Do-it-yourself phishing. Experience of the company "Aktiv", part one
Spam in our time will not see anyone. We are accustomed to it and are already taking it for granted. On the other hand, spam ceases to be just advertising, more and more “letters of happiness” are phishing. The text of these letters is designed to encourage the recipient to perform an action.
Some theory
Fishing (eng. Phishing, from fishing - fishing, fishing) - a type of Internet fraud, the purpose of which is to gain access to confidential user data - logins and passwords.
Spear phishing (English spear phishing) is a type of phishing, in which an attacker generates a phishing email for a specific recipient, using previously collected data about the recipient.
Why is it all so dangerous?
Clicking on a malicious link or opening an attachment to the letter, you launch a virus or trojan that can take control of your computer and company information systems. Spear fishing is a more dangerous type of phishing. Its malware is related to the fact that any person, having received a personal letter addressed to him, no longer considers this letter as spam and is inclined to trust and open any links / files.
Is it really relevant?
Corporate email fraud is gaining momentum. For the first half of 2016, the FBI recorded 22 thousand victims of this type of fraud, while financial losses amounted to more than $ 3 billion. Mail today is the main method of penetration into the corporate network. Attackers do not see the difference between small, medium and large businesses. Cybercriminals play against large companies for a long time, but this does not mean that they are less interested in small business. Below is an interesting infographic showing that more and more attackers are interested in precisely small business.
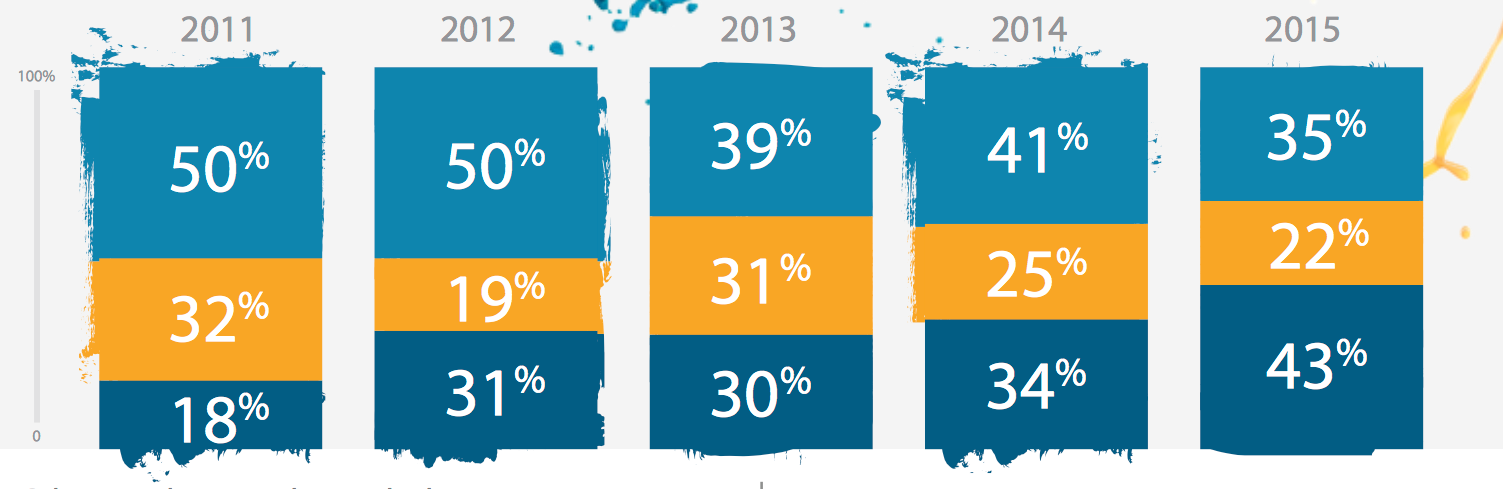

Scammers are increasingly using encryption (mention Wannacry already becoming a bad tone) like a weapon. 2016 Cisco called the "Year of ransome". For the first 3 months of 2016, fraudsters earned more than $ 200,000,000. It is estimated that by the end of the year, "revenue" was more than a billion dollars.

