Attack of the WannaCry cipher family: analysis of the situation and readiness for the next attacks

The situation with the attack of the encryptor WannaCry shook the whole world: from information security experts to the leaders of a number of large countries. And although we hear that there was no significant damage, yet this attack raises many questions. How is the situation developing? What consequences? What to prepare for? We present the current technical analysis of experts PandaLabs.
What happened
Last Friday, May 12th, an encoder, known as WannaCry, spread throughout the world. Currently, there are still a lot of unanswered questions, but at least now information security experts have answers to the question of how this attack works and spreads.
')
The PandaLabs anti-virus laboratory of Panda Security recorded the first samples that were used in this attack on the morning of May 12th. After that, our experts keep their finger on the pulse. Below we provide a preliminary analysis of this large-scale cyber attack. This cryptographer was designed to encrypt all the files that it finds on the victim’s hard disk, demanding a ransom for their decryption.
After a preliminary analysis, we can confirm that the attack was launched on May 12 using more than 700 different malicious programs to encrypt files with various extensions.
This version of the malware contains code designed to exploit a vulnerability known as ETERNALBLUE, for which on March 14 Microsoft released the corresponding patch described in security bulletin MS17-010.
WannaCry scans both the internal and external networks of the affected companies, connecting to port 445 (SMB) and searching for computers on which the above patch is not installed, in order to infect them (like a computer worm). For this, he uses the DOUBLEPULSAR version of the backdoor.
At the time of the preliminary analysis, each computer was attacked using the ETERNALBLUE exploit, i.e. infection was carried out from another computer on the same network. At that time, not a single email was found associated with this attack, and so for the time being it cannot be assumed that it was carried out using a massive spam campaign.
What makes WannaCry different from other attacks that we saw earlier?
Use of vulnerability. In this case, the penetration of a threat into the system does not require human intervention: for example, opening a letter or downloading a file from the Internet.
This method has opened the following features:
• The attack occurred almost simultaneously on the entire planet and without user intervention. Those. massive attack without human obstacles.
• All connected Windows devices that were located on the same network as the initially infected computer and did not install the corresponding patch suffered from the infection. Infection of one computer could result in the compromise of the entire corporate network.
Traditional security solutions designed to stop malicious files are generally not able to block attacks that take advantage of this and other vulnerabilities to penetrate a computer and the network. The consequence of this was that the cyber-attack hit hundreds of thousands of users in 150 countries of the world (mainly companies and public organizations).
