[Administrator's abstract] Domains, addresses and Windows: mix, but do not shake

In the next "admin summary", we’ll focus on another fundamental thing - the name resolution mechanism in IP networks. By the way, do you know why in the domain network nslookup can answer all requests with one address? And this despite the fact that the sites are opening properly. If you are thinking - welcome under cat. .
Windows is traditionally using two technologies to convert a name to an IP address — NetBIOS and the more well-known DNS.
NetBIOS Grandpa
NetBIOS (Network Basic Input / Output System) is a technology that came to us in 1983. It provides such features as:
registration and verification of network names;
establishing and breaking connections;
communication with guaranteed information delivery;
communication with non-guaranteed information delivery;
- Support management and monitoring of the driver and network card.
Within the framework of this material we are only interested in the first paragraph. When using NetBIOS, the name is limited to 16 bytes — 15 characters and a special character for the node type. The procedure for converting a name to an address is implemented by broadcast requests.
Broadcast call such a request, which is designed to receive all computers on the network. To do this, the request is sent to a special IP or MAC address for operation at the third or second level of the OSI model.
To work at the second level, the MAC address of the FF: FF: FF: FF: FF: FF is used, for the third level in the IP network, the address is the last address in the subnet. For example, in the subnet 192.168.0.0/24 this address would be 192.168.0.255
An interesting feature is that you can bind the name not to the host, but to the service. For example, to the user name for sending messages via net send.
Naturally, it is not efficient to send broadcast requests all the time, so there is a NetBIOS cache — a temporary table of matching names and IP addresses. The table is in RAM, by default the number of records is limited to sixteen, and the life of each is ten minutes. You can view its contents with the nbtstat -c command , and clear it with nbtstat -R .
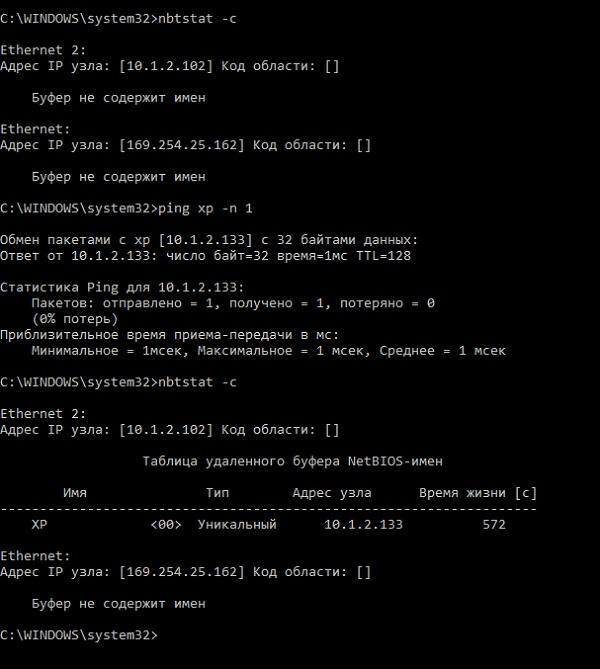
An example of the work of the cache to resolve the host name "xp" .
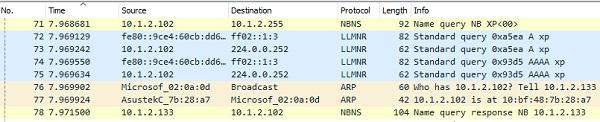
What happened at the same time from the point of view of the sniffer.
In large networks, due to the limitation on the number of entries and their lifespan, the cache no longer saves. Yes, and a large number of broadcast requests can easily slow down the network performance. To avoid this, a WINS (Windows Internet Name Service) server is used. The administrator can register the server address himself or assign it to a DHCP server. Computers turn on NetBIOS names on the server when they are turned on, and are also addressed to resolve names.
On networks with * nix servers, you can use the Samba software package as a replacement for WINS. To do this, simply add the line “wins support = yes” to the configuration file. Read more in the documentation .
In the absence of WINS, you can use the lmhosts file, which the system will “drop in” when it is not possible to resolve the name in other ways. In modern systems, it is absent by default. There is only a sample file-documentation at% systemroot% \ System32 \ drivers \ etc \ lmhost.sam. If you need lmhosts, you can create it next to lmhosts.sam.
