Bitdefender Hypervisor Introspection: a new means of dealing with hidden cyber threats
Some malware, infecting the system, may begin to perform its functions months after the infection itself. Being on a virtual machine, such malware when connected to a server can spread throughout the data center and corporate network. To counter such threats, Citrix and Bitdefender have developed a security tool that runs inside the hypervisor to detect malware running in guest virtual machines. In this case, we are talking about a Citrix server called XenServer, and the security product itself is called Bitdefender Hypervisor Introspection (HVI).
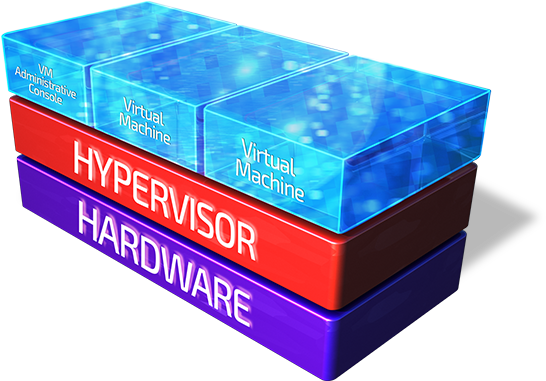
Bitdefender HVI is the first solution to monitor guest virtual machines and low-level real-time memory scanning. With it, you can track a variety of malware, detect and block them. The system can effectively deal with various threats, including targeted attacks like Carbanak, Turla, APT28 and NetTraveler.
What is special
')
If the rootkit or exploit that is inside the guest virtual machine has hidden its tracks, even advanced security tools will have difficulty finding them. The solution is to view this virtual machine from the outside, if you can control the processes inside it.
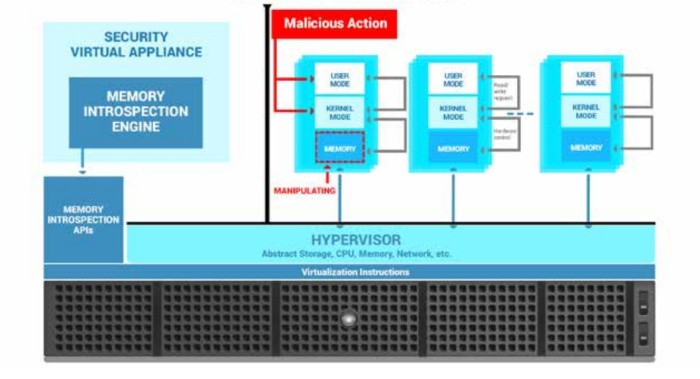
The tool Bitdefender offers is a bare-metal hypervisor that can scan virtual machines while remaining isolated from them. That way, it will see everything that happens in your infrastructure, and the malware will not be able to reach it and prevent it from working. This approach has not been previously used to create security features.

The hypervisor is isolated from the connected virtual machines and cannot be attacked by malware.
How does it work
The hypervisor provides detailed low-level scanning of the memory used by each virtual machine. To implement this concept, Citrix developed a new API in XenServer. It processes data from the hypervisor about all the memory used by a particular virtual machine. Thanks to this, Hypervisor Introspection is able to detect traces of malware actions at a level where it is simply impossible to hide them.
Thus, using Bitdefender HVI can detect hidden threats that could not make themselves known for months. The same applies to zero-day threats. Bitdefender HVI detects a threat by characteristic memory actions that are not visible at the operating system level.
Of course, there is a traditional security option - placing an agent in a virtual OS that would track changes in the system and start detecting malware if malware is detected. But the snag is that when there are tens and hundreds of virtual machines, you need very large resources to complete this task. In any case, other security solutions may work in the IT infrastructure. They do not conflict with Bitdefender HVI and perform their functions in the normal mode.
By the way, such traditional means of protection - with the installation of agents inside virtual machines - Bitdefender has also. They provide security for virtual environments on any platform: VMware, Citrix, Microsoft Hyper-V, KVM, Oracle, and others, providing real-time scanning capabilities for file systems, processes, memory, and the registry. For more information on these tools, please refer to the link .
When detecting malware actions in memory in a virtual machine, HVI provides detailed reports on the attack chain, including the affected processes, the type of violation and the time scale of the attack. In addition, HVI tools can deploy anti-malware tools directly into virtual machines when they connect to the system. All this allows third-party security tools to continue to work in the normal mode, not paying attention to virtual machines, saving time and resources, and increasing the reliability of the security system as a whole.

