How to protect a modern data center
The tendency of software-defined solutions to spread has long reached the corporate data centers. The "correct" data center today is a software-configurable data center or, as they also say, software-defined (SDDC). According to analytical agencies, more than 75% of companies are already working with software-defined data centers, while the level of virtualization in them continues to grow.

There are additional requirements for data centers. One of the most important is the high degree of infrastructure security. Reliable data center protection is a critical factor for data center owners as well as for any large enterprise.

Changes in data centers require a review of security policy. IB must become as flexible and dynamic as a modern IT infrastructure, be able to adapt to its changes, and at the same time not have a negative impact on the performance of IT systems.
')
According to experts of Kaspersky Lab, traditional protection has no place in a modern data center, the existing security concept can no longer be applicable and should be revised. New interaction scenarios have appeared, the virtual environment establishes new connections between the infrastructure components.
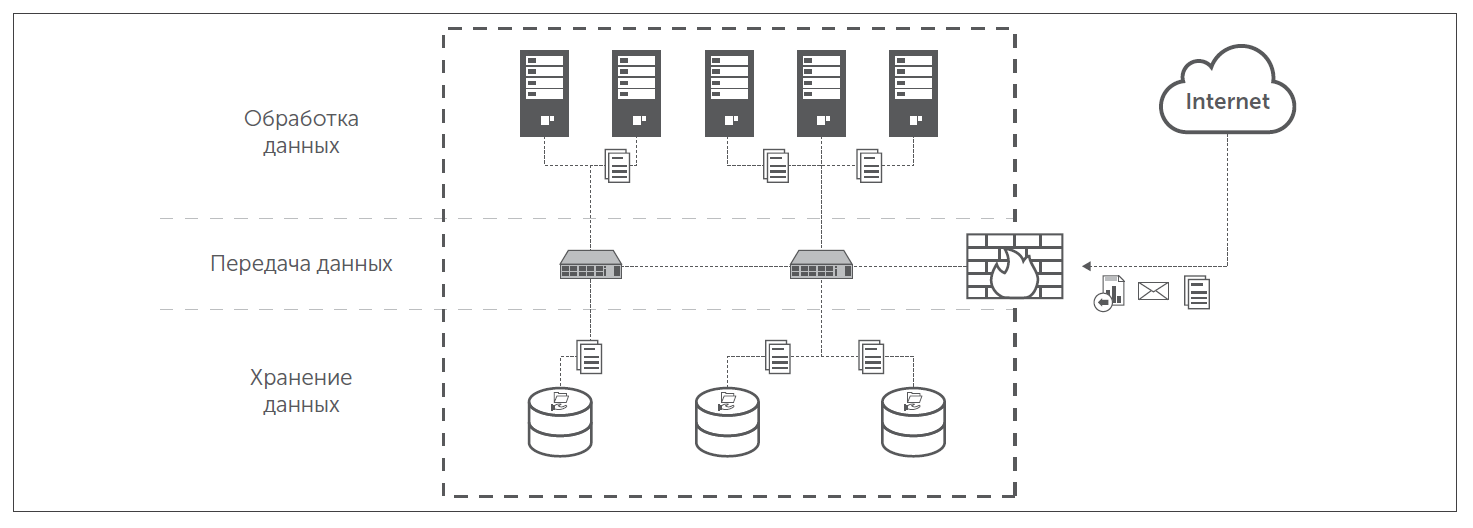
With all the new trends, the principles of building the infrastructure of corporate data centers are still quite traditional. It includes a storage, data processing and network infrastructure.
Modern data center combines:
All of these components are critical for the work of the data center and require protection, taking into account the characteristics of specific technologies. For example, in a virtual environment, traditional security solutions that are not adapted to its specificity are too “resource-intensive”, inhibit the operation of critical business applications, and create inconvenience for users.
