Shallow immersion or data recovery from the hard drive after flooding the office
The office of a small trading company was located on the ground floor of a residential building built in the seventies of the last century. During its existence, the house has pretty much decayed, but continued to be used with minor cosmetic repairs. Although the company complained about the inappropriate condition of pipes and plumbing equipment, it was not in a hurry to solve these problems at its own expense, believing that the coming major overhaul would reduce their potential costs. But, as subsequent events have shown, you should not rely on bare economic calculation without taking risks.
On a June morning, company employees discovered that the entrance to the office was flooded and steam was coming from the windows to the street. As a matter of urgency, an emergency crew was called, which stopped the flow of water into the room and began pumping. The cause of flooding was metal corrosion, which led to the destruction of one of the fittings on the hot water pipe.
Damage was caused to walls, floors, furniture, paper documentation and office equipment. The most affected were computers that were in the server-admin and remained on around the clock. The storages, which had to work while immersed in hot water, were a very sad sight.
')
rice one
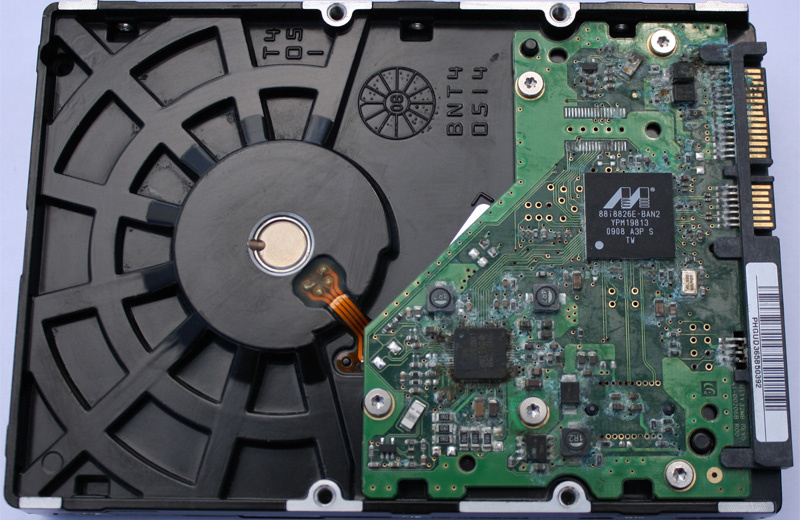
After analyzing backup copies of data that were out of the office, it was decided to restore data from some drives. One of them was the Samsung HD753LJ drive.
Approximately in this state, the drive came to our data recovery laboratory (in Figure 1, the drive is already after the dust and impurities cleaning procedure). It is known that the housing of the accumulator is not hermetic and it has an air filter for equalizing the pressure inside the accumulator with the environment.

rice 2
The design of the accumulator is such that the axis of the BMG is screwed into the case into the threaded hole and is sealed from the outside of the case with a round sticker. Unfortunately, in our case, the sticker was washed away under the influence of hot water.
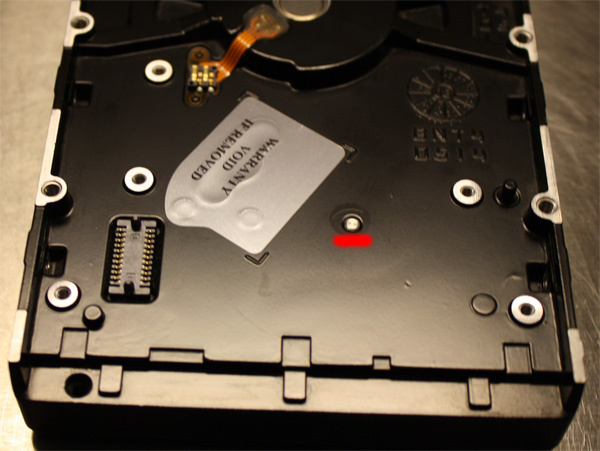
rice 3
Considering that the accumulator was kept for many hours while it was immersed in water with a peeled off protective sticker, we assume that liquid may get inside the HDA. In the conditions of laminar boxing we make opening of the store. A primary visual inspection does not reveal any serious fluid ingress into the HDA.

