On the use of video cameras with character recognition on low-performance computing devices
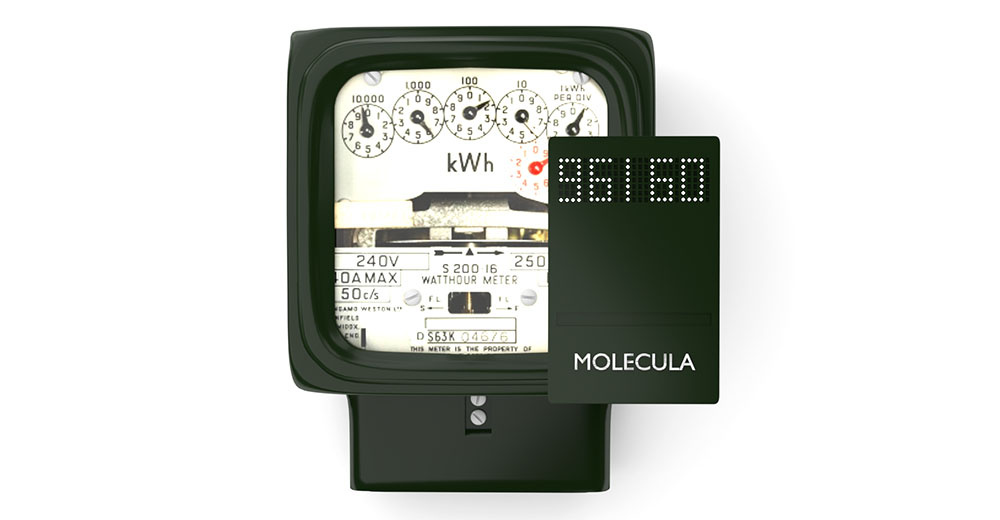
Earlier, the article described the development of a recognition method that allows optical character recognition from video on the fly. As evidence of the effectiveness of the new method, its implementation was used on a device that was not intended for this purpose - the esp8266 microcontroller. During the discussion, the question arose: where can I use devices with recognition on board (reader)? Yes, and at the cost of less than $ 50. It is clear that in the same place where devices are used more expensive, but I would like to discuss other options. We hope for the help of readers in this matter. And what do we see?
1. Readings of metering devices and measuring devices
To date, in matters of accounting and control over the use of various types of resources - electricity, gas, water and heat there has been a very clear trend - the installation of “smart” meters. A smart meter is capable of transmitting measurement results, and the smartest - by the command “from above” to disconnect the consumer from electricity in the event of non-payment, and possibly for other reasons. A smart counter in modern performance plays on the supplier’s side and leaves no freedom to choose for the consumer.
According to the company Ernst & Young, fifteen years of experience in operating smart meters in Europe did not lead to unequivocal conclusions about their effectiveness, although everyone understands that there is something in it. The main effect is achieved by reducing the cost of removal of evidence, to a lesser extent, reduce stolen energy. The pilot project in our country showed much better results - a reduction of losses by 37% in the Kaliningrad region, for example. The question remains, of course, how to remove the remaining 63%.
')
1.1. Taking into account the fact that with an estimated cost of a domestic smart meter of $ 500, its payback period will be 9 years, the following scheme is interesting, allowing to reduce the payback period at least four times:
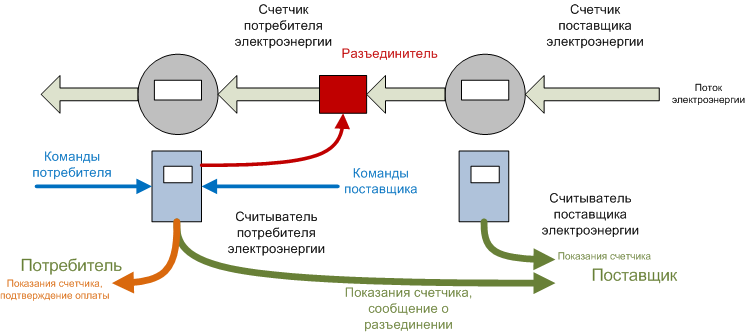
Reading is made through the reader, similar to what is depicted in the very first picture. The scheme contains two counters - the consumer’s counter, which does not need to be changed, and the supplier’s backup counter. The difficulty of synchronizing meter readings, as well as the awareness of continuous monitoring, significantly reduces the possibility of electricity theft.
Besides them, the scheme uses two optical readers with different functionalities: the reader from the supplier’s counter can only transmit readings at a specified time interval, it does not accept commands and works as an AMR generation counter.
The reader of the consumer besides directly reading indications, can carry out interaction with the consumer and the supplier, and also with the network disconnector. This reader can be in two states: 'power is disabled / allowed'. Switching of states is possible only during the payment period at the supplier’s team. If the payment is made, the supplier switches the reader to the disabled state and the next switching of the state is possible only in the next payment period.
Disabling disable is used to prevent erroneous disconnections / connections (including from third parties). Disconnection can occur only in the reader's state of "power is allowed to off".
Thus, the consumer’s reader works as an AMI generation counter — the supplier receives the consumer’s meter readings and current disconnection information from the reader, and the reader receives commands and balance messages. At the same time, the consumer can also receive information on the readings of his meter and the status of the reader based on commands.
