The blackmailer WannaCrypt attacks un-upgraded systems
On May 12, a technical article appeared on Microsoft's official blog with comments on the blackmailer WannaCrypt. Since this topic still excites many, we have translated it for you. We invite under the cat.

On May 12, 2017, we discovered a new blackmailer program that spreads like a worm, using previously eliminated vulnerabilities. On most computers, security updates are automatically installed, but some users and businesses postpone their installation. Unfortunately, a blackmailer program, known as WannaCrypt , attacks computers that do not have patches that eliminate these vulnerabilities. Because the attacks continue, we remind users to install the security update MS17-010 if they have not done so yet.
The anti-virus telemetry system Microsoft immediately detected signs of an attack. Our expert systems allowed us to recognize and define the context of this new attack in the process of its development, which made it possible for Windows Defender to provide real-time protection. Through the use of automated analysis, machine learning and predictive modeling, we were able to quickly organize protection against this malware.
')
In this blog, we present the results of a preliminary analysis of this attack. Please note that we are continuing to study this threat. The attack continues, and there is still the possibility that the attackers will try to counteract our defenses.
Blackmail programs usually do not spread quickly. In such malicious programs as WannaCrypt (other names are WannaCry, WanaCrypt0r, WCrypt, and WCRY), social engineering techniques and email are generally used as the main attack vector for users to download and launch malware. But in this non-core case, the creators of the blackmailer used a publicly available exploit code to fix the SMB EternalBlue server vulnerability ( CVE-2017-0145 ), which manifests itself when sending a specially crafted package to the SMBv1 target server. This vulnerability was eliminated in security bulletin MS17-010 , released March 14, 2017.
The WannaCrypt propagation mechanism is borrowed from well-known open SMB exploits , which provided the blackmailer with the worm's capabilities, creating an entry point for machines that were not updated even after the security update.
The exploit code WannaCrypt is designed only for non-upgraded Windows 7 and Windows Server 2008 systems (or earlier versions of the OS), so this attack is harmless to machines running Windows 10.
We did not find evidence of which particular entry vector was involved in the attack, but there are two highly probable scenarios that, in our opinion, explain the spread of this blackmailer:
Malicious software takes the form of a trojan dropper consisting of two components:
Dropper tries to connect to the following domains using the InternetOpenUrlA () API function:
In case of successful connection to the domains, the dropper stops further system infection by the blackmailer component and does not attempt to exploit the vulnerability for further propagation; he just stops working. But if the connection fails, the virus continues to drop the blackmailer component and creates a service in the system.
In other words, unlike most other malware infections, IT administrators should not block access to these domains . Note that the virus does not support work through a proxy, so you may need to create a corresponding record in the local DNS. This entry does not have to point to a server on the Internet — it is enough that it redirects to any available server that accepts connections on TCP port 80.

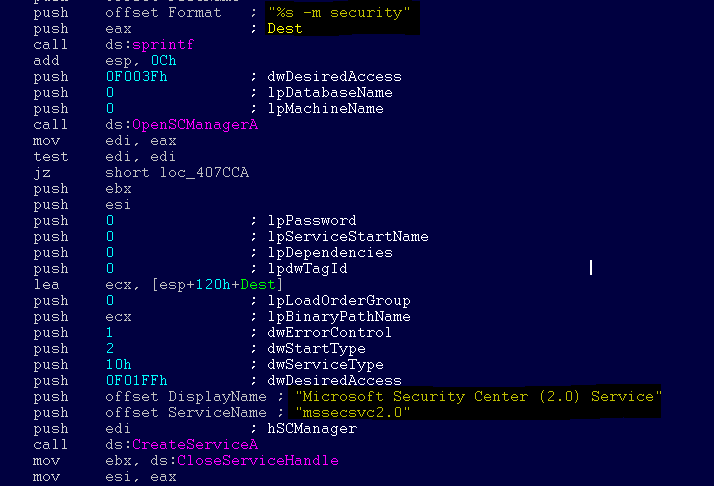
The virus creates a service called mssecsvc2.0 , whose role is to exploit the SMB vulnerability on other computers accessible from the infected system:
Service Name: mssecsvc2.0
Service Description: (Microsoft Security Center (2.0) Service)
Service options: “-m security”
The blackmailer is a dropper that contains a password-protected ZIP archive in its resource section. The procedure for encrypting documents and files in a zip archive contain tools, a decryption utility, and a message requesting redemption. In the examples that came to us for analysis, the ZIP archive was encrypted with the password WNcry @ 2ol7.