Below is a brief information about the anatomy of this attack.
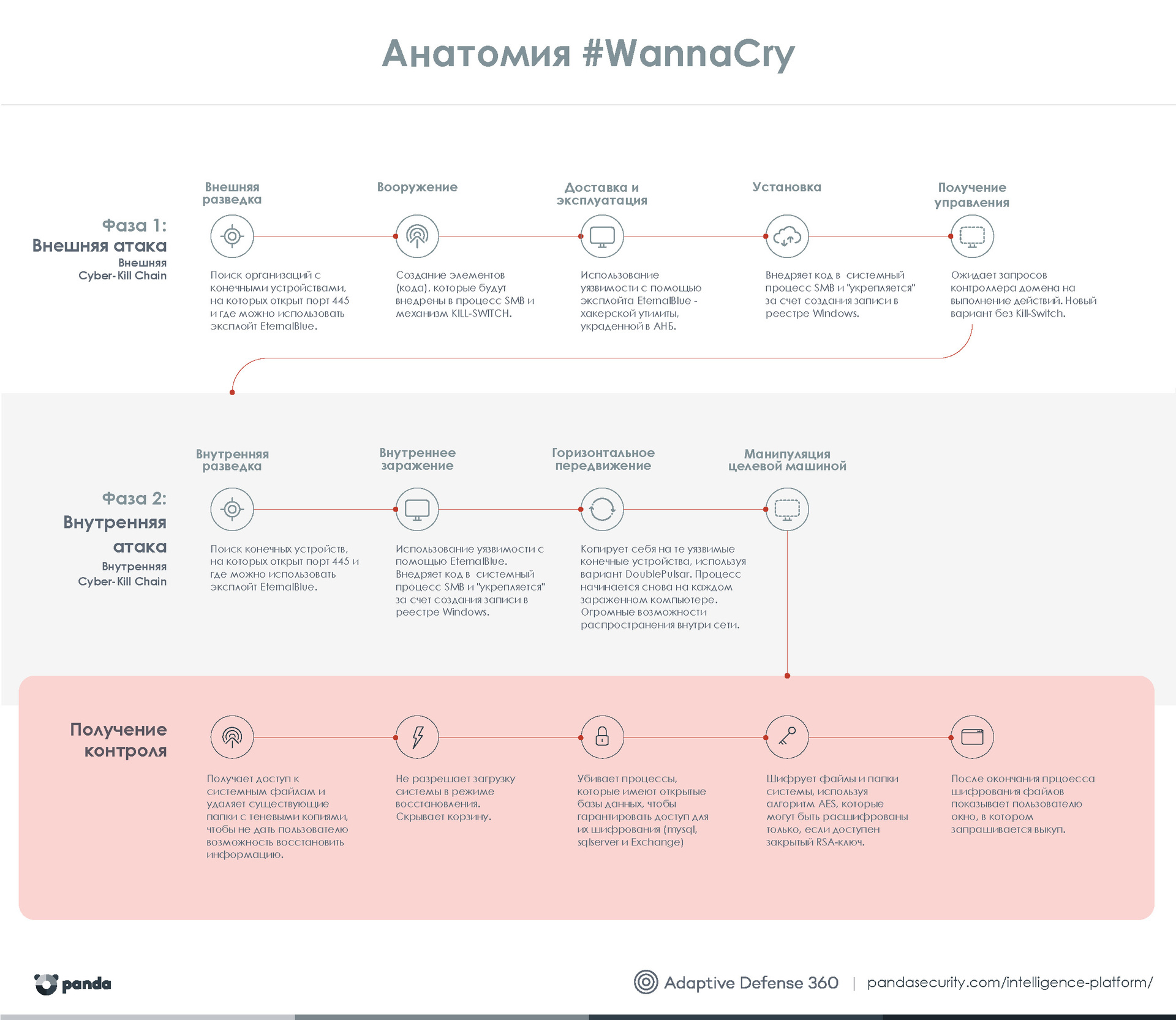
This infographic can be downloaded from the link .
Attack characteristics
The main components of the attack:
• File with hash DB349B97C37D22F5EA1D1841E3C89EB4. It has network worm functionality and uses the ETERNALBLUE vulnerability for Windows.
• File with hash 84c82835a5d21bbcf75a61706d8ab549. This file is designed to encrypt user files.

Below are some properties of the network worm:

The analyzed malicious code does not use obfuscation algorithms, does not implement virtual machine detection techniques, etc.
Below we list the sections that it contains:
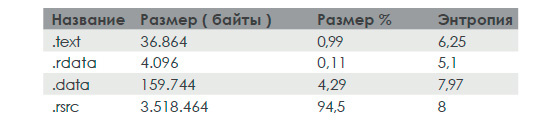
And its resources:

Below is a list of properties of a PE file found in the resources of the analyzed sample:

The second file is a password-protected self-extracting ZIP archive (password: “WNcry @ 2ol7”) containing the following elements:

The “msg” folder in this zip file contains a set of files. These files contain text strings in various languages for the user interface used for the redemption request:

Attack description
Directions of infection
At the time of the preliminary analysis, all the analyzed cases showed the following behavior: the malicious code is run onto the victim’s computers remotely using the ETERNALBLUE exploit and modification of the DOUBLEPULSAR backdoor. Thus, WannaCry manages to inject code into the LSASS operating system process. ETERNALBLUE takes full advantage of the SMB vulnerability identified in Microsoft Security Bulletin MS17-010 for distribution on the internal network by connecting to TCP port 445 of those systems on which the corresponding patch was not installed.
Interactions with a vulnerable system
The first component launched is a network worm that attempts to connect to the following URL: www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
If the domain is active, the worm takes no further action and stops the launch.

However, if he cannot establish a connection, then he continues to run, registers himself as a service on the victim’s computer and starts the service.

Service Description:

In addition to installing itself as a service, WannaCry retrieves the “R” resource corresponding to the executable PE file of this cryptographer, which encrypts user data (MD5: 84c82835a5d21bbcf75a61706d8ab549), and copies it to “C: \ WINDOWS \ taskche.exe”.
Then it launches it with the following parameters:
command line - C: \ WINDOWS \ tasksche.exe / i
NOTE: If the file "C: \ WINDOWS \ taskche.exe" exists, then it transfers it to C: \ WINDOWS \ qeriuwjhrf. Perhaps this is done in order to maintain multiple infections and avoid problems when creating "taskche.exe".
Finally, using the following command, it creates an entry in the Windows registry, as a result of which the cryptographer will be launched each time the computer restarts:
reg.exe reg add HKCU \ SOFTWARE \ Microsoft \ Windows \ CurrentVersion \ Run / v “mzaiifkxcyb819” / t REG_ SZ / d “\” C: \ WINDOWS \ tasksche.exe \ ”/ f
NOTE: The name of the value is randomly generated.
