How to use a token to make a Windows domain safer? Part 2

Email is not just a way to deliver messages today. It can be safely called the most important means of communication, information distribution and management of various processes in business. But can we always be sure of the correctness and safety of its work?
In fact, email vulnerability is a big problem.
Email is one of the oldest network services. It appeared in 1982, and at that time security issues on the Internet were not as acute as they are now. According to Mimecast's research, about 94% of the surveyed companies are completely powerless against e-mail leakage.
News feeds are regularly filled with messages about hacked e-mails of politicians, athletes, artists and other public people. Such situations could be avoided, for this you just need to know about the ability to encrypt emails.
After all, it is inexpensive, and works reliably.
What can you do to protect email?
In the last article, “How can I use a token to make a Windows domain safer? Part 1 ” we told you how to configure secure domain login. They recalled what is two-factor authentication and what are its advantages.
In this article we will talk about email security.
Standard mail protocols do not include obvious security mechanisms that would guarantee the authorship of the letters and ensure simple and easy verification. This situation with the protection of mail systems allows attackers to create letters with fake addresses. Therefore, one cannot be 100% sure that the person whose data is indicated in the “From” field is really the author of the letter. Also, the body of an e-mail is easy to change, because there are no means of checking the integrity and when sending through multiple servers, the letter can be read and changed.
One of the ways to ensure the confidentiality of correspondence is to encrypt messages, and one of the ways to verify the integrity of a letter and establish authorship is by signing it with an electronic signature .
The encrypted message will be available for reading only to those recipients who have a private key corresponding to the public one, with which the message was encrypted. Any other recipient will not even be able to open the letter.
How does the S / MIME protocol work?
S / MIME (Secure / Multipurpose Internet Mail Extensions) protocol provides authentication, message integrity, authorship, and data security.
S / MIME identifies the holder of the public key using an X.509 certificate.
S / MIME provides protection against three types of security breaches:
- perusal (opening and viewing letters without the knowledge of the author and the recipient);
- distortion (change the text of letters);
- falsification (substitution of letters).
S / MIME uses a digital signature to protect against mail corruption or tampering. Having a digital signature ensures that the message has not been changed during the transfer. In addition, does not allow the sender of the message to give up their authorship.
However, a digital signature in itself does not guarantee the transfer of messages in a confidential manner. In S / MIME, this function is encrypted. Roughly speaking, it is performed using an asymmetric cryptographic algorithm.
The S / MIME specification defines two types of MIME files: one for digital signatures, the other for message encryption. Both types are based on the syntax of cryptographic messages of the PKCS # 7 standard.
If the message must be encrypted, and some attributes must be assigned to the ciphertext, then nested envelopes are used. The outer and inner envelopes are designed to protect the digital signature, and the intermediate envelope - to protect the ciphertext.
When working with S / MIME, you must have two keys - open and closed. The keys are accompanied by a certificate, that is, information about the user, which allows to determine that he is exactly who he claims to be. The certificate can be compared with some kind of electronic passport, a kind of identity card.
To send an encrypted message, you must obtain the public key of the recipient of the message and, roughly speaking, encrypt the message using it.