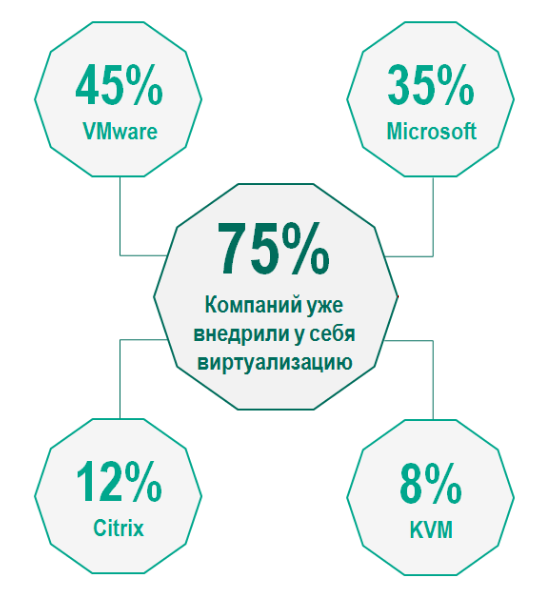
According to a survey of companies from 25 countries conducted by Kaspersky Lab, 44% of respondents use traditional solutions to protect virtual environments.
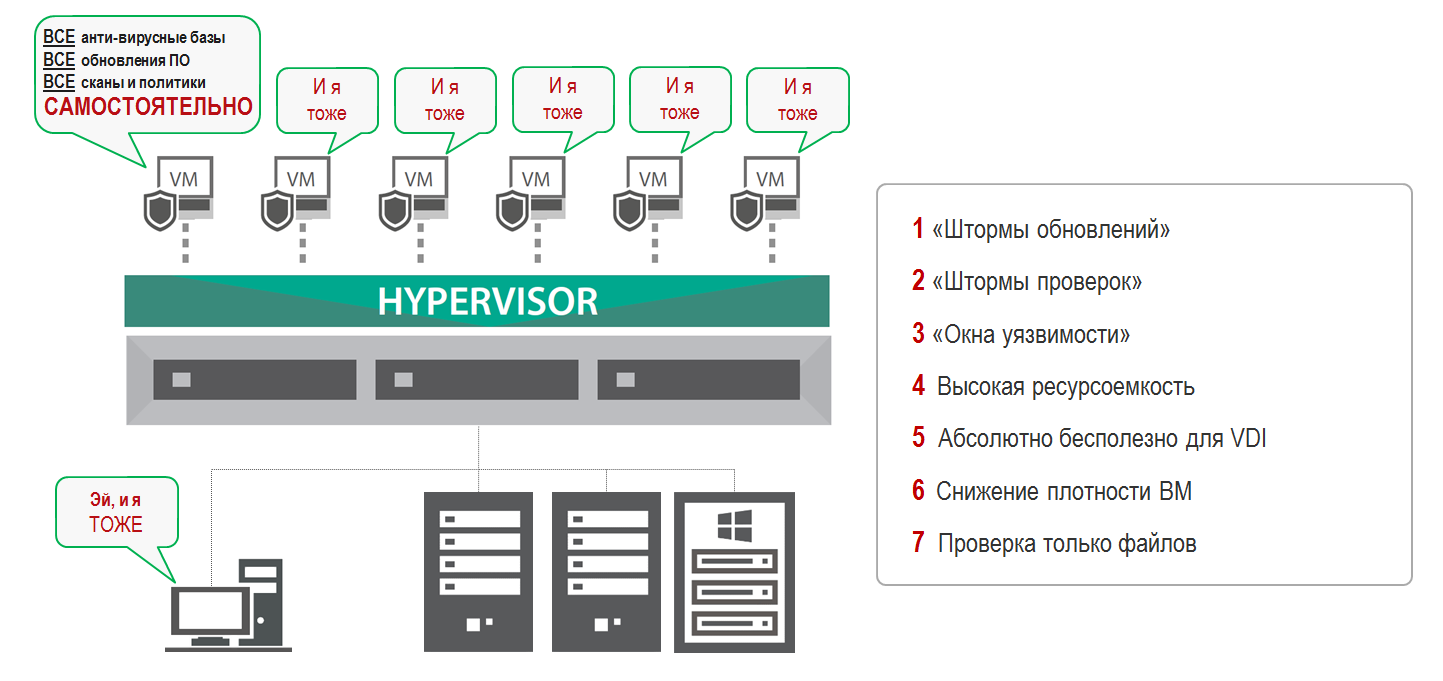
Virtual machines perform redundant tasks. VM locally stores and updates anti-virus databases, performs scans for malicious code, protects itself from network attacks. This creates a significant additional load on the host system, reducing the efficiency of the IT infrastructure and its users, which is especially noticeable during the “update storm” and “inspection storm”.