After the encryption component has started (tasksche.exe), it copies itself to a new folder with a randomly generated name located in the COMMON_APPDATA folder on the infected computer. Then he tries to add himself to autorun:
reg.exe add HKCU \ SOFTWARE \ Microsoft \ Windows \ CurrentVersion \ Run / v “RANDOM_CHARS” / t REG_SZ / d '\' C: \ ProgramData \ FOLDER \ tasksche.exe \ '' / f
The cryptographer then takes the following actions:
1. Uses the Windows “icacls” command to get full access to all the victim’s system files:
• icacls. / grant Everyone: F / T / C / Q
2. Deletes all backups (shadow copies) found in the system in the following two ways:
• vssadmin.exe vssadmin delete shadows / all / quiet
• WMIC.exe wmic shadowcopy delete
3. Prevents the computer from booting in safe mode:
• bcdedit.exe bcdedit / set {default} bootstatuspolicy ignoreallfailures
• bcdedit.exe bcdedit / set {default} recoveryenabled no
4. Removes all backup directories:
• wbadmin.exe wbadmin delete catalog –quiet
5. Creates an entry in the Windows registry, pointing to the folder containing the cryptographer:
• [HKEY_CURRENT_USER \ Software \ WanaCrypt0r]
6. Hides the recycle bin using the ATTRIB command:
• attrib + h + sc: \ $ RECYCLE
7. Using the echo cmd command, he creates a VBS script to generate a .lnk file pointing to the file decryptor:
SET ow = WScript.CreateObject (“WScript.Shell”)
SET om = ow.CreateShortcut (“C: \ @ WanaDecryptor @ .exe.lnk”)
om.TargetPath = “C: \ @ WanaDecryptor @ .exe”
om.Save
8. Finally, WannaCry tries to kill various database processes in order to be able to access the database files and encrypt them:
'taskkill.exe / f / im mysqld.exe'
'taskkill.exe / f / im sqlwriter.exe'
'taskkill.exe / f / im sqlserver.exe'
'taskkill.exe / f / im MSExchange *'
'taskkill.exe / f / im Microsoft.Exchange. *'
Distribution process
This malware has the capabilities of a worm, meaning that it is trying to spread across the network. To do this, it uses the EternalBlue (MS17-010) vulnerability to spread to all computers where this vulnerability is not closed.
It is worth noting that the worm not only searches for computers on the same local network where the infected computer is located, but it also scans the public IP addresses on the Internet.
All these actions are performed by the service that the malware installs after its launch (see the application “Presence in the system” for more information about the name of the service).
After the service has been installed and started, WannaCry creates two threads to distribute itself to other systems.
The function that runs these two threads:

First, the function tries to get the DLL that WannaCry will use to create the “payload” sent to infected computers. The malware is added to this library.
This DLL contains a function called “PlayGame” that extracts and runs the resource included in the DLL (malware). Those. The call to the “PlayGame” function is what initiates the infection of the computer.
This DLL does not "touch" the hard disk, because there is a direct integration into the process of the LSASS operating system after using the EternalBlue exploit on the compromised computer.
Distribution on the internal network
Below you can see the function used to distribute WannaCry inside the local network where the infected computer is located:

The task of this function is to collect information about the local network adapter and create an internal IP address to launch a stream that will launch an exploit and embed the required code / object into the process of the LSASS operating system.
Internet distribution
The function used to distribute WannaCry on the Internet generates random ranges of IP addresses:
Then, after it has generated IP addresses, it launches an exploit with the following code:

As you can see, when WannaCry tries to spread on the internal network or on the Internet, it calls the RUN_ETERNAL_BLUE function, whose “job” is to spread the exploit.
EternalBlue exploit
As mentioned earlier, this malicious program uses this exploit for distribution. During the analysis, we observed how he uses exactly the same code that was used by the NSA in his “implants”.
The only difference is that he doesn't need to use DoublePulsar, because its goal is to simply inject itself into the LSASS process. The code of EternalBlue payload remains unchanged:

Compared to previous analyzes, you can see that the code is identical. It makes exactly the same function requests to inject the DLL sent to the LSASS process and execute the “PlayGame” function, from which the infection process is restarted from the already infected computer to attack other computers on the network.
Since kernel-level exploit is used (ring0), then all operations performed by malware have SYSTEM rights.
Computer encryption process
Before encrypting a computer, the cryptographer checks for three mutexes (see below). If any of them is present in the system, the malware will not encrypt the data:
"Global \ MsWinZonesCacheCounterMutexA"
"Global \ MsWinZonesCacheCounterMutexW"
"MsWinZonesCacheCounterMutexA"
It is important to emphasize that if the "MsWinZonesCacheCounterMutexA" mutex is present, then when the encryption component is started, it is closed automatically and no further actions will be performed.
The cipher randomly generates a unique key for each encrypted file. This 128-bit key, created using the AES encryption algorithm, is encrypted using a public RSA key in a user header that the malware adds to all encrypted files.
Files can only be decrypted using the RSA public key corresponding to the public key used to encrypt the AES key used in the file.
A random AES key is generated using the CryptGenRandom Windows function, which does not have a known vulnerability, and therefore it is currently impossible to develop a tool to decrypt these files without knowing the private RSA key used for the attack.