Diagram of the actions of malware and reflection attacks
An excellent example of the effectiveness of the technologies used by Bitdefender (including HVI, as well as its own machine learning model) was demonstrated by the recent mass infection with the WannaCry cipher. None of the endpoints on which Bitdefender protection was used caught this infection. So, Hypervisor Introspection was able to neutralize the EternalBlue exploit from the very beginning of its appearance, even before Microsoft released the patch.
Action control
You can control and configure Bitdefender Hypervisor Introspection using the Bitdefender Gravity Zone system interface. There you can get access to managing security policies, protecting specific servers and virtual machines, determine the HVI mode of operation for specific processes and servers in general, configure the firewall, antimalware tools, monitor devices, applications and content, get detailed statistics on the activity of security tools and malware.






You can learn more about managing HVI with the Gravity Zone from the video .
System requirements
For Bitdefender HVI to work, the following conditions are necessary:
Host
- Any Intel Sandy Bridge processor or higher with support for Intel Virtualization Technology;
- VT-x or VT-d extensions activated in BIOS;
- XenServer 7 or higher.
Guest operating systems
Desktop Windows families:
- Windows 10;
- Windows 8.1;
- Windows 8;
- Windows 7.
Windows Server Families:
- Windows Server 2012 R2;
- Windows Server 2012;
- Windows Server 2008 R2.
Linux family operating systems
- Debian 8.2, 64-bit;
- Ubuntu 16.04 LTS, 64-bit;
- Ubuntu 15.04, 64-bit;
- Ubuntu 14.04 LTS 64-bit;
- CentOS 7, 64-bit;
- Red Hat Enterprise Linux 7, 64-bit.
As you can see, Bitdefender HVI currently works only with XenServer, the Citrix virtualization stack. However, you need to take into account that XenServer is based on Xen, which is open source and works in some of the world's major cloud services. Based on this, it can be expected that the situation with the “monopoly” position of XenServer will change and Bitdefender HVI will also be seen from other manufacturers. Moreover, Bitdefender announced a large contribution of Intel and Linux Foundation to the development of this tool.
Instead of an afterword
Bitdefender Hypervisor Introspection gives users a new method for detecting and neutralizing malware. It is very effective and has already proven its worth in practice - in the case of countering the EternalBlue exploit and the cipher WannaCry. At the moment, one of its main drawbacks is sharpening under XenServer, because not everyone uses it. But since HVI has already demonstrated its high efficiency, it can be expected that it will appear under other products. In all other respects, this system will significantly complicate the life of cybercriminals and increase the security of your IT infrastructure.

Bitdefender HVI is the first solution to monitor guest virtual machines and low-level real-time memory scanning. With it, you can track a variety of malware, detect and block them. The system can effectively deal with various threats, including targeted attacks like Carbanak, Turla, APT28 and NetTraveler.
What is special
')
If the rootkit or exploit that is inside the guest virtual machine has hidden its tracks, even advanced security tools will have difficulty finding them. The solution is to view this virtual machine from the outside, if you can control the processes inside it.

The tool Bitdefender offers is a bare-metal hypervisor that can scan virtual machines while remaining isolated from them. That way, it will see everything that happens in your infrastructure, and the malware will not be able to reach it and prevent it from working. This approach has not been previously used to create security features.

