Do-it-yourself phishing. Experience of the company "Aktiv", part two

In the first article, I talked about the theory of the question, but now we will move from theory to practice. So, we have successfully installed the system, set it up and are ready to start “phishing” on our own employees :)
Plan
Our plan is quite simple. At the first stage, we send several different letters to all employees. Mailings choose personalized (alcohol). The link in the mailing list leads through a blank page (which is necessary for analyzing the transitions) to the original service page. The first stage is devoted to essentially pure experiment in order to determine the entire depth of the problem. After the first letter, we officially announce to all employees that we sent letters and we send everyone to the anti-phishing training page.
After a week, we are conducting the second stage, which is similar to the first (letters with new content), but the link in the letters directly leads to our training page. The third stage - control. Following the results of the comparison and see the dynamics of the transitions on the link and calls to the IT department. With those who continue to "come across", we carry out individual work. The plan as a whole was executed and recognized as successful, but life made adjustments to it.
Sberbank
In our company, as in many, the salary is transferred to the cards. Sberbank cards occupy a leading position. Why not start phishing by checking “Sberbank”, we thought, and made the first email template that looked like this (by the way, we didn’t think up this and all the other templates ourselves, but found it on the Internet). And then the day came "X", and the staff received a similar letter.

Following the link, we made a very simple page:
<!DOCTYPE html> <html> <head> <meta http-equiv="refresh" content="0; url=https://online.sberbank.ru"/> </head> <body> </body> </html> As can be seen from the page code, there is a redirect to the real Sberbank website. We were only important the fact of the transition.
State services
Sberbank is good, but it seemed to us that it was not enough for the first mailing. What else will be interesting at once to all employees of the company? State services. They are more and more entering our lives and many people use them, respectively, this is quite a worthy object for distribution. After wandering around the expanses of the network, I turned up an interesting spam template:
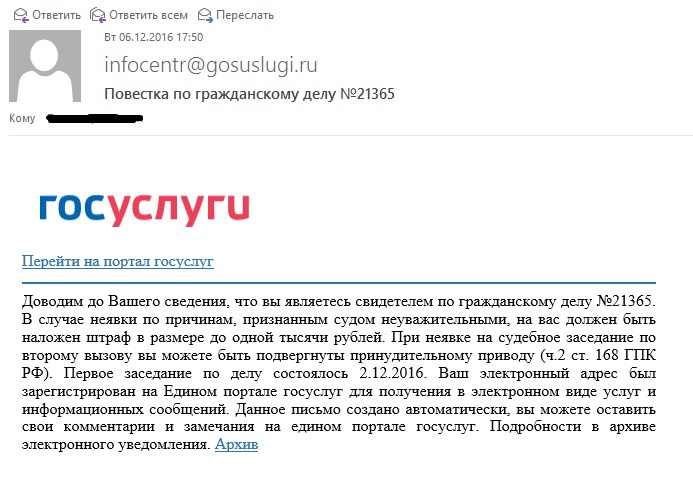
The link was again empty, the page is largely similar to Sberbank, but referring to another resource.
<!DOCTYPE html> <html> <head> <meta http-equiv="refresh" content="0; url=https://www.gosuslugi.ru"/> </head> <body> </body> </html> Results of the first stage
So, we launched the newsletter. The first hour or two was silence: someone followed the link, someone did not switch. Then calls began to be heard in the IT department. It is necessary to clarify that the staff in our company is quite advanced. An ordinary manager should know what PKI is and what it eats with. Therefore, the most gentle that we received by phone or in jira, there were messages like "Some strange spam came to us. Spin the spam filters. Closer to dinner, programmers came to work, and they became interested in our letters. Our mailing server was discovered fairly quickly, and here began a slight panic - were we hacked? I had to spend a little explanatory work with a number of managers and quench the panic, but the word of mouth was unstoppable. At this stage, we realized that we made one mistake.
You should not use intranet resources to host the system. Even if you control the DNS, you can simply ping your domain and understand that it is inside the network. Rent a virtual machine off-network and configure DNS for it, or buy several domains for the full purity of the experiment.
