WannaCry and Petya - how does the center for monitoring and response to cyber attacks in case of global incidents work?
In the light of the latest story with the Petya encryption virus, we don’t want to tell you again how to protect against it, there are already dozens of such recommendations on the Internet. We would like to share how SOC works in this case, what steps it should take to prevent and respond to global incidents.
Preventive measures
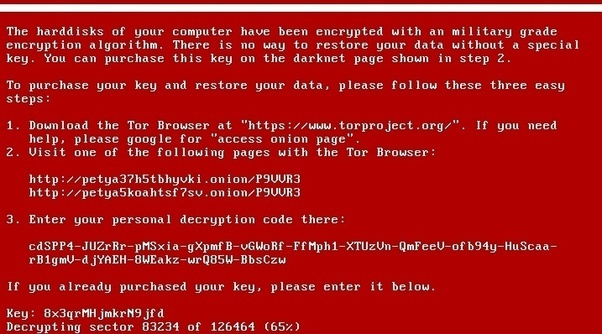
Petya, like its predecessor WannaCry, exploits the EternalBlue vulnerability, but is not limited to it, so those companies that have installed the appropriate updates from Microsoft have increased their security level.
Attack and response
15:00 MSK The first reports of an attack on large organizations. Solar JSOC analysts begin monitoring in search of details, and at the same time analyzing the situation with customers. The first line is switched to a state of heightened vigilance, manual monitoring of IPS, WAF, Anti-DDoS and perimeter network devices is carried out to detect anomalies.
')
In parallel, through partner channels and from the side of anti-virus vendors, fragmentary information begins to arrive that the malicious product Petya is running. The distribution channel is presumably EternalBlue.
The work was divided into several areas:
15:30 Moscow time . The first indicators were obtained - the initial infection of the organization went through mail phishing, there are network indicators and MD5 of the virus body. This information is promptly verified on all customers within 30 minutes. In parallel, service managers make calls to the responsible specialists of the customer.
Retrospective verification for all customers did not give positive positives. Also, all indicators were added to active rules and lists for further tracking of attempts to contact (including unsuccessful ones) at the detected malicious domain and for the rapid detection of infected machines. All network indicators of compromise are set to control access through firewalls and proxies, DNS queries are monitored.
Customers received an alert about the need to block the specified addresses on the network equipment.
15:50 Moscow time . An instruction is created to minimize the risks associated with the spread of Petya. The instructions indicate the main measures:
It is sent to customers.
Gizar Shakirov, Head of IB BASHKOMSNABBANK (PJSC):
At 15:40, we received the first call from the analyst with a warning that there was a massive contamination of the infrastructures of large energy, oil and gas, financial sector and retail companies. The epidemic is very similar to WannaCry, but new distribution channels are possible. The channel of entry, according to the first assumptions, is mail. The service manager warned that further distribution in the infrastructure may occur not only through the operation of EternalBlue, which we were upgraded to.
Also within 10 minutes, a mailing was received from Solar JSOC with the results of the retrospective analysis and network indicators that had to be blacklisted on the perimeter protection. We notified the responsible specialists of the bank in advance, therefore, as soon as the notification came, the external addresses were blocked for 5 minutes.
16:30 Moscow time . The first conclusions about the work of malware.
A dropper consisting of several components initially gets to the host:
Getting to the host, the virus tries to elevate privileges to the System. In case of success - restart and MFT encryption. In the case of failure - file encryption (as a standard crypter).
After some time, the second distribution channel in the infrastructure is revealed - PsExec + Mimikatz. A little later another is remote access to the WMI (Windows Management Instrumentation) console.
The instruction is supplemented with the following information:
Gizar Shakirov, Head of IB BASHKOMSNABBANK (PJSC):
After receiving information about additional distribution methods, critical segments and hosts were temporarily isolated at 135, 445, 1024-1035 ports or placed under special control. Solar JSOC announced that the anti-virus vendor, whose solution is used in the bank, has released signatures to detect well-known Petya samples. A forced update was promptly performed on the entire fleet of protected machines and a full scan was run on critical hosts.
During the following hours, we received information about the functionality of other malware builds. New indicators of compromise were checked in retrospect and put on active control. The duty analyst promptly interacted with the technical specialists of the customers, including at night. All suspicious email attachments were checked with special care.
Gizar Shakirov, Head of IB BASHKOMSNABBANK (PJSC):
At night, we agreed with the colleagues from JSOC an abnormal mode of operation, during which, in addition to incidents related to abnormal network or host activity and virus infections, in addition to the regular notification of the responsible bank specialists, I would immediately call me to organize a quick response and conduct fact checking incident.
Even after the WannaCry epidemic, it became clear that the use of vulnerabilities promulgated (and planned to be published) by a well-known hacker group would be the trend of the near future, and any measures related to monitoring, custom signatures and antivirus work should be considered only as compensating. Therefore, the Solar JSOC operation service continued to work even more intensively with system upgrades, including legacy, for which actual patches appeared in the customer’s infrastructures.
Thanks to all the measures listed above and the active interaction of client specialists and the Solar JSOC team, we managed to avoid any active infections with the Petya epidemic, like the WannaCry epidemic a month earlier.