In the course of its work, WannaCrypt creates the following parameters in the system registry:
The component replaces the desktop wallpaper with an image for ransom by changing the following registry key setting.
It creates the following files in the working directory of the blackmailer component:
WannaCrypt can also create the following files:
The blackmailer component sometimes also creates a service with a random name and the following path to the image: “cmd.exe / c“ <working directory of the blackmailer component> \ tasksche.exe ”” .
The component searches all computer files with the following extensions:
.123, .jpeg, .rb, .602, .jpg, .rtf, .doc, .js, .sch, .3dm, .jsp, .sh, .3ds, .key, .sldm, .3g2, .lay , .sldm, .3gp, .lay6, .sldx, .7z, .ldf, .slk, .accdb, .m3u, .sln, .aes, .m4u, .snt, .ai, .max, .sql,. ARC, .mdb, .sqlite3, .asc, .mdf, .sqlitedb, .asf, .mid, .stc, .asm, .mkv, .std, .asp, .mml, .sti, .avi, .mov, .stw, .backup, .mp3, .suo, .bak, .mp4, .svg, .bat, .mpeg, .swf, .bmp, .mpg, .sxc, .brd, .msg, .sxd, .bz2 , .myd, .sxi, .c, .myi, .sxm, .cgm, .nef, .sxw, .class, .odb, .tar, .cmd, .odg, .tbk, .cpp, .odp,. tgz, .crt, .ods, .tif, .cs, .odt, .tiff, .csr, .onetoc2, .txt, .csv, .ost, .uop, .db, .otg, .uot, .dbf, .otp, .vb, .dch, .ots, .vbs, .der ”, .ott, .vcd, .dif, .p12, .vdi, .dip, .PAQ, .vmdk, .djvu, .pas,. vmx, .docb, .pdf, .vob, .docm, .pem, .vsd, .docx, .pfx, .vsdx, .dot, .php, .wav, .dotm, .pl, .wb2, .dotx, .png, .wk1, .dwg, .pot, .wks, .edb, .potm, .wma, .eml, .potx, .wmv, .fla, .ppam, .xlc, .flv, .pps, .xlm .frm, .ppsm, .xls, .gif, .ppsx, .xlsb, .gpg, .ppt, .xlsm, .gz, .pptm, .xlsx, .h, .pptx, .xlt, .hwp, .ps1, .xltm, .ibd, .psd, .xltx, .iso, .pst, .xlw, .jar, .rar, .zip, .java .raw.
All found files WannaCrypt encrypts and renames, adding the extension .WNCRY to the file name . For example, the file picture.jpg the blackmailer component will encrypt and rename to picture.jpg.WNCRY .
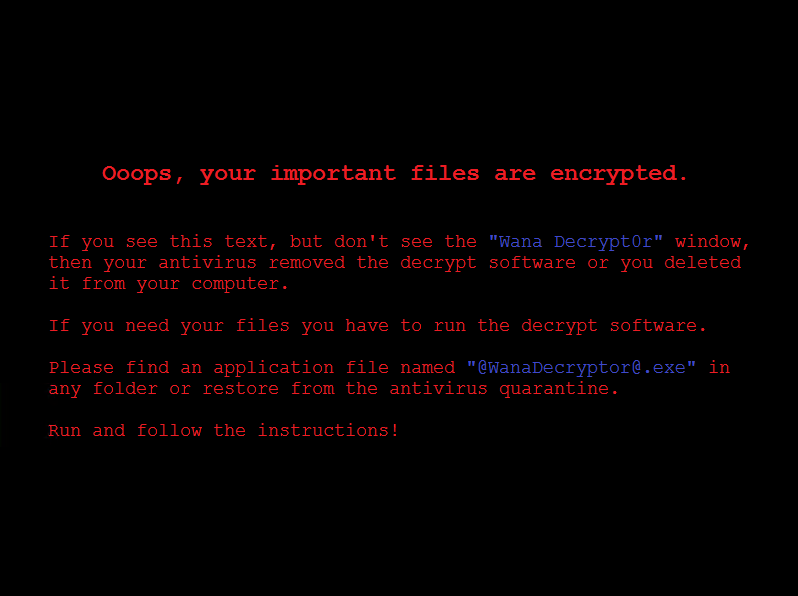
Also in each folder with encrypted files, he creates the file @ Please_Read_Me @ .txt . The latter contains the same ransom demand message that is present on the replaced desktop wallpaper (see screen shot below).