Now NetBIOS technology is not widely known, but by default it is enabled. It is worth keeping this in mind when diagnosing problems.
The standard of our days - DNS
DNS (Domain Name System) is a distributed hierarchical system for obtaining information about domains. Perhaps the most famous of these. The mechanism of operation is extremely simple, consider it on the example of determining the IP address of the host www.google.com:
if there is no address in the resolver cache, the system requests the DNS server specified in the network interface settings;
The DNS server is looking at the record for itself, and if it does not even have information about the google.com domain, it sends a request to higher-level DNS servers, for example, provider. If there are no upstream servers, the request is sent immediately to one of the 13 (excluding replicas) root servers, which have information about those who hold the upper zone. In our case, com.
after that, our server asks for the name www.google.com a server that holds the com zone;
- then the server that holds the google.com zone is already responding.
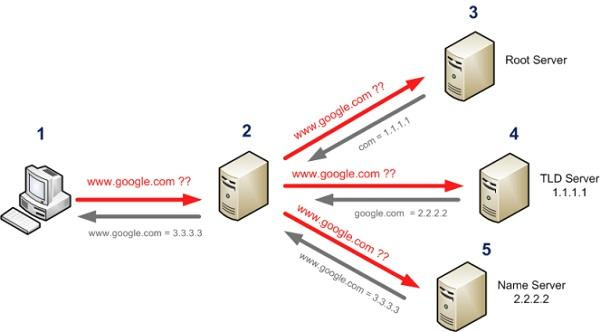
An illustrative flow of the DNS query.
Of course, DNS is not limited to simply matching the “name - address”: it supports the different types of records described by the RFC standards. I will leave their list of relevant articles .
The DNS service itself runs on UDP port 53, in rare cases using TCP.
DNS switches to TCP with the same port 53 for transferring the DNS zone and for requests larger than 512 bytes. The latter is quite rare, but at interviews potential employers like to ask questions about the DNS port with a sly squint.
As with NetBIOS, DNS has a cache not to contact the server on every request, and a file where you can manually match the address and name — known by many% Systemroot% \ System32 \ drivers \ etc \ hosts.
Unlike the NetBIOS cache, the contents of the hosts file are immediately read into the DNS cache. In addition, an interesting difference is that the DNS cache stores not only the matching of domains and addresses, but also unsuccessful name resolution attempts. You can view the contents of the cache on the command line using the ipconfig / displaydns command, and clear ipconfig / flushdns . The dnscache service is responsible for the cache.
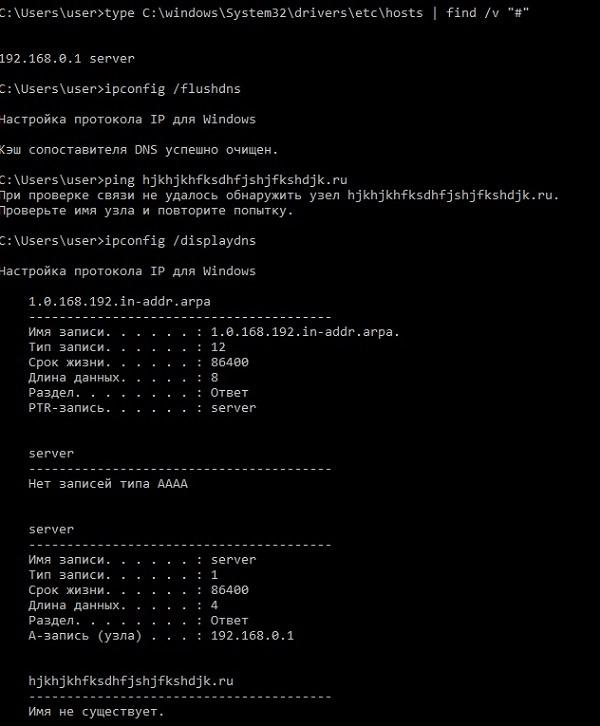
The screenshot shows that immediately after clearing the cache, the contents of the hosts file are added to it, and the presence of unsuccessful name recognition attempts in the cache is illustrated.