Experts, community, law enforcement agencies say: do not pay intruders, you encourage them to continue their activities. But people and companies are paying, the level of cipher products is growing. If the first cryptographers were similar to the work of first-year students in programming, now real professionals of the business have become involved in this. There are already cryptographically secure encryption.
The company can often face a choice: to pay, or simply to cease its activities. Naturally, many, almost everyone pays. You're scared as well as me? Not? Then let's add to this social engineering. We all now use Facebook, vk, twitter, etc. For our convenience, social networks unite people into groups. We ourselves fill out profiles, indicate where we live, the name of the company in which we work.
I am paranoid and never indicate the name of the company where I work, you say? Do you add colleagues to your friends from social networks? Do they all not indicate the name of the company? I do not think. After spending a couple of hours online, researching any company that interests us, you can quickly and easily get a list of the names and surnames of the company's employees. The hit will be quite large, and in addition to the last names, you can easily find out the list of hobbies and occupations of employees that can be used against them ... for example, to create personalized phishing emails. But corporate email addresses are not so easy to find, you say? Again disappoint. Knowing the name of the company, it is easy to find its corporate website. Accordingly, the domain is already there. Often, corporate websites also have general postal contacts, they will also be useful to us. Now the most difficult thing is that we need to get a couple of valid mailing addresses for company employees. To do this, for example, write to one of the public addresses of the company. Contact technical support, for example. Try to buy something in sales. If there is no public address on the site, you can always just call and talk with the secretary. Social engineering works wonders.
I was fortunate enough to attend the Chris "loganWHD" Hadnagy performance . The organization holds annual competitions on voluntary hacking (pentest) of other companies. The conclusion of the lecture was simple: social engineering can get any information. An untrained person is not protected from this. In addition, nothing prevents you from getting information about the company's secretary from social networks before calling. This will help simplify the conversation. So, we will assume that we found out a couple of employee addresses. We look at the pattern in the addresses. He is! Admins because the mail is not out of my head every time they come up with. There are not many patterns: last name, full name, last_name, etc. We impose a pattern on the base of surnames and names, and here we have a base of postal addresses of the company. Why do we need all this? There is such a thing as a Kill chain .