rice four
We remove the magnetic heads unit (BMG) and examine the threaded hole in the housing of the drive and its surroundings, as well as the BMG itself under a microscope. As a result of the inspection, small divorces were found near the threaded joint itself, which suggests that the liquid has fallen quite scarcely and at the time of the drive’s arrival to us it already had time to evaporate. Deformations of suspensions and sliders were not detected, the switch-preamplifier visually without damage. We carry out the operation of removing salts contained in the liquid, in order to avoid dispersion of dust on the HDA, both on the housing and on the BMG itself. We also measure the resistance of all pins on the block from the switch-preamplifier and compare it with the resistance of a similar drive. The result of the tests suggests the health of the switch-preamplifier. Based on the fact that no serious contamination was found, there are no deformations of the suspensions and sliders, and there is also a reason to assume that the switch-preamplifier is working, we conclude that there is no need to transfer the disk pack to another case and there is no need to use BMG from the drive -donora Putting the drive back.
Based on the results of the initial visual inspection, it is obvious that the printed circuit board of the “controller” of this drive has degraded as a result of electrochemical corrosion and cannot be used. In this family (F1_3D), the ROM is located in the Marvell 88i8826E MCU. Considering that it is not known whether this MCU is “alive”, as well as the complexity of soldering BGA chips, the options for obtaining the original contents of the ROM will be excluded.
In the case of Samsung drives of this family, the Hot swap technique is applicable. After reading the firmware modules, you can install the original firmware version, and also understand whether the entire firmware code was placed in the microcontroller's ROM or were used for storing overlays in the service area for its storage.
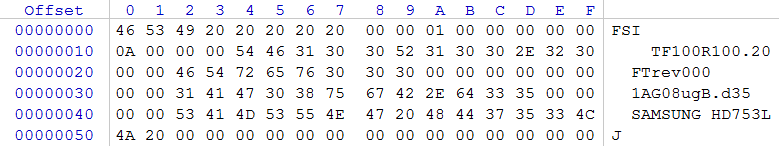
rice five
After analyzing the FSI module, we installed the firmware version 1AG08ugB.d35. Evaluating the contents of the modules 73_MOVLY, 19_BOVLY, we find that they are completely filled with zeros. This observation allows us to conclude that almost any ROM with a compatible platform identifier that does not use modules 19 and 73 for storing executable code can be used for data recovery.
We use the donor's fee, in which we write the nearest compatible ROM. The closest version available was 1AA18HuM.d35.
A test run showed a log in the terminal with some error messages that are not critical when reading user data.
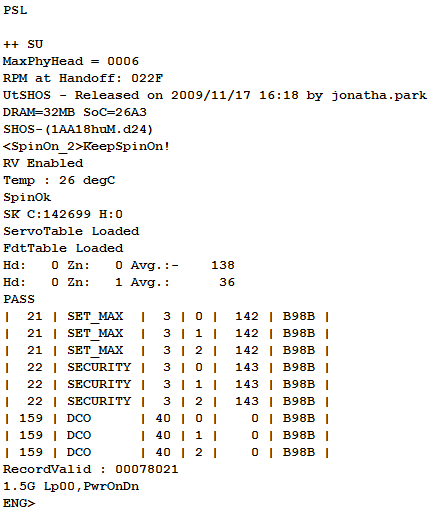
rice 6
According to the registers, the drive also announced readiness for data exchange.

rice 7
In the hard disk RAM, we modify the number of hardware repetitions from 100 read attempts to 2, in order not to provoke long delays on unreadable sections, and also partially disable offline scanning procedures.
We create the task of a sector-by-sector copy to another drive and first of all build the zone distribution map.