The cipher creates several streams and performs the following actions to encrypt files:
1. It reads the original file and copies it, adding the extension .wnryt
2. It creates a random 128-bit AES key
3. It encrypts the copied file using AES encryption.
4. It adds a header with an AES key encrypted with a public RSA key created by the malware.
5. It overwrites the original file with the encrypted file.
6. It deletes the file with the .wnryt extension
7. Finally, it renames the original file with the .wnry extension.
For each folder whose contents are encrypted by the encoder, it generates two identical files:
@ Please_Read_Me @ .txt
@ WanaDecryptor @ .exe
Recommendations
1. Appropriate patches should be applied on vulnerable computers to prevent exploitation of the SMB vulnerability. Make sure the patch is technet.microsoft.com/en-us/library/security/ms17-010 . aspx is used on all systems in your network to close the “door” for the type of exploit to be performed.
2. Block incoming connections to SMB ports (139, 445) from computers outside your network.
3. Microsoft has expanded the list of vulnerable systems for which the security patch is available:
• Windows XP
• Windows 2003
• Microsoft Windows Vista SP2
• Windows Server 2008 SP2 and R2 SP1
• Windows 7
• Windows 8.1
• Windows RT 8.1
• Windows Server 2012 and R2
• Windows 10
• Windows Server 2016
4. Finally, perform an internal audit of your network to find out where the attack started, to secure this and other threat entry points.
Considering the massive spread of the attack and trying to help as many users as possible, Panda Security experts developed the Panda WannaCry fix tool for users of other anti-viruses (not Panda). Read more here: www.pandasecurity.com/russia/support/card?id=1689
Additional Information
Hashes associated with the attack files
C4AD13742EEA06B83CDD327D456475F3 1008DC20ECD2FD51594E5822A4C48B27 25ED37A6EAE58E6BE0E5BE25E08391AD 1B3F45FDB84F5D28B115E46432B51445 ADF84F1DAE003B6A6AD06A7E0A0DE4C2 4BEE4C92CF8C724C3F8D620C596BEF0E 8182D9CEE031492868AA14AD4C544871 1176B58D48FA14BA51CC355F0D97E9EE E63AC863C125491FD7F0156690A5AD49 1244A500A542A4D711BEC19E256D3EA4 85C8AA082AF064C2E6B4AA05C3E4198C 5C3678CA08BFAE4FA111353FDAF1A908 A6E1CE9E133D986123482294AD45D688 A14392CDC6A32BAEEB7EC676E31F4DDA BC409BFD2B92E13B4A5C53CD38193E25 D101458BF12DC1B6563FA702F9856305 C8EE875F395D17175BA9534318F273AA 9524E8A3BB88438878C9691EA0F038B3 739B09535819998ED8BAA13B18759901 508EEA03857853D18EBD1CD56D6039EC 3F03A2A13B77689401769C129468A51D E511BAB670117D4B07FDBEAF8E499A0C C54C1B75241FC76D13A7C3407FD70E8B 9507F6C5D7575F08FFFC14AD82B823C5 1AD05EF49CC178A9D68CCA76411FBC63 3E17CA056714EEC628960DBB091EEACC 3ED057DCD93ACD9CBAE9B72AA2B69866 121BDE34CE23204F92CA1D86A830F897 7EEF74D99C3D42D3EC5B1C87F247981D BD8831FF2B1DE20CC89723CD2FFA1D4C 72CCC5112B 3B67F457089D9EA4AE6BEF CFFFFB5125D7DB2CB8571147D9D93967 72E39278D10C996C4F34FD01299151C1 1A784CF720AC28F68CBCDBE10144D382 3AFD873F976CCB46182B09FCE86128A2 F54FB8F54CEA92245162E3E359A122DE 6E3579165B8C1A2196D8B11997E6F430 BCA0EA97155B22D383E80F506E6DD662 723510BBFA3982F71D970B04783988BF 67CA5FA76CE212FE63B025953C3AA383 27931061EA3A9C0A4137B25BA8853E55 841595FC3743045CE1921016306AD46E F8FAF81876B00F5F906D99A73074F826 302123DDEE17B94467CA3DE7A180E27B