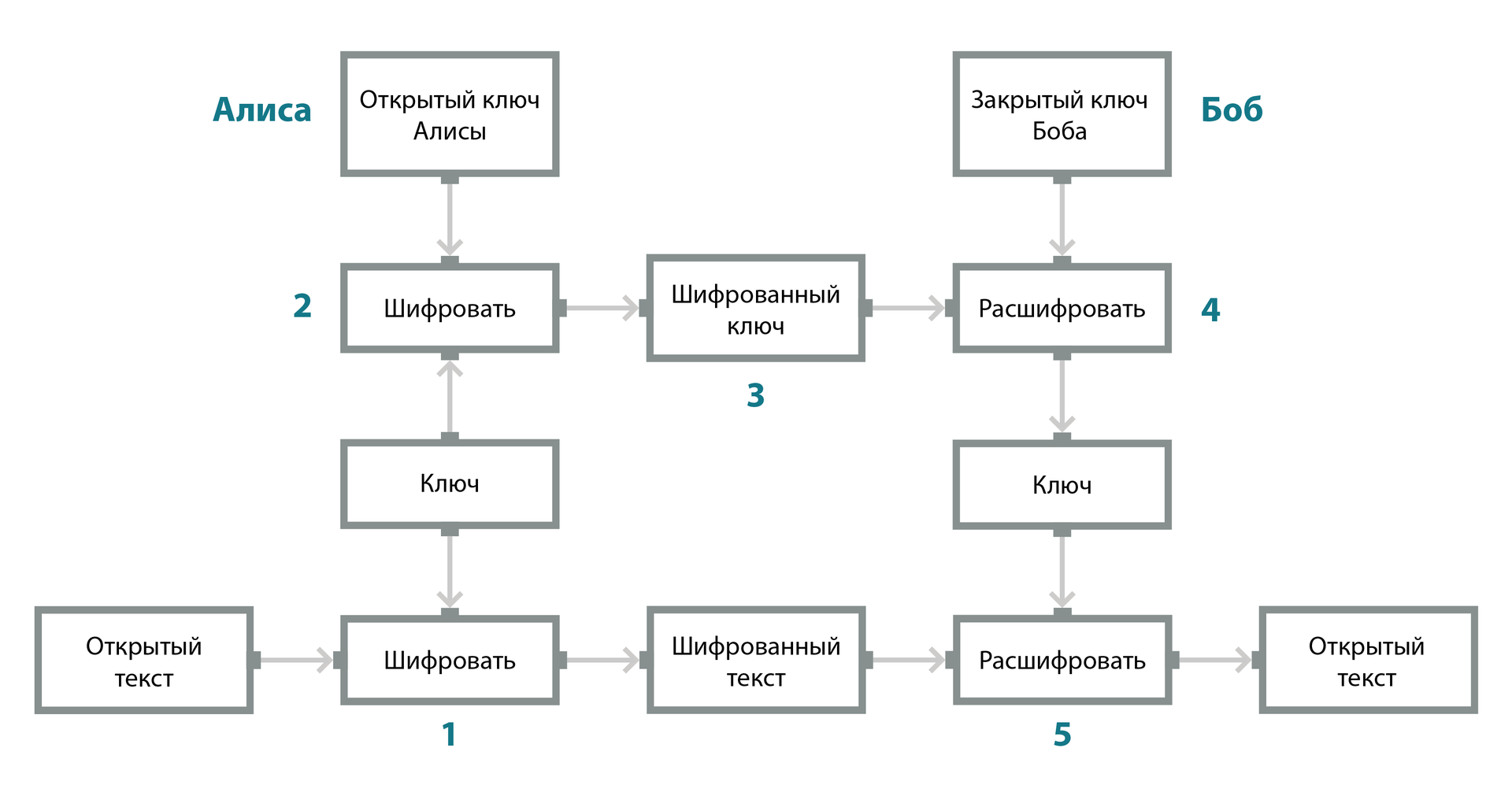
The figure shows the steps for encrypting an email in S / MIME:
- Alice creates a message that she wants to encrypt and send to Bob. Decides to send it to Bob. The messaging client, seeing that the letter needs to be encrypted, generates a random encryption key (the private key, which is usually called a session key, then a new random key is generated every time an encrypted message is sent) and encrypts the message with it.
- The session key is encrypted with the recipient’s public key and attached to the message, which means that only the Bob’s private key can decrypt it.
- The encrypted text and encrypted key are sent to Bob via SMTP (Simple Mail Transfer Protocol).
- Bob's mail client uses Bob's private key to decrypt the encrypted key and gets the decrypted session key. Privacy is guaranteed here, because only the Bob private key can be used to decrypt the session key needed to decrypt the message.
- Bob's mail client uses the decrypted session key to decrypt the mail, the result of which is the decrypted original message that was sent by Alice.
Encryption does not protect the message from forgery and content changes during transmission. Therefore, along with encryption to protect the email, you must use an electronic signature.
