Security Week 22: Vulnerability was found in Samba, ShadowBrokers opened a subscription to exploits, phishers massively mastered HTTPS
 They say that if you look at port 445 for a long time, a network worm will look out. In recent weeks, he has attracted so much attention that vulnerabilities have come to light, even in UNABLE (as everyone knows) Linux. More precisely, in the popular network file system Samba, without which Linux cannot make friends with Windows on the network.
They say that if you look at port 445 for a long time, a network worm will look out. In recent weeks, he has attracted so much attention that vulnerabilities have come to light, even in UNABLE (as everyone knows) Linux. More precisely, in the popular network file system Samba, without which Linux cannot make friends with Windows on the network.Directly found a bug to the known set of exploits has no relation, however comparisons suggest themselves - the same protocol and a similar usage scenario. It’s enough for an attacker to find Linux with an SMB resource open for writing from the Internet, download the library there, which the server will happily launch. This process is elementary automated, that is, the vulnerability clearly smells of network worms.
Xavier Mertens from the SANS Internet Storm Center pointed out that the vulnerability can be used trivially, “using one line of code exploit”. Rapid7 scanned the Network, as it is now fashionable, and found there 104 thousand systems with vulnerable Samba. Then they remembered port 139, scanned it, and found 110 thousand systems already.
You might say that putting Linux and keeping SMBs open to the world is a sore idea. And in something you are right. However, there is a large reservoir of devices for which this is a normal scenario. Speech about network storages, which often use Linux, but oh how are updated infrequently.
')
By the way, for those versions of Samba that stand at 90% of vulnerable systems, there is still no patch, so there are no technical details either (although some have already posted the proof of concept code on Twitter). Mertens recommends that if there is no update for this in your account, add the parameter
nt pipe support = no [global] section of the smb.cof file. Just in case.ShadowBrokers will merge subscription exploits
News After warming up the market, ShadowBrokers began to monetize, announcing the subscription price for monthly archives of hacker tools from a well-known office. It is simple for gentlemen in black hats, they want - they buy, they don’t want - they don’t buy, but their light-minded colleagues face a serious ethical dilemma.
 On the one hand, it is no good to supply money with a frankly cybercriminal group. On the other hand, these exploits and Trojans will definitely fall into bad hands, so security guards need to be prepared. The delay can be punished by an epidemic worse than that, so that some of the information security companies must have subscribed. The price of 100 Zcash (about $ 23,000) monthly looks low, given the powerful “advertising campaign” conducted by WannaCry.
On the one hand, it is no good to supply money with a frankly cybercriminal group. On the other hand, these exploits and Trojans will definitely fall into bad hands, so security guards need to be prepared. The delay can be punished by an epidemic worse than that, so that some of the information security companies must have subscribed. The price of 100 Zcash (about $ 23,000) monthly looks low, given the powerful “advertising campaign” conducted by WannaCry.The ShadowBrokers plan is like trying to provoke an arms race between white hats and their black opponents and how to make money from it. It is difficult to predict how many will lead to this. At least, the motivation of the group has become clearer - this is not messianism, but a criminal business project.
Phishing sites massively use https
News Users have long been accustomed to the fact that it is safe to surf only via HTTPS. Like, see the green lock to the left of the url - you can safely drive in your credentials. Well, many are accustomed to this and trust the site, if the castle is green. In vain.
The desire of crypto enthusiasts to encrypt the entire Internet and all communications in it led to the emergence of automatic issuance of certificates, such as Let's Encrypt. Somehow I don’t want to call it a certifying authority, since it doesn’t certify anything, in general. As a result, any phisher, having created a fake site, quickly acquires a green lock that helps a lot to fool people.
According to the findings of researchers from the Cisco Talos group, such malicious use of HTTPS has become widespread on the Internet, and it is time to sound the alarm. According to the SSL Store , last year, 15,270 free SSL certificates were issued for sites with the word “PayPal” in the domain name or owner ID.