A04C0BBF1E5C6C0AD79F25231500C470 E46CC7704649BEE3CF62DC7C8EEF92BC 45E1FA3B575919E2C891B91FFDAF293E 3A41839339DFF5F6DB6D97DC850FD7E6 42181CCD6CECE831758A2E41C82329EB 6AA8B6808355ACF28A7D9F023A22CB2F 77CE115A9CB11089AF058BEE1F249655 26CBA3DF81431C1DE14747259219E5E7 090115FB44E59F734274C005671835E4 8E17CCA4BD754D3E333748F3057FF48B D61AABE3D8F709AA19A7081661F7AB6D 042220A9F37E19C2D07C20D5C6556DA6 9A2459972439543FA562601E23DF4226 D0BA545DF0B96E8295F3A5362BD76A80 54CB648CBD354E727A10065DC4A3641E 358AB4719E7AF138B5F1903CDE037EB8 CFE05085B6EA60A50AC3 0E6E8C97547B 567D28DE2129DC8E1BBCDF37C11BD2A3 FEE22D2F867F539B080671234199AD90 33EBBE044B20EE3DE811A070DB37A207 A14ADEEBDD0C974A890E0119804AAA97 3F87EC08F9F8D7F752ABB83BA4D09C1B 2983BB57017272DEC91A41762B7718AC F54F2CDCF85B139638BCE882FF486E75 986FF9951F3B43C8275292AD72725E4E E52FEFDEDB065D747434C1A307EDBDA1 EC03F1D8DBF07D84E5469D5F2D1C2F71 B7909213A5E526146824D702E013EC63 E69471734BB6C68ED59EFB7F9F324391 503B4D9DB3040AF8618E0308C19953F3 30B506A13C6A20CD80D887FE2DEE3BC9 1D548EAE15B8BC050FFD41914CBA1A65 AA2748A8633FC2AB910DF4B90EA1B3DB 14485A33FD7F9EB90E34C3AF50F69540 3B1444B3377FFBECB460B1256FEA212D 84BD2553AC818F1790E6D043FC3FA239 F729666F1B67490F48AA26DA129CD78A 3C6375F586A49FC12A4DE9328174F0C1 095F70BC99454E79FB20F1042074EB9D F93ED60FB05E855118B68CDB8D7BB182 5E68461D01FE4F3D8A335C725E3C7B6F A084316EFB8543C95769CA892AEE9562 29F1E0C25F06890A25C0F478FDD2CB00 9010C6FC28BBB2AE9188228691B7C973 5FA3051376E790EA5E13342231E66DEC 1805FFE69FDC338CF7EB061A74537261 802D2274F695D3F9B864FF395E9F05 83 DFADA7FBC9156FCBBD4A03881E660D6D 9853288BBDA0FAEAF26D845E7EB6D289 37096BAA79383FAF1456507FA963C41A 2ACEA7F2CC0D7F69552878B3D12385AF B83EC73C4DCF0BE87711C59415472D13 EADDFE3E397BC61DB749B074FF5242D5 9D678C01B1F944DC9AC46AC0CFA63951 E8C8E5A66CA3CD513668D1A748823F2C 737367791A1F09C94DED82652E77C442 78F8620D07B03F4E6DB9FBF0D019B95F 1C0BD8834194C915762F16D93F5CCC37 F943B62F468A4A0B0A6E6C15061C1945 66A233C9214D3D176A76F62456BBA85E E274AC7A8C36654F094AC63047F7BEAB 493BFC730E9C86DFEB7861A5C5AA21FC F359D6A61E76D01AC0B6302E789FEFF7 1B9C23AFB77D4B57523D5310F01F3F8B FA0FDFE9AFD72E9AE09F9E0B75F8B13B 80A2AF99FD990567869E9CF4039EDF73 F039E896AD0D438F7D24C34C1F61E4B9 D1A407CE2398A599842F7E1AAEAD13A0 76EFB0E9E4847B93C0486AA5CDFDE3D7 3F7B2CF5963737C5BCC5E2892023BF52 0032ED755A83D3969714D6FABFF5D15E 9DFAF183DBB86BC429847E1D7870ADB9 E96FA4F9C77D188859346FAD8E2BB465 8DF73CCF4907B07AED96984D87958246 DC77333B3B24A53FC975D1F4127A2348 16599AB60799BD3A1CDD4693E64AD142 FDC004BEF582D9E167F093EC1B768952 7CD4CC8 2923BB8E0D27372772441F3CA 770FCA32AF3D25039F2E7A75AA2AC941 49308A8F3D5D1780E52815D4217B57E2 FACBEC0F9C72DA2BAD41A82554A7662F E9F7182311359587468700C56B8F4DAD 466CC6A5DEBF64A0CF90980916C2FA9F 532DF50DEDDC8A9B82F30E6059E34C80 FE9C079C1BB4520A90133138F2C061D6 AC434FEED7AC7E2FACCF9E66ACE99787 9CFF2C57624361A0F0840C7624F94666 C9A0882DE8189DC9B8272C36C5590EA7 92CC807FA1FF0936EF7BCD59C76B123B E6243D51E1534002755BA10C361B1DB3 5AB99FF7DE746BCC9B13D13ABF1F61D9 D98C575B632B9AA5BF35FC36EB8BACF3 5ADF1FC8616233EB8BCACD126841A5E8 EB87BBB7E22FF067D303B745599FB4B7 638A6E2B85E11873F573EF9D0AA8ED1A DE69AB7D058BD7BA4243C130AA549848 3C21810E3820AD2D3749BB2C5342669E C8C046A3C5633AE6F60F876B3EA74DE6 07D2FA1FC19396A14A235536EE3BBA16 27C9E96211FB77ED73FA24B290F8EEDC 