After the encryption is complete, WannaCrypt deletes the shadow copies of the volume with the following command:
cmd.exe / c vssadmin delete & bcdedit / set {default} bootstatuspolicy ignoreallfailures & bcdedit / set {default} recoveryenabled no & wbadmin delete catalog -quiet
After that, the desktop background is replaced by an image with the following message:
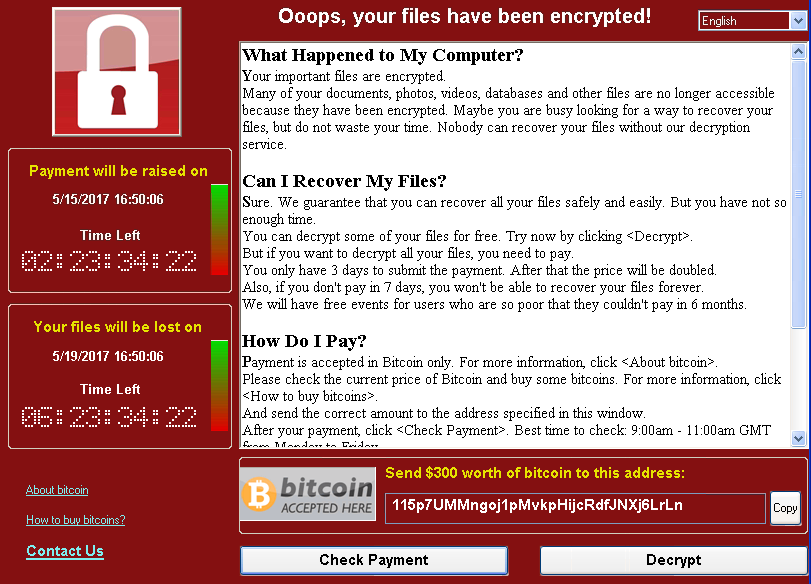
It also runs an executable component that displays a buyback requirement of $ 300 in bitcoins, as well as a timer:
The text is localized into the following languages: Bulgarian, Chinese (Simplified and Traditional), Croatian, Czech, Danish, English, Filipino, Finnish, French, German, Greek, Indonesian, Italian, Japanese, Korean, Latvian, Norwegian, Polish, Portuguese, Romanian, Russian, Slovak, Spanish, Swedish, Turkish and Vietnamese.
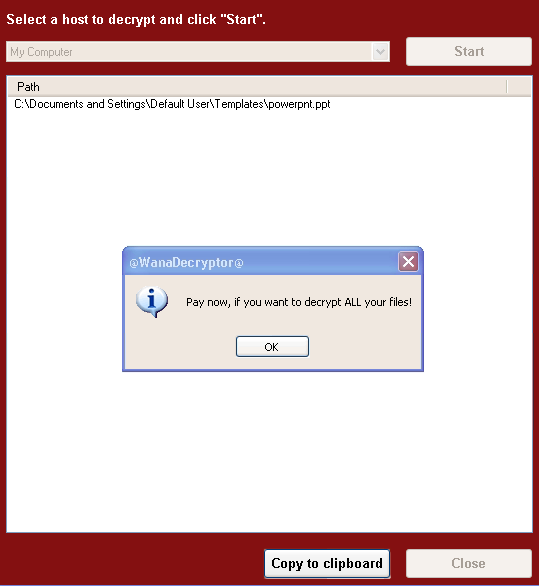
The blackmailer component also demonstrates the ability to decrypt encrypted files, allowing the user to decrypt a few random files for free. After that, he quickly recalls the need to pay the ransom in order to decrypt the remaining files.
