Routers, attack vectors and other adventures of Shurik

Not so long ago, in just one month, about 10 vulnerabilities related to getting root shell or admin accounts on home network devices saw the light. Wi-Fi and 3G routers with admin's accounts around us. By paying $ 50 for a paid account on shodan.io , anyone can access tens of millions of IoT devices. These include routers, webcams and other gadgets. On the other hand, developers and network device vendors do not attach importance to such concepts as "testing" and "security." Many serious vulnerabilities remain without patches, and if patches do come out, users are in no hurry to use them. What is the result? Legions of devices are waiting in the wings to be hacked and become bots for DDOS attacks.
Prehistory
In August 2016, the world met a botnet called Mirai. Researchers from the MalwareMustDie group began to study the malicious network activity of IoT devices in early August, and on September 20, a botnet of about 150,000 devices (mainly DVR and IP cameras) attacked Minecraft servers located at the French provider OVH.
IoT devices were infected by selecting a Telnet account on ports 23 or 2323 from a list of 62 standard passwords. IP addresses were generated absolutely randomly over the entire range, and after being included in the network, each infected device began scanning these random addresses. The code controlling the botnet was not stored in the long-term memory and, therefore, could not survive the device reset. However, given the speed at which the bots scanned the Internet, after a reboot, the device was soon re-incorporated into the botnet.
This was followed by the largest attacks on journalist Brian Krebs, on DynDNS, Liberia, the German operator Deutsche Telekom and one of the colleges in the United States. The source code of the Mirai botnet was published in early October and the attack on the German operator two months later was carried out using a modified version of Mirai, which exploited the RomPager server vulnerability on port 7547 (CWMP).
')
According to the author, who published the code Mirai, he had 380 thousand devices as part of a botnet at a time. This scale, of course, was due to negligence: Telnet service open to the outside and the absence of a mandatory password change do not contribute to security.
Anything other than webcams?
Fighting such attacks slowly but surely leads to a decrease in the number of compromised devices with standard passwords. Gradually, tactics change from selecting accounts to exploiting various kinds of vulnerabilities.
While the botnet predominantly absorbed video cameras and other IoT devices, in which the Telnet service gives access to Linux commands, the Telnet service on routers provided access only to the CLI settings. This CLI allows you to read and change the device configuration, DNS settings, ip route and system information, which in itself will allow you to conduct some attacks, but does not allow you to install software for remote control.
Such a boiling protection against bots can be found on port 23:

However, the absence of a bash terminal does not mean the absence of other attack vectors.
What is the average home router? It:
- an externally accessible web panel with an aggressive design;
- read-only file system squashfs and ~ 10 MB of flash memory;
- Of course, busybox (compact UNIX command line interface with a set of utilities);
- micro http web server; DropBear SSH server;
- open ports 80, 443, 23, 22, 21, 137.

