Cisco Meraki MX: Security Settings on the Perimeter in 4 Clicks
Administrators of small and medium-sized companies often do not use most of the functions of their corporate firewall. According to statistics, the main reasons for this are several. In 25% of cases, the main settings are made, while for others the administrator does not have enough time. Another 34% of cases they did not cope with the settings. And in 41% of cases all the available functions are simply not required by them. From this we can conclude: the security gateway should be chosen only in accordance with its own tasks and capabilities, not focusing on the entire list of functions.
For the requirements of most companies, both small and medium-sized and large, with a geographically distributed infrastructure, the Cisco Meraki MX Security Gateways are perfect. They are easy to set up, do not require the presence of security administrators in remote branches, and at the same time use the same signature sets as the top Cisco Firepower solutions.
Consider a few basic options for using Meraki MX in an organization. They can be configured in just 4 clicks of the mouse on the intuitive Meraki Cloud panel without complicated settings and command line.
One of the most common use cases for a VPN is to connect a remote employee to a corporate network. What allows the user to feel like at work and can easily use corporate services. At the same time, he will not be able to get around just that, what exactly is this user busy with, what data does he transmit and receive.
')
The second, equally common use case is similar to the first, only individual users are connected to the corporate network, but entire offices or buildings. The goal is the same - to safely and securely combine geographically remote elements of one organization into a single network. When creating such connections, you need to take into account a lot of nuances: the authentication method, the encryption protocol, the network and the type of traffic that will use the tunnel and much more.
Meraki MX family devices have the necessary set of tools for creating such VPN tunnels in automatic mode.
1. Select the VPN concentrator mode (Hub mode is selected in the center, so click Spoke).
