How to beat the Petya virus
Following the sensational campaign of the cipher virus WannaCry, which was recorded in May of this year, on June 27, more than 80 companies in Russia and Ukraine fell victim to a new attack using the extortionist cipher Petya. And this campaign was not related to WannaCry at all. Experts at Positive Technologies presented a detailed analysis of the new malware and made recommendations to combat it.
Ukrainian, Russian and international companies, in particular, Novaya Pochta, Zaporozhieoblenergo, Dneproenergo, Oschadbank, media holding TRK Lux, Mondelēz International, TESA, Nivea, Mars, operators LifeCell, UkrTeleCom, Kievstar and many other organizations have already become victims of the extortionist. In Kiev, including some ATMs and checkout terminals in stores, were infected. It was in Ukraine that the first attacks were recorded.
')
An analysis of the ransomware sample conducted by our experts showed that Petya’s principle of operation is based on encrypting the master boot record (MBR) of the boot sector of a disk and replacing it with its own. This record is the first sector on the hard disk, it contains the partition table and the loader program, which reads from this table information about which partition of the hard disk the system will boot from. The original MBR is stored in the 0x22nd disk sector and is encrypted using a XOR byte operation with 0x07.
After launching the malicious file, a task is created to restart the computer, delayed for 1-2 hours, at which time you can run the bootrec / fixMbr command to restore the MBR and restore the OS to work. Thus, it is possible to start the system even after its compromise, but it will not be possible to decrypt the files. Each disk generates its own AES key, which exists in memory until encryption is completed. It is encrypted using the RSA public key and deleted. Restoring content after completion requires knowledge of the private key, thus, without knowing the key, data cannot be recovered. Presumably, the malware encrypts files to a maximum of 15 directories. That is, files nested to a greater depth are safe (at least for this modification of the cryptographer).
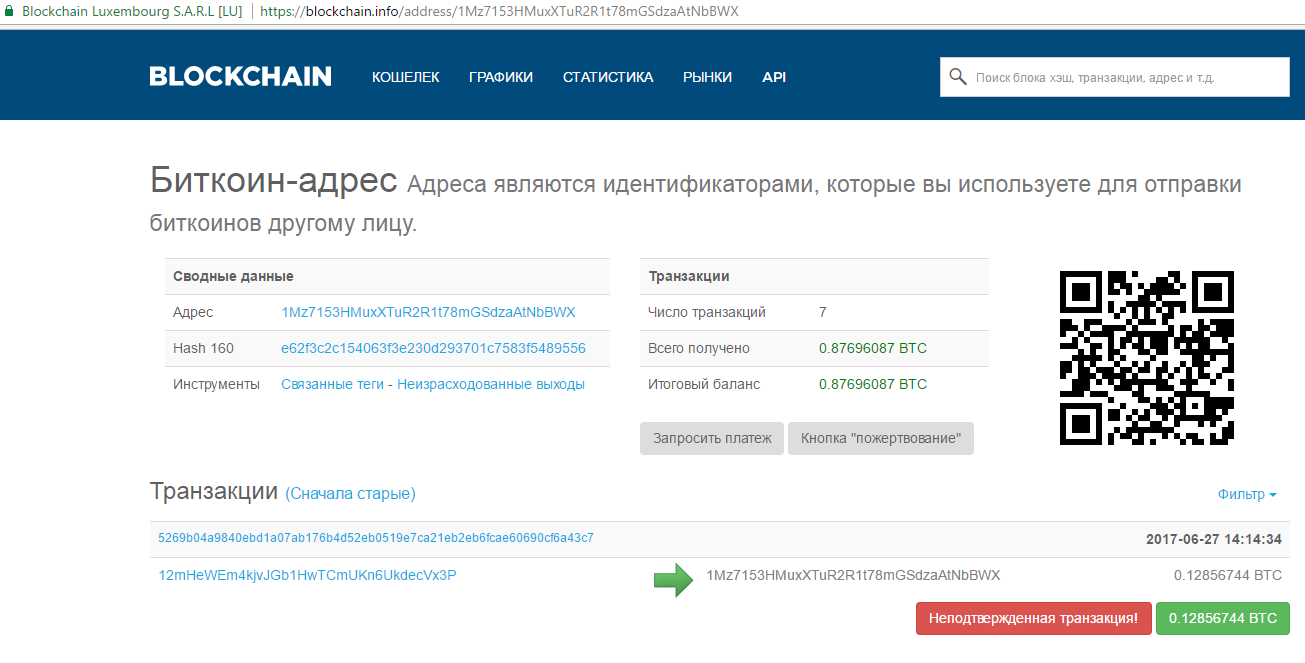
If the disks were successfully encrypted after a reboot, a window is displayed on the screen with a message about the requirement to pay a ransom of $ 300 (as of June 27, 2017 - approximately 0.123 bitcoins) to obtain the file unlock key. For the transfer of money specified bitcoin wallet 1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX . A few hours after the start of the attack, the wallet already receives transactions that are multiples of the requested amount - some victims chose to pay the ransom, not waiting for the researchers to study the malware and try to find a file recovery tool.
