Security Week 24: 95 fixes from Microsoft, the router merges the data with LEDs, for MacOS there is a runner service
 This Tuesday of patches is just a holiday of some kind! Microsoft decided to please admins and released 95 fixes for Windows of all supported versions, Office, Skype, Internet Explorer and Edge. 18 of these are for critical vulnerabilities, including three RCEs. Who does not know, these are the holes that allow you to remotely run the code without authentication, that is, the most dangerous of all. The first two, according to Microsoft, are already under attack.
This Tuesday of patches is just a holiday of some kind! Microsoft decided to please admins and released 95 fixes for Windows of all supported versions, Office, Skype, Internet Explorer and Edge. 18 of these are for critical vulnerabilities, including three RCEs. Who does not know, these are the holes that allow you to remotely run the code without authentication, that is, the most dangerous of all. The first two, according to Microsoft, are already under attack.CVE-2017-8543 is contained in the Windows Search Service (WSS) search engine. Service is convenient, but as it turned out, with a hole. Hacker, connecting via SMB, can totally enslave the system, for example, change, delete files, create new accounts. The problem exists in the current versions of Windows, and in Windows XP and Server 2003. To solve it, Microsoft again released separate patches to unsupported systems. Looks like this is a company habit. All the vendors would do that!
CVE-2017-8464 is a beautiful, if I may say so, hole that allows you to run code with the help of a clever shortcut. It’s enough for the user to see the malicious shortcut in Explorer so that his machine will execute some bad code. The problem exists in operating systems, starting with Windows 7 SP1, the exact list of versions can be seen here . By the way, the vulnerability of the same type used the great and terrible Stuxnet.
CVE-2017-8527 sits in a font library, in the way it handles embedded fonts. Again, total enslavement, this time through the font on the website or in the document. That is, it is enough to go to the website with any text, as long as it is written in a specially designed font so that the hacker can do almost anything with your system. With your level of authority, naturally - a good reason to sit under the ordinary user, and not under the administrator. The list of vulnerable products is long , and you need to patch not only Windows.
')
Researchers forced the router to transfer data by flashing LEDs
 News Research When researchers have nothing to do, they invent fancy ways of hacking into all protected systems. Aerobatics for these gloomy geniuses is to break a computer that is not connected to the Internet. This is quite feasible, thanks to the two-legged carriers of infections, popping flash drives everywhere, but to implement a Trojan on the system is only half the battle. You also need to somehow extract the stolen data, and here the security men do not hold back their imagination.
News Research When researchers have nothing to do, they invent fancy ways of hacking into all protected systems. Aerobatics for these gloomy geniuses is to break a computer that is not connected to the Internet. This is quite feasible, thanks to the two-legged carriers of infections, popping flash drives everywhere, but to implement a Trojan on the system is only half the battle. You also need to somehow extract the stolen data, and here the security men do not hold back their imagination.A group of comrades from the Ben-Gurion University in the Negev invented a new use for household routers and switches. If you implement a special software on the device (they took a router with DD-WRT firmware for the experiment and loaded a home-made script on it), then it can blink with indicators, transferring data in binary representation with a speed of up to 1000 bps per LED. Receiving this data requires, of course, direct visibility to the device, and the camera with a high frame rate.
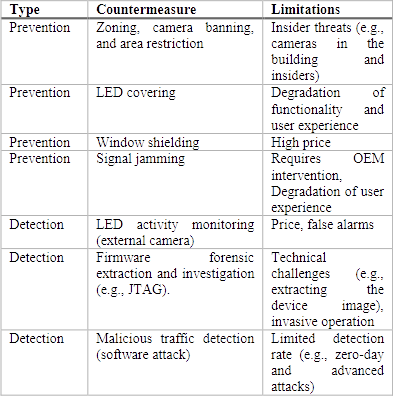
Special mention deserves the list of methods developed by the researchers to protect against such data leakage. Potential victims are encouraged to glue the indicators, make them blink randomly with the help of a modified firmware, and you can also keep the windows curtained or paste them with a dubbing film. It sounds ridiculous, but institutions dealing with information interesting for foreign intelligence agencies should think about it.
Such data extraction methods are suitable for tightly fenced networks, where the perimeter cannot be overcome by more reasonable methods. A home-class router doesn’t have much to do with such a network, and most likely it will not be directly visible from the window - but, let's say, a WiFi access point may well become a data leakage channel.
The darknet service appeared extortionists Trojans for MacOS
News The market of ransomware Trojans is developing and expanding, which is noticeable to the naked eye. And it has already expanded so much that even for Macs a new RaaS service has appeared. Not that this is a new kind of cloud service - it is Ransomware as a Service.
The name is not quite correct in this case, but how solid it sounds! And behind this is the site on the darknet, the creators of which offer everyone to bungle a runner for MacOS with the given parameters. Researchers from Fortinet who discovered the service contacted the authors and they advertised themselves as former developers from Yahoo and Facebook. At the same time, they did not take money for their services - they just made a Trojan and sent it to customers. Like, their interest is only in gathering information. However, judging by the FAQ hanging on the website, the runner requires sending money to the bitcoin wallet of the creators, they promise to send the customer to the distributor 70% of the amount collected.
The letter was a very uncomplicated extortionist Trojan. No zerodeev - the development and conduct of the attack falls entirely on the customer. If there is no good exploit whale under the poppy hand, you can simply convince the victim to put a suspicious program on himself. By the way, quite a working method.

The Trojan, named MacRansom, encrypts 128 user files with a symmetric algorithm. The key is set in the code, but as it turned out when analyzing the code, when encrypting, an 8-byte random number is used instead, which is not sent anywhere. In other words, no one is going to decrypt files. However, it is technically more than realistic to unscramble the 64-bit key if there is an unencrypted version of the file.

Antiquities
Fish # 6
Resident dangerous virus, encrypted, standardly infects COM and EXE files when they are executed and closed. In infected files, increases by 100 the value of the year the file was last modified.
It supports almost all functions of the "stealth" virus (see the description of the virus "V-4096"). It encrypts its body, not only in files, but also in its TSR-copy (when entering a virus, through a chain of int 21h, the virus decrypts itself, and when it goes out, it encrypts).
Since 1991, it “hangs up” the system, having previously reported “FISH VIRUS # 6 - EACH DIFF - BONN 2/90”. In addition, it contains the lines “COD”, “SHARK”, “CARP”, “BASS”, “TROUT”, “MUSKYZ”, “SOLE”, “PILE”, “MACKEREL”, “FISH”, “TUNA”, “FISH” FI. Intercepts int 13 and int 21h.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 67.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/331094/
All Articles