Clever blocking bypass in Ukraine
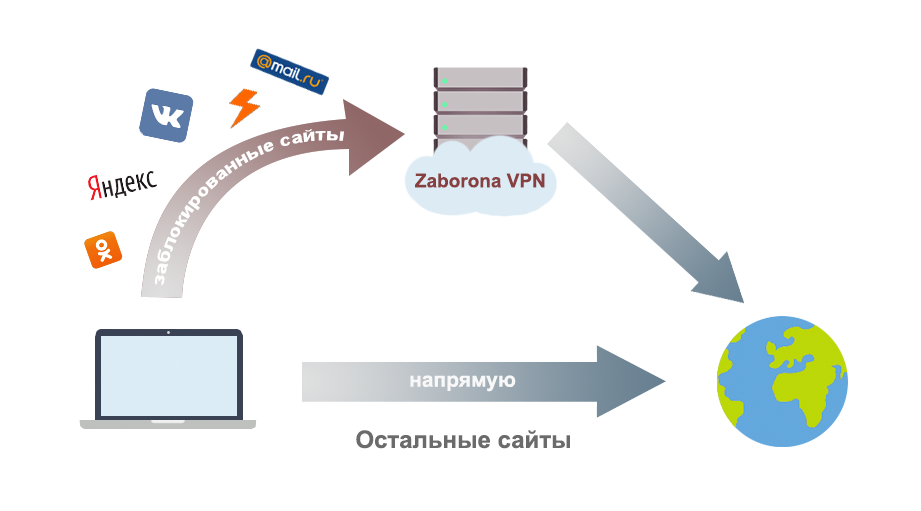
The article describes how to set up a free service Zaborona.Help to bypass website blocking in Ukraine.
The peculiarity of the configuration is that only traffic to blocked networks is routed through VPN , other sites work directly . It works on all major platforms: Windows, Linux, iOS, MacOS, Android.
VPN does not affect Internet speed, does not replace IP for other sites and does not interfere with the operation of online games, voice traffic, etc.
')
The problems of popular bypass locks
- Browser plug - ins - do not work for mobile applications, they proxy all traffic through their servers. Have access to the content of the page and threaten security.
- Regular VPNs route all traffic through their servers. Affects the speed of the Internet, increase delays, replaces the IP for all sites.
- Proxy browsers do not allow to bypass the blocking of mobile applications.
The configuration process is described on the example of OpenVPN and can be easily repeated in a few minutes.
Settings on the client side are performed using a single configuration file and do not require manual entry of addresses and passwords.
Server selection
The VPN server must have good connectivity at the network level with your ISP so that delays are minimal, as well as with the resources you plan to visit through this VPN. Datacenters in the USA, China, Japan are not the best choice.
I will give several options that I chose for the service Zaborona.help:
Linode.com - cool and reliable hosting with good channels.
Pros:
- Gigabit channel, good connectivity in Europe
- Routing unit / 64 IPv6 addresses. You can issue real IPs directly to VPN clients.
Minuses:
- The minimum cost is $ 5
- 1TB of outgoing traffic at the minimum rate
- $ 20 for each terabyte of over-limit
Scaleway.com - cheap hosting with unlimited traffic.
Pros:
- The minimum price for a server is € 3
- Unlimited traffic, 200Mbit / s
- Datacenter in Poland (close to Ukraine)
Minuses:
- One IPv6 address per server (how stupid!)
- Not the best connectivity with locked resources
For reliability, several servers from both providers are used at once. Balancing is done primitively, at the DNS level.
The service domain to which vpn.zaborona.help clients are connected has several A-records directed to all servers at once. This allows you to evenly spread clients across servers. The minimum TTL of records allows you to quickly remove the problem server from the general list and redirect clients.
List of blocked services
From the presidential decree of Ukraine №133 / 2017 there is a list of companies subject to blocking. Knowing this list, you can make a list of all IP ranges owned by these companies.
To do this, you can use the service bgp.he.net
Here's what the BGP announcements of Yandex look like bgp.he.net/AS13238#_prefixes
We collect all the necessary ranges. Neighboring networks are combined into one range to reduce the total number of routes on the client.