Starting from the second stage, we have already corrected. We have no such problem.
Accounting
A separate story deserves the reaction of accounting. Accounting takes part in the payment of salaries to employees, and having received our "letters of happiness from Sberbank", could not but respond. She did it violently and beautifully. Better reaction in real "phishing" can not be imagined! Bookkeeping did three things. First, they called Sberbank and clarified the authenticity of the letters. Sberbank explained that this is phishing, you do not need to download anything and follow the links. Secondly, the accounting staff reported to the IT department about the spamming incident. And the most valuable, the accounting department warned all employees of the company about the danger of the letters received.
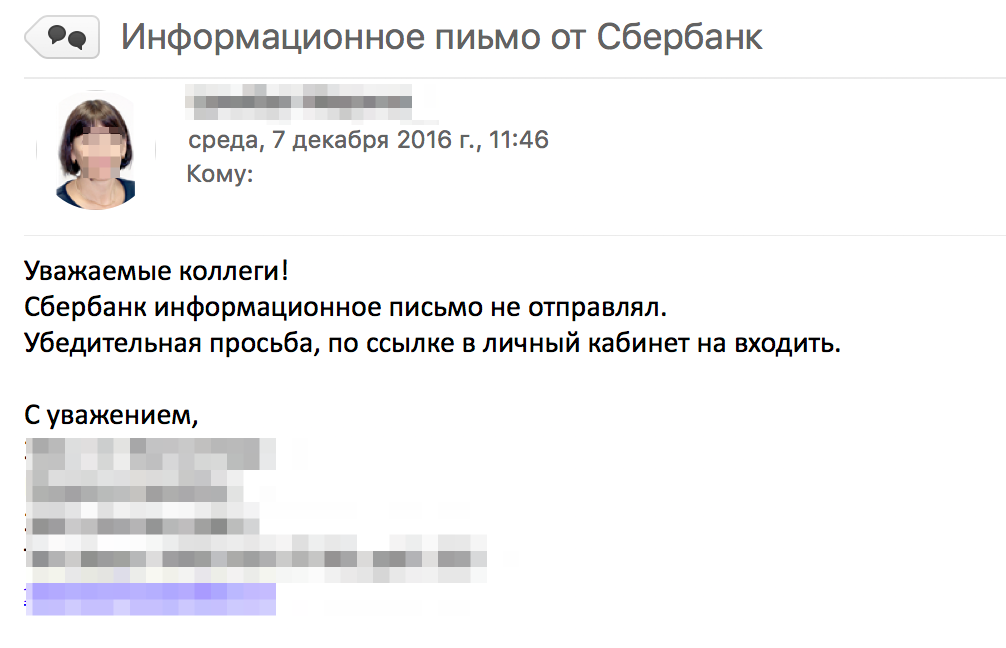
Let me remind you once again that this was not a staged, but a real reaction of the company's employees. In addition to the management of the company, nobody knew about the planned letters. At the first stage, it was important for us to understand how the company will behave in a phishing attack. After a subsequent analysis and analysis of the situation, we realized that a partially violent reaction was partially provoked by our second mistake:
Do not make the newsletter to everyone at once. Such broadcasts cause quick effect of word of mouth and in the first stage can distort the real problem. It is necessary to divide employees into groups so that employees with the same mailing are far from each other and cannot quickly exchange suspicions. Mailings should be quantized and avoid mass mailing at one time.
Social networks
Employees use social networks, and we simultaneously monitored their reactions to these resources.
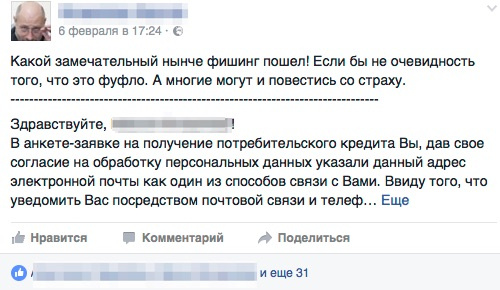
The posts caused interesting discussions (it should be noted that the “tusovka” of our employees is very “i-Chechnaya”).

