"Confrontation" PHDays VII: Beginners are lucky or rob banks, break GSM
This year we (CARK Kazakhstan) for the first time participated in the Battle of Attackers and Defenders (The Standoff) on PHDays as evil hackers. In the post we will try to describe how the event took place, due to which we managed to win and what ultimately lay in that metal case.
Introductory
We have been visiting PHDays for several years with our team and mostly won small contests. Therefore, this year we were only interested in winning the main competition.
')
Composition
This year we went to the conference with a team of 13 people: pentesters, reversers, hardwarders, system administrators, Ph.D., students, students and fitness trainers. But seven people participated directly in the confrontation.

A few links to start:
1) The Standoff rules themselves
2) On Habré there are already several posts on “Confrontation” from Defenders and SOC: one and two .
Training
From the equipment we took:
MikroTik RB951Ui-2HnD - 1pc.
Zyxel Keenetic - 1 pc. (lost)
Tplink 8port hub - 1pc
Alfa Usb Wifi Adapter - 5pcs
SDR, Proxmark with LF and HF antennas, BladeRF, HackRF, equipment for GSM, etc. As you can guess, we were watched very carefully at the airport. And our hands itched to raise their own base station during the flight to communicate.
Also in the office in Astana, a brutal machine (we call it Brute Alice) was prepared with the Radeon R9 290X on board and access via VPN. This baby played a key role in our victory.
First day
We arrived at the site as early as 8-9 in the morning. We were among the first and managed to take a table in the farthest corner. There was no access to the local area network yet, and we started working on organizing the work space: we bought local SIMs for the Internet, set up a router, set firewall rules, created a wifi access point KNFC (Kairat Nurtas Fan Club, a club of fans of the local superstar Kairat Nurtas), which at the end competitions other teams mercilessly attacked, and began to expect the start of the competition. By 12 o'clock, access to the internal network appeared and we were given a login and password to the portal with tasks. The standoff has begun.
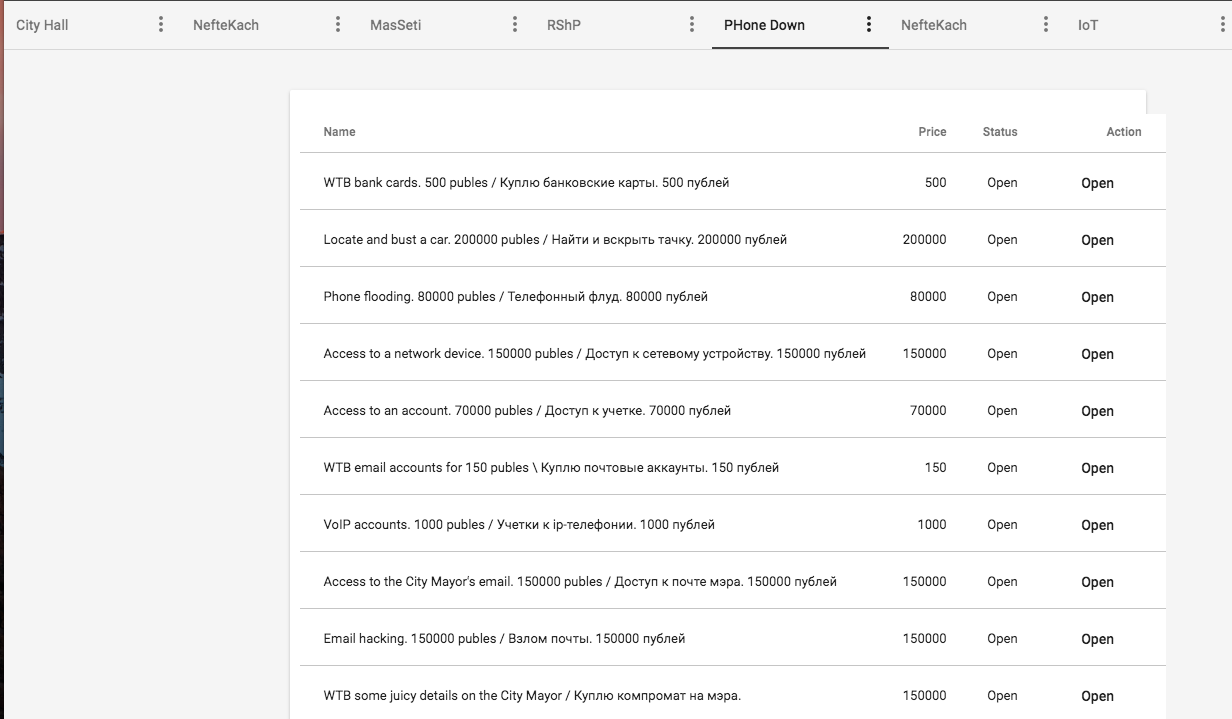
System with taska.
After viewing the list of tasks (there were about 50 of them), part of the team began to scan subnets, another part - look for vulnerabilities on web resources, and hardwarders immediately switched to tasks from GSM. Two guys made themselves badges for the media and started walking around the teams of the attackers and defenders, interviewing (and quite successfully!) And photographing the desktops of the participants. They managed to do a lot of pictures.
From mining:
Password from teamviewer one of the organizers of the competition. Gave access to the screen with the control of traffic lights in the city. And we did not miss the opportunity to take advantage of this: we managed to stop the movement in the city, but nothing was counted for “peeping” =) Although there were no prohibitions in the rules of participation in social engineering.
Until the evening, we mainly carried out reconnaissance, tried to exploit services. They delved into the essence of the infrastructure, dealt with tasks, threw minor vulnerabilities into the local bugbounty portal and did not even stay in the top 5. In the evening, the hardwarders were able to carry out the interception of compromising materials to the mayor of the city, which immediately provided us with the first place until the morning. For this task, 150 000 posts were given (the game currency of the city).
After our hardwarders from the press changed their clothes back to the participants of the confrontation, they began to pray to the GSM-network gods.