Preventive measures
Petya, like its predecessor WannaCry, exploits the EternalBlue vulnerability, but is not limited to it, so those companies that have installed the appropriate updates from Microsoft have increased their security level.
Attack and response
15:00 MSK The first reports of an attack on large organizations. Solar JSOC analysts begin monitoring in search of details, and at the same time analyzing the situation with customers. The first line is switched to a state of heightened vigilance, manual monitoring of IPS, WAF, Anti-DDoS and perimeter network devices is carried out to detect anomalies.
')
In parallel, through partner channels and from the side of anti-virus vendors, fragmentary information begins to arrive that the malicious product Petya is running. The distribution channel is presumably EternalBlue.
The work was divided into several areas:
- Alert customers on the first appeared work indicators and events.
- Focus communication with technology and technical partners to share first results on virus analyzes.
- And - somewhat atypically - active tracking of media and vendor forums and CERT to search for additional information and indicators. This part of the work attracted, among other things, our marketing, which monitored the Facebook feed, “exploded” with information about infections.
15:30 Moscow time . The first indicators were obtained - the initial infection of the organization went through mail phishing, there are network indicators and MD5 of the virus body. This information is promptly verified on all customers within 30 minutes. In parallel, service managers make calls to the responsible specialists of the customer.
Retrospective verification for all customers did not give positive positives. Also, all indicators were added to active rules and lists for further tracking of attempts to contact (including unsuccessful ones) at the detected malicious domain and for the rapid detection of infected machines. All network indicators of compromise are set to control access through firewalls and proxies, DNS queries are monitored.
Customers received an alert about the need to block the specified addresses on the network equipment.
15:50 Moscow time . An instruction is created to minimize the risks associated with the spread of Petya. The instructions indicate the main measures:
- Update Windows and ABC databases.
- Closing TCP port 445 where it is possible and does not violate the normal functioning of the services.
- In some cases, it may be effective to protect the MBR from being overwritten.
It is sent to customers.
Gizar Shakirov, Head of IB BASHKOMSNABBANK (PJSC):
At 15:40, we received the first call from the analyst with a warning that there was a massive contamination of the infrastructures of large energy, oil and gas, financial sector and retail companies. The epidemic is very similar to WannaCry, but new distribution channels are possible. The channel of entry, according to the first assumptions, is mail. The service manager warned that further distribution in the infrastructure may occur not only through the operation of EternalBlue, which we were upgraded to.
Also within 10 minutes, a mailing was received from Solar JSOC with the results of the retrospective analysis and network indicators that had to be blacklisted on the perimeter protection. We notified the responsible specialists of the bank in advance, therefore, as soon as the notification came, the external addresses were blocked for 5 minutes.
16:30 Moscow time . The first conclusions about the work of malware.
A dropper consisting of several components initially gets to the host:
- A modified version of the crypto-fiber Misha and Petya.
- A scanner module that detects hosts that are potentially vulnerable to EternalBlue.
- A module that uses the PsExec + Mimikatz bundle for distribution (dumping passwords and distributing to windows machines on the network via the Microsoft remote administration utility, which requires an open 445 port to work).
Getting to the host, the virus tries to elevate privileges to the System. In case of success - restart and MFT encryption. In the case of failure - file encryption (as a standard crypter).
After some time, the second distribution channel in the infrastructure is revealed - PsExec + Mimikatz. A little later another is remote access to the WMI (Windows Management Instrumentation) console.
The instruction is supplemented with the following information:
- Blocking the launch of the software "PSEXEC.EXE" on potentially vulnerable machines.
- As a temporary measure, disable remote access to WMI.
Gizar Shakirov, Head of IB BASHKOMSNABBANK (PJSC):
After receiving information about additional distribution methods, critical segments and hosts were temporarily isolated at 135, 445, 1024-1035 ports or placed under special control. Solar JSOC announced that the anti-virus vendor, whose solution is used in the bank, has released signatures to detect well-known Petya samples. A forced update was promptly performed on the entire fleet of protected machines and a full scan was run on critical hosts.
During the following hours, we received information about the functionality of other malware builds. New indicators of compromise were checked in retrospect and put on active control. The duty analyst promptly interacted with the technical specialists of the customers, including at night. All suspicious email attachments were checked with special care.
Gizar Shakirov, Head of IB BASHKOMSNABBANK (PJSC):
At night, we agreed with the colleagues from JSOC an abnormal mode of operation, during which, in addition to incidents related to abnormal network or host activity and virus infections, in addition to the regular notification of the responsible bank specialists, I would immediately call me to organize a quick response and conduct fact checking incident.
Even after the WannaCry epidemic, it became clear that the use of vulnerabilities promulgated (and planned to be published) by a well-known hacker group would be the trend of the near future, and any measures related to monitoring, custom signatures and antivirus work should be considered only as compensating. Therefore, the Solar JSOC operation service continued to work even more intensively with system upgrades, including legacy, for which actual patches appeared in the customer’s infrastructures.
Thanks to all the measures listed above and the active interaction of client specialists and the Solar JSOC team, we managed to avoid any active infections with the Petya epidemic, like the WannaCry epidemic a month earlier.
Source: https://habr.com/ru/post/331860/
All Articles