2. For Spoke, select Split tunneling mode in order to use the VPN tunnel only for traffic to the central office, and issue Internet traffic directly to the light.
3. All subnets have already been calculated, you only need to choose which VPNs can use (specify yes / no opposite).
4. Save. Now the Meraki cloud will automatically coordinate the addressing and parameters of the IPsec AES128 tunnels and distribute the data about the VPN routes on the MX device in the network (Figure 1).
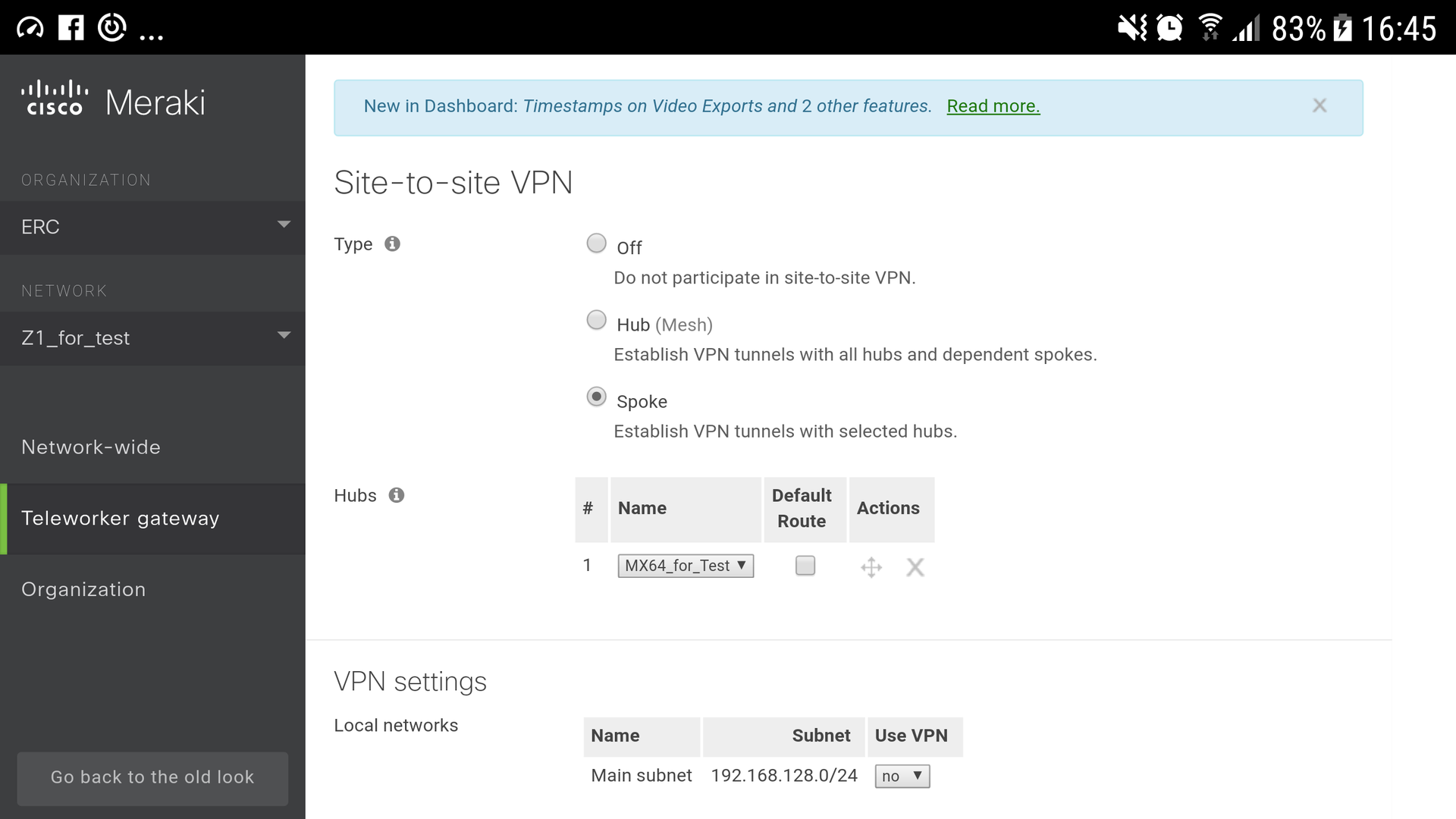
Figure 1
Any network is a target for intrusions and malicious attacks. Such invasions are caused by confidential information leaks, shutdowns of business-critical applications, and even enterprise crashes. Meraki MX is equipped with advanced and customizable tools to counter such threats. IPS tandem on SourceFire Snort, Cisco Advanced Malware Protection and daily signature database updates protect the corporate network from potential risks. A system of retrospective analysis will allow to take measures even in the case of passing 0Day attacks.
1. Enable anti-virus scanning (Malware prevention - enabled).
2. Enable protection against unauthorized access based on SourceFire (Intrusion detection and prevention - select Mode Prevention).
3. Choose from three pre-set IPS rule sets from most loyal to restrictive (Connectivity / Balanced / Security).
4. Save. Now you are protected and can view the analytics (Fig. 2).

Figure 2
Content filtering system provides secure use of the Internet by users within the network. When a user requests a URL, it is checked in several stages and can be blocked for viewing due to the presence of malicious or unwanted content.
1. Select the categories of web sites that need to be blocked (we recommend blocking Adult, Bot Nets, Confirmed SPAM, Illegal, Malware Sites, Phishing, Proxy Avoidance, SPAM URLs, Spyware).
2. Enable search filtering (Web search filtering - enabled).
3. Enable YouTube filtering (YouTube for schools - enabled).
4. Save. Now, the employees of your company (or students of your school) have limited access to sites that cannot be used in the workplace (Fig. 3).