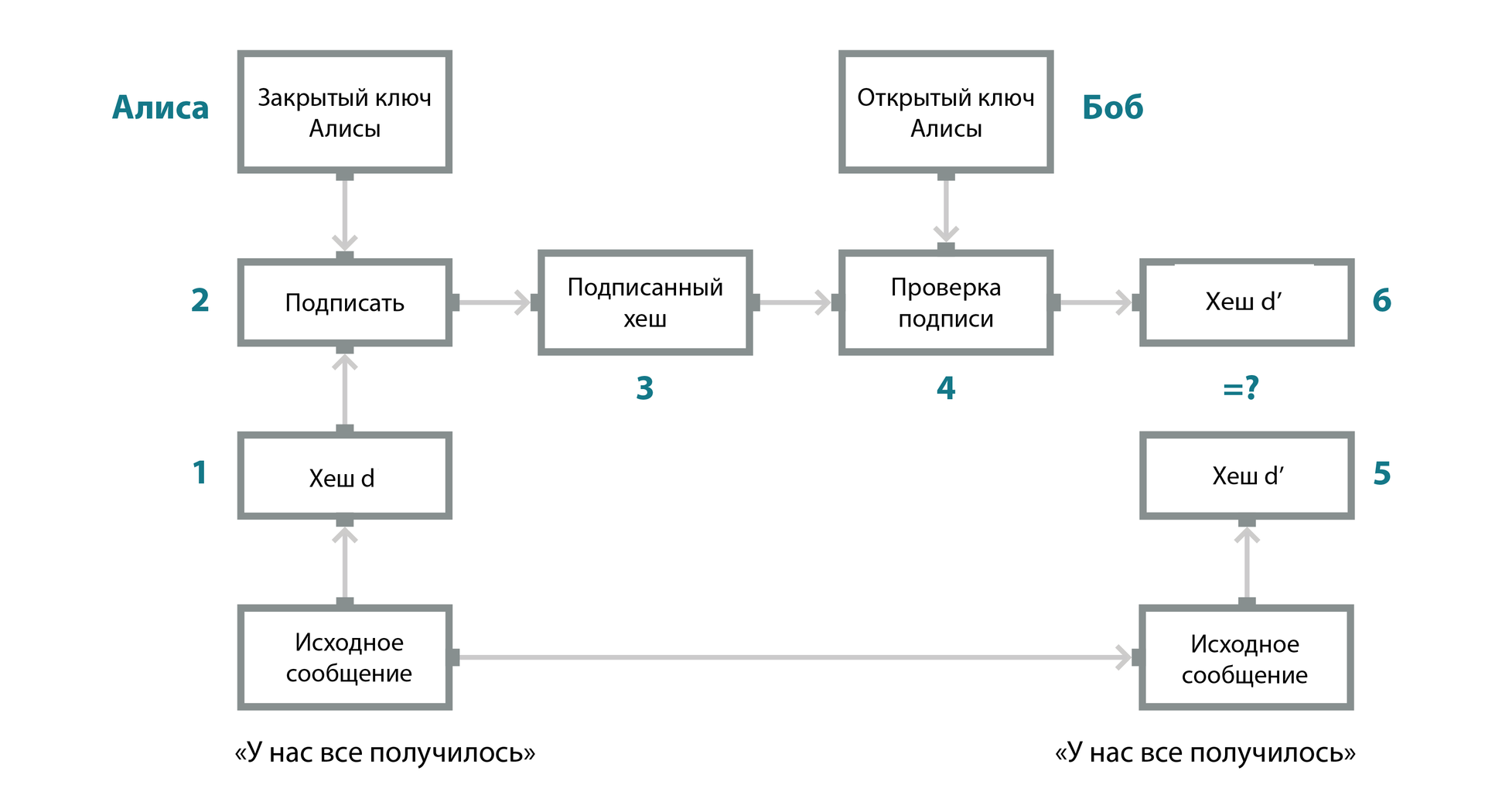
The figure shows the steps of authenticating and detecting a fake message using an electronic signature:
- Alice creates the message and signs it electronically. The mail client, seeing that the message must be signed, generates a hash of Alice's message (the result is the hash d - “digest”).
- The hash is signed by the messaging client using Alice's private key. This means that only her public key will be able to verify the signature on this hash.
- The signed hash along with the message is sent to Bob.
- Bob's mail client uses Alice's public key to verify the hash signature and makes sure that the signature on the hash is correct.
- Bob's mail client computes a new hash based on the text sent by Alice (result in hash d).