And having received their support, they rushed to the GSM network.
The primary scan on BladeRF using GnuRadio blocks to decrypt GSM traffic showed that the network works completely on 2G and several devices with specific numbers are connected to it (presumably bots in the base station itself), as well as several devices with numbers that are formed from IMSI Sims. We determined the latter by connecting to the network using ordinary phones (in Kazakhstan, they are called “ZhaiFony”). At the base station there was no identification via IMSI, which made it easier for us to connect to the network using jajfonov. But we were ready for a different outcome: we would simply create virtual sims based on osmocombb programs and the motorola c118 phone, which would have IMSI with MNC and MMC identification as the base station.
But then we got stuck: we could not get more data from BladeRF and GnuRadio, but it was clearly visible that the packets were still present. Then we decided to connect to the 2G network scan what was created to work in 2G and feels like a fish in it - a motorola c118 phone with a Calypso GSM modem inside and osmocombb programs on the backend. Since the task was to scan the network, we used the osmocombb program branch called sylvain. In the first minutes of network scanning, we realized that it does not encrypt, or rather, encryption is implemented at the A5 / 0 level.
We listened to the network using the implementation of the stack of programs:
1) On the motorola itself, the osmocombb / master firmware was launched for compal e88 of the first layer layer1.highram.bin. This is the layer1 of the OSI model, which implements the entire physical part of the modem.
2) The host launched an osmocombb / sylvian receiver in the misc - ccch_scan folder. This tool allows you to receive data from layer1 and manages it to search for data from a specific ARFCN, that is, the base station on the CCCH. Then it allows you to send them to the desired address, in our case, the loopback.
3) Loopback with us listened to all your favorite wireshark, which showed the scan results.
The screen on which it is clear that we started for this task:

At some point, we noticed a high activity of two clients of the network: they were actively exchanging messages. As soon as their correspondence talked about money (well, our hardwarders know English perfectly), we recorded the entire conversation. It turned out that the conversation was between the mayor of the city and someone else about affiliated structures and corruption, “great! - we thought, - we spotted you, bad-bad mayor! ”.
Screen on which correspondence in wireshark is visible:

