintri | Tintri OS, Tintri Global Center | |
| VMware | Vcenter | |
| ESXi | Over 6.0 | |
| Worldox | GX3 DMS | |
| Xerox | Multifunction scan for network resource | Firmware without ConnectKey Firmware |
The list is taken from the Microsoft site, where it is regularly updated.
The list of products that use the old version of the protocol is quite large - you should definitely think about the consequences before disabling SMB v1.
Still, disable
If there are no programs and devices using SMB v1 on the network, then, of course, it is better to disable the old protocol. At the same time, if Windows 8/2012 is turned off on the SMB server using the Powershell cmdlet, then for Windows 7/2008 you will need to edit the registry. This can also be done using Powershell:
Set–ItemProperty –Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB1 –Type DWORD –Value 0 –Force Or in any other convenient way. In this case, to apply the changes will need to reboot.
To disable SMB v1 support on the client, simply stop the service responsible for its work and fix the dependencies of the lanmanworkstation service. This can be done with the following commands:
sc.exe config lanmanworkstation depend=bowser/mrxsmb20/nsi sc.exe config mrxsmb10 start=disabled For the convenience of disabling the protocol throughout the network, it is convenient to use group policies, in particular Group Policy Preferences. With them you can conveniently work with the registry.

Creating a registry item through group policies.
To disable the protocol on the server, simply create the following parameter:
path: HKLM: \ SYSTEM \ CurrentControlSet \ Services \ LanmanServer \ Parameters;
new parameter: REG_DWORD with the name SMB1;
- value: 0.
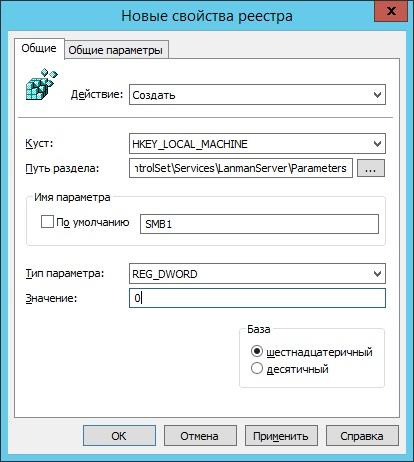
Creating a registry key to disable SMB v1 on the server through group policies.
To disable SMB v1 support on clients, you need to change the value of two parameters.
First, disable the SMB v1 protocol service:
path: HKLM: \ SYSTEM \ CurrentControlSet \ services \ mrxsmb10;
parameter: REG_DWORD with the name Start;
- value: 4.

We update one of the parameters.
Then we fix the LanmanWorkstation service dependency so that it does not depend on SMB v1:
path: HKLM: \ SYSTEM \ CurrentControlSet \ Services \ LanmanWorkstation;
parameter: REG_MULTI_SZ named DependOnService;
- value: three lines - Bowser, MRxSmb20 and NSI.
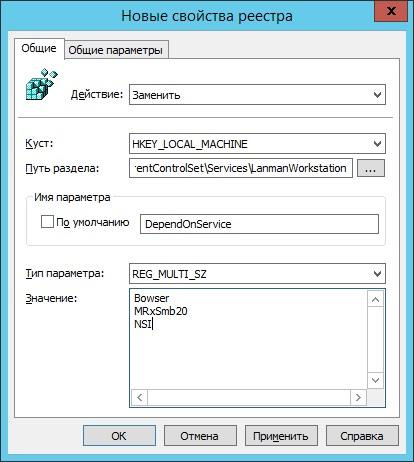
And replace another.
After applying Group Policy, you must restart the organization’s computers. After restarting SMB v1 will cease to be used.
Works - do not touch
Strangely enough, this old commandment is not always useful - in a rarely updated infrastructure, cryptographers and Trojans can start. However, inaccurately shutting down and updating services can paralyze the work of an organization as well as viruses.
Tell me, have you turned off SMB of the first version? There were a lot of victims?
')
Source: https://habr.com/ru/post/331906/
All Articles