The worm attempts to infect non-updated Windows-based machines on the local network. At the same time, it performs a massive scan of Internet IP addresses to find and infect other vulnerable computers. This creates a large amount of SMB traffic from the infected host, as security specialists can notice, as shown below.
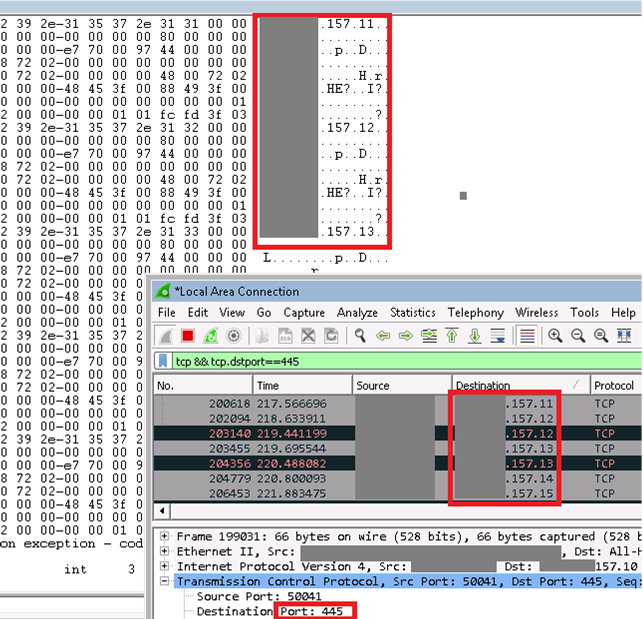
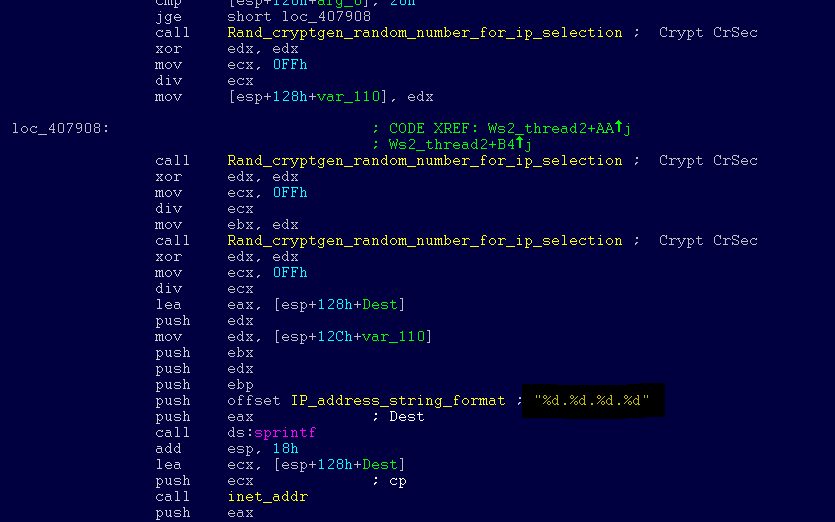
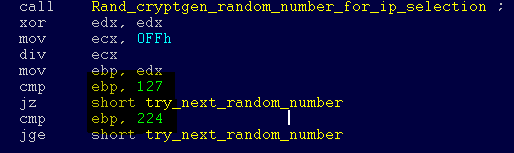
The Internet scanning procedure generates random octets collected into IPv4 addresses. After this, the malware attacks a computer located at an available IP address, trying to exploit the CVE-2017-0145 vulnerability. The program does not infect computers that have the first octet of an IPv4 address equal to 127 or more than 224, in order not to waste time accessing the local loopback addresses. Once a vulnerable machine has been detected and infected, it becomes the next source of infection for other machines. The infection cycle continues as unprotected computers are detected.