And of course, the correspondence itself:
Night
After we climbed to the first line, a keen desire arose to hold out there to the end. Our team decided to stay overnight and continue the night battles. Some of the guys switched to SCADA systems, others tried to break the bank itself, in which participants and city residents had money, the hardwarders continued to hack GSM (but by the middle of the night they still went to bed, because some genius turned off the GSM network, which the respected the organizers had to re-raise in the morning). A git-repository with the source code of the bank and an API was found, through which it was possible to pull out the logins and md5-hashes of the bank users. And then the heat began. The RDot team for 5-10 minutes before us found the same vulnerability and has already started withdrawing users' money to their accounts. We also quickly began to change passwords and withdraw money to ourselves. In the process of transferring money, we noticed that someone is trying to divert our session through the XSS-sniffer, good, they did not succeed. XSS did not work, but we decided to punish the negligent attacker and began to generate fake cookies, similar to the original ones, and send it all to a remote attacking server in order to fill them with false data. We also discovered the Server-side Template Injection vulnerability, but we didn’t have time to unleash it. Most of the users had four or five-digit passwords, but some of the fattest accounts had 12-digit passes, which only got lost in the morning. In the morning, we and the RDot team removed almost all the money from the accounts with easy passwords. At this point, we noticed that the password from the bank account, issued to us by the organizers, consisted of only 12 hex characters in lower case. We assumed that the passwords to the bank accounts of other participants were generated in the same way, and, setting the “correct” mask, we began to crack the hashes of the opposing teams, at the same time changing our own password to a more complex one. After a couple of hours, baby Alice gave us the password from the bank account of one of the attacking teams! 5 minutes and we managed to transfer all their money to your account.
Unfortunately, the organizers did not count the transfer of money from the account of the other team and returned the balance to them.
By morning, the Defenders woke up, realized that they had not followed the bank, and temporarily closed it.
Second day
Pentesters continued to find minor vulnerabilities and toss them into the bugbounty. The hardwarders woke up and started performing the next GSM call. By lunchtime, they managed to perform a task with the interception of the machine. Here is what the team member himself writes:
“I'll tell you about the task with the search and interception of the stolen car. The task itself was difficult, but some hacker made it more fun. We were already able to clone the phone of the thief, and the last task remained - to write the number of the tracker inside the stolen vehicle and take control, but someone had tipped the tracker. And when I started sending commands to the tracker, this someone started to answer for him. At some point, he sends me a message “u win!”, And I run to the organizer - look! And they are with a surprised face: we did not program the robot to such answers. Then we learned that some kind of hacker troll us. He raised the spirits of the whole team, the organizers and the participants. ”
But it is worth highlighting the technical details of intercepting a car tracker.
First of all, we found commands sent to the tracker, and tried to send the same commands, but this didn’t work - it means that the tracker checks the sending number. This did not stop our hardwarders, because the support of the GSM gods has already been received, and they need more hack. The guys got the thief in the TMSI data packets and forged the same one, which should have given our virtual sim card the same number as that of the thief, but this did not help either.
It was decided to completely copy the mobile phone thief - we began to hunt for his IMSI. Every mobile phone changes its TMSI from time to time, and at this moment, in an open form, you can catch its IMSI if you look for localization packages, or rather its updates. Having found such a package, we received the data to clone the phone thief. We cloned it using software from osmocombb and virtual sims in motorola c118. Having gained control, we determined the location of the car and transferred control to one of our zhayfon, so that no one could repeat our success, because we stopped sending commands and the broadcast became quiet after the hunt.
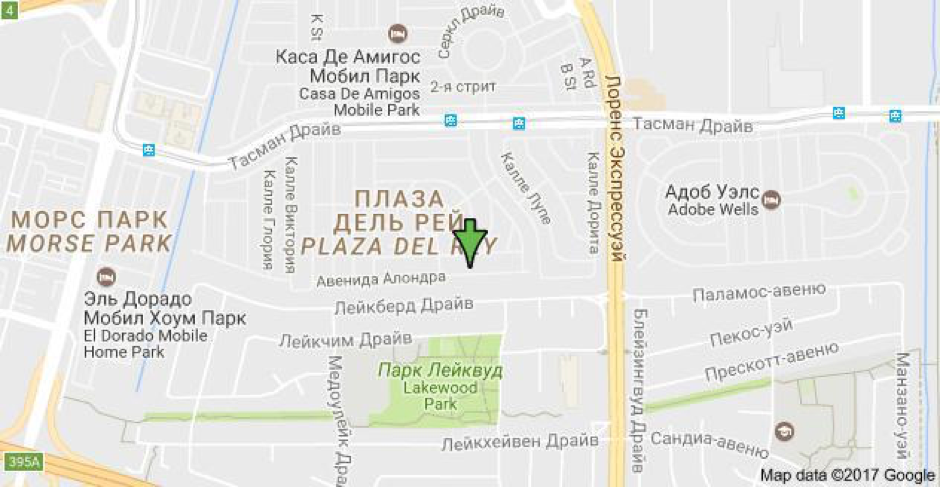
Screen interception control:

And, of course, I remember the location of the car itself - oddly enough, it was in Silicon Valley:
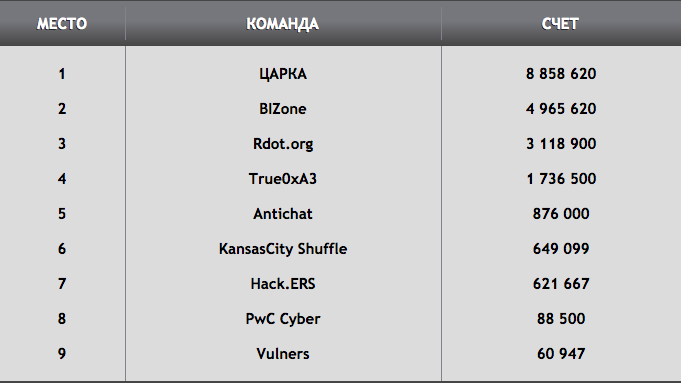
The bank did not work the whole day. By lunchtime, we already got rid of the passwords from the “fat” accounts and we sat waiting for the organizers to open it at least temporarily, and it happened! We got into the 5-minute window when they had to start the bank in order to change the passwords for the teams (after our teams were hacked), and at that moment we managed to transfer another 3 million posts to our account. This moment was captured on video when the Buffalos took the stage and we returned the lead in real time.
So it happened to hold out until the end of the event. Until the last moment, they doubted whether it would be possible to keep the first place. But luck and the GSM Gods were on our side.

In general, the organization was at a high level, the organizers were very friendly and helped with technical problems. There were a lot of tasks, but it so happened that part of the team concentrated on the bank and stealing money from the accounts, although according to the organizers, there should not have been vulnerabilities in the bank service.
PS: and the suitcasecontained the cash prize was actually empty. The money was in a separate envelope.
Introductory
We have been visiting PHDays for several years with our team and mostly won small contests. Therefore, this year we were only interested in winning the main competition.
')
Composition
This year we went to the conference with a team of 13 people: pentesters, reversers, hardwarders, system administrators, Ph.D., students, students and fitness trainers. But seven people participated directly in the confrontation.

A few links to start:
1) The Standoff rules themselves
2) On Habré there are already several posts on “Confrontation” from Defenders and SOC: one and two .
Training
From the equipment we took:
MikroTik RB951Ui-2HnD - 1pc.
Zyxel Keenetic - 1 pc. (lost)
Tplink 8port hub - 1pc
Alfa Usb Wifi Adapter - 5pcs
SDR, Proxmark with LF and HF antennas, BladeRF, HackRF, equipment for GSM, etc. As you can guess, we were watched very carefully at the airport. And our hands itched to raise their own base station during the flight to communicate.
Also in the office in Astana, a brutal machine (we call it Brute Alice) was prepared with the Radeon R9 290X on board and access via VPN. This baby played a key role in our victory.
First day
We arrived at the site as early as 8-9 in the morning. We were among the first and managed to take a table in the farthest corner. There was no access to the local area network yet, and we started working on organizing the work space: we bought local SIMs for the Internet, set up a router, set firewall rules, created a wifi access point KNFC (Kairat Nurtas Fan Club, a club of fans of the local superstar Kairat Nurtas), which at the end competitions other teams mercilessly attacked, and began to expect the start of the competition. By 12 o'clock, access to the internal network appeared and we were given a login and password to the portal with tasks. The standoff has begun.

System with taska.
After viewing the list of tasks (there were about 50 of them), part of the team began to scan subnets, another part - look for vulnerabilities on web resources, and hardwarders immediately switched to tasks from GSM. Two guys made themselves badges for the media and started walking around the teams of the attackers and defenders, interviewing (and quite successfully!) And photographing the desktops of the participants. They managed to do a lot of pictures.
From mining:
Password from teamviewer one of the organizers of the competition. Gave access to the screen with the control of traffic lights in the city. And we did not miss the opportunity to take advantage of this: we managed to stop the movement in the city, but nothing was counted for “peeping” =) Although there were no prohibitions in the rules of participation in social engineering.