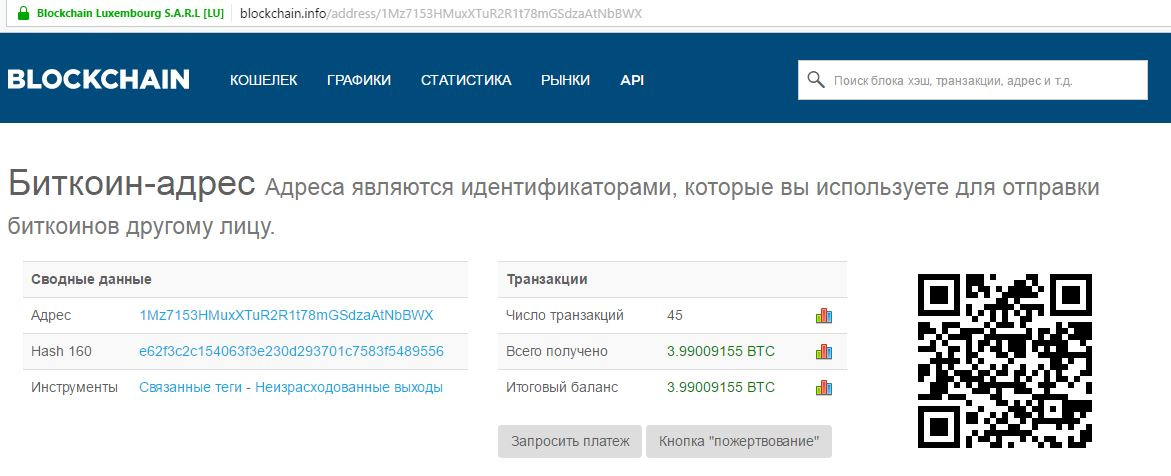
At the moment, the number of transactions has increased to 45.
Petya uses 135, 139, 445 TCP ports for distribution (using SMB and WMI services). Distribution within the network to other nodes occurs by several methods: using Windows Management Instrumentation (WMI) and PsExec , as well as using an exploit that exploits the MS17-010 vulnerability ( EternalBlue ). WMI is a technology for centrally managing and monitoring the work of various parts of the computer infrastructure running on the Windows platform. PsExec is widely used to administer Windows and allows you to run processes on remote systems. However, to use these utilities, you must have local administrator privileges on the victim's computer, which means that the encryption officer can continue to distribute only from those devices whose user has the maximum privileges of the OS. The EternalBlue exploit allows you to get maximum privileges on a vulnerable system. The cryptographer also uses the publicly available Mimikatz utility to open the credentials of all Windows users, including local administrators and domain users. Such a toolkit allows Petya to maintain performance even in those infrastructures where the WannaCry lesson was taken into account and the corresponding security updates were installed, which is why the encryption tool is so effective .
As part of testing for penetration of modern corporate infrastructures, Positive Technologies experts regularly demonstrate the possibility of using the EternalBlue exploit (in 44% of the work in 2017), as well as the successful use of the Mimikatz utility to develop the attack vector to gain full control over the domain (in each project).