After successfully infecting a vulnerable computer, the malware executes shell-level code at the kernel level, which seems to be copied from an open Trojan using the DOUBLEPULSAR backdoor, but with certain changes to reset and execute the blackmailer component dumper for 32 and 64-bit systems.
To get the most advanced protection from Microsoft, upgrade your system to Windows 10 . Keeping your computer up to date allows you to take advantage of the latest features and active protection mechanisms present in the latest versions of Windows.
We recommend that customers who have not yet installed security update MS17-010 do this as quickly as possible. If you are currently unable to install this update, we recommend two possible solutions that will reduce the scale of infection:
Windows Defender Anti-Virus (Windows Defender) identifies this threat as Ransom: Win32 / WannaCrypt , starting with update 1.243.297.0. Windows Defender Antivirus uses cloud-based protection that protects against the latest threats.
At enterprises, it is recommended to use Device Guard to block devices and ensure kernel security based on virtualization, which ensures that only trusted applications run and effectively prevents the execution of malicious software.
Use Advanced Threat Protection Office 365 protection , which has a machine learning function that blocks dangerous attachments in email messages, for example, containing blackmailers.
Monitor network performance using Advanced Threat Protection (ATP) in Windows Defender , which notifies information security personnel of suspicious activities. Download this brochure to find out how ATP in Windows Defender helps you find, investigate, and eliminate blackmailers from the network. Windows Defender Advanced Threat Protection - Ransomware response playbook .
The SHA1 code of the analyzed examples:
Files created by the blackmailer:
Registry keys created by the blackmailer:
If you see an inaccuracy of the translation, please report this to private messages.

On May 12, 2017, we discovered a new blackmailer program that spreads like a worm, using previously eliminated vulnerabilities. On most computers, security updates are automatically installed, but some users and businesses postpone their installation. Unfortunately, a blackmailer program, known as WannaCrypt , attacks computers that do not have patches that eliminate these vulnerabilities. Because the attacks continue, we remind users to install the security update MS17-010 if they have not done so yet.
The anti-virus telemetry system Microsoft immediately detected signs of an attack. Our expert systems allowed us to recognize and define the context of this new attack in the process of its development, which made it possible for Windows Defender to provide real-time protection. Through the use of automated analysis, machine learning and predictive modeling, we were able to quickly organize protection against this malware.
')
In this blog, we present the results of a preliminary analysis of this attack. Please note that we are continuing to study this threat. The attack continues, and there is still the possibility that the attackers will try to counteract our defenses.
Attack vector
Blackmail programs usually do not spread quickly. In such malicious programs as WannaCrypt (other names are WannaCry, WanaCrypt0r, WCrypt, and WCRY), social engineering techniques and email are generally used as the main attack vector for users to download and launch malware. But in this non-core case, the creators of the blackmailer used a publicly available exploit code to fix the SMB EternalBlue server vulnerability ( CVE-2017-0145 ), which manifests itself when sending a specially crafted package to the SMBv1 target server. This vulnerability was eliminated in security bulletin MS17-010 , released March 14, 2017.
The WannaCrypt propagation mechanism is borrowed from well-known open SMB exploits , which provided the blackmailer with the worm's capabilities, creating an entry point for machines that were not updated even after the security update.
The exploit code WannaCrypt is designed only for non-upgraded Windows 7 and Windows Server 2008 systems (or earlier versions of the OS), so this attack is harmless to machines running Windows 10.
We did not find evidence of which particular entry vector was involved in the attack, but there are two highly probable scenarios that, in our opinion, explain the spread of this blackmailer:
- Mailing developed in accordance with the social engineering techniques of e-mail messages that pushed users to open them and run malicious code and activate the SMB exploit worm spreading functionality.
- Infection through an SMB exploit when accessing unpatched computers from other infected machines.
Dropper
Malicious software takes the form of a trojan dropper consisting of two components:
- Component attempting to exploit the SME server CVE-2017-0145 vulnerability on other computers.
- The blackmailer component, known as WannaCrypt.
