Biocryptography as a chance to escape from cryptoapocalypse
 There was a time, among scientists there was a fashion to blame nature for non-optimal solutions and a lot of crutches used. One nineteenth-century physicist even entered the story with a statement in the spirit that the Lord God is a poor optician, and he would not give a penny to him (God) for the construction of the human eye. Then even the institute in Moscow was named after him, but not for it.
There was a time, among scientists there was a fashion to blame nature for non-optimal solutions and a lot of crutches used. One nineteenth-century physicist even entered the story with a statement in the spirit that the Lord God is a poor optician, and he would not give a penny to him (God) for the construction of the human eye. Then even the institute in Moscow was named after him, but not for it.So, he was wrong (although it would have been possible to do without a blind spot). Now science now and then peeps from living organisms separate principles and techniques. Yes, they are not always energy efficient, often their area of application is narrow, but tested by millions of years of survival. And what is interesting is that even in such a lifeless field as cryptography, there is an application to what life had invented once. Of course, animals do not encrypt the transmitted information, so that there is nothing directly to steal. We need to go deeper, as the famous Oscar-winner put it.
It is rumored that the emergence of full-fledged quantum computers is getting closer, closer and the end of encryption in the form in which we know and love. Intelligence services in anticipation are rubbing their hands, cryptographers rushing around in search of a cryptographic "silver bullet", and journalists almost every week make sensations that someone has already created a quantum computer and all our little secrets are no longer secrets.
All this is reminiscent of the hysteria around the “mistake of the year 2000”, under which decent money was allocated and mastered all over the world, except that there is less noise, because not every man in the street is aware of the importance of data confidentiality, 2000 as if the on-board computers of airliners would be cut out, anyone would frighten.
')
Nevertheless, there is a benefit from the quantum hype. While visionaries indulge in quantum annealing and try to find tasks for which this makes sense, cryptographers are developing new strong encryption algorithms. Their inquisitive gaze turned to quasi-biological computational methods. In fact, the topic is not new, and it has been developed for more than a dozen years, but it promises to be very relevant if it gets its due development.
Any biological system solves some of its tasks, be it the search for food, the adaptation to changing environmental conditions, the counteraction of aggression, and so on. This can be represented as a computational model - relatively rough, due to the fact that humanity has not studied life too deeply. And there are a number of tasks, including cryptographic and cryptanalytic, for the solution of which these models turn out to be extremely effective. Yes, yes, talking about neural networks, I am sure, everyone learned them. But not only about them.
Neural networks
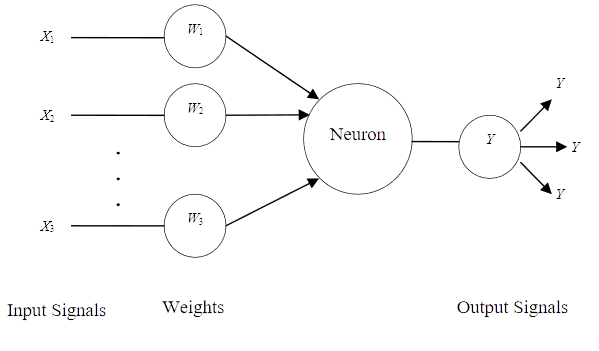 In short, an artificial neural network is a very, very rough
In short, an artificial neural network is a very, very rough In cryptography, neural networks can be used for key exchange, and this is almost the most important step in the confidential transmission of information. The Diffie-Hellman protocol is based on number theory, and its persistence is enough only until the attacker has a quantum computer. But the neural algorithm works differently. It is based on multilevel perceptrons located at the two ends of an unprotected communication channel.
The private key of each side is represented as the initial weights of the perceptron connections.
The initiator sends an initial data stream to its counterpart, and this stream is fed to the perceptron inputs on both sides. The data from the perceptron outputs of the side are sent to each other, then the obtained streams are compared and the link weights are modified, then the procedure is repeated. Thus, perceptrons teach each other (synchronize), and after reaching full synchronization, the weights of the connections of both perceptrons become the same — the session key is generated. Both sides have this key, but at the same time it has not been transmitted anywhere and in any form.
If a simple single-level perceptron is used in such a scheme, as in the picture, the third party will be able to calculate the initial weights from the initial data stream and the output stream of the neural network. Therefore, multilevel perceptrons with hidden layers are used - in this case, no one from the outside can figure out exactly which weights are modified in each iteration. The picture below shows an example of a neural network with multiple inputs, one hidden layer, and one output - the so-called tree-like parity machine.
