Petya.A, Petya.C, PetrWrap or PetyaCry? New virus threat for companies in Russia and Ukraine
Not so long ago, we released an article on integrated proactive protection against targeted attacks and encryption viruses, which included the latest major virus infections of malware such as Ransomware. We can add another example to the piggy bank.
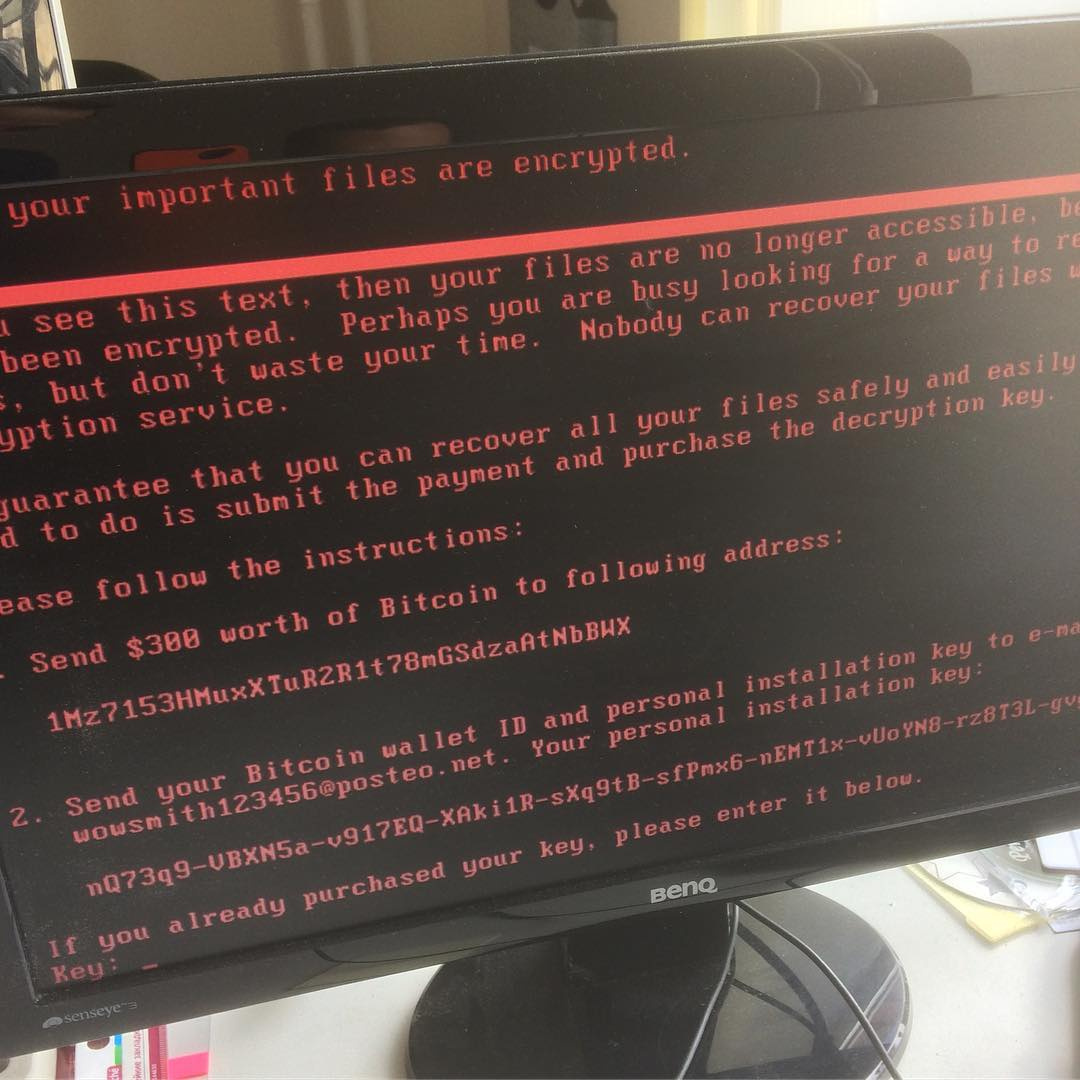
June 27, 2017 registered a massive hacker attack on servers and workstations of networks of large Russian, Ukrainian companies and organizations around the world, the list of which is being replenished continuously and more and more similar photos appear on social networks:
')
The virus is a modification of the 2016 extortioner Petya.A / Petya.C, which has been acclaimed in 2016. The new Petya.C virus is spreading in several ways:
When a user opens malware attached to an e-mail disguised as a document (these can be Order-20062017.doc files (or another date), myguy.xls, or modifications), the computer calls 84.200.16 [.] 242, downloading the malicious the Myguy.xls file to the root of the C: \ drive. After downloading, the following operations occur:
After the reboot, the user is shown a window demanding payment of $ 300 in Bitcoin equivalent to the wallet 1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX. At 23:30, the attackers had already transferred 3.277 BTC (paid by 31 people), at the current rate (at the time of publication, 1 BTC is equivalent to $ 2,409) it is $ 7894.