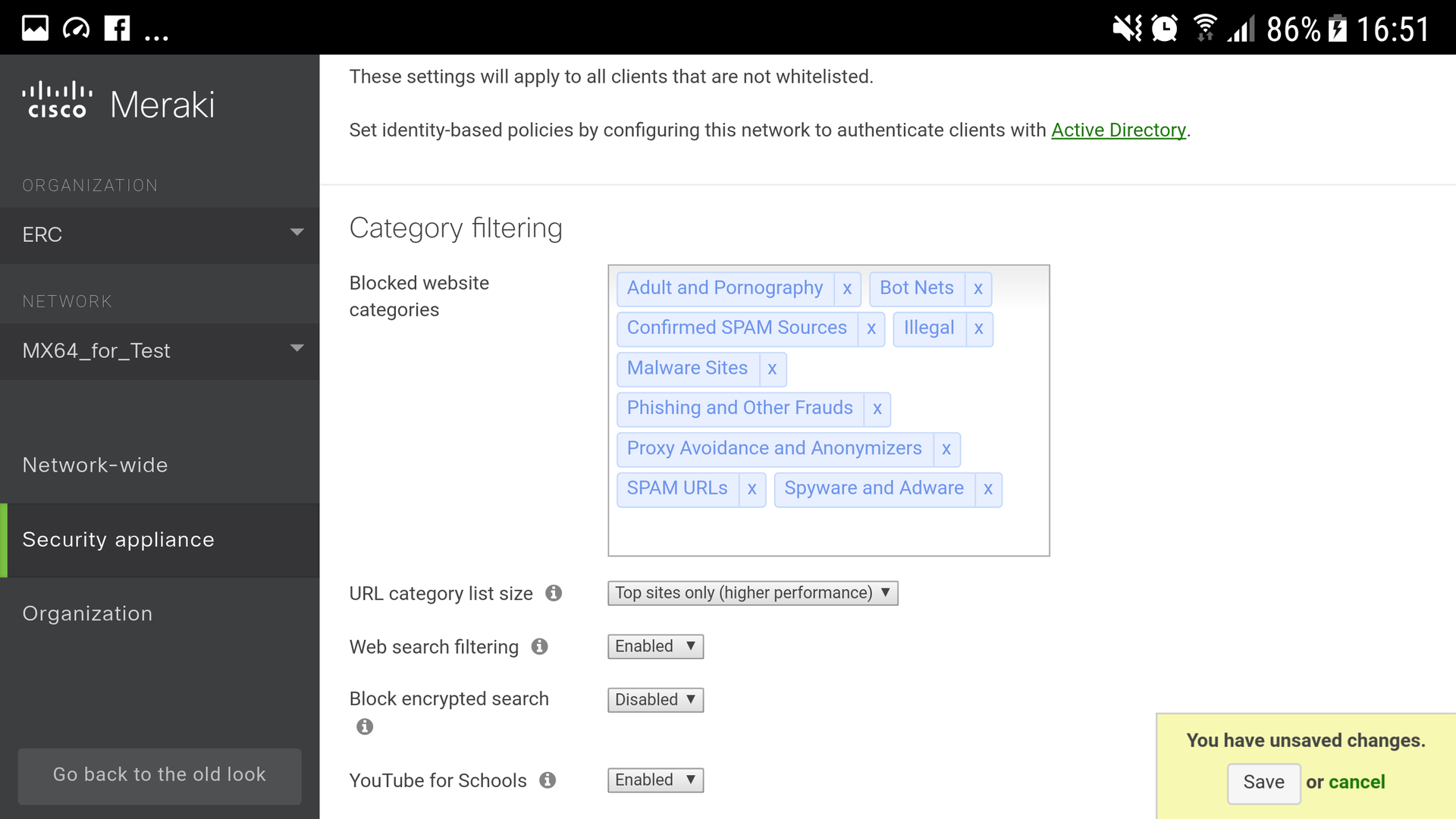
Figure 3
Currently, together with a systematic increase in data transmission speeds in telecommunications, the share of interactive traffic is extremely sensitive to the parameters of the transportation environment. Therefore, the task of ensuring quality of service (Quality of Service - QoS) is becoming increasingly important. We need business critical applications to take precedence over various multimedia applications and not suffer from filling the channel.
1. Select the parameters for the allowable load of input and output traffic for both WAN uplinks (you also have the ability to connect a 3G / 4G modem as an additional uplink for fault tolerance).
2. Enable load balancer between uplinks (Load Balancing - enabled).
3. Enable traffic shaping rules. For VoIP and Videoconferencing set the priority to High. For categories Peer-to-peer, Online backup, Video & Music, set the bandwidth limit and the priority to Low.
4. With these settings, even in the case of limited bandwidth, your users will not notice a decrease in data transfer speed: the channel for business applications will not be blocked by outgoing traffic. These functions are available on all Cisco Meraki MX Security Gateways; all that remains is to choose the model you need depending on your needs, the availability of WiFi, PoE, specific ports (Fig. 4, 5).