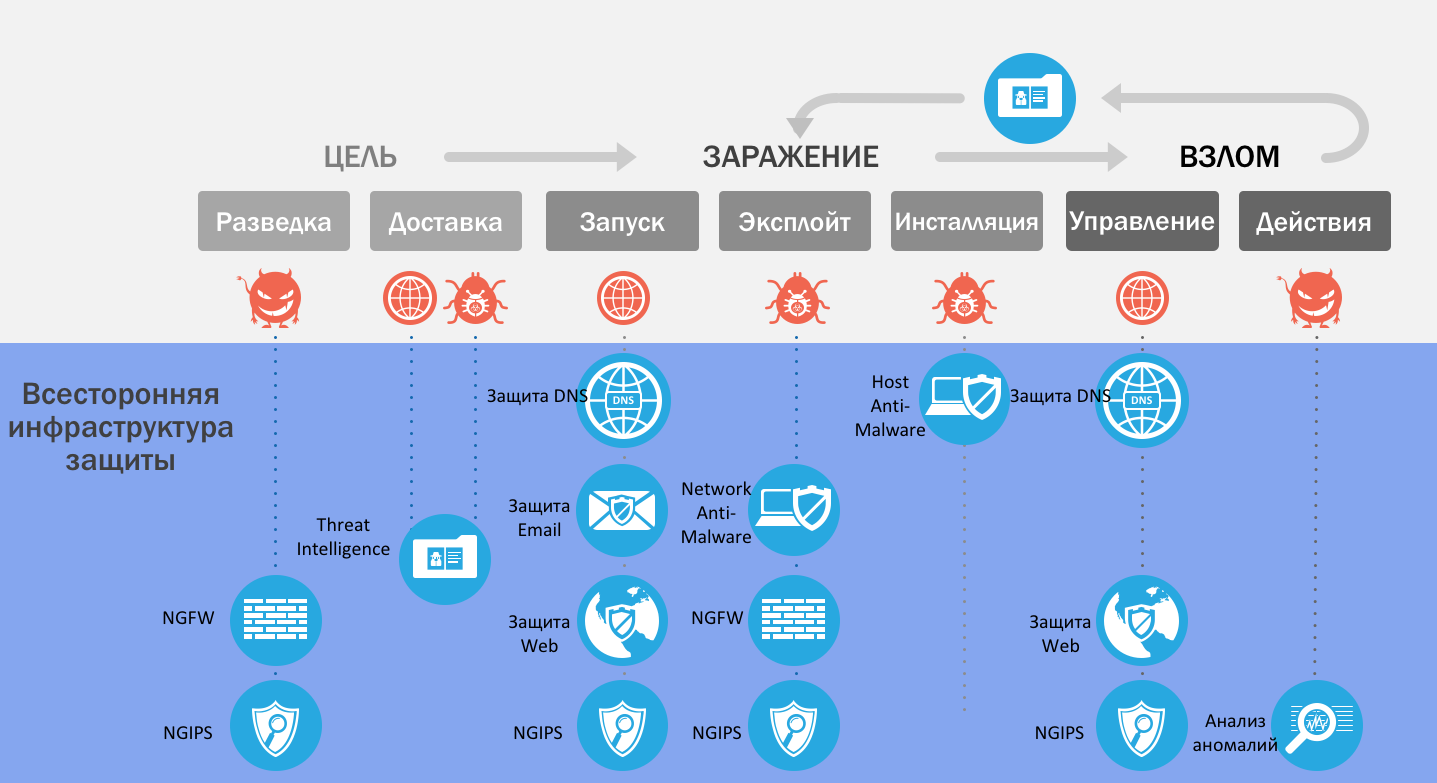
We are interested in the upper part of the picture. So, we all understood that attackers could easily carry out exploration of us on social networks. Accordingly, a list of addresses will be compiled and sent. If we are talking about a targeted attack on a company, and taking intelligence into account, we assume that it is it that is going on, specifically to circumvent the standard spam protection, attackers have acquired several temporary domains and, accordingly, all our spam filters will be passed, and the letter will appear in the mail employee box. What's next? Run the attached file / click on the link. Untrained user (certainly several among the employees of the company) will follow the link, open the attachment. According to Positive Technologies, in 2015, 24% of users, after receiving a letter, followed the link, and 15% entered their credentials or installed software. The percentage of such users from year to year only grows.
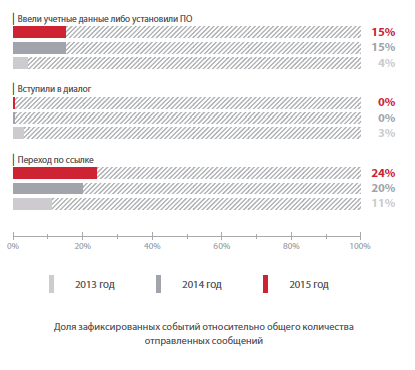
Will the exploit work? Yes (here you can insert a lot about WannaCry) . And that's why. The HP Enterprise report has such an interesting infographic, these are new software vulnerabilities that appeared in 2015. Vulnerabilities are, and regularly find new ones. And researchers even know about them:

Often no one knows about them. And it happens like this (and there is also the NSA).
On this "Kill chain" is over for us. Infection occurred, the attacker took possession of our computer. What will he do with him further of course interesting? In any case, we leave the rest beyond the scope of this article. We want to understand what we can oppose to this? And we can oppose a little. Yes, it is possible by corporate policies and regulations to prohibit people from using social networks and publishing information about work in them, but as the number of employees grows, this becomes unrealistic. Yes, you can train spam filters and use expensive threat detection systems, but even the most advanced of them are often not 100% guaranteed to filter dangerous email.
What remains? It remains to train and once again train employees on a regular basis, to train to identify phishing and simply delete these letters, before notifying the IT department / security service of the receipt of a suspicious letter. We recently conducted anti-phishing training at our company.
Training
How are we going to learn? And we will teach, arranging a social pentest of his company. You can go in several ways.