Thus, Petya has the functionality that allows it to spread to other computers, and this process is avalanche-like. This allows the cryptographer to compromise including the domain controller and develop an attack before gaining control over all nodes of the domain, which is equivalent to the complete compromise of the infrastructure.
We reported on the existing threat of compromise more than a month ago in alerts about the WannaCry attack and gave recommendations on how to identify vulnerable systems, how to protect them and what to do if an attack has already occurred. Additional recommendations we will give in this article. In addition, our company has developed a free utility WannaCry_Petya_FastDetect for automated detection of infrastructure vulnerabilities. MaxPatrol detects this vulnerability in both Audit mode and Pentest mode. Detailed instructions are indicated in our recommendations . In addition, the MaxPatrol SIEM set up the appropriate correlation rules to identify the Petya attack.
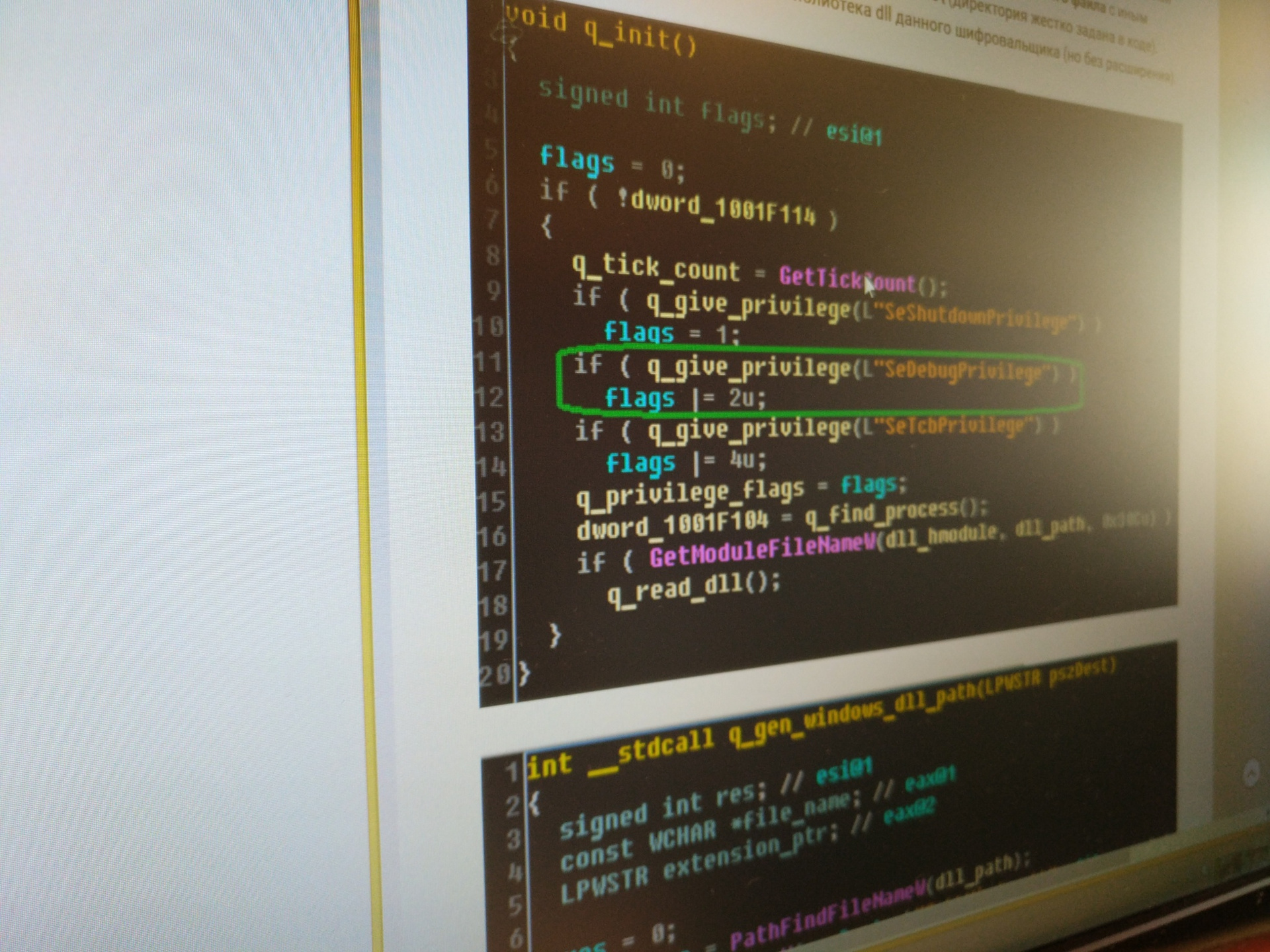
Positive Technologies experts have revealed “kill-switch” - the ability to disable cipher crawler locally. If the process has administrative privileges in the OS, then before replacing the MBR, the cryptographer checks for the presence of the perfc file (or another empty file with a different name) without an extension in the C: \ Windows \ directory (the directory is hard coded in the code). This file has the same name as the dll library of this cryptographer (but without the extension).