When attempting to resolve a name, DNS servers typically configured on the network adapter are typically used. But in some cases, for example, when connecting to a corporate VPN, you need to send permission requests for certain names to other DNS. For this, in Windows systems, starting from 7 \ 2008 R2, a name resolution policy table (NRPT) has appeared. It is configured through the registry, in the HKEY_LOCAL_MACHINE \ SOFTWARE \ Policies \ Microsoft \ Windows NT \ DnsClient \ DnsPolicyConfig or group policies section.

Setting the name resolution policy through GPO .
If there are several technologies in one network, where each is also with its own cache, the order of their use is important.
Name Resolution Procedure
Windows is trying to resolve names in the following order:
checks if the name does not match the local host name;
looks into the DNS resolver cache;
if a match is not found in the cache, a query is sent to the DNS server;
if the host name is “flat”, for example, “servername”, the system accesses the NetBIOS cache. Names of more than 16 characters or compound, for example, “servername.domainname.ru” - NetBIOS is not used;
if it was not possible to resolve the name at this stage, a request is made to the WINS server;
if it fails, the system tries to get the name of the broadcast request, but no more than three attempts;
- last attempt - the system is looking for entries in the local lmhosts file.
For convenience, I will illustrate the algorithm with a flowchart:
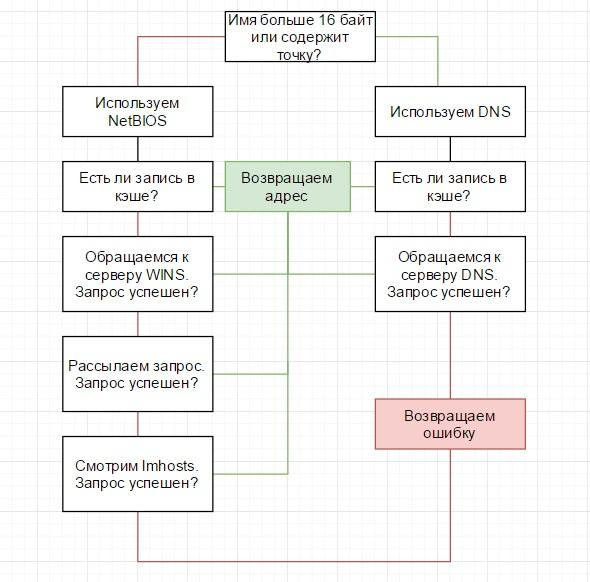
Algorithm name resolution in Windows.
That is, when you run the ping server.domain.com command, NetBIOS and its broadcast requests will not be used, only the DNS will work, but with a short name, the procedure will go a long way. You can easily verify this by running the simplest script:
@echo off echo %time% ping hjfskhfjkshjfkshjkhfdsjk.com echo %time% ping xyz echo %time% pause Performing the second ping takes a few seconds longer, and the sniffer will show broadcast requests.
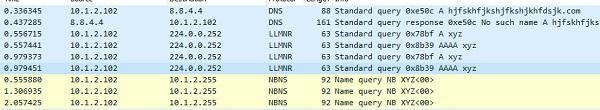
Sniffer shows DNS queries for a long name and NetBIOS broadcasts for a short one.
Separate mentioning deserve domain networks - they query with a short name will work a little differently.
Active Directory and suffixes
Active Directory is tightly integrated with DNS and does not function without it. An entry in DNS is created for each domain computer, and the computer gets a full name (FQDN - fully qualified domain name) of the form name.subdomain.domain.com.
In order to avoid the need to enter the FQDN at work, the system automatically adds a part of the domain name to the host for various operations - whether it is registration in DNS or getting an IP address by name. First, add the entire domain name, then the next part to the point.
When you try to start the ping servername command, the system will do the following:
if the DNS name does not exist in the cache, the system will ask the DNS server about the host servername.subdomain.domain.com;
- if the answer is no, the system will ask for servername.domain.com , in case we contact the host of the parent domain.
However, suffixes are not added by default to compound names like www.google.com . This behavior is configured by group policies.
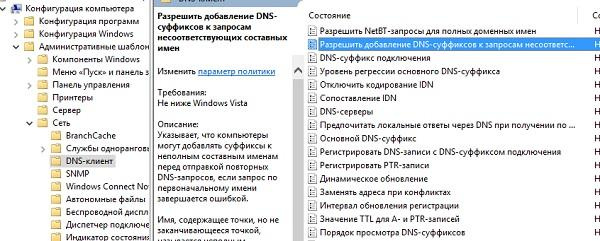
Configure adding DNS suffixes through group policies.
