The fading border between corporate and personal accounts
In the past few years, one can observe how the boundary between corporate and personal accounts is gradually blurred in terms of the level of security and consumer properties that they offer, and the accounts themselves are becoming increasingly compatible. Let's see how these two different areas of application of accounts become more similar to each other.

How does the blurring of boundaries between methods of multifactor authentication of corporate and consumer level?
If some two-factor authentication methods were originally developed for consumer use and only later adapted to the corporate environment, others, on the contrary, were created for use in the corporate environment, but found application in personal use.
')
The American National Institute of Standards and Technology (NIST) has calculated that employees of this institute have to authenticate an average of 23 times within 24 hours. The main conclusion of this study was the recommendation for organizations to implement solutions for single sign-on (single sign on, SSO), where possible, to minimize user fatigue syndrome from passwords.
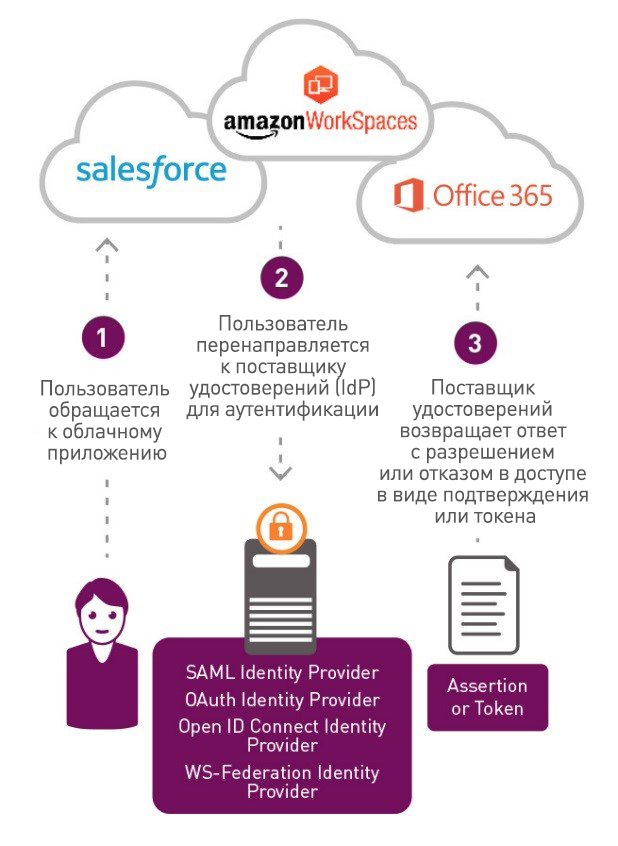
According to analysts from Gartner, “Single Sign-On (SSO) allows you to perform authentication only once, and then automate this procedure to access various resources. This mechanism eliminates the need for separate logon and authentication when working with separate systems, actually acting as an intermediary between the user and target applications. ”
In a corporate environment, the single sign-on mechanism is implemented using password vaults or identity federation protocols such as Kerberos, SAML, or Open ID Connect. Consumer services are dominated by federated authentication technologies, which are predecessors to the single sign-on mechanism. However, password stores are also available to consumers. For example, when you click on the “Sign in with Google” button to log in with a Google account, the Open ID Connect protocol allows you to use your Google account to access a new independent website, and thus eliminates the need to create a new account and log in with a new username and password combination.
According to a recent study by Gemalto Authentication and Identity Management Index, 88% of IT decision makers have already implemented single sign-on, or intend to do so in the next two years.
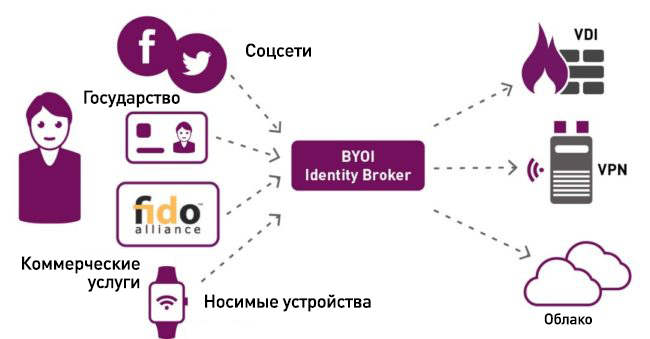
Suppose tomorrow is your first day at a new job. Can you use one of your social network accounts to access the network, VPN and some cloud applications? If an account broker is implemented on the new job, the answer to this question will be positive!
Similarly, if your organization has an account broker, you can allow your business partners to log in to your partner portal using their social network accounts, which will save them from having to create and maintain a new account - and this is really it’s worth it, especially considering how many leaks occurred through the use of supplier or partner accounts, such as in the case of a leak in Target.
Account Broker (Identity Broker) is a system that allows you to implement an authentication scheme using existing accounts (Bring-Your-Own-Identity, BYOI) and allows users to authenticate to various websites using their account. When using this mechanism, a single account can be associated with users from different sources. This is done using protocols such as SAML 2.0 or Open ID Connect, which are specifically designed to perform a similar task.
In the future, we will see an increasing number of account providers that not only support individual corporate accounts, but also work with numerous external account providers - supporting, for example, social network accounts, medical smart cards, commercially purchased accounts. , such as FIDO, as well as accounts created with numerous wearable devices that use smart card chips.
This kind of account brokering will make our current account universal.
In fact, creating a universal online account is the ultimate goal of the FIDO Alliance . We are talking about a universal account that would be compatible with both consumer services and the corporate environment. The abbreviation FIDO, derived from the words fast identity online, means a industry-wide initiative aimed at creating a universal form factor for strong authentication that consumers could use to work with consumer and corporate services. The development of FIDO is carried out by the efforts of major industry players such as PayPal, Microsoft, Google, ARM, Lenovo, MasterCard, Bank of America, American Express, and the list goes on. The idea behind FIDO is that the PKI authentication technology will allow us to use the same USB key, a retina scan, a Bluetooth authentication token or a mobile device to access bank accounts, cloud applications or to access social networks.
To learn more about consumer and enterprise security transformation, see our Digital Identities webinar : or download the IAM Trends and Enterprise Mobility eBook report.