Pentest to order
After wandering through the expanses of the Internet, you can quite easily find a few companies that will gladly release your social pentester:
For example, www.infosec.ru - phishman.ru - http://www.antiphish.ru
You can go this way, but you need to understand that the budget of this event will depend on the size of the organization and be several hundred thousand rubles in the minimum version. At the request of the customer, representatives of pentestors can even conduct a full-fledged social search and retrieve mail addresses themselves, or they can work with ready-made data. Training on the results of the foam will cost some money. From the interesting on the Internet, we found a couple of SaS services:
• phishme.com
• infosecinstitute.com/phishsim
Such services will cost about $ 20 a year for a postal address, but it must be remembered that the ready-made database of templates contained in them will be English-speaking (although you can always upload your templates) + all international services (apparently in order to avoid legal claims ) it is mandatory to write in small letters at the bottom of the letter that this is a phishing test, which, in my opinion, somewhat reduces the purity of the experiment.
Game options
One of the best teaching methods is gaming. For example, recently Sberbank did it . The method is undoubtedly effective, but contains a couple of flaws. Unfortunately, this method actually works once, and given the development of means and capabilities, you need to be trained in phishing on a regular basis. But most importantly, the game must be done by yourself and by yourself. In the open access ready-made solutions could not be found.
Gophish

Now let me tell you about the solution that we ultimately chose for us: GoPhish - OpenSource framework for phishing. GoPhish , perhaps, is undeservedly ignored by Habré. Search could find only one article on this product, and the product is worth it.
GoPhish features
Gophish sends letters to predefined templates and lists of email-addresses. Also, this software uses the embedded web server to display phishing pages. Links to go to these pages are in the text of letters. To control the phishing test process, the “campaign” entity is used - it combines a letter template, an address list with a list of “user-targets” (Last Name, First Name, email address), a phishing page and a set of SMTP parameters. After the “company” is launched in the software interface, you can see which of the users followed the link to the phishing page, and who did not. Gophish also provides an API , but the basic functionality was enough for us.
Install GoPhish
The product is written in Go and in compiled form is one binary. Installation is simple and does not cause problems, there is a good and simple manual . The entire installation procedure is reduced to generating an ssl certificate and creating a simple and understandable config.json file.