If a VM is not used for a long time, its anti-virus databases become obsolete, a “window of vulnerability” appears, and these are threats to the security of the entire corporate data center. In the traditional approach, it is also not possible to ensure the security of all file operations.
If traditional solutions are deployed to protect virtual infrastructures, their impact may be almost worse than the penetration of malware. They can seriously slow down the work of IT systems, preventing them from functioning normally, as well as creating problems for the execution of business tasks by company employees.
If the organization of information security issues is poorly or not worked out at all, then many of the existing threats will be dangerous even for the most modern data centers, where the best infrastructure security is implemented using, for example, micro-segmentation. Therefore, in any case, specialized solutions designed specifically for virtual environments should be used to protect the data center from cyber attacks and malware.
Software-defined data centers combine a large number of systems aimed at solving different tasks. Security technologies must work in the right place at the right time, regardless of the complexity and scale of the infrastructure.
There are problems of uncontrolled growth of the number of VMs, network interaction in virtualized infrastructures, when network traffic bypasses the physical equipment installed to protect the corporate network and its perimeter. As a result, network protection devices do not provide complete control. A permanently turned off VM is no longer updated and becomes a weak link in information security. In the VDI infrastructure, the damage or infection of the “golden image” can lead to the emergence of hundreds of dangerous virtual machines.
Network storage devices (NAS) also require an additional solution specifically designed to protect critical data without compromising system performance.
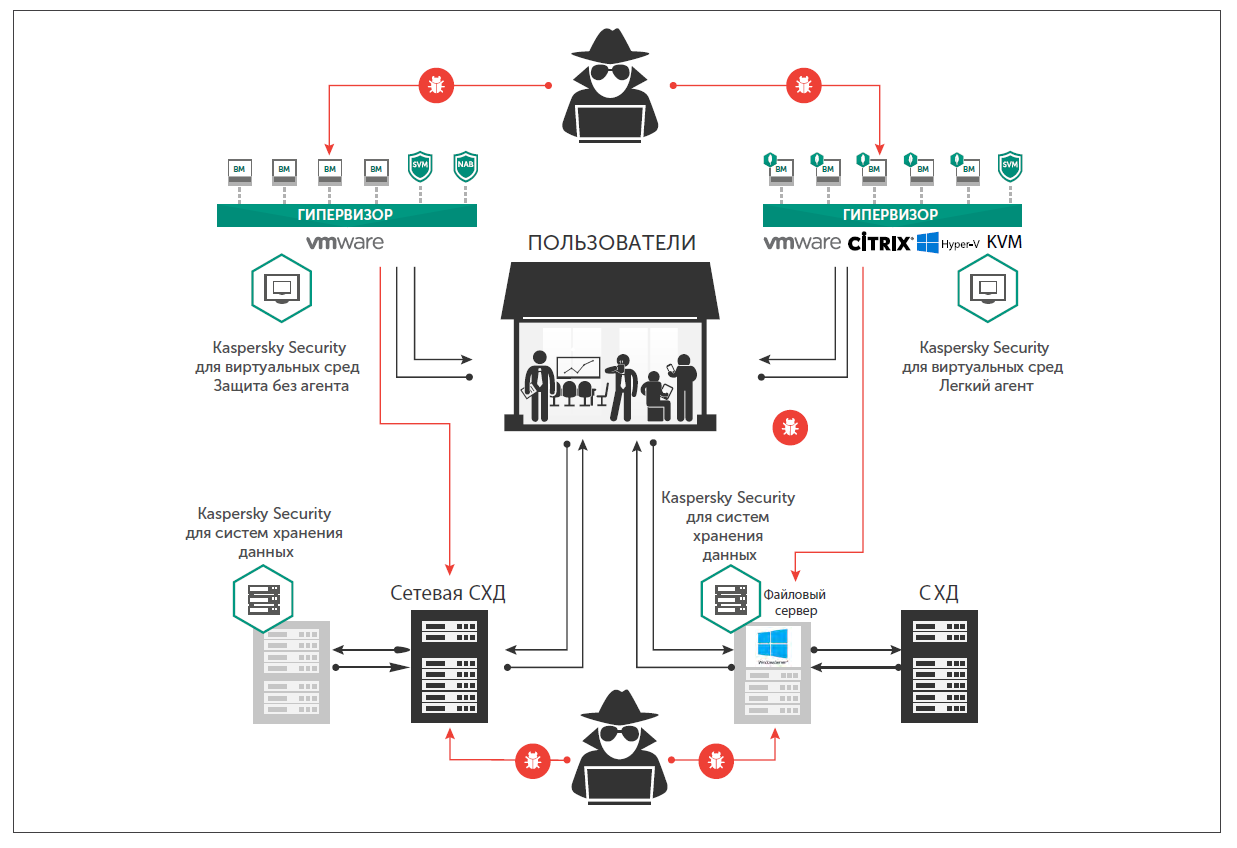
Kaspersky Lab offers a specialized solution to protect modern data centers, which has a minimal impact on its performance and speed of systems. It provides for integration with technological solutions used in the data center and management from a single console.
Let's see what Kaspersky Lab offers to protect corporate data centers.
The VMware vSphere platform with NSX technology allows you to quickly create or reconfigure your network topology and quickly implement a security strategy using a joint solution from Kaspersky Lab and VMware. It was specifically designed to protect software-defined data centers built on VMware technology.

Features agentless protection in Kaspersky Security for virtual environments.
The Kaspersky Security for Virtual Environments solution does not require the installation of an additional agent on protected VMs, and the “extra” processes for the virtualized environment are transferred to dedicated security devices that scan files and network traffic without degrading the performance of key data center systems. Each VM is protected immediately after power on.
