Is it always safe to encrypt or recover data from an external hard drive Prestigio Data Safe II
The owner of a small business on Monday evening decided to take up a financial analysis of current affairs. When he arrived home in the evening, he settled into his home office, connected an external drive Prestigio Data Safe II 500GB to the laptop and plunged into numbers. Suddenly his thoughts were interrupted by the noise, and then a pet ran into the room with a shrill meow. on others, hissing at any attempt to approach.
When the culmination of events disappeared and the reasons for this behavior of a pet became clear, the owner discovered that the case was not limited to the frightened cat. Real chaos reigned on the table and around it: documents scattered around the room and a lifeless hard drive dangling on a USB cable.

rice one
After eliminating the consequences of the race of the unfortunate animal, close attention was paid to the hard drive. On the back of the disk owner, he ran a light chill when he didn’t wait for the utility's launch drive to offer a password to access the hidden section. After several fruitless attempts, the system administrator was urgently called.
')
The administrator, making sure of the futility of trying to work with the drive via USB, dismantled the box, removed the Toshiba MK5059GSXP HDD and connected it to the SATA port of the computer. Having booted Windows, in the Disk Management snap-in, I discovered that from the point of view of the OS, the drive does not contain any partitions. An attempt was made to launch an automatic recovery program, but the scan, which had barely begun, suspended the computer, and there were clicks from the drive. At this stage, it was decided that it was time to stop.
With this background, the drive came to our data recovery lab. Based on the fact that the drive was after the impact and when attempting to scan, it began to make knocking sounds, then the first operation would be to clean it from dust and conduct an examination in a laminar box. Suspension and slider BMG, recirculation air filter, as well as the upper surface in the disc pack are subject to thorough examination.

rice 2
Inspection of the recirculating air filter and BMG did not reveal deformations and the presence of metal particles, on the basis of which we conclude that the drive can be started with the original BMG. Examination of the upper surface under a microscope reveals a small radial scratch at the outer edge.
Assembling the drive, connect it to the PC3000 port and power up. Characteristic air noise is heard when the shaft rotates and the sound of the calibration test passes. Further, there is a certain delay, after which the drive finally issues a register readiness to accept commands.

rice 3
We perform firmware backup, in the process we discover the unreadable G-list. Since this defect list is necessary for the operation of the broadcast system, the drive does not allow reading any sectors from the user area in the normal mode.
Attempting to write to an unused track in the service area causes the hard disk to start knocking sounds, which clearly indicates recording problems. Since we don’t have the opportunity to rewrite the unreadable module, we will not attempt to write a pure G-list module.
For Toshiba drives that do not have or do not work correctly recording heads, or there are serious damages in the service area, which do not allow to function correctly, you can use the features of the technological mode. After switching on the technology mode, the drive changes the operation logic: no logging to SMART logs is performed, offline scanning is disabled, and the translation system does not take into account entries in the P-list and G-list.
Before reading in the technological mode, you need to analyze the P-list of the hard disk in order to take into account all excluded areas from the PBA range and, when reading out, obtain user data that was recorded within the LBA range (which includes exceptions from the P-list) without shifts.
The next step is to build a zone distribution map in order to understand how the logical space is formed. For reading, we will construct a map of the mini zones and sort them in descending order, since during the examination damage was found at the outer edge of the plate.
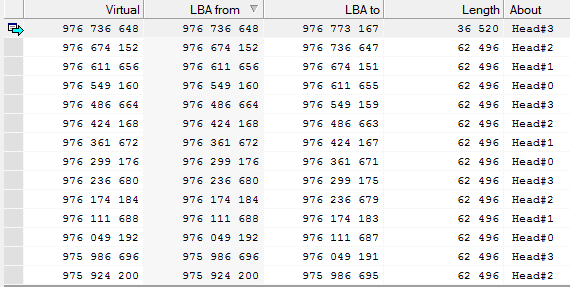
rice four
In this case, without much difficulty, up to 15,998 xxx sectors were read. Then there were difficulties in reading.