Dropper tries to connect to the following domains using the InternetOpenUrlA () API function:
- www [.] iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea [.] com
- www [.] ifferfsodp9ifjaposdfjhgosurijfaewrwergwea [.] com
In case of successful connection to the domains, the dropper stops further system infection by the blackmailer component and does not attempt to exploit the vulnerability for further propagation; he just stops working. But if the connection fails, the virus continues to drop the blackmailer component and creates a service in the system.
In other words, unlike most other malware infections, IT administrators should not block access to these domains . Note that the virus does not support work through a proxy, so you may need to create a corresponding record in the local DNS. This entry does not have to point to a server on the Internet — it is enough that it redirects to any available server that accepts connections on TCP port 80.

The virus creates a service called mssecsvc2.0 , whose role is to exploit the SMB vulnerability on other computers accessible from the infected system:
Service Name: mssecsvc2.0
Service Description: (Microsoft Security Center (2.0) Service)
Service options: “-m security”

Blackmailer WannaCrypt
The blackmailer is a dropper that contains a password-protected ZIP archive in its resource section. The procedure for encrypting documents and files in a zip archive contain tools, a decryption utility, and a message requesting redemption. In the examples that came to us for analysis, the ZIP archive was encrypted with the password WNcry @ 2ol7.
In the course of its work, WannaCrypt creates the following parameters in the system registry:
- HKLM \ SOFTWARE \ Microsoft \ Windows \ CurrentVersion \ Run \\ <random string> = “<blackmailer component working directory> \ tasksche.exe”
- HKLM \ SOFTWARE \ WanaCrypt0r \\ wd = “<blackmailer component working directory>”
The component replaces the desktop wallpaper with an image for ransom by changing the following registry key setting.
- HKCU \ Control Panel \ Desktop \ Wallpaper: “<working directory of the blackmailer component> \ @ WanaDecryptor @ .bmp”
It creates the following files in the working directory of the blackmailer component:
- 00000000.eky
- 00000000.pky
- 00000000.res
- 274901494632976.bat
- @ Please_Read_Me @ .txt
- @ WanaDecryptor @ .bmp
- @ WanaDecryptor @ .exe
- b.wnry
- c.wnry
- f.wnry
- m.vbs
- msg \ m_bulgarian.wnry
- msg \ m_chinese (simplified) .wnry
- msg \ m_chinese (traditional) .wnry
- msg \ m_croatian.wnry
- msg \ m_czech.wnry
- msg \ m_danish.wnry
- msg \ m_dutch.wnry
- msg \ m_english.wnry
- msg \ m_filipino.wnry
- msg \ m_finnish.wnry
- msg \ m_french.wnry
- msg \ m_german.wnry
- msg \ m_greek.wnry
- msg \ m_indonesian.wnry
- msg \ m_italian.wnry
- msg \ m_japanese.wnry
- msg \ m_korean.wnry
- msg \ m_latvian.wnry
- msg \ m_norwegian.wnry
- msg \ m_polish.wnry
- msg \ m_portuguese.wnry
- msg \ m_romanian.wnry
- msg \ m_russian.wnry
- msg \ m_slovak.wnry
- msg \ m_spanish.wnry
- msg \ m_swedish.wnry
- msg \ m_turkish.wnry
- msg \ m_vietnamese.wnry
- r.wnry
- s.wnry
- t.wnry
- TaskData \ Tor \ libeay32.dll
- TaskData \ Tor \ libevent-2-0-5.dll
- TaskData \ Tor \ libevent_core-2-0-5.dll
- TaskData \ Tor \ libevent_extra-2-0-5.dll
- TaskData \ Tor \ libgcc_s_sjlj-1.dll
- TaskData \ Tor \ libssp-0.dll
- TaskData \ Tor \ ssleay32.dll
- TaskData \ Tor \ taskhsvc.exe
- TaskData \ Tor \ tor.exe
- TaskData \ Tor \ zlib1.dll
- taskdl.exe
- taskse.exe
- u.wnry
WannaCrypt can also create the following files:
- % SystemRoot% \ tasksche.exe
- % SystemDrive% \ intel \ <random directory name> \ tasksche.exe
- % ProgramData% \ <random directory name> \ tasksche.exe
The blackmailer component sometimes also creates a service with a random name and the following path to the image: “cmd.exe / c“ <working directory of the blackmailer component> \ tasksche.exe ”” .