- After that, Bob’s mail client compares the verified hash and the newly calculated one in step 5. This allows Bob to know if the digital signature is valid. If the two hashes are the same, then the message actually came from Alice and was not forged during the transfer.
Microsoft Outlook and other email clients use the S / MIME protocol to encrypt and sign emails. If the recipient and the sender of the encrypted email are used by different email clients, this does not mean that they will not be able to read each other's encrypted emails. For example, we consider the process of setting up the Microsoft Outlook email client, as the most common in a corporate environment. Other email clients can also be used to encrypt and sign messages. Their setup is generally similar, but there may be nuances.
How to set up message protection in Microsoft Outlook using Rutoken EDS PKI?
And now for the cause. Set up encryption and signing letters .
For example, I will use the device for secure storage of keys and certificates Rutoken EDS PKI .
As keys and certificates appeared on the token, we will not explain in detail. You can get them in the certification center or create them yourself, as described in one of our past articles.
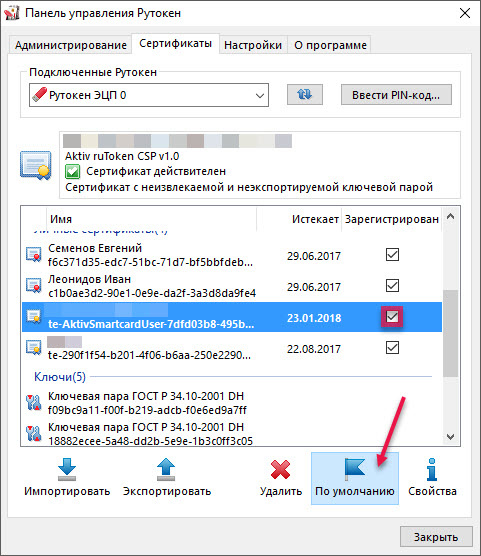
To begin with, using the Rutoken panel, save the certificate to the local storage and set its “default” parameter.
On the “Certificates” tab click on the name of the required certificate, click “Default”. Also check the box in the row with this certificate in the "Registered" column.
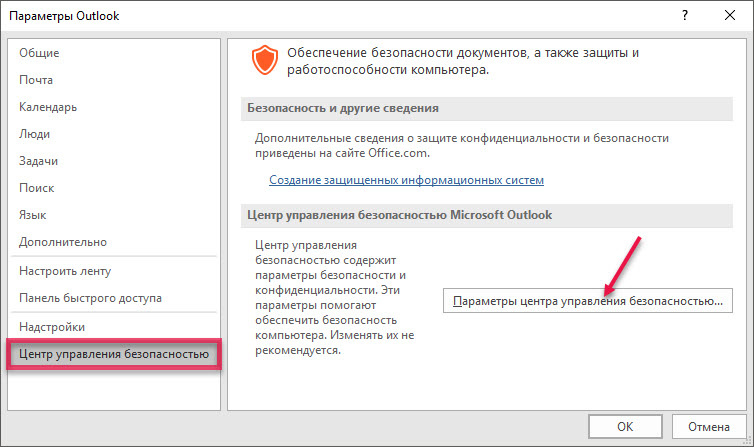
In Microsoft Outlook, select the “File” menu item and the “Parameters” sub-item.
Select "Security Control Center" and click "Security Control Center Settings ...".
')
Select "Email Protection" and select the necessary checkboxes.
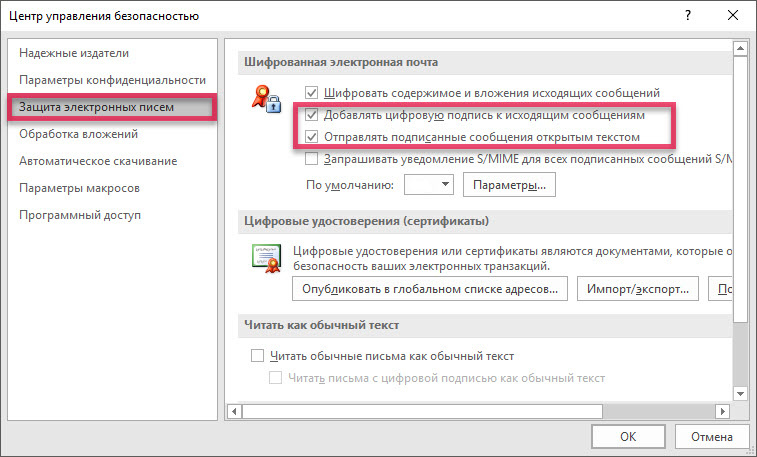
Click "Options".