The reader allows any meter to be made multi-tariff, since it captures not only the meter readings, but also the moment of reading.
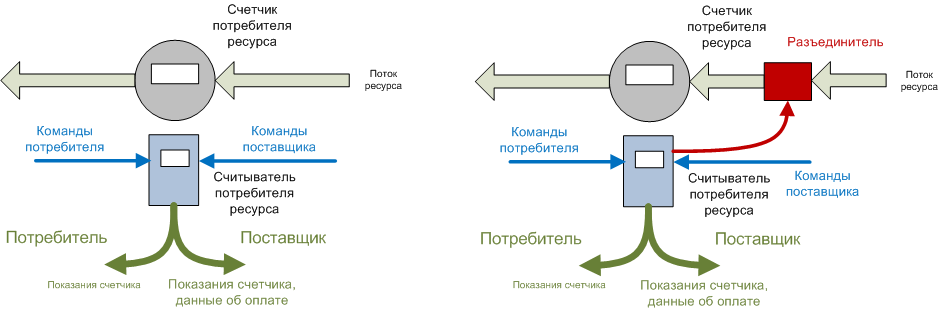
1.2. In addition, we should not forget about other types of resources - gas, water and heat. Since the theft of such resources is more difficult than electricity, then to take readings from metering devices you can get by with simplified schemes.
1.3. Another example of the use of a device is the reading of measuring devices. For example, a large number of trade organizations use scales from various manufacturers, which are equipped with digital terminals that do not have access to communicate with computers. When automating processes in such organizations, it is possible to use the discussed devices to read the necessary information.
2. Identification of the car license plate
Today, the recognition of license plates can be considered a trivial task. There is not only a large number of recognition solutions on the server, but also cameras with onboard recognition: Italian Tattile , Hungarian Arh , German Siemens , British Mav , Chinese HIKVision and Dahua , Russian Iris and many others.
Of course, there are a large number of applications in which cameras with the ability to recognize license plates could be used. For example:
2.1. Parking management. Currently, various presence sensors are being used to track free parking spaces, mounted on or under the vehicle. Such sensors can determine the free / occupied place, but are not able to determine the number of the car that occupies this place. Adding this feature would allow customers to offer new types of service, in addition to identifying the vehicle upon entry / exit:
- post car location;
- booking a parking space with different time frames;
- escorting a car to a parking space with dynamic signs
as it is done in the underground city in Finland;


* Freeze frames were made from the video above.
- the introduction of differentiated payment, depending on the location of the place on
parking; - the organization of the interface between the car and parking subject to binding
phone number to the car number; - receiving information about the amount of payment after the place is vacated and payment by card,
tied to the phone, tied to the car number;
2.2. Manage vehicle refueling. The ability to refuel without leaving the car (in the presence of a tanker) according to the scheme:
- Determining the number of the car approached the column;
- Check the availability of the necessary funds on the card tied to the phone, tied to the car number;
- Request for confirmation of refueling;
- Refueling;
- Automatic payment;

* the basis for the image was taken from the init-e.ru resource.
2.3. Search hijacked car. The low price of the device allows you to dramatically increase the number of surveillance cameras with the ability to recognize on board and build a city-wide system for fixing the movement and / or parking of the car with the desired number, model and color. For such a system, there is no need to send video or individual frames. All the necessary information is a few dozen bytes, so you can set up a very fast data exchange.
2.4. An applied task in which it is necessary to read the readings of measuring devices and determine the number of the vehicle is to organize automated weighing on public roads. In case of overload, the reader transmits the vehicle number to the server, which can send the relevant information to other readers to monitor the movement of the overloaded vehicle.
3. Infrastructure
In all the examples considered, only one side of the data collection systems was considered, namely, the reader. It is clear that this is only part of the system that collects data. This data needs to be somewhere and somehow transferred for processing, which implies a data receiver and a transmission channel. Thus, we get a structure consisting of a data source, two-way transmission channels and data recipients.
3.1. For transmission over a channel, various wireless (Bluetooth, WiFi, GSM, GPRS, LPWAN, ...) and wired (PLC, xDSL) technologies or their combinations are used. The choice of a specific architecture depends on the problem being solved. Since the amount of transmitted data is small, the most convenient technology for long-distance transmission is LPWAN , which include Swift , Sigfox , LoRaWAN , as well as technologies based on LTE-M and NB-IoT cellular networks.
3.2. In most examples, the reader works with one data recipient — the system server; however, in data acquisition systems from metering devices, the reader works with two recipients — the system server and the user. Moreover, for a user who is at a short distance, it is convenient to use channels with WiFi or Bluetooth for data transfer.
3.3. In the examples of parking and refueling management, it is easy to identify a vehicle in the system, however, to provide feedback, communication with the driver of the vehicle is necessary. To do this, you need services at various levels, at which it is possible to register the connection between the car’s number and the driver’s smartphone or equip the vehicles directly with cellular communications. In this case, users registered on such services can send messages to each other on the car number, just as the system can send messages on violations and fines to the car number.
Thus, the existing infrastructure allows to build new services for solving interesting applied problems.
Source: https://habr.com/ru/post/331226/
All Articles