5AFC535A9980BD8DD110F09199E8E117 E19E0CFC694635856245CA8E1FE336C1 8C6713681FFB5FBB83FF9353D89DF48D 623AFE21D3470FD52861D4F2A0865C28 27F2D7C5F217FD61F8B455DE8B1F6157 845FCF3E7EAB17A1B63832C187BC5142 DD0925A4D16CD673AA06E3B15F8136CC 9EBF1A2A96A1F13DC 62A6B6ACB5FD3B8 46D140A0EB13582852B5F778BB20CF0E 03601EBAB06ADCC05545AAF3CE59601D C4ADA07E9F750A2F9E3B5A592C3E8C4E A7C448789FEFCD319352B414CE0FA3BF 6381B98EF2C1C7F1E1678F178274E87A A8365EF51AA4158197204A914BF2045F 9C4301C9E49E9B767B2DAEFCF2E28134 8965AE4D1E2ECE0E0BF452CE558F8812 D7CF8AE014540314A92281B0E92D7FA6 1B94CD23AE55C020B9DF900E5896DA8C C1426666EB3D9330E1820B3494451D9B 653999EDCDE5D55BC03C135A44B514FD DF42E1E035F656FBDA255708DCEB51E2 D4AE7DE6B8345C4024D762A2D5BAF7A3 3885029409955C34AE9D176C447EBC93 903D26CA69E2717B1440E0E498543FC7 47EC325CE31E197538632F35303CF654 458425117EC0EC9306146E5058859C78 B67B7879F4C66D8F908A1AE26C46620F 0F417FDFD64E0EC7EFCC13616FEC93CD 38554E7D5807C0653D5B1AD8AD245C2 AA1F73335722C85F85EE5B2E3BFF1406 D759469E07466288E1BE034A5CE2B638 C29D733523CB6CC3FF331021FBE7D554 7F2BC30723E437C150C00538671B3580 3600607AB080736DD31859C02EAFF188 4BB0DB7B5DEA5A5F7215CABE8F7155AF C69EE6BDAF30ED9EDC37D2274AD5F5D1 C39F774F7B4257F0EC3A7329063FC39C 27CB59DB5793FEBD7D20748FD2F5 89B2 79E5A2B3F31F8541EB38DAE80C4A34C8 4B700C7A304A9E8D2CB63687FE5D2415 B4D42CF15E9ACD6E9DEE71F236EF0DEC 37EB07CF2FD3CFC16B87624565796529 C27AC2A321145CC8EA1A97F0A329D139 1A68EFEDA07AD2F449E844D4E3383B85 D27B7EDCD6FE5D6C55CF1AA09AB87C8B A70B7A60F9C13A3306FB3E54229862A1 6D26E44407A6CBB6C63AFE4914EFD135 F94429CC043169462D34EDD14117DDD2 7660AB72BCD3CBCC4E9ADFB84F7BAEAA D46D2C27A42DC41564283E74FC7DC43D 36F5B8EF2561A02B89CE62DE705458DD 9929D18280A6309C3FC1A175E73EAF79 F107A717F76F4F910AE9CB4DC5290594 31DAB68B11824153B4C975399DF0354F A05DAF549FEEE576BB4586D37BFA7F23 8621727CDE2817D62209726034ABD9D3 13D702666BB8EADCD60D0C3940C39228 CD7A1B9D4B0FB02489102305A944D0B9 580AAF34E9E37A64CF4313A20EAB6380 E9CFA94806D89999FFFE5B1583B13DBE 7E587A620BDBCD29B3FC20C5E0A5F2D8 1358D78A5427E04F3CFC8FFF9E4F8C32 638F9235D038A0A001D5EA7F5C5DC4AE 7D31ADCA26C6C830F6EA78ED68DE166B A7D730D66AC8154D503AF560EBB043CB 9F38D2F801D57DBF714B60B55170DE0C 0D859C69106E05931BEB5FC2B4AD4DB3 BEE302BE6278964A8CB653BC7FCE5530 DB349 B97C37D22F5EA1D1841E3C89EB4 246C2781B88F58BC6B0DA24EC71DD028 181C3455DD325A2A6ECD971278B7D41C 932D593C0DCE308F2C496F8318BFA4A9 7B968EBEA8D77C59AA553100D04CD8B4 882D70B718FB0640FD8C57028EE34A18 89347BA13DAB2940C83EA753F89EE3A4 9B97ECB5BA558FD0B64A5461CF75D465 4DF48816B2563928D941B530A4CC090F 93EBEC8B34A4894C34C54CCA5039C089 5D52703011722DFF7A501884FECC0C73 CEBDE4399C4413BC5CC647447093D251 533146828B909C886B3316F4F73067C4 5318B32086E6D33DEFA4295B1DF07D22 2700C59EA6E1A803A835CC8C720C82CA 8FF9C908DEA430CE349CC922CEE3B7DC 05C37CC103AFB24036D75F87A021BECB 54A116FF80DF6E6031059FC3036464DF B8A7B71BFBDE9901D20AB179E4DEAD58 2D1E3A2DF4F147F025C7349926EE88B0 91EBCD98CCF513572467244221455851 1894418EC97703F5E52D9EE132FC3A90 5BEF35496FCBDBE841C82F4D1AB8B7C2 44EC4895F054266A22FA40364C46ECBD BEC0B7AFF4B107EDD5B9276721137651 1CFE70E37DFD11D68A0F558E687BE77F E16B903789E41697ECAB21BA6E14FA2B BE73E513A5D647269551B4850F0C74B8 2E8847A115AC0B9D49F5481E773CAD3D 0156EDF6D8D35DEF2BF71F4D91A7DD22 975D2600C0AD9FF 21DFBFE09C831843A 100A94944C3009877B73F19FCD4D5280 9503AF3B691E22149817EDB246EA7791 FF81D72A277FF5A3D2E5A4777EB28B7B 05A00C320754934782EC5DEC1D5C0476 92F88C128B460489D98672307D01CEA7 C39ED6F52AAA31AE0301C591802DA24B 269E032DEA2A1C6B7841BDFE5F54F26B 3D072024C6A63C2BEFAAA965A610C6DF 5B2B45A2BC04B92DDAFC5C12F3C8CFA6 57AAA19F66B1EAB6BEA9891213AE9CF1