The component searches all computer files with the following extensions:
.123, .jpeg, .rb, .602, .jpg, .rtf, .doc, .js, .sch, .3dm, .jsp, .sh, .3ds, .key, .sldm, .3g2, .lay , .sldm, .3gp, .lay6, .sldx, .7z, .ldf, .slk, .accdb, .m3u, .sln, .aes, .m4u, .snt, .ai, .max, .sql,. ARC, .mdb, .sqlite3, .asc, .mdf, .sqlitedb, .asf, .mid, .stc, .asm, .mkv, .std, .asp, .mml, .sti, .avi, .mov, .stw, .backup, .mp3, .suo, .bak, .mp4, .svg, .bat, .mpeg, .swf, .bmp, .mpg, .sxc, .brd, .msg, .sxd, .bz2 , .myd, .sxi, .c, .myi, .sxm, .cgm, .nef, .sxw, .class, .odb, .tar, .cmd, .odg, .tbk, .cpp, .odp,. tgz, .crt, .ods, .tif, .cs, .odt, .tiff, .csr, .onetoc2, .txt, .csv, .ost, .uop, .db, .otg, .uot, .dbf, .otp, .vb, .dch, .ots, .vbs, .der ”, .ott, .vcd, .dif, .p12, .vdi, .dip, .PAQ, .vmdk, .djvu, .pas,. vmx, .docb, .pdf, .vob, .docm, .pem, .vsd, .docx, .pfx, .vsdx, .dot, .php, .wav, .dotm, .pl, .wb2, .dotx, .png, .wk1, .dwg, .pot, .wks, .edb, .potm, .wma, .eml, .potx, .wmv, .fla, .ppam, .xlc, .flv, .pps, .xlm .frm, .ppsm, .xls, .gif, .ppsx, .xlsb, .gpg, .ppt, .xlsm, .gz, .pptm, .xlsx, .h, .pptx, .xlt, .hwp, .ps1, .xltm, .ibd, .psd, .xltx, .iso, .pst, .xlw, .jar, .rar, .zip, .java .raw.
All found files WannaCrypt encrypts and renames, adding the extension .WNCRY to the file name . For example, the file picture.jpg the blackmailer component will encrypt and rename to picture.jpg.WNCRY .
Also in each folder with encrypted files, he creates the file @ Please_Read_Me @ .txt . The latter contains the same ransom demand message that is present on the replaced desktop wallpaper (see screen shot below).
After the encryption is complete, WannaCrypt deletes the shadow copies of the volume with the following command:
cmd.exe / c vssadmin delete & bcdedit / set {default} bootstatuspolicy ignoreallfailures & bcdedit / set {default} recoveryenabled no & wbadmin delete catalog -quiet
After that, the desktop background is replaced by an image with the following message:

It also runs an executable component that displays a buyback requirement of $ 300 in bitcoins, as well as a timer:

The text is localized into the following languages: Bulgarian, Chinese (Simplified and Traditional), Croatian, Czech, Danish, English, Filipino, Finnish, French, German, Greek, Indonesian, Italian, Japanese, Korean, Latvian, Norwegian, Polish, Portuguese, Romanian, Russian, Slovak, Spanish, Swedish, Turkish and Vietnamese.
The blackmailer component also demonstrates the ability to decrypt encrypted files, allowing the user to decrypt a few random files for free. After that, he quickly recalls the need to pay the ransom in order to decrypt the remaining files.

Ability to spread
The worm attempts to infect non-updated Windows-based machines on the local network. At the same time, it performs a massive scan of Internet IP addresses to find and infect other vulnerable computers. This creates a large amount of SMB traffic from the infected host, as security specialists can notice, as shown below.