Discussed interesting theory of obtaining a base of postal addresses.

Training
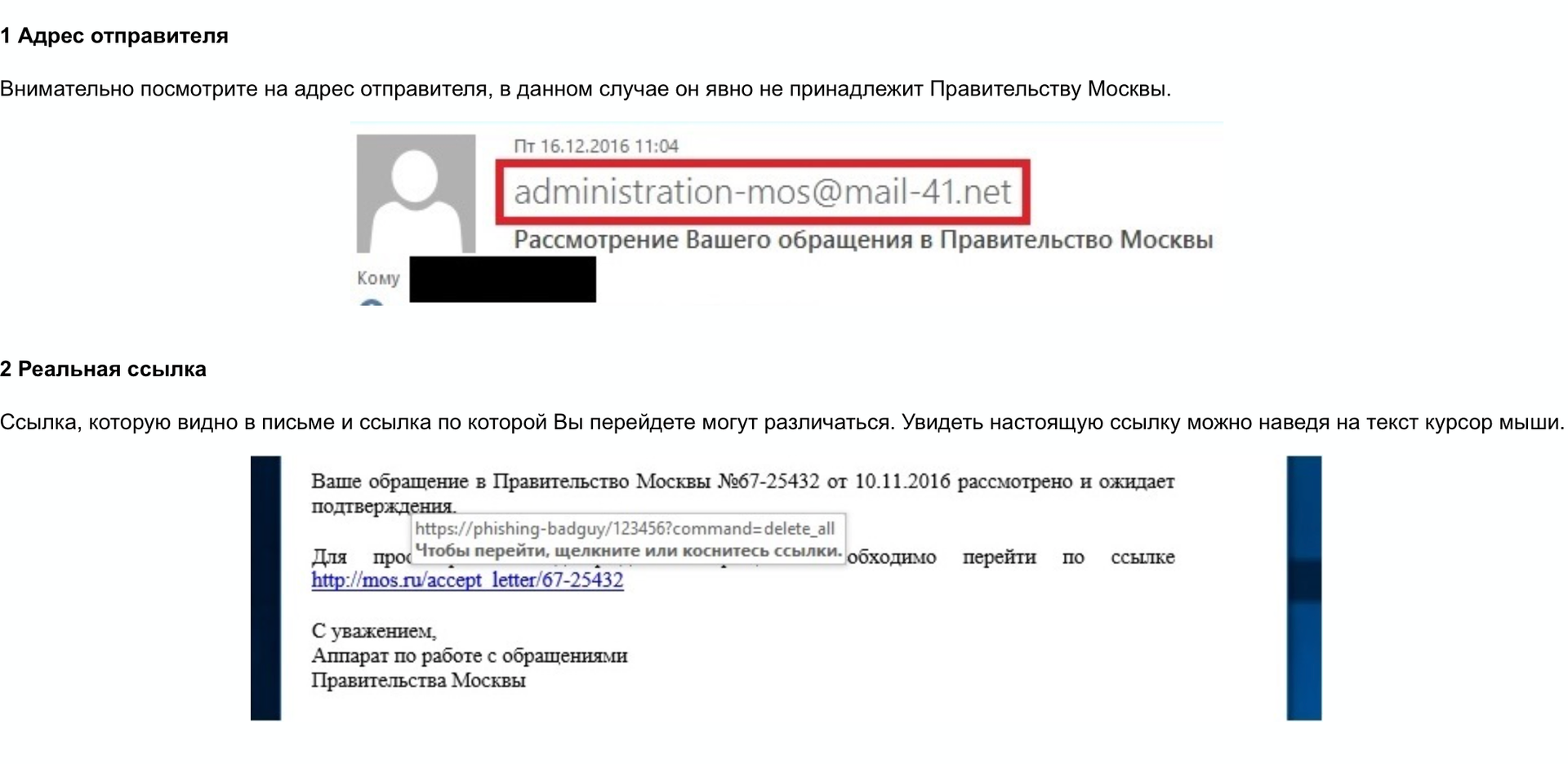
A special page was created for employee training, where simple examples explained how it can be understood that a letter is phishing. I will give here a small example from the page, and at the end of the article in the archive I will attach its full version.