List of command centers
gx7ekbenv2riucmf.onion
57g7spgrzlojinas.onion
xxlvbrloxvriy2c5.onion
76jdd2ir2embyv47.onion
cwwnhwhlz52maqm7.onion
List of Bitcoin Wallets
blockchain.info/address/12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw
blockchain.info/address/115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
blockchain.info/es/address/1BANTZQqhs6HtMXSZyE2uzud5TJQMDEK3m
blockchain.info/address/13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94
Command Line Command List
C: \ WINDOWS \ mssecsvc.exe
C: \ WINDOWS \ mssecsvc.exe -m security
C: \ WINDOWS \ tasksche.exe / i
cmd.exe / c “C: \ ProgramData \ dqzdvrnqkzci137 \ tasksche.exe” C: \ ProgramData \ dqzdvrnqkzci137 \ tasksche.exe
@ WanaDecryptor @ .exe fi
list of files
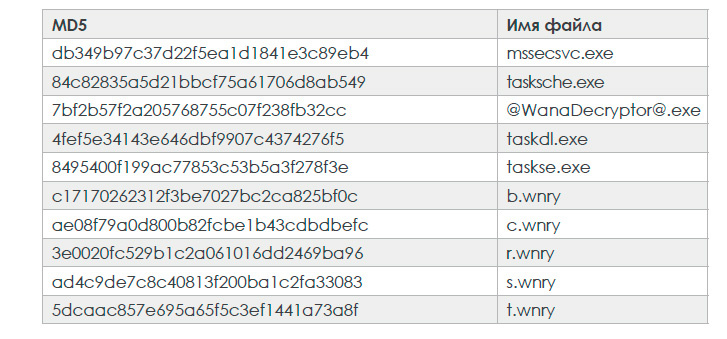
Survival assurance
Service:
• Name: mssecsvc2.0
• Description: “Microsoft Security Center (2.0) Service”
Created registry key (autostart):
HKLM \ SOFTWARE \ Microsoft \ Windows \ CurrentVersion \ Run \ obsbeuqp
321 C: \ WINDOWS \ system32 \ tasksche.exe \ ”” / f
Mutexes created during encryption
'Global \ MsWinZonesCacheCounterMutexA'
'Global \ MsWinZonesCacheCounterMutexW'
File extensions encrypted by the sample being analyzed
“.Doc” “.docx” “.xls” “.xlsx” “.ppt” “.pptx” “.pst” “.ost” “.msg” “.eml” “.vsd” “.vsdx” “. txt ”“ .csv ”“ .rtf ”“ .123 ”“ .wks ”“ .wk1 ”“ .pdf ”“ .dwg ”“ .onetoc2 ”“ .snt ”“ .jpeg ”“ .jpg ”“ .docb ” “.Docm” “.dot” “.dotm” “.dotx” “.xlsm” “.xlsb” “.xlw” “.xlt” “.xlm” “.xlc” “.xltx” “.xltm” “. pptm ”“ .pot ”“ .pps ”“ .ppsm ”“ .ppsx ”“ .ppam ”“ .potx ”“ .potm ”“ .edb ”“ .hwp ”“ .602 ”“ .sxi ”“ .sti ” “.Sldx” “.sldm” “.sldm” “.vdi” “.vmdk” “.vmx” “.gpg” “.aes” “.ARC” “.PAQ” “.bz2” “.tbk” “. bak ”“ .tar ”“ .tgz ”“ .gz ”“ .7z ”“ .rar ”“ .zip ”“ .backup ”“ .iso ”“ .vcd ”“ .bmp ”“ .png ”“ .gif ” “.Raw” “.cgm” “.tif” “.tiff” “.nef” “.psd” “.ai” “.svg” “.djvu” “.m4u” “.m3u” “.mid” “. wma "" .flv ”“ .3g2 ”“ .mkv ”“ .3gp ”“ .mp4 ”“ .mov ”“ .avi ”“ .asf ”“ .mpeg ”“ .vob ”“ .mpg ”“ .wmv ”“ .fla ”“ .Swf ”“ .wav ”“ .mp3 ”“ .sh ”“ .class ”“ .jar ”“ .java ”“ .rb ”“ .asp ”“ .php ”“ .jsp ”“ .brd ”“ .sch ”“ .dch ”“ .dip ”“ .pl ”“ .vb ”“ .vbs ”“ .ps1 ”“ .bat ”“ .cmd ”“ .js ”“ .asm ”“ .h ”“ .pas ”“ .Cpp ”“ .c ”“ .cs ”“ .suo ”“ .sln ”“ .ldf ”“ .mdf ”“ .ibd ”“ .myi ”“ .myd ”“ .frm ”“ .odb ”“ .dbf ”“ .db ”“ .mdb ”“ .accdb ”“ .sql ”“ .sqlitedb ”“ .sqlite3 ”“ .asc ”“ .lay6 ”“ .lay ”“ .mml ”“ .sxm "“ .otg ”“ .Odg ”“ .uop ”“ .std ”“ .sxd ”“ .otp ”“ .odp ”“ .wb2 ”“ .slk ”“ .dif ”“ .stc ”“ .sxc ”“ .ots ”“ .ods ”“ .3dm ”“ .max ”“ .3ds ”“ .uot ”“ .stw ”“ .sxw ”“ .ott ”“ .odt ”“ .pem ”“ .p12 ”“ .csr ”“ .crt "" .Key "" .pfx "" .der
Who is behind the WannaCry attacks?
Information security experts are trying to find out the details and take measures to prevent further spread. Given the scale of the attack, a lot of nuances and unknown moments regarding this threat, we are still far from complete clarity of the picture.