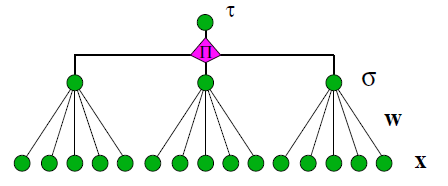 With stochastic learning, weights change pseudo-randomly, and then those changes are discarded that degrade the result — that is, even with the same private keys and the same initial flow (random or non-random), the session key will be different each time. Attacking such a protocol is extremely difficult: the third party listening to the channel cannot fully synchronize without knowing the private key of one of the parties. And this key can be made very long without a significant drop in the performance of the perceptron. And yet the persistence of the neural key exchange algorithm is still under discussion, it is possible that more effective in practice attacks on it will be developed.
With stochastic learning, weights change pseudo-randomly, and then those changes are discarded that degrade the result — that is, even with the same private keys and the same initial flow (random or non-random), the session key will be different each time. Attacking such a protocol is extremely difficult: the third party listening to the channel cannot fully synchronize without knowing the private key of one of the parties. And this key can be made very long without a significant drop in the performance of the perceptron. And yet the persistence of the neural key exchange algorithm is still under discussion, it is possible that more effective in practice attacks on it will be developed.Perceptrons can be used not only to generate a key - in a synchronized form, they are quite suitable for data encryption and decryption. There is, however, a nuance: neural networks are prone to distort the processed data, that is, on top of this you will need to push down the error correction protocol. AES and other traditional symmetric algorithms lack this disadvantage.
Genetic algorithms
 These algorithms are also well studied. They are built on the principles of evolution postulated by neo-Darwinism. We take a set of initial values (individual), collect a population from many different individuals, cut off the worst individuals with the help of the fitness function, create offspring from the best individuals by recombining the values with the addition of mutations (random correction of values), and so on. Fitness function plays the role of an aggressive environment, its value determines the proximity of the individual to the desired solution. After a certain number of iterations, we will have an individual close enough to solving the problem. Everything, as in life.
These algorithms are also well studied. They are built on the principles of evolution postulated by neo-Darwinism. We take a set of initial values (individual), collect a population from many different individuals, cut off the worst individuals with the help of the fitness function, create offspring from the best individuals by recombining the values with the addition of mutations (random correction of values), and so on. Fitness function plays the role of an aggressive environment, its value determines the proximity of the individual to the desired solution. After a certain number of iterations, we will have an individual close enough to solving the problem. Everything, as in life.As for the use in cryptography, GAs are useful in the development of primitives - Boolean functions and S-blocks. These are the most important elements of block and stream ciphers; without them, a cipher can be cracked using statistical analysis when comparing plain text and ciphertext. Moreover, if they are created randomly, they will be non-optimal and may weaken the algorithm against certain methods of cryptanalysis. Therefore, cipher developers construct primitives manually, and in this process there is something very hellish for the developers themselves.
It is here that genetic algorithms are very much in topic, since in fact it is the task of searching for extrema by several criteria: balance, high nonlinearity, low autocorrelation, high algebraic degree. For
In addition, cryptographers have the idea of using genetic algorithms directly for symmetric encryption without the use of a Boolean function. The essence is in the iterative encryption of each data block with different initial pseudo-random sequences. The blocks eventually evolve to the complete absence of statistical correlation of the ciphertext with the source text. At the same time, the encryption process slows down in proportion to the number of iterations (generations).
Artificial immune systems
A relatively new area based on known mechanisms of the immune system of living organisms. In general, it is a system of elements that must meet the goal (to identify antigens), not to worsen the result (not to attack the cells of their own organism).
There are several algorithms, similar, by the way, to genetic ones. Thus, in the clonal selection algorithm, those cells are selected that respond best to antigens, while instead of creating offspring, as in GA, successful cells are cloned with the addition of mutations. The better the cell is, the more copies are produced, and the fewer mutations are introduced. Then the population of cells is checked again for the reaction to the antigen (for fitness functions), the best are selected again, etc.
The principle of the immune network algorithm is somewhat different. The cells form a network, with each cell reacting both to the antigen and to the neighboring cells, stimulated (that is, cloned and mutated), and the cell to which the neighboring cells react is inhibited. In the absence of antigens, the network gets rid of the worst cells and stabilizes, and in the presence of the antigen, the best cells begin to multiply, destroying the lower-quality neighbors.
Artificial immune networks are most often used in much the same way as natural ones, that is, to detect a malicious invasion of the system. As for the use in cryptography, immune algorithms have potential in the same areas as neural networks and genetic algorithms, since they are related to them.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/329332/
All Articles