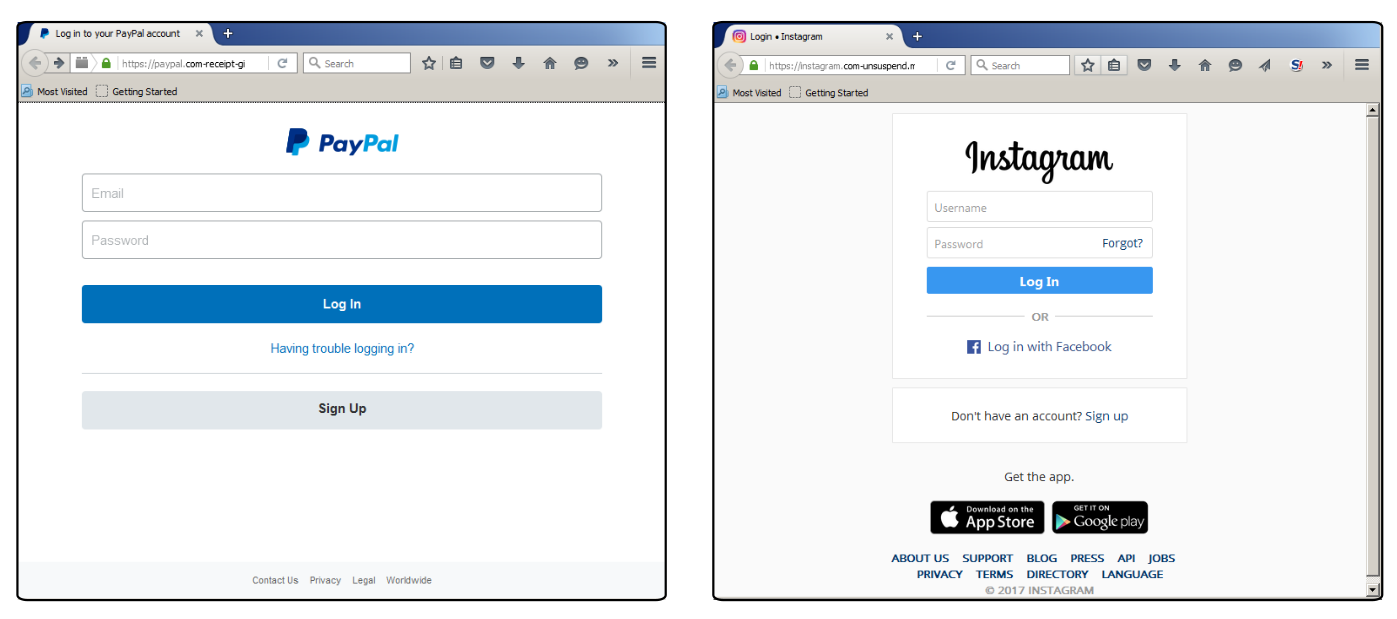 What to do with it is not very clear. Even if you teach users to carefully read the url, it will help only partly, since it is not always clear whether this is a phishing domain, or just one of the many legitimate domains of the organization. Similarly, with the verification of the certificate - every time you need to know exactly the name of the legal entity. Sooner or later, help will come from the side of technology, but for now, one can only advise to “loosen one's eyes.”
What to do with it is not very clear. Even if you teach users to carefully read the url, it will help only partly, since it is not always clear whether this is a phishing domain, or just one of the many legitimate domains of the organization. Similarly, with the verification of the certificate - every time you need to know exactly the name of the legal entity. Sooner or later, help will come from the side of technology, but for now, one can only advise to “loosen one's eyes.”
Antiquities
"Klaeren-971"
Resident non-dangerous virus, encrypted, infects .COM- and .EXE-files, except COMMAND.COM, when they start. Intercepts int 21h. In May, it erases CMOS, fills the screen with the words “Klaeren Hac, Hac!” And at the same time flashes with the indicators NumLock, CapsLock, ScrollLock.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 73.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/330116/
All Articles