How to protect yourself from data encryption?
The first step is to update the anti-virus software signatures on servers and workstations (if anti-virus software is available) - the signature database should be updated on 06/27/2017 no earlier than 20:00 (the first mentions of adding Petya.C to the signature database started arriving at 19h). Here is a list of malicious files and their hash values:
On already infected systems, the specified files are located in the file system in the following folders:
In the malware's code, experts found an interesting opportunity to protect against Petya.C by manually creating the C: \ Windows \ perfc.dll file using a standard Notepad.
In addition to updating antivirus software, we recommend that you apply additional protection measures:
In no case do not transfer money to the account of the attackers, their email is blocked, and in any case you will not be able to recover the data in this way.
When infecting a workstation / server on the network, it is necessary to take appropriate measures to eliminate malware:
Data from hard drives encrypted with the old Petya virus was recovered as follows . The descrambler for the old version of Petya was published on Github . Decoder for the new version of Petya.C yet.
In the course of distribution over the network, a version of the Microsoft Windows Sysinternals tool, PsExec, is supposedly used.
There is a SIGMA rule for detecting PsExec usage, it can be automatically converted to a Splunk and ElasticSearch request:
The reason for the wide spread of the virus is the failure to implement the basic necessary measures to protect against targeted attacks of this kind:
Organizational measures cannot provide reliable and effective protection against targeted attacks and extortionate software; therefore, a set of technical measures is required, which we described in our previous article.
Author: Evgeny Borodulin, Chief Architect, Informzaschita
e.borodulin@infosec.ru
June 27, 2017 registered a massive hacker attack on servers and workstations of networks of large Russian, Ukrainian companies and organizations around the world, the list of which is being replenished continuously and more and more similar photos appear on social networks:

')
The virus is a modification of the 2016 extortioner Petya.A / Petya.C, which has been acclaimed in 2016. The new Petya.C virus is spreading in several ways:
- by exploiting vulnerabilities in SMB MS17-010 (similar to the May Wanna Cry);
- by directed emailing malware
- vulnerability used to execute malicious code: CVE-2017-0199
- used vulnerability to spread and infect: CVE-2017-0144 , aka EternalBlue
When a user opens malware attached to an e-mail disguised as a document (these can be Order-20062017.doc files (or another date), myguy.xls, or modifications), the computer calls 84.200.16 [.] 242, downloading the malicious the Myguy.xls file to the root of the C: \ drive. After downloading, the following operations occur:
- opening a malicious file using the utility C: \ Windows \ System32 \ mshta.exe;
- cipher loader download at french-cooking [.] com;
- Files appear on the computer: C: \ Windows \ perfc.dat, C: \ myguy.xls.hta
- connecting the infected computer to the addresses 111.90.139 [.] 247, coffeeinoffice [.] xyz;
- spreading the virus over the network through TCP ports: 1024-1035, 135, 445 using the vulnerability CVE-2017-0144;
- infection MBR (master boot record Windows). If the MBR infection is successful (for this, the virus needs to obtain local administrator privileges, which allows to realize a known vulnerability in SMB), the computer issues a blue screen of death Windows and reboots, the encrypter loads on reboot and the encryption of the entire hard disk begins the screen with the standard procedure for analyzing the hard disk in Windows in case of an unexpected failure is displayed - Check Disk.