"admin_server" : { "listen_url" : "127.0.0.1:3333", "use_tls" : true, "cert_path" : "gophish.crt", "key_path" : "gophish.key" } To clarify something here, I consider it superfluous. Everything is simple and clear. It remains to start the service by running the following command:gophish@gophish.dev:~/src/github.com/gophish/gophish$ ./gophish
All further work is done using the framework web interface. The first thing you need to do is add employees (Users & Groups tab). You can import a list of users from a csv file (for example, by unloading csv with the necessary fields from AD) or enter user data manually. Next, you need to create letter templates (the Email templates tab). Letter text can be entered as text (“Text” tab) or using HTML (“HTML” tab).
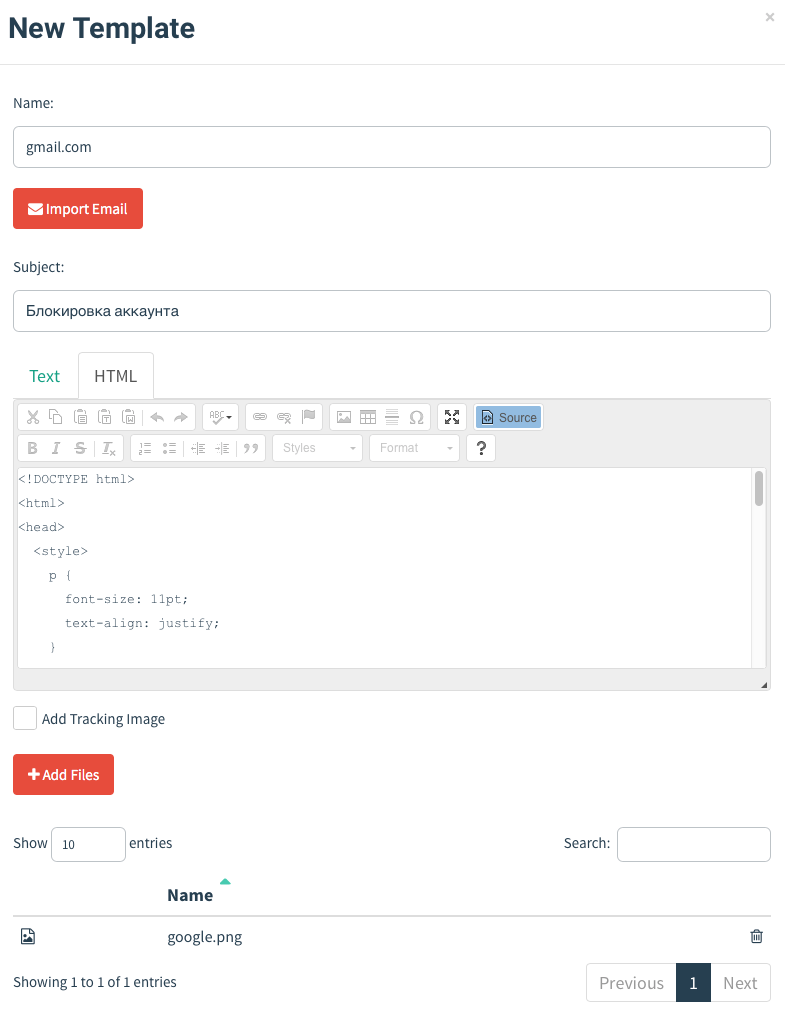
If the “Add tracking image” checkbox is ticked, a 1x1 pixel “tracking image” will be added to the letter. The picture is used to track the fact of opening a letter by the user. The following reference values can be used in the text of the letter:
| Value | Description |
|---|---|
| {{.FirstName}} | Name |
| {{.LastName}} | Surname |
| {{.Position}} | Position |
| {{.From}} | Sender |
| {{.TrackingURL}} | url to track |
| {{.Tracker}} | Tracking image |
| {{.URL}} | conversion url |
Next, create “phishing” pages (“Landing Pages” tab), the HTML page code should be entered into the appropriate interface window. Since we are not going to engage in real phishing among our employees, but we want to train them, as a phishing page, we used a page with educational material that tells employees what phishing is and how not to fall for it. (We will lay out the page template in the second part of the article).

You can also create pages with input fields. Moreover, there are options that preserve the numbers and passwords entered by users, but it is better to use this very carefully. Now we create sending profiles (“Sending Profiles” tab), i.e. essentially some postal data on behalf of whom, the employee will receive a letter and which mail server will we use for mailing. In the last step, create a campaign (Campaigns tab). "Company" combines all previously described. After entering all the parameters, you need to click the "Launch campaign" button, and the company will start automatically.
The results of the company can be monitored on the tab "Dashboard".
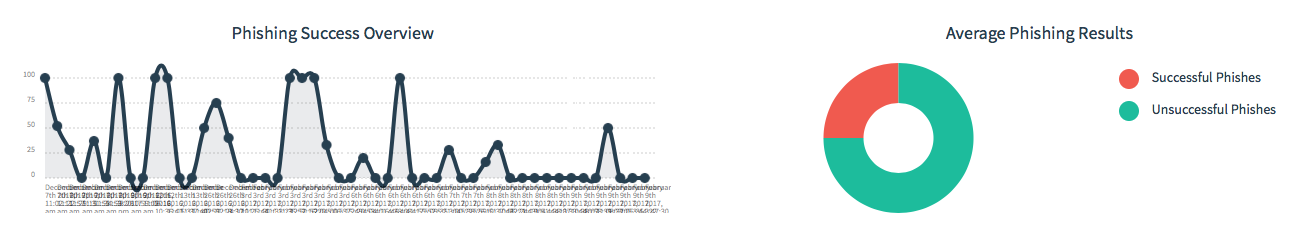
This tab shows the total percentage of users referred by links and the performance of each company as a percentage. You can always go and see the details of the company and see the specific employees who clicked on the link.
To be continued
This concludes the first part of our article. Soon we will add the second half in which we will share with you templates for phishing emails and a learning page. We will tell about the reaction of our employees (it was sometimes unpredictable and beautiful!) And share the results that we were able to achieve. And we also mention our rakes, which we advise you not to attack.
Part 2
')
Source: https://habr.com/ru/post/329470/
All Articles