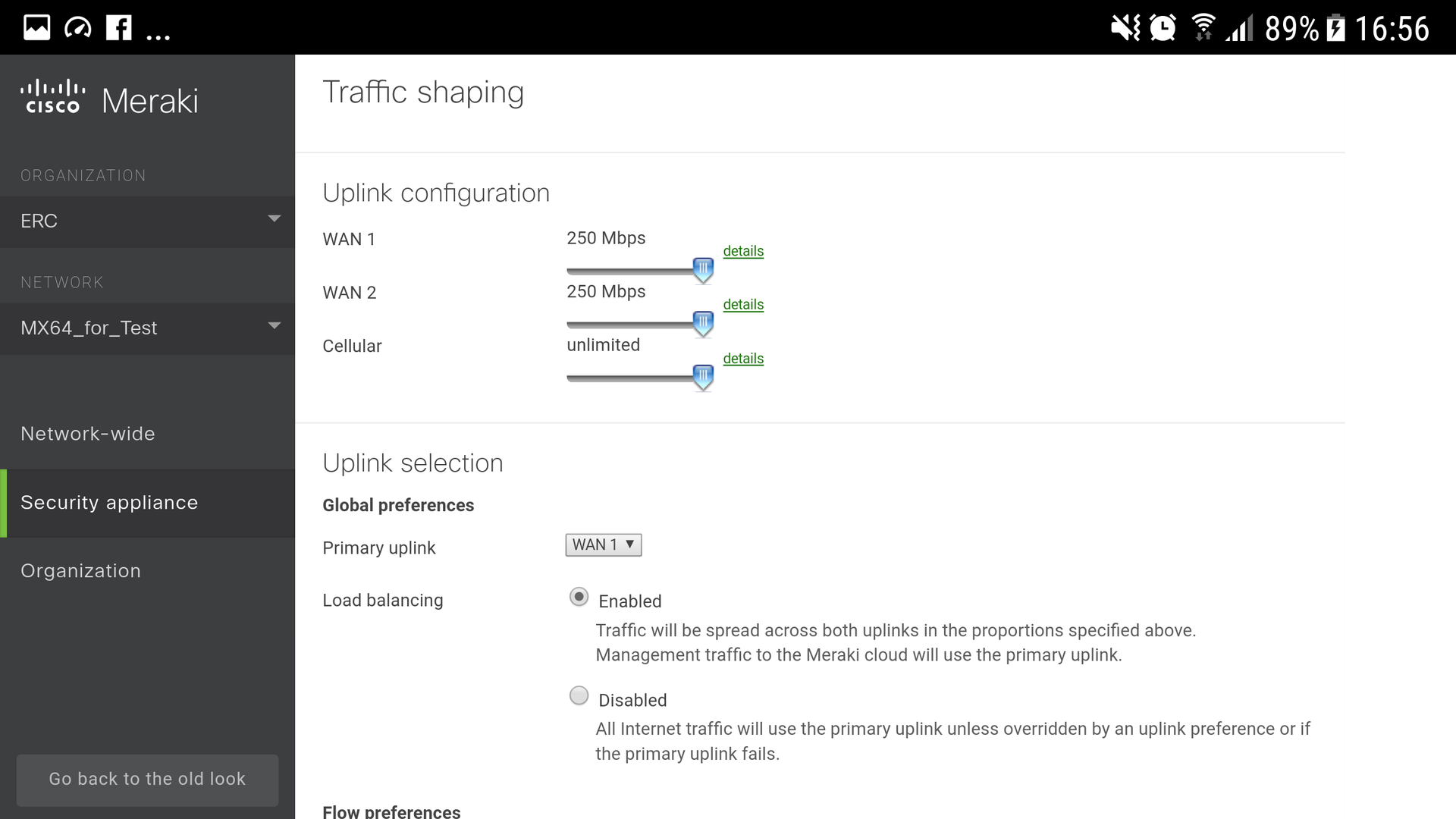
Figure 4
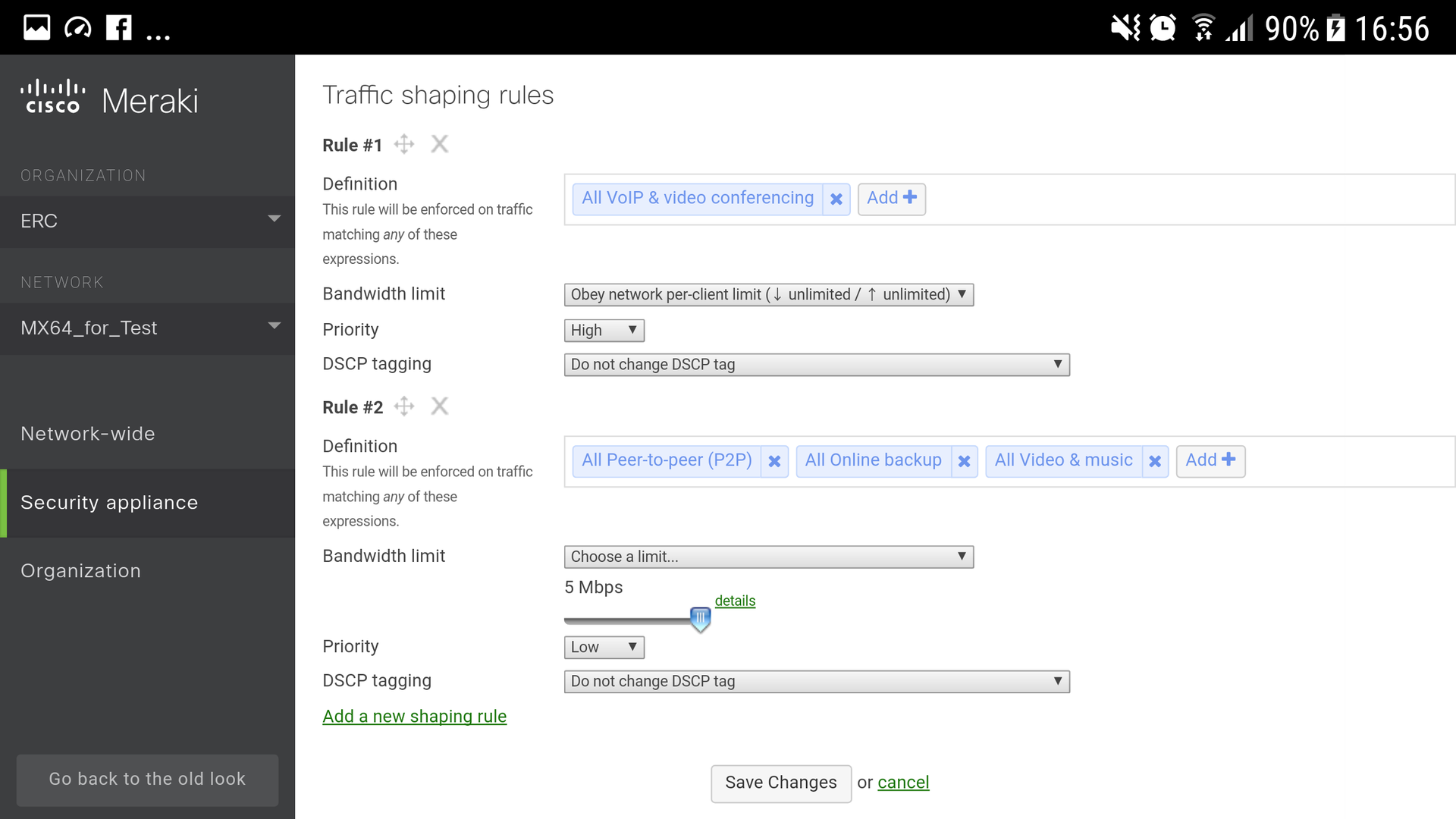
Figure 5
In Russia, the Cisco Meraki solution is currently not available for ordering.
In Ukraine, Azerbaijan, Georgia, Cisco Meraki can be purchased directly from local Cisco partners .
For the requirements of most companies, both small and medium-sized and large, with a geographically distributed infrastructure, the Cisco Meraki MX Security Gateways are perfect. They are easy to set up, do not require the presence of security administrators in remote branches, and at the same time use the same signature sets as the top Cisco Firepower solutions.
Consider a few basic options for using Meraki MX in an organization. They can be configured in just 4 clicks of the mouse on the intuitive Meraki Cloud panel without complicated settings and command line.