Multifactorial assimilation
How does the blurring of boundaries between methods of multifactor authentication of corporate and consumer level?
If some two-factor authentication methods were originally developed for consumer use and only later adapted to the corporate environment, others, on the contrary, were created for use in the corporate environment, but found application in personal use.
')
- Biometric technologies include fingerprint and iris scanning, which is implemented in native applications for authentication in the consumer or corporate segment. For example, the biometric bracelet for two-factor authentication Nymi is worn on your arm and uses the heart rate reduction characteristic of your body for authentication and access to resources.
- The most typical example of context-based authentication is when you select the “Remember me on this device” checkbox, or when you use Verified-By-Visa (VBV) or MasterCard SecureCode (MsSc) passwords. When entering a corporate or consumer service with a browser and device bundle previously unknown to this system, the user is prompted to undergo additional testing using another authentication factor, for example, using a one-time password (OTP). In particular, when making transactions in e-commerce or in e-banking using 3-D Secure standard, this additional check is performed whenever there is any suspicion about the transaction, and then users are asked to specify a VBV or McSc password.
- Push authentication in one step allows you to authenticate an account in one step on a mobile device — a similar method is used to authenticate both in consumer-class services (for example, to access e-mail) and in corporate authentication services.

Single sign-on mechanism at work and at home
The American National Institute of Standards and Technology (NIST) has calculated that employees of this institute have to authenticate an average of 23 times within 24 hours. The main conclusion of this study was the recommendation for organizations to implement solutions for single sign-on (single sign on, SSO), where possible, to minimize user fatigue syndrome from passwords.
According to analysts from Gartner, “Single Sign-On (SSO) allows you to perform authentication only once, and then automate this procedure to access various resources. This mechanism eliminates the need for separate logon and authentication when working with separate systems, actually acting as an intermediary between the user and target applications. ”
In a corporate environment, the single sign-on mechanism is implemented using password vaults or identity federation protocols such as Kerberos, SAML, or Open ID Connect. Consumer services are dominated by federated authentication technologies, which are predecessors to the single sign-on mechanism. However, password stores are also available to consumers. For example, when you click on the “Sign in with Google” button to log in with a Google account, the Open ID Connect protocol allows you to use your Google account to access a new independent website, and thus eliminates the need to create a new account and log in with a new username and password combination.
According to a recent study by Gemalto Authentication and Identity Management Index, 88% of IT decision makers have already implemented single sign-on, or intend to do so in the next two years.
Interoperability is the key to creating a universal account
Suppose tomorrow is your first day at a new job. Can you use one of your social network accounts to access the network, VPN and some cloud applications? If an account broker is implemented on the new job, the answer to this question will be positive!
Similarly, if your organization has an account broker, you can allow your business partners to log in to your partner portal using their social network accounts, which will save them from having to create and maintain a new account - and this is really it’s worth it, especially considering how many leaks occurred through the use of supplier or partner accounts, such as in the case of a leak in Target.
Account Broker (Identity Broker) is a system that allows you to implement an authentication scheme using existing accounts (Bring-Your-Own-Identity, BYOI) and allows users to authenticate to various websites using their account. When using this mechanism, a single account can be associated with users from different sources. This is done using protocols such as SAML 2.0 or Open ID Connect, which are specifically designed to perform a similar task.
In the future, we will see an increasing number of account providers that not only support individual corporate accounts, but also work with numerous external account providers - supporting, for example, social network accounts, medical smart cards, commercially purchased accounts. , such as FIDO, as well as accounts created with numerous wearable devices that use smart card chips.
This kind of account brokering will make our current account universal.

In fact, creating a universal online account is the ultimate goal of the FIDO Alliance . We are talking about a universal account that would be compatible with both consumer services and the corporate environment. The abbreviation FIDO, derived from the words fast identity online, means a industry-wide initiative aimed at creating a universal form factor for strong authentication that consumers could use to work with consumer and corporate services. The development of FIDO is carried out by the efforts of major industry players such as PayPal, Microsoft, Google, ARM, Lenovo, MasterCard, Bank of America, American Express, and the list goes on. The idea behind FIDO is that the PKI authentication technology will allow us to use the same USB key, a retina scan, a Bluetooth authentication token or a mobile device to access bank accounts, cloud applications or to access social networks.
To learn more about consumer and enterprise security transformation, see our Digital Identities webinar : or download the IAM Trends and Enterprise Mobility eBook report.
Source: https://habr.com/ru/post/329768/
All Articles