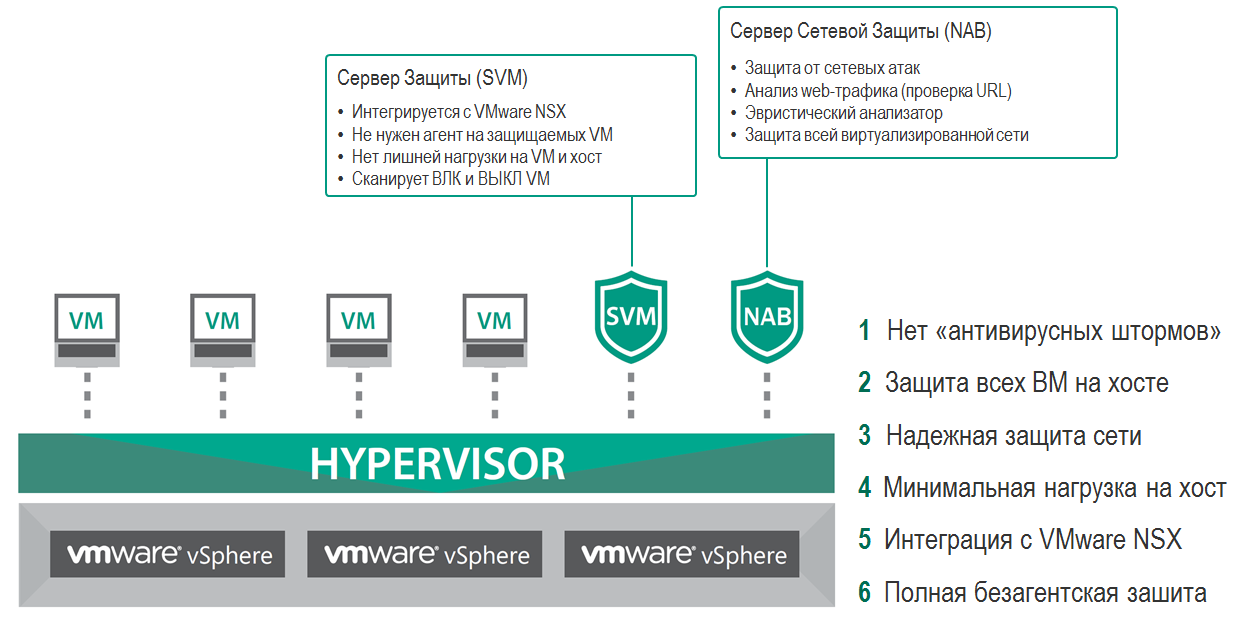
Kaspersky Security interacts with the VMware infrastructure through an API, which allows not only to protect each VM, block network threats and integrate deeply with system processes.
Automatic deployment simplifies the work of staff, each VM receives a level of protection according to the corporate information security policy. The data center can react to IS incidents in real time by reconfiguring the network topology. The entire corporate data center is protected 24x7.

The solution architecture was originally designed to minimally impact the operation of business-critical servers.
If Kaspersky sees malicious activity, then the VMware NSX platform immediately receives information about it, and then the configuration of the IT infrastructure can be rebuilt by the VMware NSX platform completely automatically.
Some virtual environments do not include an API that allows the integration of the infrastructure itself and the solution to protect it. And the VDI infrastructure, for example, requires reliable protection of the user regardless of his level of awareness of current threats and methods to prevent them.
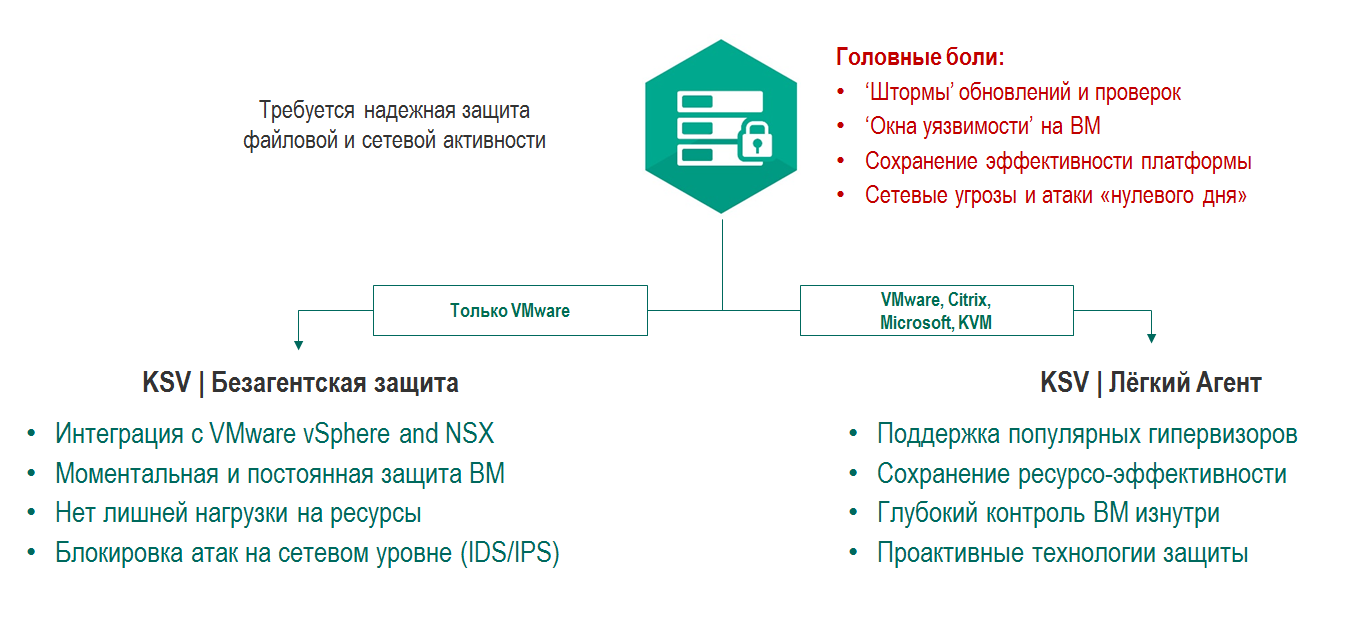
Kaspersky Security solution with light agents provides additional levels of protection.