Change the configuration name, select the certificates for signing and encryption.
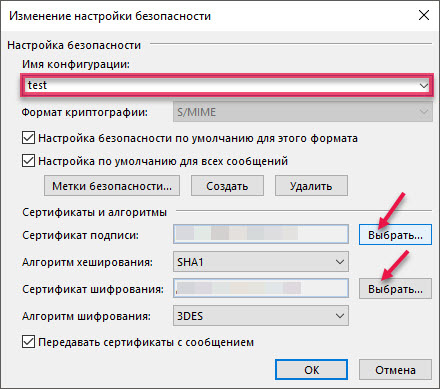
After that, all emails sent using MS Outlook will be automatically encrypted and signed.
To start the exchange of emails, you must send a certificate to the recipient of the encrypted letter. To do this, you can send him a letter with a certificate file or an email signed by electronic signature.
We will send a signed letter.
To sign a letter with an electronic signature, go to the “Settings” tab and click “Encryption” (so that the letter is only signed). It's simple!
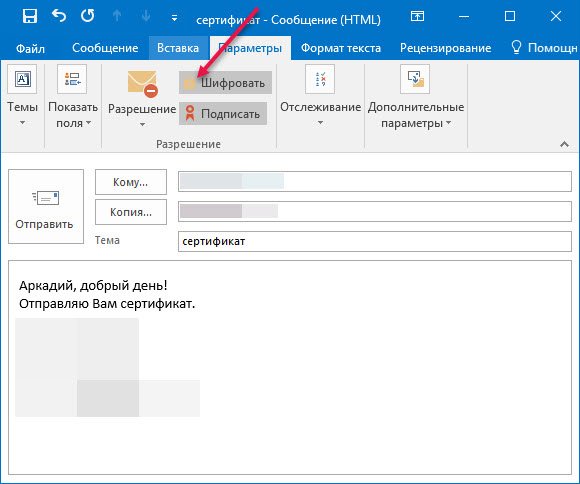
The recipient needs to add you to the Outlook contacts and reply to your email with an encrypted and signed email. After that, you can exchange encrypted letters with the recipient, and no one except you two can read them.
Sometimes it is necessary to sign only the file attached to the letter. This can be done by signing the file itself in one of the popular Microsoft Word or Microsoft Excel applications.
We will look at the process of signing a file in Microsoft Word.
How to sign a file in Microsoft Word?
You can protect the file from changes with an electronic signature.
The public key of the author of the document should be distributed to all users.
which will work with the signed document. This is usually done by sending a public key certificate to all users in your contact list.
How it works?
There is a document that must be signed. Using a special software from the content of the document and the private key creates a unique character sequence. This sequence is an electronic signature. It is always unique to this user and this document.