The hypervisor is isolated from the connected virtual machines and cannot be attacked by malware.
How does it work
The hypervisor provides detailed low-level scanning of the memory used by each virtual machine. To implement this concept, Citrix developed a new API in XenServer. It processes data from the hypervisor about all the memory used by a particular virtual machine. Thanks to this, Hypervisor Introspection is able to detect traces of malware actions at a level where it is simply impossible to hide them.
Thus, using Bitdefender HVI can detect hidden threats that could not make themselves known for months. The same applies to zero-day threats. Bitdefender HVI detects a threat by characteristic memory actions that are not visible at the operating system level.
Of course, there is a traditional security option - placing an agent in a virtual OS that would track changes in the system and start detecting malware if malware is detected. But the snag is that when there are tens and hundreds of virtual machines, you need very large resources to complete this task. In any case, other security solutions may work in the IT infrastructure. They do not conflict with Bitdefender HVI and perform their functions in the normal mode.
By the way, such traditional means of protection - with the installation of agents inside virtual machines - Bitdefender has also. They provide security for virtual environments on any platform: VMware, Citrix, Microsoft Hyper-V, KVM, Oracle, and others, providing real-time scanning capabilities for file systems, processes, memory, and the registry. For more information on these tools, please refer to the link .
When detecting malware actions in memory in a virtual machine, HVI provides detailed reports on the attack chain, including the affected processes, the type of violation and the time scale of the attack. In addition, HVI tools can deploy anti-malware tools directly into virtual machines when they connect to the system. All this allows third-party security tools to continue to work in the normal mode, not paying attention to virtual machines, saving time and resources, and increasing the reliability of the security system as a whole.

Diagram of the actions of malware and reflection attacks
An excellent example of the effectiveness of the technologies used by Bitdefender (including HVI, as well as its own machine learning model) was demonstrated by the recent mass infection with the WannaCry cipher. None of the endpoints on which Bitdefender protection was used caught this infection. So, Hypervisor Introspection was able to neutralize the EternalBlue exploit from the very beginning of its appearance, even before Microsoft released the patch.
Action control
You can control and configure Bitdefender Hypervisor Introspection using the Bitdefender Gravity Zone system interface. There you can get access to managing security policies, protecting specific servers and virtual machines, determine the HVI mode of operation for specific processes and servers in general, configure the firewall, antimalware tools, monitor devices, applications and content, get detailed statistics on the activity of security tools and malware.






You can learn more about managing HVI with the Gravity Zone from the video .
System requirements
For Bitdefender HVI to work, the following conditions are necessary:
Host
- Any Intel Sandy Bridge processor or higher with support for Intel Virtualization Technology;
- VT-x or VT-d extensions activated in BIOS;
- XenServer 7 or higher.
Guest operating systems
Desktop Windows families:
- Windows 10;
- Windows 8.1;
- Windows 8;
- Windows 7.
Windows Server Families:
- Windows Server 2012 R2;
- Windows Server 2012;
- Windows Server 2008 R2.
Linux family operating systems
- Debian 8.2, 64-bit;
- Ubuntu 16.04 LTS, 64-bit;
- Ubuntu 15.04, 64-bit;
- Ubuntu 14.04 LTS 64-bit;
- CentOS 7, 64-bit;
- Red Hat Enterprise Linux 7, 64-bit.
As you can see, Bitdefender HVI currently works only with XenServer, the Citrix virtualization stack. However, you need to take into account that XenServer is based on Xen, which is open source and works in some of the world's major cloud services. Based on this, it can be expected that the situation with the “monopoly” position of XenServer will change and Bitdefender HVI will also be seen from other manufacturers. Moreover, Bitdefender announced a large contribution of Intel and Linux Foundation to the development of this tool.
Instead of an afterword
Bitdefender Hypervisor Introspection gives users a new method for detecting and neutralizing malware. It is very effective and has already proven its worth in practice - in the case of countering the EternalBlue exploit and the cipher WannaCry. At the moment, one of its main drawbacks is sharpening under XenServer, because not everyone uses it. But since HVI has already demonstrated its high efficiency, it can be expected that it will appear under other products. In all other respects, this system will significantly complicate the life of cybercriminals and increase the security of your IT infrastructure.
Source: https://habr.com/ru/post/329184/
All Articles