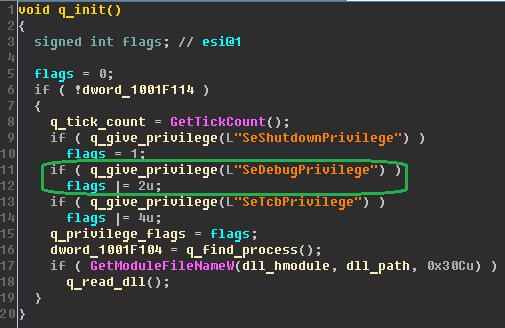
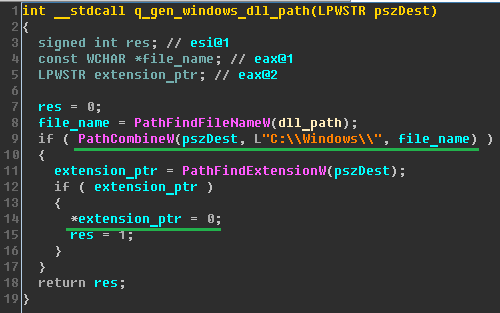
The presence of such a file in the specified directory may be one of the indicators of compromise. If the file is present in this directory, then the execution of the malware is completed, thus creating a file with the correct name can prevent the MBR from being spoofed and further encryption.

If the cryptographer does not detect such a file during the scan, then the file is created and the process of running the malware runs. Presumably, this happens so that the MBR substitution process does not start again.
On the other hand, if the process does not initially have administrative privileges, the encryption officer will not be able to check for the presence of an empty file in the C: \ Windows \ directory, and the file encryption process will still start, but without replacing the MBR and restarting the computer.
In order not to become a victim of such an attack, you must first update the software used to the latest versions, in particular, install all the latest updates for MS Windows. In addition, it is necessary to minimize user privileges on workstations.
If the infection has already occurred, we do not recommend paying money to attackers. The e- mail address of the violators wowsmith123456@posteo.net was blocked, and even if the ransom payment was made, the key for decrypting files will most likely not be received. To prevent the encoder from spreading on the network, it is recommended to turn off other computers that have not been infected, disconnect infected nodes from the network and remove images of compromised systems. In case researchers find a way to decrypt files, locked data can be recovered in the future. In addition, this image can be used to analyze the encoder, which will help researchers in their work.
In the long term, it is recommended to develop a system of regular staff training to raise their awareness of information security issues, based on the demonstration of practical examples of potential attacks on the company's infrastructure using social engineering methods. It is necessary to regularly check the effectiveness of such trainings. It is also necessary to install anti-virus software on all computers with a self-defense function, providing for entering a special password to disable or change settings. In addition, it is necessary to ensure regular updates of software and operating systems on all nodes of the corporate infrastructure, as well as an effective process of managing vulnerabilities and updates. Regular audits of information security and penetration testing will allow timely identification of existing weaknesses in the protection and vulnerability of systems. Regular monitoring of the perimeter of the corporate network will allow you to monitor the Internet interfaces of the network services available on the network and make adjustments to the firewall configuration on time. For the timely detection and suppression of an already occurring attack, it is necessary to monitor the internal network infrastructure, for which it is recommended to use the SIEM class system.