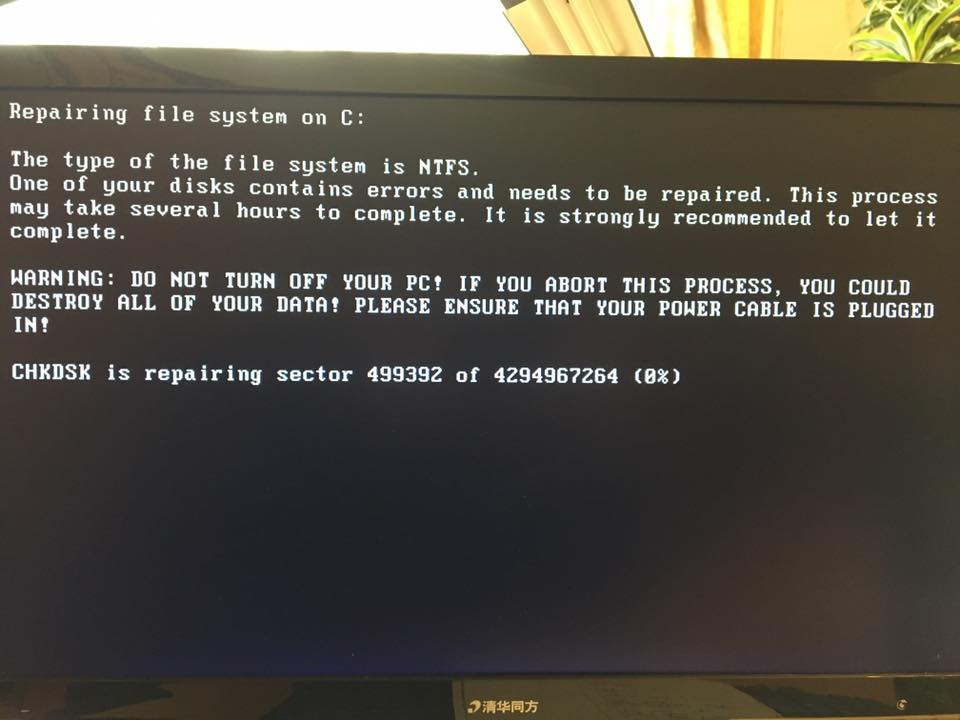
In case the virus fails to obtain local administrator rights and infect the MBR partition, it launches the file encryption utility on the disk, with the exception of the Windows system directory, as well as folders containing browser files (unlike WannaCry, which scanned the system and encrypted certain files). formats), similar to the behavior of the old extortionist Mischa - this behavior was observed in laboratory studies, the vast majority of victims were subjected to full disk encryption and blocking access to the system after restarting ki.
After the reboot, the user is shown a window demanding payment of $ 300 in Bitcoin equivalent to the wallet 1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX. At 23:30, the attackers had already transferred 3.277 BTC (paid by 31 people), at the current rate (at the time of publication, 1 BTC is equivalent to $ 2,409) it is $ 7894.
How to protect yourself from data encryption?
The first step is to update the anti-virus software signatures on servers and workstations (if anti-virus software is available) - the signature database should be updated on 06/27/2017 no earlier than 20:00 (the first mentions of adding Petya.C to the signature database started arriving at 19h). Here is a list of malicious files and their hash values:
- Order-20062017.doc file, size 6215 bytes, SHA1: 101CC1CB56C407D5B9149F2C3B8523350D23BA84, MD5: 415FE69BF
- 32634CA98FA07633F4118E1, SHA256: FE2E5D0543B4C8769E401EC216D78A5A3547DFD426FD47E097DF04A5F7D6D206;
- file myguy.xls, size is 13893 bytes, SHA1: 736752744122A0B5EE4B95DDAD634DD225DC0F73, MD5: 0487382A4DAF8EB9660F1C67E30F8B25, EE29B9C01318A1E23836B9494Pfeyfends;
- bcpd
On already infected systems, the specified files are located in the file system in the following folders:
- C: \ Windows \ perfc.dat
- C: \ myguy.xls.hta
- % APPDATA% \ 10807.exe
In the malware's code, experts found an interesting opportunity to protect against Petya.C by manually creating the C: \ Windows \ perfc.dll file using a standard Notepad.