rice five
An attempt to rebuild the chain in ascending order with further reading showed the presence of defects from the very beginning of the logical range.
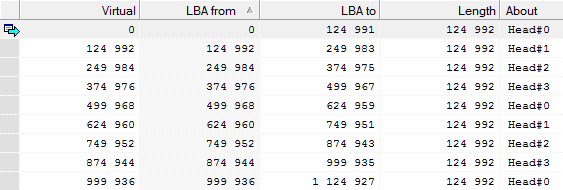
rice 6
We exclude reading on head No. 0 and try to read further, then problems with 249 xxx sectors are detected, we also exclude reading on head No. 2. We perform zone reading with heads No. 1 and No. 3 in the interval from 0 to 15,998,975 sectors.
For further reading of the problem areas, we will use the PIO mode to more accurately control the state of the drive. After completing a certain number of attempts to read with different timeouts, wait for readiness and different size of jumps when instabilities are detected, proceed to the stage of multipass reading of defects. As a result of all reading attempts, less than 3,000 sectors out of a total of 976,773,168 sectors remained unread.
Fill in the unread sectors on the copy with the 0xDE 0xAD pattern. We analyze regular expressions for various popular file types and find the absence of user data on the disk, but at the same time we can say that the disk is filled with some data by more than 95% (according to how many sectors are filled with non-zero values).
At this stage, we will postpone the sector-by-sector copy and analyze the features of the USB-SATA bridge used in the box.

rice 7
This USB-SATA adapter is based on the MCU J-Micron 20339. Take a drive, all sectors of which are filled with 0x00, connect to this adapter and connect to the PC.
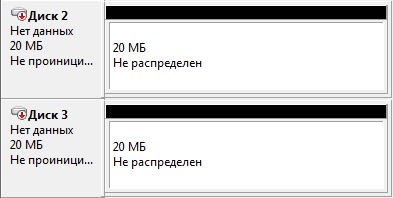
rice eight
OS found 2 drives of 20Mb each. When analyzing, it turned out that the first section is read only. On the second record is available.

rice 9
Based on the device names in the passport data, it can be assumed that the role of the first is to store an application that configures the size of a public and hidden section, as well as opening access to a hidden section. The second section is designed to store "public" data and the third appears only when you enter the password in the proprietary utility.
When opening in the disk editor in each sector of any of the devices we see filling with a certain pattern.
rice ten
Let's disconnect the disk from this adapter and analyze if the controller has some metadata on the drive itself, since the disk was initially completely filled with zeros. In sector 0x18FBF (102,335) and sector 0x18FCF (102,351), filling with a certain chaotic content is detected.
Starting from sector 102 352, we will record the sector number in the first 4 bytes over 40 960 sectors. Reconnecting the drive to the adapter, let's analyze the filling of the first twenty megabyte partition. We will see that throughout the entire section the pattern remains as in fig. 10, but with changes in the first bytes. Having performed XOR operations between the original pattern and the current values, we get the sectors, the contents of which will be zeros with the sector number in the first 4 bytes.
Based on this, we can assert that this controller encrypts data using XOR operation, the key size is 512 bytes. The disadvantage of this “encryption” is that in sectors filled with zeros, but read through this USB-SATA adapter, all 512 bytes of the key will be in their original form. Also note that in drives, where sectors 102 335 and 102 351 contain incorrect content in terms of the JM20339 firmware, new keys will be generated randomly.
Let's return to the copy of the problem drive and analyze the read card. Let us make sure that the key sectors 102 335 and 102 351 are read and additional analysis methods for finding the key will not be required. Transfer the contents of the key sectors to the blank drive and see which XOR pattern will be generated by the JM20339 controller firmware.
Let's create a backup copy of the drive on which the patient has had a sector-specific copy of the patient, and perform an XOR operation on each sector, starting from sector 102352 with the obtained key.
Starting the analysis of regular expressions, we note that there are many signs of the presence of popular file types (jpg, doc, xls, etc.). This circumstance confirms the correctness of data decryption.
For convenience of analysis, in the 0 sector we will write the classical partition table, in which we will describe the 3 partitions available on this drive. In our original task we will substitute the drive with decrypted data.
Since the client’s task was to restore the data from the hidden partition, we will evaluate the integrity of the file system on it by analyzing the location of the metadata and check if there are any unread sections. The analysis reveals that 16 sectors in the MFT could not be read, which indicates a loss of no more than 8 file records. Further comparison of files with the read card allows you to identify 73 more files affected by the contact of the sliders with the surfaces of the plates.
99, 9% of the recovered files are the final result that satisfied the client.
As a conclusion, you can once again remind everyone of the need for backup and also note that to this day there are quite a few solutions on the market, where the data encryption option is just a marketing ploy that cannot reliably protect user data.
Next post: Shallow immersion or data recovery from the hard drive after flooding the office
Previous publication: Data Recovery from an External Hard Drive Seagate FreeAgent Go
When the culmination of events disappeared and the reasons for this behavior of a pet became clear, the owner discovered that the case was not limited to the frightened cat. Real chaos reigned on the table and around it: documents scattered around the room and a lifeless hard drive dangling on a USB cable.