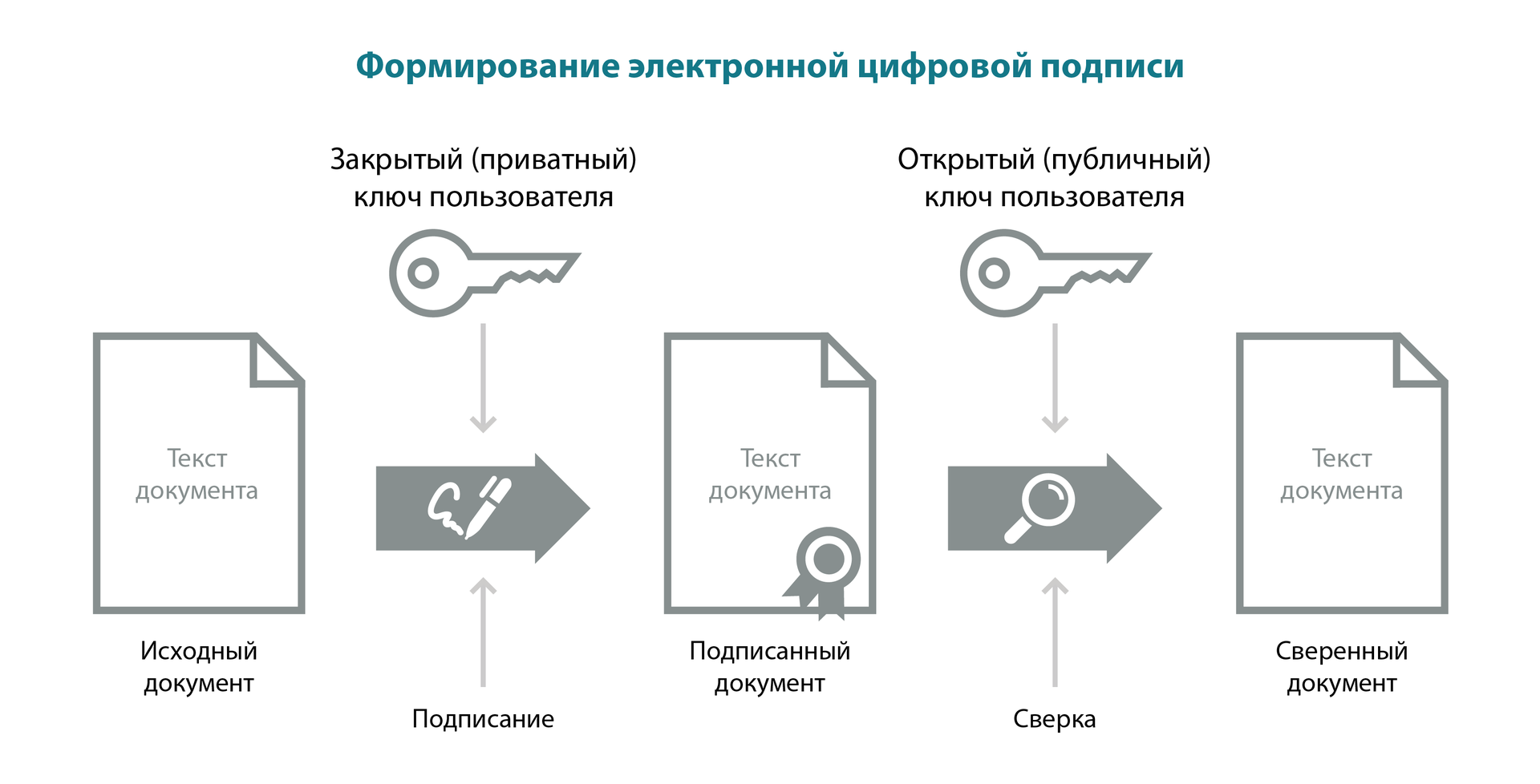
The electronic signature is a document requisite that allows you to establish the fact of distortion of information in an electronic document from the moment the electronic signature was generated and to confirm that it belongs to its owner.
An electronic signature can be tantamount to a handwritten signature on a paper document, so it is very important that the attacker is unable to deliver the attacker.
To secure your electronic signature, the private key of the electronic signature must be stored on a token or smart card. Then your electronic signature will be protected by a PIN, and even in case of theft of a token or smart card, the attacker will not be able to use it.
For example, let's sign any document in DOCX format.
I will use the Microsoft Word 2016 application.
You will need a token or a smart card. For example, I will use Rutoken EDS 2.0.
To get started, open the document you want to sign.
Select "File" and click "Document Protection".