In addition to updating antivirus software, we recommend that you apply additional protection measures:
- Manually block requests to resources on the Internet (brackets near points are inserted so that there are no hyperlinks):
- 84.200.16 [.] 242
- 84.200.16 [.] 242 / myguy.xls
- french-cooking [.] Com / myguy.exe
- 111.90.139 [.] 247
- COFFEINOFFICE [.] XYZ - If there are already infected workstations or servers on the network, you should disable TCP ports 1024-1035, 135 and 445.
- If the workstation is already infected and the user sees the “blue screen of death for Windows”, the computer starts to reboot itself by running the Check Disk utility, it is urgent to turn it off via power , in this case the data on the hard disk will not be encrypted .
- Install security update for Windows KB4013389 dated March 14, 2017 (see Microsoft Security Bulletin MS17-010). Download the update by the link .
On computers with outdated Windows XP and Windows 2003, you need to install security patches manually by downloading them from direct links:
- Windows XP SP3
- Windows Server 2003 x86
- Windows Server 2003 x64 - Install security update for Microsoft Office. Download updates for your version by the link .
- If it is impossible to install security updates, disable the SMB v1 / v2 / v3 protocol on workstations and servers in accordance with the instructions .
- If you have NGFW / NGTP / IPS protection, configure blocking attacks that exploit EternalBlue (MS17-010)
What to do after infection?
In no case do not transfer money to the account of the attackers, their email is blocked, and in any case you will not be able to recover the data in this way.
When infecting a workstation / server on the network, it is necessary to take appropriate measures to eliminate malware:
- Disconnect the infected machine from the local network;
- When an MBR is infected, in some cases it is possible to recover using bootrec / RebuildBcd, bootrec / fixMbr, bootrec / fixboot;
- If there is no backup, make a backup of the encrypted disk (if a decoder appears, data can be restored. Hope is instilled by the previous XData malware extortionist previous large-scale attack in Ukraine - the creator of the virus published the encryption keys a few days after the spread of the virus, promptly appeared Software for data decryption);
- Boot from the boot disk / flash drive, install the system, fully formatting the encrypted hard drive;
- Install the latest Windows security updates ( KB4013389 is required );
- Install antivirus software, update the signature database;
- Restore data from backup (in case of backup of unencrypted data, before infection).
Data from hard drives encrypted with the old Petya virus was recovered as follows . The descrambler for the old version of Petya was published on Github . Decoder for the new version of Petya.C yet.
Detection of the spread of the virus over the network
In the course of distribution over the network, a version of the Microsoft Windows Sysinternals tool, PsExec, is supposedly used.
There is a SIGMA rule for detecting PsExec usage, it can be automatically converted to a Splunk and ElasticSearch request:
title: PsExec tool execution on destination host
status: experimental
description: Detect PsExec installation and execution events (service and Sysmon)
author: Thomas Patzke
reference: www.jpcert.or.jp/english/pub/sr/ir_research.html
logsource:
product: windows
detection:
service_installation:
EventID: 7045
ServiceName: 'PSEXESVC'
ServiceFileName: '* \ PSEXESVC.exe'
service_execution:
EventID: 7036
ServiceName: 'PSEXESVC'
sysmon_processcreation:
EventID: 1
Image: '* \ PSEXESVC.exe'
User: 'NT AUTHORITY \ SYSTEM'
condition: service_installation or service_execution or sysmon_processcreation
falsepositives:
- unknown
level: low
An epidemic again?
The reason for the wide spread of the virus is the failure to implement the basic necessary measures to protect against targeted attacks of this kind:
- timely update of system software;
- raising awareness of employees in the field of information security and the formation of the principles of safe work with email.
Organizational measures cannot provide reliable and effective protection against targeted attacks and extortionate software; therefore, a set of technical measures is required, which we described in our previous article.
Author: Evgeny Borodulin, Chief Architect, Informzaschita
e.borodulin@infosec.ru
Source: https://habr.com/ru/post/331788/
All Articles