Until the evening, we mainly carried out reconnaissance, tried to exploit services. They delved into the essence of the infrastructure, dealt with tasks, threw minor vulnerabilities into the local bugbounty portal and did not even stay in the top 5. In the evening, the hardwarders were able to carry out the interception of compromising materials to the mayor of the city, which immediately provided us with the first place until the morning. For this task, 150 000 posts were given (the game currency of the city).
After our hardwarders from the press changed their clothes back to the participants of the confrontation, they began to pray to the GSM-network gods.

And having received their support, they rushed to the GSM network.
The primary scan on BladeRF using GnuRadio blocks to decrypt GSM traffic showed that the network works completely on 2G and several devices with specific numbers are connected to it (presumably bots in the base station itself), as well as several devices with numbers that are formed from IMSI Sims. We determined the latter by connecting to the network using ordinary phones (in Kazakhstan, they are called “ZhaiFony”). At the base station there was no identification via IMSI, which made it easier for us to connect to the network using jajfonov. But we were ready for a different outcome: we would simply create virtual sims based on osmocombb programs and the motorola c118 phone, which would have IMSI with MNC and MMC identification as the base station.
But then we got stuck: we could not get more data from BladeRF and GnuRadio, but it was clearly visible that the packets were still present. Then we decided to connect to the 2G network scan what was created to work in 2G and feels like a fish in it - a motorola c118 phone with a Calypso GSM modem inside and osmocombb programs on the backend. Since the task was to scan the network, we used the osmocombb program branch called sylvain. In the first minutes of network scanning, we realized that it does not encrypt, or rather, encryption is implemented at the A5 / 0 level.
We listened to the network using the implementation of the stack of programs:
1) On the motorola itself, the osmocombb / master firmware was launched for compal e88 of the first layer layer1.highram.bin. This is the layer1 of the OSI model, which implements the entire physical part of the modem.
2) The host launched an osmocombb / sylvian receiver in the misc - ccch_scan folder. This tool allows you to receive data from layer1 and manages it to search for data from a specific ARFCN, that is, the base station on the CCCH. Then it allows you to send them to the desired address, in our case, the loopback.
3) Loopback with us listened to all your favorite wireshark, which showed the scan results.
The screen on which it is clear that we started for this task:

At some point, we noticed a high activity of two clients of the network: they were actively exchanging messages. As soon as their correspondence talked about money (well, our hardwarders know English perfectly), we recorded the entire conversation. It turned out that the conversation was between the mayor of the city and someone else about affiliated structures and corruption, “great! - we thought, - we spotted you, bad-bad mayor! ”.
Screen on which correspondence in wireshark is visible:

And of course, the correspondence itself:
Correspondence
Secret sms chat:
to: 901708
from: 901706
sms: Dear Tomas, Can I call you now?
to: 901706
from: 901708
sms: Hello. I thought we already discounted this yesterday. I have no time to talk with you ...
to: 901706
from: 901708
sms: how much?
to: 901708
from: 901706
sms: 10,000 EUR.
from: 901708
to: 901706
sms: Well, ok. I'll wait for your payment. Hereby you can open five sale points downtown.
from: 901708
to: 901706
sms: And, btw: nobody. This is our both interest.
to: 901708
from: 901706
sms: Dear Tomas, Can I call you now?
to: 901706
from: 901708
sms: Hello. I thought we already discounted this yesterday. I have no time to talk with you ...
to: 901706
from: 901708
sms: how much?
to: 901708
from: 901706
sms: 10,000 EUR.
from: 901708
to: 901706
sms: Well, ok. I'll wait for your payment. Hereby you can open five sale points downtown.
from: 901708
to: 901706
sms: And, btw: nobody. This is our both interest.
Night
After we climbed to the first line, a keen desire arose to hold out there to the end. Our team decided to stay overnight and continue the night battles. Some of the guys switched to SCADA systems, others tried to break the bank itself, in which participants and city residents had money, the hardwarders continued to hack GSM (but by the middle of the night they still went to bed, because some genius turned off the GSM network, which the respected the organizers had to re-raise in the morning). A git-repository with the source code of the bank and an API was found, through which it was possible to pull out the logins and md5-hashes of the bank users. And then the heat began. The RDot team for 5-10 minutes before us found the same vulnerability and has already started withdrawing users' money to their accounts. We also quickly began to change passwords and withdraw money to ourselves. In the process of transferring money, we noticed that someone is trying to divert our session through the XSS-sniffer, good, they did not succeed. XSS did not work, but we decided to punish the negligent attacker and began to generate fake cookies, similar to the original ones, and send it all to a remote attacking server in order to fill them with false data. We also discovered the Server-side Template Injection vulnerability, but we didn’t have time to unleash it. Most of the users had four or five-digit passwords, but some of the fattest accounts had 12-digit passes, which only got lost in the morning. In the morning, we and the RDot team removed almost all the money from the accounts with easy passwords. At this point, we noticed that the password from the bank account, issued to us by the organizers, consisted of only 12 hex characters in lower case. We assumed that the passwords to the bank accounts of other participants were generated in the same way, and, setting the “correct” mask, we began to crack the hashes of the opposing teams, at the same time changing our own password to a more complex one. After a couple of hours, baby Alice gave us the password from the bank account of one of the attacking teams! 5 minutes and we managed to transfer all their money to your account.
Unfortunately, the organizers did not count the transfer of money from the account of the other team and returned the balance to them.
By morning, the Defenders woke up, realized that they had not followed the bank, and temporarily closed it.
Second day
Pentesters continued to find minor vulnerabilities and toss them into the bugbounty. The hardwarders woke up and started performing the next GSM call. By lunchtime, they managed to perform a task with the interception of the machine. Here is what the team member himself writes:
“I'll tell you about the task with the search and interception of the stolen car. The task itself was difficult, but some hacker made it more fun. We were already able to clone the phone of the thief, and the last task remained - to write the number of the tracker inside the stolen vehicle and take control, but someone had tipped the tracker. And when I started sending commands to the tracker, this someone started to answer for him. At some point, he sends me a message “u win!”, And I run to the organizer - look! And they are with a surprised face: we did not program the robot to such answers. Then we learned that some kind of hacker troll us. He raised the spirits of the whole team, the organizers and the participants. ”
But it is worth highlighting the technical details of intercepting a car tracker.
First of all, we found commands sent to the tracker, and tried to send the same commands, but this didn’t work - it means that the tracker checks the sending number. This did not stop our hardwarders, because the support of the GSM gods has already been received, and they need more hack. The guys got the thief in the TMSI data packets and forged the same one, which should have given our virtual sim card the same number as that of the thief, but this did not help either.
It was decided to completely copy the mobile phone thief - we began to hunt for his IMSI. Every mobile phone changes its TMSI from time to time, and at this moment, in an open form, you can catch its IMSI if you look for localization packages, or rather its updates. Having found such a package, we received the data to clone the phone thief. We cloned it using software from osmocombb and virtual sims in motorola c118. Having gained control, we determined the location of the car and transferred control to one of our zhayfon, so that no one could repeat our success, because we stopped sending commands and the broadcast became quiet after the hunt.
Screen interception control:

And, of course, I remember the location of the car itself - oddly enough, it was in Silicon Valley:

The bank did not work the whole day. By lunchtime, we already got rid of the passwords from the “fat” accounts and we sat waiting for the organizers to open it at least temporarily, and it happened! We got into the 5-minute window when they had to start the bank in order to change the passwords for the teams (after our teams were hacked), and at that moment we managed to transfer another 3 million posts to our account. This moment was captured on video when the Buffalos took the stage and we returned the lead in real time.
So it happened to hold out until the end of the event. Until the last moment, they doubted whether it would be possible to keep the first place. But luck and the GSM Gods were on our side.


In general, the organization was at a high level, the organizers were very friendly and helped with technical problems. There were a lot of tasks, but it so happened that part of the team concentrated on the bank and stealing money from the accounts, although according to the organizers, there should not have been vulnerabilities in the bank service.
PS: and the suitcase
Source: https://habr.com/ru/post/329980/
All Articles