The Internet scanning procedure generates random octets collected into IPv4 addresses. After this, the malware attacks a computer located at an available IP address, trying to exploit the CVE-2017-0145 vulnerability. The program does not infect computers that have the first octet of an IPv4 address equal to 127 or more than 224, in order not to waste time accessing the local loopback addresses. Once a vulnerable machine has been detected and infected, it becomes the next source of infection for other machines. The infection cycle continues as unprotected computers are detected.
After successfully infecting a vulnerable computer, the malware executes shell-level code at the kernel level, which seems to be copied from an open Trojan using the DOUBLEPULSAR backdoor, but with certain changes to reset and execute the blackmailer component dumper for 32 and 64-bit systems.


WannaCrypt attack protection
To get the most advanced protection from Microsoft, upgrade your system to Windows 10 . Keeping your computer up to date allows you to take advantage of the latest features and active protection mechanisms present in the latest versions of Windows.
We recommend that customers who have not yet installed security update MS17-010 do this as quickly as possible. If you are currently unable to install this update, we recommend two possible solutions that will reduce the scale of infection:
- Disable SMBv1 by following the instructions in Microsoft Knowledge Base Article 2696547 and earlier recommendations.
- Examine the possibility of adding a rule to a firewall or router that blocks incoming SMB traffic through port 445.
Windows Defender Anti-Virus (Windows Defender) identifies this threat as Ransom: Win32 / WannaCrypt , starting with update 1.243.297.0. Windows Defender Antivirus uses cloud-based protection that protects against the latest threats.
At enterprises, it is recommended to use Device Guard to block devices and ensure kernel security based on virtualization, which ensures that only trusted applications run and effectively prevents the execution of malicious software.
Use Advanced Threat Protection Office 365 protection , which has a machine learning function that blocks dangerous attachments in email messages, for example, containing blackmailers.
Monitor network performance using Advanced Threat Protection (ATP) in Windows Defender , which notifies information security personnel of suspicious activities. Download this brochure to find out how ATP in Windows Defender helps you find, investigate, and eliminate blackmailers from the network. Windows Defender Advanced Threat Protection - Ransomware response playbook .
Resources
- Download security updates for English-speaking systems: Windows Server 2003 SP2 x64 , Windows Server 2003 SP2 x86 , Windows XP SP2 x64 , Windows XP SP3 x86 , Windows XP Embedded SP3 x86 , Windows 8 x86 , Windows 8 x64 .
- Download security updates for localized systems: Windows Server 2003 SP2 x64 , Windows Server 2003 SP2 x86 , Windows XP SP2 x64 , Windows XP SP3 x86 , Windows XP Embedded SP3 x86 , Windows 8 x86 , Windows 8 x64 .
- Security Update MS17-010: https://technet.microsoft.com/en-us/library/security/ms17-010.aspx .
- Recommendations for customers about the behavior when a WannaCrypt attack is detected: https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/ .
- General information about blackmailers: https://www.microsoft.com/en-us/security/portal/mmpc/shared/ransomware.aspx .
Signs of invasion
The SHA1 code of the analyzed examples:
- 51e4307093f8ca8854359c0ac882ddca427a813c
- e889544aff85ffaf8b0d0da705105dee7c97fe26
Files created by the blackmailer:
- % SystemRoot% \ mssecsvc.exe
- % SystemRoot% \ tasksche.exe
- % SystemRoot% \ qeriuwjhrf
- b.wnry
- c.wnry
- f.wnry
- r.wnry
- s.wnry
- t.wnry
- u.wnry
- taskdl.exe
- taskse.exe
- 00000000.eky
- 00000000.res
- 00000000.pky
- @ WanaDecryptor @ .exe
- @ Please_Read_Me @ .txt
- m.vbs
- @ WanaDecryptor @ .exe.lnk
- @ WanaDecryptor @ .bmp
- 274901494632976.bat
- taskdl.exe
- Taskse.exe
- Files with the “.wnry” extension
- Files with “.WNCRY” extension
Registry keys created by the blackmailer:
- HKLM \ SOFTWARE \ WanaCrypt0r \ wd
If you see an inaccuracy of the translation, please report this to private messages.
Source: https://habr.com/ru/post/328910/
All Articles