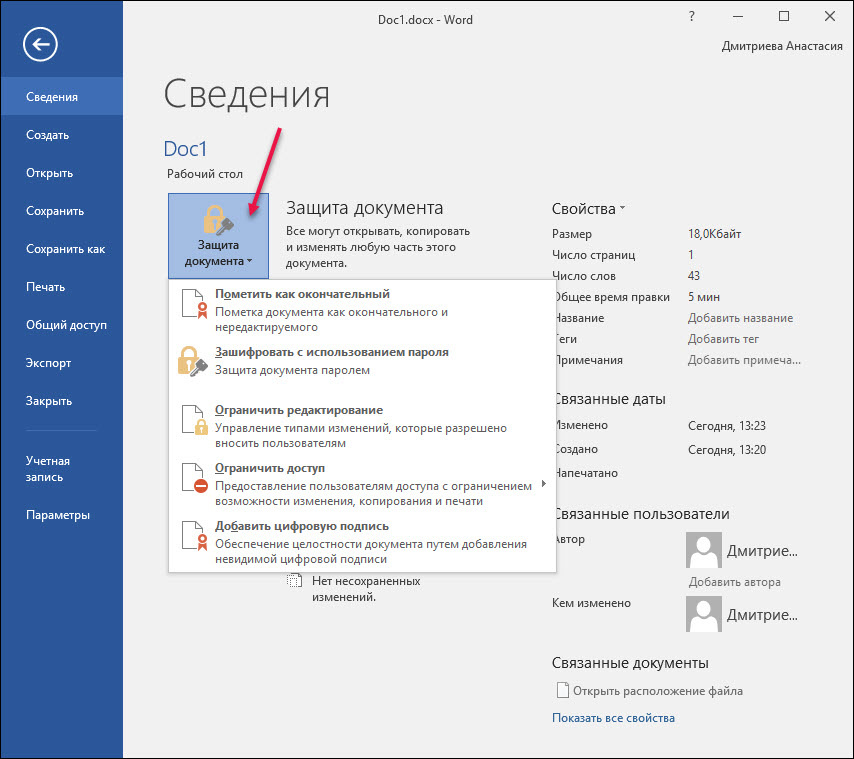
Select "Add Digital Signature".
A signature window will open. It allows you to add personal certificates that will be used when generating a signature. One of the certificates is selected automatically.
In the drop-down list, select the type of confirmation and, if necessary, enter the purpose of signing the document.
Click "Change" and select the required certificate.
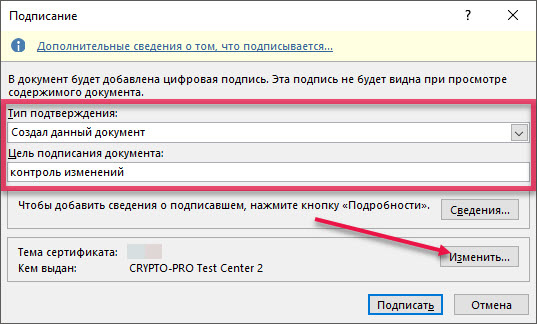
After selecting the certificate, click "Sign" and enter the token PIN. The signature will be saved in the document. An icon appears in the status bar indicating that the document was created with a signature.
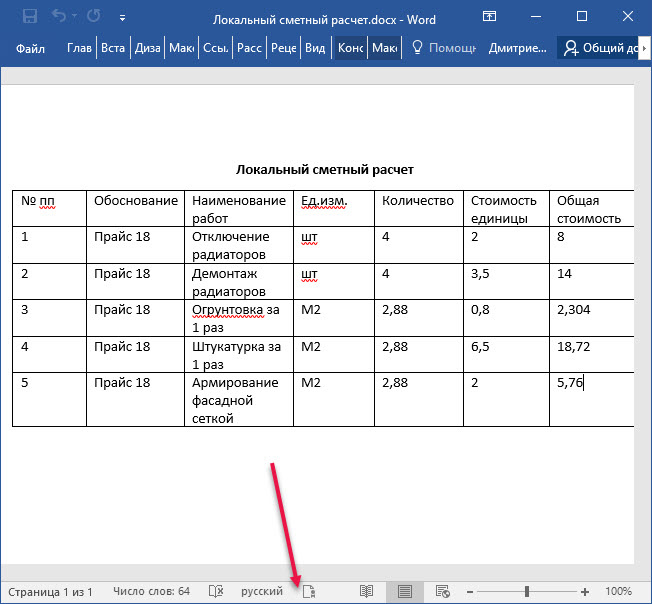
Now, if someone changes the document, he will have to sign it again. And this means that you will always know who is the author of the latest version of the document. And you will understand whether your version of the document has been changed.
This, in turn, will make the exchange of documents more secure and “transparent”.
We summarize
As a result of the settings you made, you can send messages that will:
- sent by you;
- read only by selected recipients;
- protected against changes during transmission;
- created and signed by you.
In the next article we will explain what Bitlocker is, how it can protect your information from intruders and how to configure it.
Source: https://habr.com/ru/post/329904/
All Articles