Control stage
The second stage was already proceeding calmly enough. There was neither a heated discussion nor conspiracy theories. Those who followed the link found themselves on our training page and understood that this was “the IT department started the test again”. More interesting was the reaction to the control stage of testing without pages of training. It can be characterized by the following ticket:
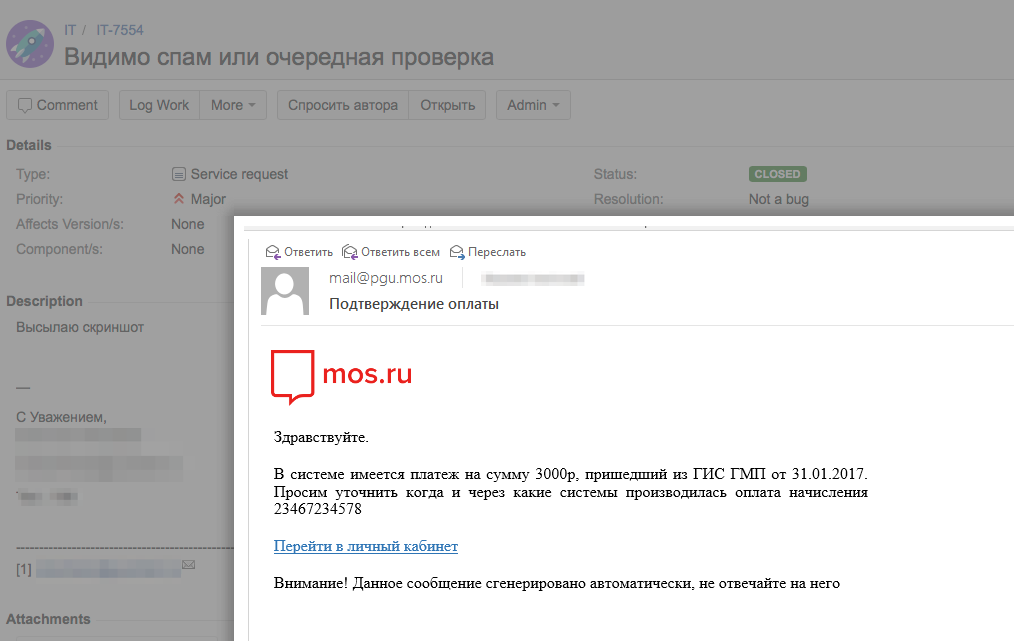
More and more employees reacted as we needed.
Results
What we finally managed to achieve:
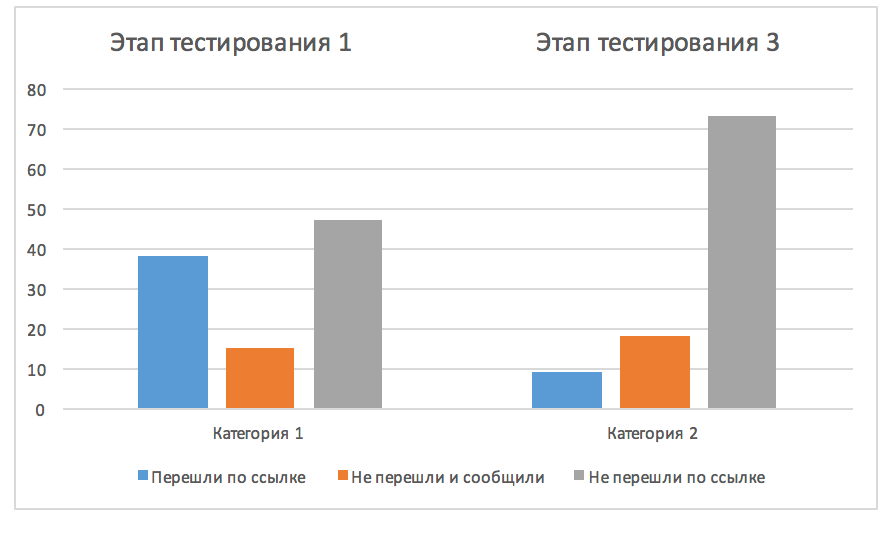
Most importantly, we taught employees not to follow suspicious links. From 39% at the first stage, we managed to reduce the number of those who transferred to 9%. Those. the perimeter of a possible attack was reduced by 4 times. The number of people who began not only to ignore phishing emails, but began to report them, increased. It should be noted separately that the system records specific individuals, and it is quite possible to work personally with the remaining 9%, which we successfully do.
