Incident Report: GoldenEye / Petya

On June 27, 2017, a massive attack began using a family option.
cryptographers, known as GoldenEye, from which many countries of the world have suffered.
In addition to encrypting files, this family of encryptors is characterized by encrypting the MBR (Windows Master Boot Record) with rights, blocking full access to the computer.
general information
')
This version of the malware is distributed as a DLL, which has a parameter that changes with each sample to start the encryption process on the computer. On startup, it encrypts certain files on the disks of the infected system. With administrator rights, it also encrypts the boot sector of the system, preventing access to the PC until a special access code is entered that will decrypt the system.
Such an access key is provided after the victim pays the required ransom. Also, this cryptographer creates a scheduled task to shut down the computer. After restarting the PC, GoldenEye displays a false window with information indicating that there are disk issues that will be fixed soon.
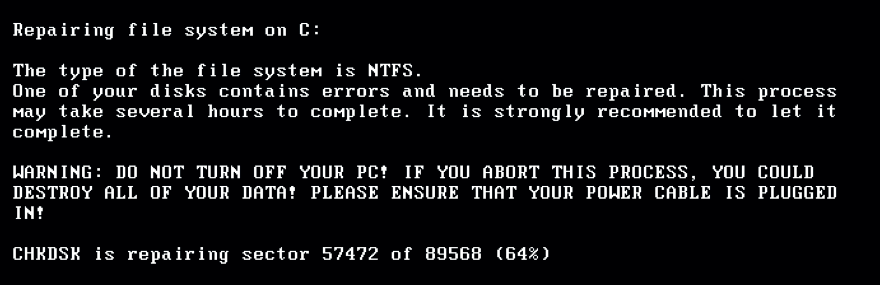
After that, a redemption window is displayed on the screen.
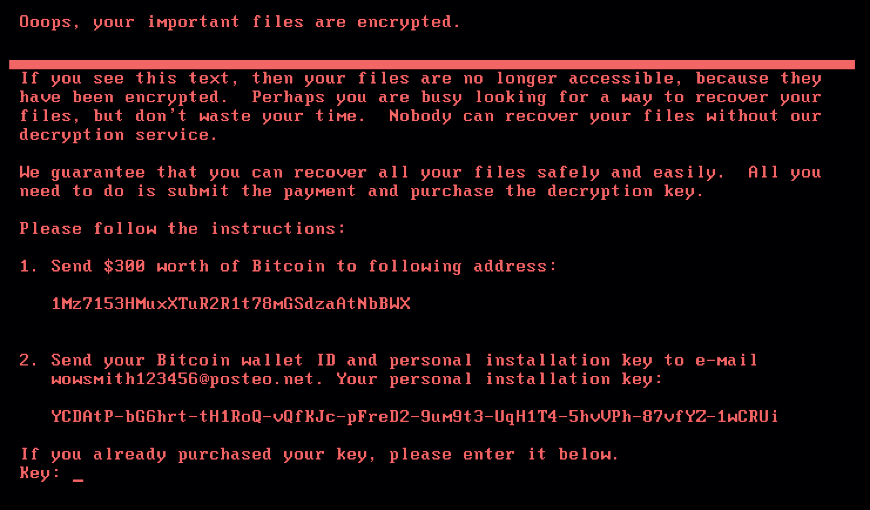
Spread
This time we saw various methods of penetrating and spreading the threat in networks:
• Attack against update system in MeDoc, a popular electronic service
document circulation in Ukraine (this country was hit hard by the attack)
• ETERNALBLUE: This threat variant uses code that exploits a vulnerability,
published by Microsoft on March 14, 2017 and described in MS17-010.
• PSEXEC: Includes remote execution on the system using the PSEXEC command.
• WMI: Contains remote execution on the system using the WMI command
General analysis of samples
Sample 1: 7e37ab34ecdcc3e77e24522ddfd4852d
We did not see the direction of entry. But we saw three different techniques for distribution on the internal network:
• EternalBlue

• PSEXEC
v8 = wsprintfW (a2, L ”% s \\\\% s -accepteula -s“, v3, a3);
v9 = wsprintfW (& a2 [v8], L ”-d C: \\ Windows \\ System32 \\ rundll32.exe \” C: \\ Windows \\% s \ ”, # 1“, & v14)
+ v8;
• WMI
wbem \ wmic.exe% s / node: "% ws" / user: "% ws" / password: "% ws" process call create “C: \ Windows
\ System32 \ rundll32.exe \ ”C: \ Windows \% s \” # 1

Sample 2: 71b6a493388e7d0b40c83ce903bc6b04
We have seen that the direction of entry is EZVIT, part of the MeDoc product, a popular system.
electronic document management in Ukraine. This is confirmed by the execution of GoldenEye through this program:

We will continue to analyze patterns associated with this cyber attack, and will provide new information as it arrives.
Tips and tricks
• Be careful of documents attached to unknown emails.
senders. Analyze all incoming and outgoing emails to detect threats, and
filter executables to prevent them from reaching the end user.
• Update your operating systems, software and firmware on all devices.
• This time we discovered the use of ETERNALBLUE, and therefore we recommend that you download and install the following patch on all computers in your network:
technet.microsoft.com/en-us/library/security/ms17-010.aspx
• Trust only next-generation endpoint security solutions, such as Adaptive Defense and Adaptive Defense 360 .
• If you are already a client of Adaptive Defense, and in the case of large-scale attacks, set the mode of operation in the Adaptive Defense solution to Lock: run only those processes that Panda Security has classified as reliable.
• Periodically make backup copies and check that they work correctly and do not
connected to the network.
Source: https://habr.com/ru/post/331886/
All Articles