rice eight
We start reading in UDMA mode with a wait timeout of 300 milliseconds, with the interruption of the operation when instability is detected, a soft reset and a jump of 100,000 sectors ahead.
UNC errors are detected on sectors 6 24x xxx and 89 36x xxx. The remaining sections are read without difficulty.
We send the drive to sleep mode and on the copies we make an analysis of zero sector.
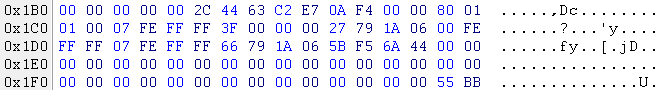
rice 9
In fig. 9 shows that there are records of two sections. The first section starts with sector 0x0000003F (63) and its length is 0x061A7927 (102,398,247) sectors. The second section begins with sector 0x061A7966 (102 398 310), and its length is 0x446AF55B (1 147 860 315) sectors. At offset 0x1BE is the value 0x80 - a sign of the activity of the partition (the partition is bootable). According to the localization of defects, it is obvious that they fall on the first section.
In sector 63 there is the boot sector of the first partition, in which, in addition to the bootloader code that transfers control to NTLDR, there are file system parameters.
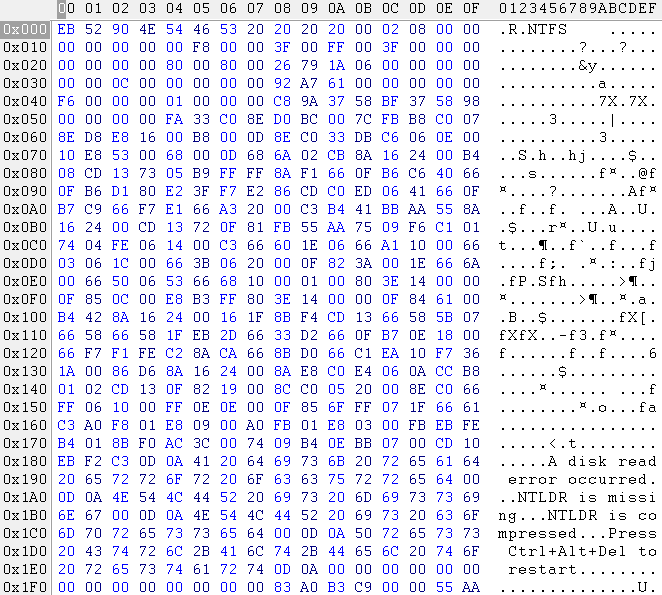
rice ten
Of the file system parameters, we note: the sector is 512 bytes, 8 sectors in a cluster, the size of the partition in the boot sector corresponds to the size described in the partition table.
The first sector of the MFT is calculated by the formula: X * Y + Z, where X is the number of the first cluster of the MFT location, Y is the number of sectors in the cluster, Z is the offset before the start of the partition.
0x00000000000C0000 * 0x08 + 0x3F = 0x000000000060003F (6 291 519)
Since we have an unflattering fragment for this offset, we calculate the position of the MFT Mirror
0x000000000061A792 * 0x08 + 0x3F = 0x00000000030D3CCF (51 199 183)
There are no unread fragments for this offset. Having determined the position of the MFT and having analyzed its location, we build a map.

rice eleven
We read partially unread first MFT fragment. The operation passes without difficulty.
Let's analyze the MFT records and compare them with the read card. As a result, we find that defects fall on only two files.
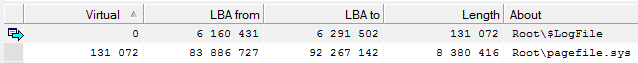
rice 12
The first is the NTFS service structure, which is noncritical.
The second is a virtual memory file in Windows and is also of no value to the Customer.
To clarify the nature of the defect, we read the unread fragments of these files, which will show the presence of completely unreadable sections of several thousand sectors, which indicates the incorrect operation of the drive in the last minutes.
As a conclusion, I would like to remind everyone again of the need for backup and that it is desirable to keep copies not in the same places where drives with basic operating data are located, since in the case of such a fairly easily foreseeable force majeure, all existing information.
Previous publication: Is it always safe to encrypt or recover data from an external hard drive Prestigio Data Safe II
Next post: Admin Sin or Data Recovery from Knocking Western Digital WD5000AAKX HDD
On a June morning, company employees discovered that the entrance to the office was flooded and steam was coming from the windows to the street. As a matter of urgency, an emergency crew was called, which stopped the flow of water into the room and began pumping. The cause of flooding was metal corrosion, which led to the destruction of one of the fittings on the hot water pipe.
Damage was caused to walls, floors, furniture, paper documentation and office equipment. The most affected were computers that were in the server-admin and remained on around the clock. The storages, which had to work while immersed in hot water, were a very sad sight.
')

rice one
After analyzing backup copies of data that were out of the office, it was decided to restore data from some drives. One of them was the Samsung HD753LJ drive.
Approximately in this state, the drive came to our data recovery laboratory (in Figure 1, the drive is already after the dust and impurities cleaning procedure). It is known that the housing of the accumulator is not hermetic and it has an air filter for equalizing the pressure inside the accumulator with the environment.

rice 2
The design of the accumulator is such that the axis of the BMG is screwed into the case into the threaded hole and is sealed from the outside of the case with a round sticker. Unfortunately, in our case, the sticker was washed away under the influence of hot water.

rice 3
Considering that the accumulator was kept for many hours while it was immersed in water with a peeled off protective sticker, we assume that liquid may get inside the HDA. In the conditions of laminar boxing we make opening of the store. A primary visual inspection does not reveal any serious fluid ingress into the HDA.