Instead of concluding,
I want to give a few more letters and attach links to archives with samples of phishing letters and a training page.

This letter had a certain "success" at the control stage.
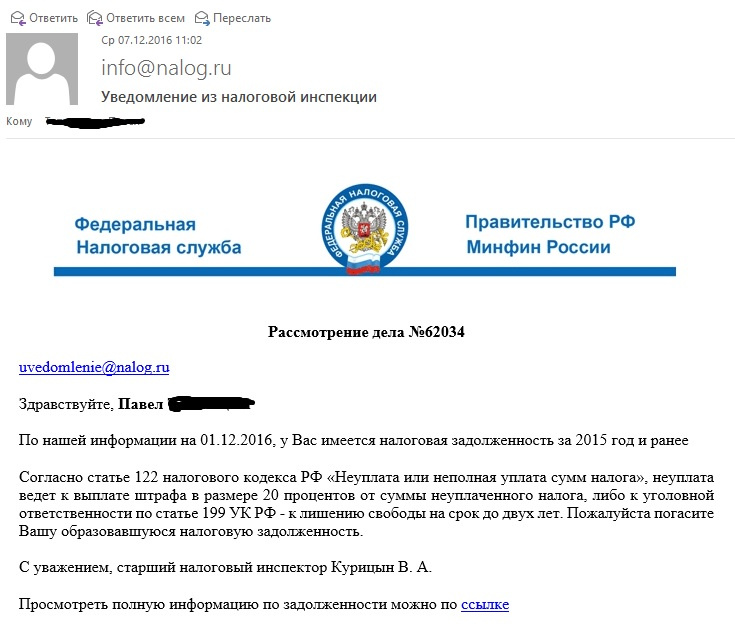
In the reporting period, tax letters are very relevant.
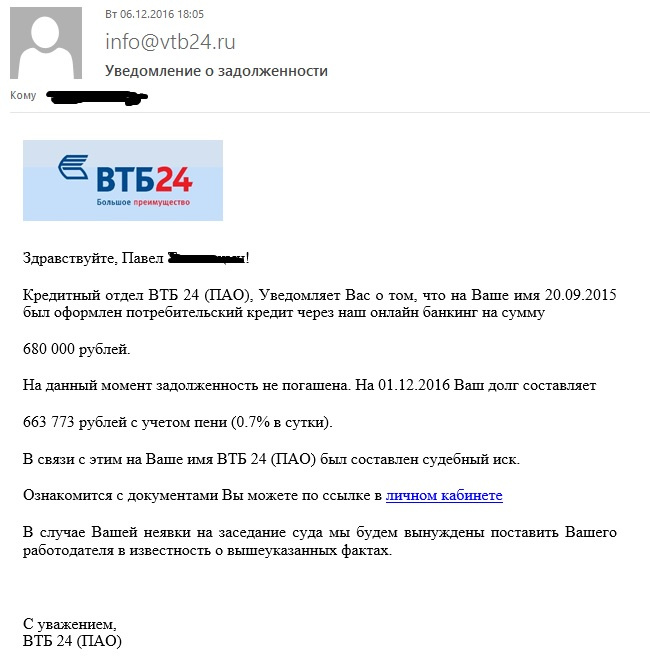
Phishing banks never lose their relevance.
As promised, I attach two archives:
Train your company staff. Arrange a variety of checks. And do it not once, but organize checks on a regular basis. One time people may not be enough. If you do not do this, the attacker will make it and the attack can be successful.
')
Source: https://habr.com/ru/post/329538/
All Articles