The following indicators can be used to detect Petya attacks in the infrastructure:
IDS / IPS rules triggered:
Signatures:

Ukrainian, Russian and international companies, in particular, Novaya Pochta, Zaporozhieoblenergo, Dneproenergo, Oschadbank, media holding TRK Lux, Mondelēz International, TESA, Nivea, Mars, operators LifeCell, UkrTeleCom, Kievstar and many other organizations have already become victims of the extortionist. In Kiev, including some ATMs and checkout terminals in stores, were infected. It was in Ukraine that the first attacks were recorded.
')
An analysis of the ransomware sample conducted by our experts showed that Petya’s principle of operation is based on encrypting the master boot record (MBR) of the boot sector of a disk and replacing it with its own. This record is the first sector on the hard disk, it contains the partition table and the loader program, which reads from this table information about which partition of the hard disk the system will boot from. The original MBR is stored in the 0x22nd disk sector and is encrypted using a XOR byte operation with 0x07.
After launching the malicious file, a task is created to restart the computer, delayed for 1-2 hours, at which time you can run the bootrec / fixMbr command to restore the MBR and restore the OS to work. Thus, it is possible to start the system even after its compromise, but it will not be possible to decrypt the files. Each disk generates its own AES key, which exists in memory until encryption is completed. It is encrypted using the RSA public key and deleted. Restoring content after completion requires knowledge of the private key, thus, without knowing the key, data cannot be recovered. Presumably, the malware encrypts files to a maximum of 15 directories. That is, files nested to a greater depth are safe (at least for this modification of the cryptographer).
If the disks were successfully encrypted after a reboot, a window is displayed on the screen with a message about the requirement to pay a ransom of $ 300 (as of June 27, 2017 - approximately 0.123 bitcoins) to obtain the file unlock key. For the transfer of money specified bitcoin wallet 1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX . A few hours after the start of the attack, the wallet already receives transactions that are multiples of the requested amount - some victims chose to pay the ransom, not waiting for the researchers to study the malware and try to find a file recovery tool.

At the moment, the number of transactions has increased to 45.
Petya uses 135, 139, 445 TCP ports for distribution (using SMB and WMI services). Distribution within the network to other nodes occurs by several methods: using Windows Management Instrumentation (WMI) and PsExec , as well as using an exploit that exploits the MS17-010 vulnerability ( EternalBlue ). WMI is a technology for centrally managing and monitoring the work of various parts of the computer infrastructure running on the Windows platform. PsExec is widely used to administer Windows and allows you to run processes on remote systems. However, to use these utilities, you must have local administrator privileges on the victim's computer, which means that the encryption officer can continue to distribute only from those devices whose user has the maximum privileges of the OS. The EternalBlue exploit allows you to get maximum privileges on a vulnerable system. The cryptographer also uses the publicly available Mimikatz utility to open the credentials of all Windows users, including local administrators and domain users. Such a toolkit allows Petya to maintain performance even in those infrastructures where the WannaCry lesson was taken into account and the corresponding security updates were installed, which is why the encryption tool is so effective .
As part of testing for penetration of modern corporate infrastructures, Positive Technologies experts regularly demonstrate the possibility of using the EternalBlue exploit (in 44% of the work in 2017), as well as the successful use of the Mimikatz utility to develop the attack vector to gain full control over the domain (in each project).
Thus, Petya has the functionality that allows it to spread to other computers, and this process is avalanche-like. This allows the cryptographer to compromise including the domain controller and develop an attack before gaining control over all nodes of the domain, which is equivalent to the complete compromise of the infrastructure.