You can also configure DNS suffixes by group policies or on the DNS tab of the advanced TCP \ IP properties of the network adapter. It is convenient to view the current settings using the ipconfig / all command.
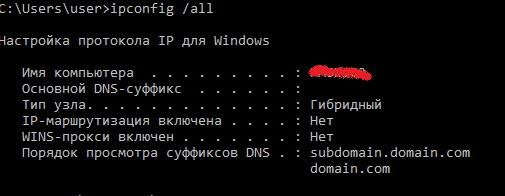
DNS suffixes and their order in the output of ipconfig / all .
However, the nslookup utility works a little differently: it adds suffixes to long names as well. You can see what is happening inside nslookup by turning on the diagnostic mode with the debug directive or the extended diagnostic mode with the dc2 directive. For example, here is the output of the command to resolve the name ya.ru:
nslookup -dc2 ya.ru ------------ Got answer: HEADER: opcode = QUERY, id = 1, rcode = NOERROR header flags: response, want recursion, recursion avail. questions = 1, answers = 1, authority records = 0, additional = 0 QUESTIONS: 4.4.8.8.in-addr.arpa, type = PTR, class = IN ANSWERS: -> 4.4.8.8.in-addr.arpa name = google-public-dns-b.google.com ttl = 86399 (23 hours 59 mins 59 secs) ------------ ╤: google-public-dns-b.google.com Address: 8.8.4.4 ------------ Got answer: HEADER: opcode = QUERY, id = 2, rcode = NOERROR header flags: response, want recursion, recursion avail. questions = 1, answers = 1, authority records = 0, additional = 0 QUESTIONS: ya.ru.subdomain.domain.com, type = A, class = IN ANSWERS: -> ya.ru.subdomain.domain.com internet address = 66.96.162.92 ttl = 599 (9 mins 59 secs) ------------ : ------------ Got answer: HEADER: opcode = QUERY, id = 3, rcode = NOERROR header flags: response, want recursion, recursion avail. questions = 1, answers = 0, authority records = 1, additional = 0 QUESTIONS: ya.ru.subdomain.domain.com, type = AAAA, class = IN AUTHORITY RECORDS: -> domain.com ttl = 19 (19 secs) primary name server = ns-2022.awsdns-60.co.uk responsible mail addr = awsdns-hostmaster.amazon.com serial = 1 refresh = 7200 (2 hours) retry = 900 (15 mins) expire = 1209600 (14 days) default TTL = 86400 (1 day) ------------ ╚ : ya.ru.subdomain.domain.com Address: 66.96.162.92 Because of the suffixes, the nslookup utility didn’t produce the same result as the ping:
ping ya.ru -n 1 ya.ru [87.250.250.242] 32 : 87.250.250.242: =32 =170 TTL=52 This behavior is sometimes confusing for novice system administrators.
I personally encountered such a problem: in the domain, nslookup always gave the same address in response to any request. As it turned out, when creating a domain, someone chose the name domain.com.ru, which does not belong to an organization in the “big Internet”. Nslookup added the domain name to all requests, then the parent suffix - com.ru. The com.ru domain on the Internet has a wildcard entry, that is, any request of the form XXX.com.ru will be successfully resolved. Therefore, nslookup and gave all the questions one answer. To avoid such problems, it is not recommended to use domains that do not belong to you for naming.
When diagnosing it is worth remembering that the nslookup utility works directly with the DNS server, unlike the usual name resolver. If you take the computer out of the domain and place it on a different subnet, nslookup will show that everything is in order, but without setting the DNS suffixes, the system will not be able to contact the servers by short names.
Hence the frequent questions - why ping does not work, and nslookup works.
In terms of finding and resolving name resolution errors, I can recommend not to be afraid to use a tool for analyzing traffic - a sniffer. With him, all traffic is in full view, and if unnecessary suffixes are added, this will be reflected in DNS queries. If there are no DNS and NetBIOS queries, the incorrect response is taken from the cache.
If it is not possible to start the sniffer, I recommend to compare the output of ping and nslookup, clear the caches, check the work with another DNS server.
By the way, if you remember the curious DNS-curiosities from your own practice - share in the comments.
')
Source: https://habr.com/ru/post/330944/
All Articles