At the output we get the following list excluding IPv6 ranges:
Network list routed through Zaborona VPN server
# Vkontakte
- 87.240.128.0/18
93.186.224.0/20
95.142.192.0/20
95.213.0.0/18
185.29.130.0/24
185.32.248.0/22
2a00: bdc0 :: / 36
2a00: bdc0: e003 :: / 48
2a00: bdc0: e004 :: / 46
2a00: bdc0: e008 :: / 48
2a00: bdc0: f000 :: / 36
# Yandex
- 5.45.192.0/18
5.255.192.0/18
37.9.64.0/18
37.140.128.0/18
77.75.152.0/22
77.75.159.0/24
77.88.0.0/18
84.201.128.0/18
87.250.224.0/19
93.158.128.0/18
95.108.128.0/17
100.43.64.0/19
109.235.160.0/21
130.193.32.0/19
141.8.128.0/18
178.154.128.0/17
185.32.185.0/24
185.32.186.0/24
185.71.76.0/22
199.21.96.0/22
199.36.240.0/22
213.180.192.0/19
2001: 678: 384 :: / 48
2620: 10f: d000 :: / 44
2a02: 6b8 :: / 32
2a02: 5180 :: / 32
# Mail.ru
- 5.61.16.0/21
5.61.232.0/21
79.137.157.0/24
79.137.183.0/24
94.100.176.0/20
95.163.32.0/19
95.163.248.0/21
128.140.168.0/21
178.22.88.0/21
178.237.16.0/20
185.5.136.0/22
185.16.148.0/22
185.16.244.0/22
188.93.56.0/21
194.186.63.0/24
195.211.20.0/22
195.218.168.0/24
217.20.144.0/20
217.69.128.0/20
178.22.91.0/24
178.22.92.0/23
185.16.244.0/23
195.211.128.0/22
208.87.94.0/24
2a00: 1148 :: / 32
2a00: b4c0 :: / 32
# Kaspersky Lab
- 77.74.176.0/22
77.74.181.0/24
77.74.183.0/24
93.159.228.0/22
185.54.220.0/23
185.85.12.0/24
185.85.14.0/23
77.74.176.0/21
91.103.64.0/21
93.159.224.0/21
2a03: 2480 :: / 33
- 87.240.128.0/18
93.186.224.0/20
95.142.192.0/20
95.213.0.0/18
185.29.130.0/24
185.32.248.0/22
2a00: bdc0 :: / 36
2a00: bdc0: e003 :: / 48
2a00: bdc0: e004 :: / 46
2a00: bdc0: e008 :: / 48
2a00: bdc0: f000 :: / 36
# Yandex
- 5.45.192.0/18
5.255.192.0/18
37.9.64.0/18
37.140.128.0/18
77.75.152.0/22
77.75.159.0/24
77.88.0.0/18
84.201.128.0/18
87.250.224.0/19
93.158.128.0/18
95.108.128.0/17
100.43.64.0/19
109.235.160.0/21
130.193.32.0/19
141.8.128.0/18
178.154.128.0/17
185.32.185.0/24
185.32.186.0/24
185.71.76.0/22
199.21.96.0/22
199.36.240.0/22
213.180.192.0/19
2001: 678: 384 :: / 48
2620: 10f: d000 :: / 44
2a02: 6b8 :: / 32
2a02: 5180 :: / 32
# Mail.ru
- 5.61.16.0/21
5.61.232.0/21
79.137.157.0/24
79.137.183.0/24
94.100.176.0/20
95.163.32.0/19
95.163.248.0/21
128.140.168.0/21
178.22.88.0/21
178.237.16.0/20
185.5.136.0/22
185.16.148.0/22
185.16.244.0/22
188.93.56.0/21
194.186.63.0/24
195.211.20.0/22
195.218.168.0/24
217.20.144.0/20
217.69.128.0/20
178.22.91.0/24
178.22.92.0/23
185.16.244.0/23
195.211.128.0/22
208.87.94.0/24
2a00: 1148 :: / 32
2a00: b4c0 :: / 32
# Kaspersky Lab
- 77.74.176.0/22
77.74.181.0/24
77.74.183.0/24
93.159.228.0/22
185.54.220.0/23
185.85.12.0/24
185.85.14.0/23
77.74.176.0/21
91.103.64.0/21
93.159.224.0/21
2a03: 2480 :: / 33
This list changes extremely rarely, so it will not be difficult to update it if necessary.
OpenVPN setup
OpenVPN 2.4 will be used on the server. It is recommended to use this version. In the repositories of Ubuntu LTS version of OpenVPN 2.3, therefore, you can install the required version by connecting the official openvpn repository .
Certificate issuance
The easiest way to generate certificates is to use the easy-rsa utility. This fork from ValdikSS allows you to generate certificates that are simultaneously suitable for both OpenVPN and Ipsec.
Key generation with easy-rsa
$ git clone https://github.com/ValdikSS/easy-rsa-ipsec.git
$ cd easy-rsa-ipsec/easyrsa3
$ ./easyrsa init-pki
init-pki complete; you may now create a CA or requests.
$ ./easyrsa build-ca nopass
Generating a 2048 bit RSA private key
…
Common Name (eg: your user, host, or server name) [Easy-RSA CA]:Cool VPN Server
…
$ ./easyrsa build-server-full zaborona.help nopass
Generating a 2048 bit RSA private key
…
Write out database with 1 new entries
Data Base Updated
# public . .
$ ./easyrsa build-client-full public nopass
Generating a 2048 bit RSA private key
…
Write out database with 1 new entries
Data Base Updated
:
:
easyrsa3/pki/ca.crt —
easyrsa3/pki/issued/zaborona.help.crt —
easyrsa3/pki/private/zaborona.help.key —
:
easyrsa3/pki/ca.crt —
easyrsa3/pki/issued/public.crt —
easyrsa3/pki/private/public.key —
. VPN . - 0.0.0.0 .