rice one
After eliminating the consequences of the race of the unfortunate animal, close attention was paid to the hard drive. On the back of the disk owner, he ran a light chill when he didn’t wait for the utility's launch drive to offer a password to access the hidden section. After several fruitless attempts, the system administrator was urgently called.
')
The administrator, making sure of the futility of trying to work with the drive via USB, dismantled the box, removed the Toshiba MK5059GSXP HDD and connected it to the SATA port of the computer. Having booted Windows, in the Disk Management snap-in, I discovered that from the point of view of the OS, the drive does not contain any partitions. An attempt was made to launch an automatic recovery program, but the scan, which had barely begun, suspended the computer, and there were clicks from the drive. At this stage, it was decided that it was time to stop.
With this background, the drive came to our data recovery lab. Based on the fact that the drive was after the impact and when attempting to scan, it began to make knocking sounds, then the first operation would be to clean it from dust and conduct an examination in a laminar box. Suspension and slider BMG, recirculation air filter, as well as the upper surface in the disc pack are subject to thorough examination.

rice 2
Inspection of the recirculating air filter and BMG did not reveal deformations and the presence of metal particles, on the basis of which we conclude that the drive can be started with the original BMG. Examination of the upper surface under a microscope reveals a small radial scratch at the outer edge.
Assembling the drive, connect it to the PC3000 port and power up. Characteristic air noise is heard when the shaft rotates and the sound of the calibration test passes. Further, there is a certain delay, after which the drive finally issues a register readiness to accept commands.

rice 3
We perform firmware backup, in the process we discover the unreadable G-list. Since this defect list is necessary for the operation of the broadcast system, the drive does not allow reading any sectors from the user area in the normal mode.
Attempting to write to an unused track in the service area causes the hard disk to start knocking sounds, which clearly indicates recording problems. Since we don’t have the opportunity to rewrite the unreadable module, we will not attempt to write a pure G-list module.
For Toshiba drives that do not have or do not work correctly recording heads, or there are serious damages in the service area, which do not allow to function correctly, you can use the features of the technological mode. After switching on the technology mode, the drive changes the operation logic: no logging to SMART logs is performed, offline scanning is disabled, and the translation system does not take into account entries in the P-list and G-list.
Before reading in the technological mode, you need to analyze the P-list of the hard disk in order to take into account all excluded areas from the PBA range and, when reading out, obtain user data that was recorded within the LBA range (which includes exceptions from the P-list) without shifts.
The next step is to build a zone distribution map in order to understand how the logical space is formed. For reading, we will construct a map of the mini zones and sort them in descending order, since during the examination damage was found at the outer edge of the plate.

rice four
In this case, without much difficulty, up to 15,998 xxx sectors were read. Then there were difficulties in reading.

rice five
An attempt to rebuild the chain in ascending order with further reading showed the presence of defects from the very beginning of the logical range.