rice four
We remove the magnetic heads unit (BMG) and examine the threaded hole in the housing of the drive and its surroundings, as well as the BMG itself under a microscope. As a result of the inspection, small divorces were found near the threaded joint itself, which suggests that the liquid has fallen quite scarcely and at the time of the drive’s arrival to us it already had time to evaporate. Deformations of suspensions and sliders were not detected, the switch-preamplifier visually without damage. We carry out the operation of removing salts contained in the liquid, in order to avoid dispersion of dust on the HDA, both on the housing and on the BMG itself. We also measure the resistance of all pins on the block from the switch-preamplifier and compare it with the resistance of a similar drive. The result of the tests suggests the health of the switch-preamplifier. Based on the fact that no serious contamination was found, there are no deformations of the suspensions and sliders, and there is also a reason to assume that the switch-preamplifier is working, we conclude that there is no need to transfer the disk pack to another case and there is no need to use BMG from the drive -donora Putting the drive back.
Based on the results of the initial visual inspection, it is obvious that the printed circuit board of the “controller” of this drive has degraded as a result of electrochemical corrosion and cannot be used. In this family (F1_3D), the ROM is located in the Marvell 88i8826E MCU. Considering that it is not known whether this MCU is “alive”, as well as the complexity of soldering BGA chips, the options for obtaining the original contents of the ROM will be excluded.
In the case of Samsung drives of this family, the Hot swap technique is applicable. After reading the firmware modules, you can install the original firmware version, and also understand whether the entire firmware code was placed in the microcontroller's ROM or were used for storing overlays in the service area for its storage.

rice five
After analyzing the FSI module, we installed the firmware version 1AG08ugB.d35. Evaluating the contents of the modules 73_MOVLY, 19_BOVLY, we find that they are completely filled with zeros. This observation allows us to conclude that almost any ROM with a compatible platform identifier that does not use modules 19 and 73 for storing executable code can be used for data recovery.
We use the donor's fee, in which we write the nearest compatible ROM. The closest version available was 1AA18HuM.d35.
A test run showed a log in the terminal with some error messages that are not critical when reading user data.

rice 6
According to the registers, the drive also announced readiness for data exchange.

rice 7
In the hard disk RAM, we modify the number of hardware repetitions from 100 read attempts to 2, in order not to provoke long delays on unreadable sections, and also partially disable offline scanning procedures.
We create the task of a sector-by-sector copy to another drive and first of all build the zone distribution map.

rice eight
We start reading in UDMA mode with a wait timeout of 300 milliseconds, with the interruption of the operation when instability is detected, a soft reset and a jump of 100,000 sectors ahead.
UNC errors are detected on sectors 6 24x xxx and 89 36x xxx. The remaining sections are read without difficulty.
We send the drive to sleep mode and on the copies we make an analysis of zero sector.

rice 9
In fig. 9 shows that there are records of two sections. The first section starts with sector 0x0000003F (63) and its length is 0x061A7927 (102,398,247) sectors. The second section begins with sector 0x061A7966 (102 398 310), and its length is 0x446AF55B (1 147 860 315) sectors. At offset 0x1BE is the value 0x80 - a sign of the activity of the partition (the partition is bootable). According to the localization of defects, it is obvious that they fall on the first section.
In sector 63 there is the boot sector of the first partition, in which, in addition to the bootloader code that transfers control to NTLDR, there are file system parameters.

rice ten
Of the file system parameters, we note: the sector is 512 bytes, 8 sectors in a cluster, the size of the partition in the boot sector corresponds to the size described in the partition table.
The first sector of the MFT is calculated by the formula: X * Y + Z, where X is the number of the first cluster of the MFT location, Y is the number of sectors in the cluster, Z is the offset before the start of the partition.
0x00000000000C0000 * 0x08 + 0x3F = 0x000000000060003F (6 291 519)
Since we have an unflattering fragment for this offset, we calculate the position of the MFT Mirror
0x000000000061A792 * 0x08 + 0x3F = 0x00000000030D3CCF (51 199 183)
There are no unread fragments for this offset. Having determined the position of the MFT and having analyzed its location, we build a map.

rice eleven
We read partially unread first MFT fragment. The operation passes without difficulty.
Let's analyze the MFT records and compare them with the read card. As a result, we find that defects fall on only two files.

rice 12
The first is the NTFS service structure, which is noncritical.
The second is a virtual memory file in Windows and is also of no value to the Customer.
To clarify the nature of the defect, we read the unread fragments of these files, which will show the presence of completely unreadable sections of several thousand sectors, which indicates the incorrect operation of the drive in the last minutes.
As a conclusion, I would like to remind everyone again of the need for backup and that it is desirable to keep copies not in the same places where drives with basic operating data are located, since in the case of such a fairly easily foreseeable force majeure, all existing information.
Previous publication: Is it always safe to encrypt or recover data from an external hard drive Prestigio Data Safe II
Next post: Admin Sin or Data Recovery from Knocking Western Digital WD5000AAKX HDD
Source: https://habr.com/ru/post/331090/
All Articles