DNS , , , VPN.
OpenVPN
mode server
proto tcp
dev-type tun # tun, L2
dev zaborona # tun
topology subnet
server 192.168.224.0 255.255.252.0 # IP . ,
server-ipv6 2a01:7e01:e001:77:8000::/65 # IPv6 . , ipv6
push "dhcp-option DNS 8.8.8.8" # DNS
push "route 8.8.8.8" # VPN
push "dhcp-option DNS 74.82.42.42" # HE.net DNS
push "route 74.82.42.42" # Route to HE.net DNS
txqueuelen 250
keepalive 300 900
persist-tun
persist-key
cipher AES-128-CBC
ncp-ciphers AES-128-GCM
user nobody
duplicate-cn
# log logs/openvpn.log
#status logs/status.log 30
ca ca.crt
cert zaborona.help.crt
key zaborona.help.key
dh dh2048.pem
# Routes
# Yandex network
push "route 5.45.192.0 255.255.192.0"
push "route 5.255.192.0 255.255.192.0"
push "route 37.9.64.0 255.255.192.0"
push "route 37.140.128.0 255.255.192.0"
push "route 77.88.0.0 255.255.192.0"
push "route 84.201.128.0 255.255.192.0"
push "route 87.250.224.0 255.255.224.0"
push "route 93.158.128.0 255.255.192.0"
push "route 95.108.128.0 255.255.128.0"
push "route 100.43.64.0 255.255.224.0"
push "route 130.193.32.0 255.255.224.0"
push "route 141.8.128.0 255.255.192.0"
push "route 178.154.128.0 255.255.128.0"
push "route 199.21.96.0 255.255.252.0"
push "route 199.36.240.0 255.255.252.0"
push "route 213.180.192.0 255.255.224.0"
push "route-ipv6 2620:10f:d000::/44"
push "route-ipv6 2a02:6b8::/32"
# Mail.ru network
push "route 5.61.16.0 255.255.248.0"
push "route 5.61.232.0 255.255.248.0"
push "route 79.137.157.0 255.255.255.0"
push "route 79.137.183.0 255.255.255.0"
push "route 94.100.176.0 255.255.240.0"
push "route 95.163.32.0 255.255.224.0"
push "route 95.163.248.0 255.255.248.0"
push "route 128.140.168.0 255.255.248.0"
push "route 178.22.88.0 255.255.248.0"
push "route 178.237.16.0 255.255.240.0"
push "route 185.5.136.0 255.255.252.0"
push "route 185.16.148.0 255.255.252.0"
push "route 185.16.244.0 255.255.252.0"
push "route 188.93.56.0 255.255.248.0"
push "route 194.186.63.0 255.255.255.0"
push "route 195.211.20.0 255.255.252.0"
push "route 195.218.168.0 255.255.255.0"
push "route 217.20.144.0 255.255.240.0"
push "route 217.69.128.0 255.255.240.0"
push "route-ipv6 2a00:1148::/32"
push "route-ipv6 2a00:a300::/32"
push "route-ipv6 2a00:b4c0::/32"
# VK.com network
push "route 87.240.128.0 255.255.192.0"
push "route 93.186.224.0 255.255.240.0"
push "route 95.142.192.0 255.255.240.0"
push "route 95.213.0.0 255.255.192.0"
push "route 185.32.248.0 255.255.252.0"
push "route-ipv6 2a00:bdc0::/36"
push "route-ipv6 2a00:bdc0:e006::/48"
# Kaspersky network
push "route 77.74.176.0 255.255.252.0"
push "route 77.74.181.0 255.255.255.0"
push "route 77.74.183.0 255.255.255.0"
push "route 93.159.228.0 255.255.252.0"
push "route 185.54.220.0 255.255.254.0"
push "route 185.85.12.0 255.255.255.0"
push "route 185.85.14.0 255.255.254.0"
/etc/openvpn
zaborona.conf —
ca.crt —
zaborona.help.crt —
zaborona.help.key —
, , .
.ovpn
nobind
client
# . DNS.
remote vpn.zaborona.help
remote-cert-tls server
cipher AES-128-CBC
setenv opt ncp-ciphers AES-128-GCM
setenv opt block-outside-dns
dev tun
proto tcp
<ca>
easyrsa3/pki/ca.crt
</ca>
<cert>
easyrsa3/pki/issued/public.crt
</cert>
<key>
easyrsa3/pki/private/public.key
</key>
: OpenVPN .
c :
Windows
MacOS
iOS
Android
, , Github. - , pull request-.
, VPN , . , .
Source: https://habr.com/ru/post/329248/
All Articles