The attack caused many questions and disputes. Why did the NSA not report this critical vulnerability in Microsoft? And anyway, who is behind this attack?
Whoever it is, their methodology refutes the version that behind this attack is a highly professional organization, which employs very talented hackers. Someone is already beginning to point out the involvement of the DPRK in this attack, which is often suspected of many such crimes. Clues that point to attacks against Sony and the Central Bank of Bangladesh, suspected of hackers from the DPRK, reinforce this theory, but it is too early to discuss the potential source of the attack with any certainty.
Anyway, one thing is clear: the danger is still quite serious. The treasure in the form of cool cyber-weapons that was stolen by the NSA and “merged” by a group of hackers calling themselves Shadow Brokers is still relevant for exploitation. In a blog, Microsoft President Brad Smith asked what would happen if a certain amount of tomahawks were stolen from the US military. This is a very apt comparison.US intelligence agencies are investing millions of dollars in cyber-weapons that exploit vulnerabilities in operating systems like Windows, and these types of weapons are in the strictest confidence because they pose a serious danger.
What to do next?
In this regard, it is best to adopt a constructively different approach to traditional security products. If hackers take into account the fact that the anti-virus should not know the malware used to attack, then it is obvious that you just need to use the security model that specializes in controlling everything that is still unknown.
In a number of recent cases investigated by the PandaLabs anti-virus laboratory, we have seen new variants of attacks, among which are those that do not use malware as such, but rather rely on scripts and the use of legitimate tools of the operating system to avoid detection by traditional security solutions. . And this is just an excellent example of how high a level of qualification and professionalism cyber-criminals have achieved in recent months.
Due to the visibility of the unknown threats provided by the Adaptive Defense solution, as well as its unique capabilities to prevent, detect and apply the required measures for an instant reaction to an attack, our users were protected from the very first moment of this attack.
The enhanced protection offered by the Adaptive Defense solution , thanks to a new security model based on continuous monitoring and classification of all active processes, once again using the example of this attack, has shown that it has become one of the few solutions able to withstand this frightening reality.
• Adaptive Defense - enhanced protection against unknown threats to users of other corporate anti-virus solutions with which it is able to work in parallel and without conflicts
• Adaptive Defense 360 - a complete EPP + EDR solution that provides high-performance traditional protection of end devices + enhanced protection against unknown threats
Demo console Adaptive Defense 360
( Chrome Firefox) .
: demologin.pandasecurity.com
: DRUSSIAN_FEDERATION_C14@panda.com
: DRUSSIAN#123
- Adaptive Defense 360
1 .
Panda Security: sales@rus.pandasecurity.com
Source: https://habr.com/ru/post/328882/
All Articles