Connection with the new branch - AutoVPN
One of the most common use cases for a VPN is to connect a remote employee to a corporate network. What allows the user to feel like at work and can easily use corporate services. At the same time, he will not be able to get around just that, what exactly is this user busy with, what data does he transmit and receive.
')
The second, equally common use case is similar to the first, only individual users are connected to the corporate network, but entire offices or buildings. The goal is the same - to safely and securely combine geographically remote elements of one organization into a single network. When creating such connections, you need to take into account a lot of nuances: the authentication method, the encryption protocol, the network and the type of traffic that will use the tunnel and much more.
Meraki MX family devices have the necessary set of tools for creating such VPN tunnels in automatic mode.
4-click setup
1. Select the VPN concentrator mode (Hub mode is selected in the center, so click Spoke).
2. For Spoke, select Split tunneling mode in order to use the VPN tunnel only for traffic to the central office, and issue Internet traffic directly to the light.
3. All subnets have already been calculated, you only need to choose which VPNs can use (specify yes / no opposite).
4. Save. Now the Meraki cloud will automatically coordinate the addressing and parameters of the IPsec AES128 tunnels and distribute the data about the VPN routes on the MX device in the network (Figure 1).

Figure 1
Threat Protection
Any network is a target for intrusions and malicious attacks. Such invasions are caused by confidential information leaks, shutdowns of business-critical applications, and even enterprise crashes. Meraki MX is equipped with advanced and customizable tools to counter such threats. IPS tandem on SourceFire Snort, Cisco Advanced Malware Protection and daily signature database updates protect the corporate network from potential risks. A system of retrospective analysis will allow to take measures even in the case of passing 0Day attacks.
4-click setup
1. Enable anti-virus scanning (Malware prevention - enabled).
2. Enable protection against unauthorized access based on SourceFire (Intrusion detection and prevention - select Mode Prevention).
3. Choose from three pre-set IPS rule sets from most loyal to restrictive (Connectivity / Balanced / Security).
4. Save. Now you are protected and can view the analytics (Fig. 2).

Figure 2
Acceptable Internet use
Content filtering system provides secure use of the Internet by users within the network. When a user requests a URL, it is checked in several stages and can be blocked for viewing due to the presence of malicious or unwanted content.
4-click setup
1. Select the categories of web sites that need to be blocked (we recommend blocking Adult, Bot Nets, Confirmed SPAM, Illegal, Malware Sites, Phishing, Proxy Avoidance, SPAM URLs, Spyware).
2. Enable search filtering (Web search filtering - enabled).
3. Enable YouTube filtering (YouTube for schools - enabled).
4. Save. Now, the employees of your company (or students of your school) have limited access to sites that cannot be used in the workplace (Fig. 3).

Figure 3
Shaping and traffic prioritization
Currently, together with a systematic increase in data transmission speeds in telecommunications, the share of interactive traffic is extremely sensitive to the parameters of the transportation environment. Therefore, the task of ensuring quality of service (Quality of Service - QoS) is becoming increasingly important. We need business critical applications to take precedence over various multimedia applications and not suffer from filling the channel.
4-click setup
1. Select the parameters for the allowable load of input and output traffic for both WAN uplinks (you also have the ability to connect a 3G / 4G modem as an additional uplink for fault tolerance).
2. Enable load balancer between uplinks (Load Balancing - enabled).
3. Enable traffic shaping rules. For VoIP and Videoconferencing set the priority to High. For categories Peer-to-peer, Online backup, Video & Music, set the bandwidth limit and the priority to Low.
4. With these settings, even in the case of limited bandwidth, your users will not notice a decrease in data transfer speed: the channel for business applications will not be blocked by outgoing traffic. These functions are available on all Cisco Meraki MX Security Gateways; all that remains is to choose the model you need depending on your needs, the availability of WiFi, PoE, specific ports (Fig. 4, 5).

Figure 4

Figure 5
In Russia, the Cisco Meraki solution is currently not available for ordering.
In Ukraine, Azerbaijan, Georgia, Cisco Meraki can be purchased directly from local Cisco partners .
Source: https://habr.com/ru/post/328862/
All Articles