Hosting provider paid a million dollars to ransomware hackers

On June 10, NAYANA, a South Korean hosting company, fell victim to the Erebus ransomware attack (detected by Trend Micro as RANSOM_ELFEREBUS.A). As a result, 153 Linux servers and more than 3,400 business sites hosted by the hosting provider were infected.
In a message published on the NAYANA website on June 12, the company reported that the attackers demanded an unprecedented ransom of 550 Bitcoins (BTC) or $ 1.62 million for decrypting files on all infected servers. Here are some of the negotiations with the extortionists:
My boss told me to give you a good price, since you buy a lot of cars,
550 BTC
If you do not have enough money, you need to take a loan.
')
You have 40 employees,
The annual salary of each employee is 30,000 US dollars
All employees 30 000 * 40 = $ 1 200 000
All 550BTC servers = $ 1,620,000
If you can not pay, you are bankrupt.
You will have to look into the eyes of your children, wife, customers and employees.
You will also lose your reputation and business.
You will get a lot of lawsuits.
Later on June 14, NAYANA announced an agreement on payment by installments in the amount of 397.6 BTC (about $ 1.01 million as of June 19, 2017). On June 17, the company announced that the second of the three payments was made. On June 18, NAYANA began restoring the server in batches. There are currently database errors on some of the second batch servers. The third payment will be paid after successful recovery of the first and second batch of servers.
Although this is not comparable in terms of the ransom amount, the case resembles what happened to a hospital in Kansas, whose employees did not receive full access to the encrypted files after the payment. Instead, the extortionist demanded redemption.
Erebus was first seen in September 2016, when it was distributed through malicious advertising . It reappeared in February 2017, already using a method that bypassed Windows account control. Here are some of the technical details that are available on the Linux version of Erebus:
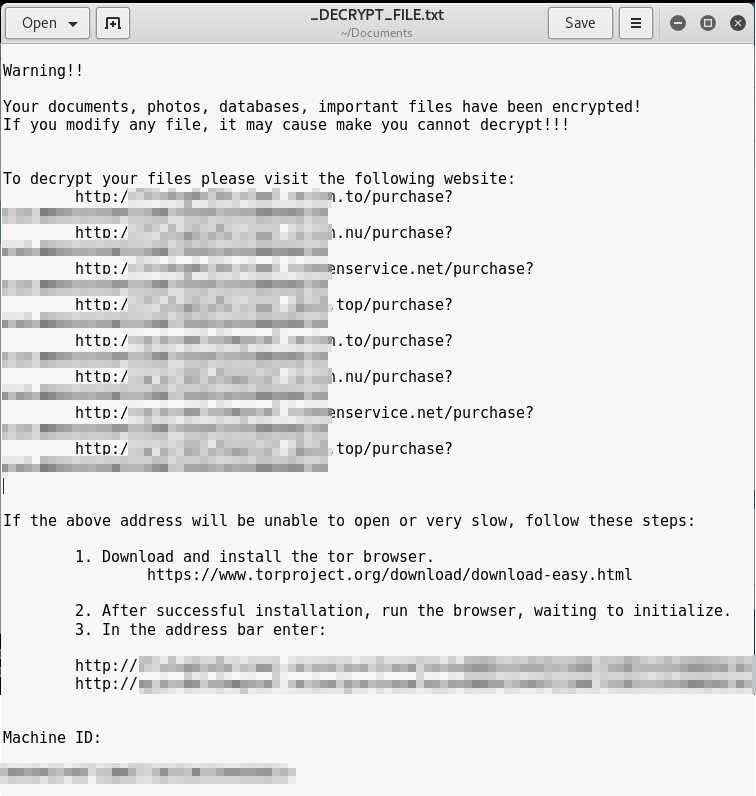
Figure 1: Erebus has a multilingual redemption notice (English version above)

Figure 2: A demo video frame from intruders showing how to decrypt files
Possible vector of virus attacks
Regarding how Linux systems get infected, we can only assume that Erebus may have used the Linux exploit. For example, based on open source information, the researchers found that the NAYANA site runs on the Linux 2.6.24.2 kernel, which was compiled back in 2008. Therefore, security threats such as DIRTY COW can provide root attackers with access to vulnerable Linux systems.
In addition, the NAYANA website uses outdated versions of Apache 1.3.36 and PHP 5.1.4, both of which were released back in 2006. The version of Apache used by NAYANA runs under the user nobody (uid = 99), which indicates that some previously known exploits could also be used in the attack.
Figure 3: Erebus Linux Rasomware
It is worth noting that this virus extortionist is limited in geographical coverage and, in fact, attacks are concentrated in South Korea. However, data from the VirusTotal service show otherwise - several samples were also obtained from Ukraine and Romania. A possible reason could be that they were sent by other information security researchers.
Encryption procedure
Each file encrypted by Erebus will have the following format:
| Header (0x438 bytes) |
| RSA-2048-encrypted original filename |
| RSA-2048-encrypted AES key |
| AES-encrypted RC4 key |
| RC4-encrypted data |
First, each individual file is divided into blocks of 500 kB and scrambled using the RC4 encryption algorithm with randomly generated keys. The RC4 key is then encoded with an AES encryption algorithm. The AES key is encrypted again using the RSA-2048 algorithm, whose public key is stored in a file.
Each file has one public key RSA-2048 common to all. The RSA-2048 keys are generated locally, while the private key required for decryption is stored in an AES key that is encrypted using an additional randomly generated (possibly, also based on Machine ID). The analysis shows that decryption is impossible without obtaining RSA-keys.
Target file types
Typically, encryption is directed to office documents, databases, archives, and multimedia files. This is also characteristic of this version of Erebus, which encrypts 433 file types, but there is also a focus on encrypting the web servers and the data stored on them.
The table below lists the folders that Erebus is looking for.
var / www / - folders where files / data of web sites are stored, and ibdata files are used in MySQL:
| Included directories: | Excluded directories: |
| var / www / | $ / bin / |
| Included files: | $ / boot / |
| ibdata0 | $ / dev / |
| ibdata1 | $ / etc / |
| ibdata2 | $ / lib / |
| ibdata3 | $ / lib64 / |
| ibdata4 | $ / proc / |
| ibdata5 | $ / run / |
| ibdata6 | $ / sbin / |
| ibdata7 | $ / srv / |
| ibdata8 | $ / sys / |
| ibdata9 | $ / tmp / |
| ib_logfile0 | $ / usr / |
| ib_logfile1 | $ / var / |
| ib_logfile2 | /.gem/ |
| ib_logfile3 | /.bundle/ |
| ib_logfile4 | /.nvm/ |
| ib_logfile5 | /.npm/ |
How to protect yourself?
One vulnerable machine on the network is sometimes enough to infect all connected systems and servers. Given the risks to operations, reputation and profits, companies must be proactive in addressing such threats. Recommendations for reducing risks include:
- Backing up important files
- Disable or minimize the number of third-party or unverified repositories
- Application of the principle of least privilege
- Software update of servers and terminals (or use of virtual patches)
- Regular network monitoring
- Check event logs for signs of intrusion or infection
Hash functions of SHA256 RANSOM_ELFEREBUS.A:
0b7996bca486575be15e68dba7cbd802b1e5f90436ba23f802da66292c8a055f
d889734783273b7158deeae6cf804a6be99c3a5353d94225a4dbe92caf3a3d48
We will update this post in case new information is received about the features of the spread of the virus.
Source: https://habr.com/ru/post/331266/
All Articles