Hackers used the Intel Serial-over-LAN CPU function to bypass the firewall
Researchers at Microsoft managed to detect malicious software that uses Intel Serial-over-LAN (SOL) as a “bridge” to transfer information, which is part of the Active Management Technology (AMT) toolkit. SOL technology works in such a way that traffic bypasses the network stack of the local computer, so it is not “seen” and does not block firewalls and antivirus software. This allows you to easily retrieve data from infected hosts.
 / photo by Andi Weiland CC
/ photo by Andi Weiland CC
At the beginning of the year, Intel was already faced with dangerous vulnerabilities in Intel ME. Then the problem affected solutions of Intel Active Management Technology (AMT), Intel Standard Management Manageability (ISM), Intel Small Business Technology (SBT) and allowed an unprivileged attacker to gain remote access to hardware management. The vulnerability, designated CVE-2017-5689 , the developers of the IT giant patch.
')
And here is a new situation, but already connected with the peculiarities of the work of Intel Serial-over-LAN. AMT SOL is part of the Intel Management Engine (ME) - a separate processor embedded in an Intel CPU that runs on its own operating system. The technology was introduced to simplify the work of system administrators in large companies that manage networks with a large number of stations.
Since the AMT SOL interface functions inside Intel ME, it is separated from the main operating system — that is, the environment where the firewalls and antivirus software are running. Moreover, AMT SOL works even when the computer is turned off, but still physically connected to the network - this allows you to transmit data using the TCP protocol, which opens up certain opportunities for attackers.
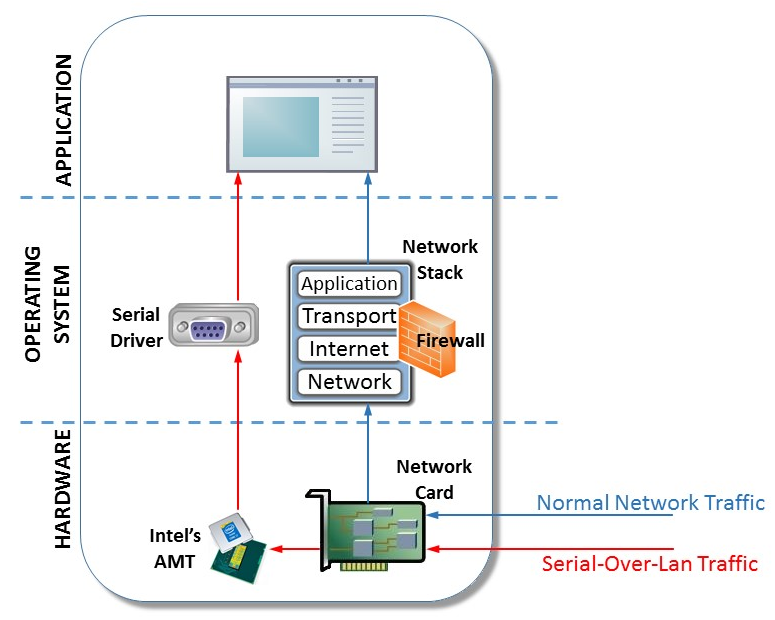 AMT SOL components ( Source )
AMT SOL components ( Source )
The AMT SOL features are disabled by default and can only be activated by a system administrator, which reduces the level of risk. However, in large companies, SOL is often used for its intended purpose. Having played on the features of the solution, a group of hackers wrote malicious code that allows them to steal data through SOL.
Microsoft experts claim that the malware that uses SOL to steal data is backed up by Platinum, which has been active in South and Southeast Asia for several years. The group was first spotted in 2009 and has since carried out many attacks. Last year, it was reported that Platinum installed malware with the help of hotpatching technology, a mechanism that allows Microsoft to install updates without having to restart the computer.
The SOL protocol implemented in the Platinum tool uses the Redirection Library API (imrsdk.dll). Information transfer is carried out using IMR_SOLSendText () and IMR_SOLReceiveText () calls, which are analogues of send () and recv (). The protocol used is identical to the TCP protocol, with the exception of the added variable-length header for tracking errors in data transmission (CRC-16, etc.). This video shows how Platinum is used to send malware to the system.
It is worth noting that the possibility of such an attack has been discussed before, but so far there have been no attempts to use Intel AMT SOL for data output.
“This is a typical example of how technology designed to simplify the lives of users or system administrators is transformed into an actual vulnerability,” said Ksenia Shilak, Sales Director at SEC-Consult. - And this is, in fact, bad news: if any vulnerability was used, it could be fixed. And in this case, the use of architectural features. "
PS Other materials on the topic from our blog:
 / photo by Andi Weiland CC
/ photo by Andi Weiland CCAt the beginning of the year, Intel was already faced with dangerous vulnerabilities in Intel ME. Then the problem affected solutions of Intel Active Management Technology (AMT), Intel Standard Management Manageability (ISM), Intel Small Business Technology (SBT) and allowed an unprivileged attacker to gain remote access to hardware management. The vulnerability, designated CVE-2017-5689 , the developers of the IT giant patch.
')
And here is a new situation, but already connected with the peculiarities of the work of Intel Serial-over-LAN. AMT SOL is part of the Intel Management Engine (ME) - a separate processor embedded in an Intel CPU that runs on its own operating system. The technology was introduced to simplify the work of system administrators in large companies that manage networks with a large number of stations.
Since the AMT SOL interface functions inside Intel ME, it is separated from the main operating system — that is, the environment where the firewalls and antivirus software are running. Moreover, AMT SOL works even when the computer is turned off, but still physically connected to the network - this allows you to transmit data using the TCP protocol, which opens up certain opportunities for attackers.

The AMT SOL features are disabled by default and can only be activated by a system administrator, which reduces the level of risk. However, in large companies, SOL is often used for its intended purpose. Having played on the features of the solution, a group of hackers wrote malicious code that allows them to steal data through SOL.
Microsoft experts claim that the malware that uses SOL to steal data is backed up by Platinum, which has been active in South and Southeast Asia for several years. The group was first spotted in 2009 and has since carried out many attacks. Last year, it was reported that Platinum installed malware with the help of hotpatching technology, a mechanism that allows Microsoft to install updates without having to restart the computer.
The SOL protocol implemented in the Platinum tool uses the Redirection Library API (imrsdk.dll). Information transfer is carried out using IMR_SOLSendText () and IMR_SOLReceiveText () calls, which are analogues of send () and recv (). The protocol used is identical to the TCP protocol, with the exception of the added variable-length header for tracking errors in data transmission (CRC-16, etc.). This video shows how Platinum is used to send malware to the system.
It is worth noting that the possibility of such an attack has been discussed before, but so far there have been no attempts to use Intel AMT SOL for data output.
“This is a typical example of how technology designed to simplify the lives of users or system administrators is transformed into an actual vulnerability,” said Ksenia Shilak, Sales Director at SEC-Consult. - And this is, in fact, bad news: if any vulnerability was used, it could be fixed. And in this case, the use of architectural features. "
PS Other materials on the topic from our blog:
- A world-wide cyber attack: how to avoid becoming a victim and defend yourself against a WannaCry trojan
- Building Qualified and Secured Infrastructures Based on VMware Solutions
- vCloud Availability: deep immersion in traffic replication
- vCloud Director: how to create a secure connection between two organizations
- Top 12 Cloud Security Threats According to the Cloud Security Alliance
Source: https://habr.com/ru/post/330572/
All Articles