In this case, the average age of the firmware on the device is 3-4 years. This age correlates with the average age of the router itself, or, in other words, users change the device itself rather than update its firmware. Recently, this statistic has been changing for the better by providers who, remotely and without user intervention, diagnose, configure and roll updates on users' routers. True, it works only for those devices that providers supply under its own brand.
At the moment, it has been empirically established that the passwords of about 15 out of 100 devices have never changed from the default values. And knowing only the five most popular couples, you can access the admin panel of every tenth device:
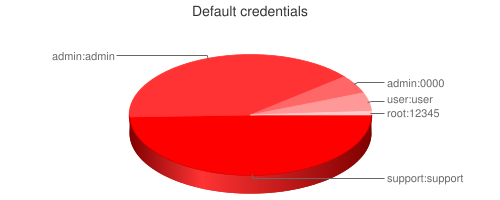
By accessing the web panel, the attacker also has a unique opportunity to ruin the lives of all users on the other side, conduct DNS Spoofing and explore the internal network. With great luck, he is also able to call commands such as ping or traceroute from a web panel, find a vulnerability in the web server code to get a shell, or use one of those already found.
The variety and simplicity of known vulnerabilities (as well as bug reports) in router software indicate that device functionality is rarely covered by sufficient testing and software developers do not have the necessary skills for safe development. Also, the development does not take into account the models of intruders. A buyer can purchase a router with one of the similar vulnerabilities on board:
NETGEAR DGN2200v1 / v2 / v3 / v4 - 'ping.cgi' RCE ( link )
The lack of checks in ping.cgi leads to the fact that the entered IP address from the user goes directly to bash. You can execute arbitrary commands in the terminal simply by writing them in the IP address field in the POST request. Like this: 12/12/12; nc -l 4444 -e / bin / bash. Instead of nc, you can add a more functional load, for example, msfvenom. 3000 devices waiting in the wings to unlock the potential. Operation will require authorization on the web interface.Multiple vulnerabilities in GoAhead WIFICAM cameras ( link )
Numerous vulnerabilities have been discovered in more than 1,250 models of IP cameras, and around 130,000 cameras are at risk. The error in the implementation of the custom authorization mechanism, which allows you to get the admin password, and the OS Command Injection vulnerability on the set_ftp.cgi page, which allows you to execute any terminal commands, together give complete control over the device without any restrictions. Impressive! The use of this vulnerability was added in its arsenal of the botnet TheMoon, known since 2014. In the course of the study, infected cameras were detected, to the settings.ini file of which a script was added that downloads malicious code from the attacker's server when the device was booted.
At the end of the download chain, the executable file compiled for the ARM architecture arrives from the attacker's server:
which 17 of 54 antiviruses are identified as Linux / Proxy.Linksys Smart Wi-Fi Vulnerabilities ( link )
According to a study of 25 models of the Linksys Smart Wi-Fi routers that are being actively sold all over the world, 10 vulnerabilities of various degrees of danger were exposed. Among the vulnerabilities are those that allow you to execute arbitrary commands with root privileges. Despite the fact that in total, using Shodan can detect only about 1000 units, the researchers talk about more than 7000 scanned devices.Siklu EtherHaul Unauthenticated Remote Command Execution Vulnerability (<7.4.0) ( link )
These serious pieces of iron from Siklu provide subscribers with communication through the millimeter-wave radio waves at frequencies of 70/80 GHz. The researcher discovered that the mysterious port 555 on them serves to communicate with other Siklu EH. Add to this the lack of restrictions on access to the port and storing passwords in the clear, he got an exploit to change the admin password. This architectural design error was assigned its CVE number: CVE-2017-7318 .Bypassing Authentication on iball Baton Routers ( link )
Although the admin panel of the iBall Baton 150M device is securely closed by HTTP authorization, the password.cgi page is visible to anyone. It seems that the developers have forgotten about this fact and stored passwords from all three accounts on the device in clear text in the HTML-page script; 1500 admin passwords in the public domain!
These examples were collected in just one month. There are also routersecurity.org router vulnerability aggregator and the wonderful routersploit framework that collect dozens of vulnerabilities and exploits under one roof.
A huge number of holes in the web admin code allows you to get passwords and execute arbitrary code.
Alternative threat vectors
In addition to the web interface, an average of 4-5 ports are open on the router. These include Telnet (23), SSH (22) and FTP (21).
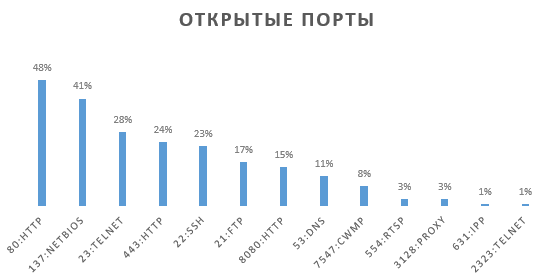
As practice shows, the Telnet service serves to access the CLI settings of the router, and FTP - to remotely update the firmware. For example, for 18,000 D-Link DSL 2750U modems, when selecting accounts, anyone has the ability to roll firmware with a built-in backdoor. This way he will receive bots that will surely survive the reboot and are unlikely to be hacked by anyone else. The action algorithm is as follows:
- Download the firmware for this device from the site of the manufacturer D-Link.
- Unpack
- Supplement it with a backdoor account or a script that runs the bind shell. At this step, the attacker can show imagination and embody any of his ways of getting a shell.
- Assemble the Frankenstein back using the available tools. For example, the firmware framework.
- Update device firmware via FTP.
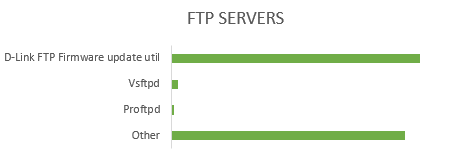
In addition to FTP updates from D-Link, you can also update via Telnet ( 140,000 CLI available) or via a web panel. DNS Hijack on this background does not look serious.
Recent attacks on Eir D1000 devices were related to OS Command Injection vulnerability in CWMP implementation - TR-064. The result was an infection of about 900,000 devices with a modified version of Mirai. Another vulnerability in the RomPager <4.34 server under its own name Misfortune Cookie (CVE-2014-9222) has the highest CVSS value of 10 .
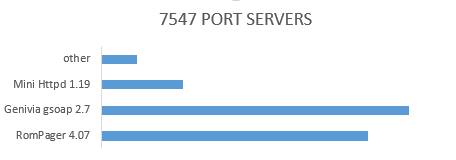
Meanwhile, slightly less than half of all CWMPs use the vulnerable RomPager 4.07. This is almost 2,500,000 devices available. Check Point at RSA 2017 presented their own study of the security issues of the TR-064.
RomPager 4.07 is not the only ancient service used by firmware providers. Genivia gSOAP 2.7 was released in 2004, and DropBear SSH 0.46 was released in the second half of 2005.

At least some vulnerabilities are known for DropBear (DoS and Authenticated RCE).
On April 4, researchers Bertin Jose and Fernandez Ezequiel published a report , according to which 18 vendors, 78 models and more than half a million devices contain an error in the SNMP agent, which allows anyone who wants to get full read / write access over all values. The mistake is that the agent simply does not check the community string: any combinations are authorized. Vulnerability has received the fashionable name StringBleed, and mainly home cable modems are exposed to it, although researchers talk about the detection of other systems with similar vulnerabilities. The consequences are the same as in the absence of authorization at all.
And finally, 9 out of 1000 routers provide a free DNS server with recursion enabled by default. The technique of operation has been known for a long time and will exist until the default DNS on routers stops responding to requests from the Internet.
Conclusion
Manufacturers of home network devices are gradually closing the usual ways to get bots. Instead of brute force tactics, the attacker's focus shifts to exploiting vulnerabilities, and this gives significantly better results than brute force. Continuous scanning of the entire range of IP addresses allows attackers to find all vulnerable devices. In fact, a huge number of device models are subject to certain vulnerabilities, some are specific to a particular model, and some cover hundreds of thousands or millions of copies, turning devices into toys for intruders.
Ways of dealing with botnets are simple (we list as the efficiency decreases):
- by default, restrict access to the administration panel, CLI and FTP from the Internet;
- use the latest firmware versions;
- force customers to change standard passwords;
- restrict brute force attempts.
The most massive devices is the primary goal of researchers; until security receives proper priority, the development cycle will introduce new vulnerabilities into the router software.
The report was presented at the third meeting of the Nizhny Novgorod Defcon NN community and all lovers of the live narration can watch its video:
Source: https://habr.com/ru/post/329902/
All Articles