We reported on the existing threat of compromise more than a month ago in alerts about the WannaCry attack and gave recommendations on how to identify vulnerable systems, how to protect them and what to do if an attack has already occurred. Additional recommendations we will give in this article. In addition, our company has developed a free utility WannaCry_Petya_FastDetect for automated detection of infrastructure vulnerabilities. MaxPatrol detects this vulnerability in both Audit mode and Pentest mode. Detailed instructions are indicated in our recommendations . In addition, the MaxPatrol SIEM set up the appropriate correlation rules to identify the Petya attack.
Positive Technologies experts have revealed “kill-switch” - the ability to disable cipher crawler locally. If the process has administrative privileges in the OS, then before replacing the MBR, the cryptographer checks for the presence of the perfc file (or another empty file with a different name) without an extension in the C: \ Windows \ directory (the directory is hard coded in the code). This file has the same name as the dll library of this cryptographer (but without the extension).


The presence of such a file in the specified directory may be one of the indicators of compromise. If the file is present in this directory, then the execution of the malware is completed, thus creating a file with the correct name can prevent the MBR from being spoofed and further encryption.

If the cryptographer does not detect such a file during the scan, then the file is created and the process of running the malware runs. Presumably, this happens so that the MBR substitution process does not start again.
On the other hand, if the process does not initially have administrative privileges, the encryption officer will not be able to check for the presence of an empty file in the C: \ Windows \ directory, and the file encryption process will still start, but without replacing the MBR and restarting the computer.
In order not to become a victim of such an attack, you must first update the software used to the latest versions, in particular, install all the latest updates for MS Windows. In addition, it is necessary to minimize user privileges on workstations.
If the infection has already occurred, we do not recommend paying money to attackers. The e- mail address of the violators wowsmith123456@posteo.net was blocked, and even if the ransom payment was made, the key for decrypting files will most likely not be received. To prevent the encoder from spreading on the network, it is recommended to turn off other computers that have not been infected, disconnect infected nodes from the network and remove images of compromised systems. In case researchers find a way to decrypt files, locked data can be recovered in the future. In addition, this image can be used to analyze the encoder, which will help researchers in their work.
In the long term, it is recommended to develop a system of regular staff training to raise their awareness of information security issues, based on the demonstration of practical examples of potential attacks on the company's infrastructure using social engineering methods. It is necessary to regularly check the effectiveness of such trainings. It is also necessary to install anti-virus software on all computers with a self-defense function, providing for entering a special password to disable or change settings. In addition, it is necessary to ensure regular updates of software and operating systems on all nodes of the corporate infrastructure, as well as an effective process of managing vulnerabilities and updates. Regular audits of information security and penetration testing will allow timely identification of existing weaknesses in the protection and vulnerability of systems. Regular monitoring of the perimeter of the corporate network will allow you to monitor the Internet interfaces of the network services available on the network and make adjustments to the firewall configuration on time. For the timely detection and suppression of an already occurring attack, it is necessary to monitor the internal network infrastructure, for which it is recommended to use the SIEM class system.
The following indicators can be used to detect Petya attacks in the infrastructure:
- C: \ Windows \ perfs
- Task in Windows Scheduler with an empty name and action (reboot)
- "% WINDIR% \ system32 \ shutdown.exe / r / f"
IDS / IPS rules triggered:
- msg: "[PT Open] Unimplemented Trans2 Sub-Command code. Possible ETERNALBLUE (WannaCry, Petya) tool"; sid: 10001254; rev: 2;
- msg: "[PT Open] ETERNALBLUE (WannaCry, Petya) SMB MS Windows RCE"; sid: 10001255; rev: 3;
- msg: "[PT Open] Trans2 Sub-Command 0x0E. Likely ETERNALBLUE (WannaCry, Petya) tool"; sid: 10001256; rev: 2;
- msg: "[PT Open] Petya ransomware perfc.dat component"; sid: 10001443; rev: 1
- msg: "[PT Open] SMB2 Create PSEXESVC.EXE"; sid: 10001444; rev: 1
Signatures:
Source: https://habr.com/ru/post/331858/
All Articles