rice 6
We exclude reading on head No. 0 and try to read further, then problems with 249 xxx sectors are detected, we also exclude reading on head No. 2. We perform zone reading with heads No. 1 and No. 3 in the interval from 0 to 15,998,975 sectors.
For further reading of the problem areas, we will use the PIO mode to more accurately control the state of the drive. After completing a certain number of attempts to read with different timeouts, wait for readiness and different size of jumps when instabilities are detected, proceed to the stage of multipass reading of defects. As a result of all reading attempts, less than 3,000 sectors out of a total of 976,773,168 sectors remained unread.
Fill in the unread sectors on the copy with the 0xDE 0xAD pattern. We analyze regular expressions for various popular file types and find the absence of user data on the disk, but at the same time we can say that the disk is filled with some data by more than 95% (according to how many sectors are filled with non-zero values).
At this stage, we will postpone the sector-by-sector copy and analyze the features of the USB-SATA bridge used in the box.

rice 7
This USB-SATA adapter is based on the MCU J-Micron 20339. Take a drive, all sectors of which are filled with 0x00, connect to this adapter and connect to the PC.

rice eight
OS found 2 drives of 20Mb each. When analyzing, it turned out that the first section is read only. On the second record is available.

rice 9
Based on the device names in the passport data, it can be assumed that the role of the first is to store an application that configures the size of a public and hidden section, as well as opening access to a hidden section. The second section is designed to store "public" data and the third appears only when you enter the password in the proprietary utility.
When opening in the disk editor in each sector of any of the devices we see filling with a certain pattern.

rice ten
Let's disconnect the disk from this adapter and analyze if the controller has some metadata on the drive itself, since the disk was initially completely filled with zeros. In sector 0x18FBF (102,335) and sector 0x18FCF (102,351), filling with a certain chaotic content is detected.
Starting from sector 102 352, we will record the sector number in the first 4 bytes over 40 960 sectors. Reconnecting the drive to the adapter, let's analyze the filling of the first twenty megabyte partition. We will see that throughout the entire section the pattern remains as in fig. 10, but with changes in the first bytes. Having performed XOR operations between the original pattern and the current values, we get the sectors, the contents of which will be zeros with the sector number in the first 4 bytes.
Based on this, we can assert that this controller encrypts data using XOR operation, the key size is 512 bytes. The disadvantage of this “encryption” is that in sectors filled with zeros, but read through this USB-SATA adapter, all 512 bytes of the key will be in their original form. Also note that in drives, where sectors 102 335 and 102 351 contain incorrect content in terms of the JM20339 firmware, new keys will be generated randomly.
Let's return to the copy of the problem drive and analyze the read card. Let us make sure that the key sectors 102 335 and 102 351 are read and additional analysis methods for finding the key will not be required. Transfer the contents of the key sectors to the blank drive and see which XOR pattern will be generated by the JM20339 controller firmware.
Let's create a backup copy of the drive on which the patient has had a sector-specific copy of the patient, and perform an XOR operation on each sector, starting from sector 102352 with the obtained key.
Starting the analysis of regular expressions, we note that there are many signs of the presence of popular file types (jpg, doc, xls, etc.). This circumstance confirms the correctness of data decryption.
For convenience of analysis, in the 0 sector we will write the classical partition table, in which we will describe the 3 partitions available on this drive. In our original task we will substitute the drive with decrypted data.
Since the client’s task was to restore the data from the hidden partition, we will evaluate the integrity of the file system on it by analyzing the location of the metadata and check if there are any unread sections. The analysis reveals that 16 sectors in the MFT could not be read, which indicates a loss of no more than 8 file records. Further comparison of files with the read card allows you to identify 73 more files affected by the contact of the sliders with the surfaces of the plates.
99, 9% of the recovered files are the final result that satisfied the client.
As a conclusion, you can once again remind everyone of the need for backup and also note that to this day there are quite a few solutions on the market, where the data encryption option is just a marketing ploy that cannot reliably protect user data.
Next post: Shallow immersion or data recovery from the hard drive after flooding the office
Previous publication: Data Recovery from an External Hard Drive Seagate FreeAgent Go
Source: https://habr.com/ru/post/330642/
All Articles