Kaspersky Security with light agents supports the most popular virtualization platforms, including VMware vSphere, Microsoft Hyper-V, Citrix XenServer and KVM, while in a VDI environment such as VMware Horizon and Citrix XenDesktop, performance is maintained.

A light agent controls the launch of programs and protects virtual jobs.
A dedicated virtual machine (SVM, Security Virtual Machine) performs a centralized scan of all VMs, a lightweight agent that is installed on each VM, allows you to not only check files, but also scan memory and processes.

Deploying a light agent in a VDI environment enables you to use advanced security features, including launch control of applications, devices and URLs, as well as heuristic e-mail and Internet traffic analysis modules.
Application launch control means the following:

Protection features with a light agent in Kaspersky Security for virtual environments.
Application Privilege Control manages application activity within each individual VDI machine, restricts access to resources based on rules and policies. Virtual workplaces are also protected from complex attacks, including encryption viruses.
An intrusion prevention system combines a network attack blocker (NAB) and a firewall. It detects and blocks the latest network attacks, monitors network traffic for malicious activity. And device control manages access to storage devices, network devices, printing devices, and system buses, providing privacy and protection against data leakage.
It also provides protection for incoming and outgoing traffic (HTTP, FTP). Each link (URL) is checked by a light agent to make sure that it is not malicious and / or phishing. POP3, SMTP, IMAP, and NNTP protocol protection intercepts and scans each email message with an incident notification about each VDI user.
How difficult is protection with a light agent, how to install it correctly? The process involves several steps. Need to:
Kaspersky Securtiy for storage systems integrates with a variety of enterprise-level network storage systems using ICAP and RPC protocols, ensuring protection of every file operation and eliminating the risk of malware infecting important corporate files. The antivirus engine scans every file when it is launched or modified, and heuristic analysis can even detect new and unknown threats.
Scan configuration allows you to create so-called "trusted zones", which can be excluded from the scan, along with certain file formats and processes, such as backup.
Installing a “heavy” solution for VM protection creates a high load, significantly increases the use of resources on hypervisors and can negate all the advantages of the software-defined data center. The use of old approaches or insufficient attention to the organization of the protection of the data center can lead to its failure and cause serious damage to business and reputation. It is important that the security solution be designed specifically for such infrastructures, provide for effective integration with the core technologies and do not adversely affect the performance and performance of the systems.
Equally important is security in the cloud area when deploying virtual servers. For example, providers, owners of commercial data centers, offer their customers anti-virus protection of virtual servers (VPS / VDS) running under Windows Server and Linux. The lightweight agent is installed on the client's virtual machine, and its deployment allows you to activate advanced security features. Thus, RUVDS offers Kaspersky Security for Virtualization 4.0 Light Agent (Kaspersky Anti-Virus light agent for virtual environments). Peaks in resource consumption are smoothed using an intelligent task distribution system that automatically groups and prioritizes VPS verification tasks.
The security system controls the behavior of programs running on the VM, rolls back malicious actions and protects against encryption programs. Protection technology against network attacks and intrusion prevention system protects the virtual infrastructure from network threats. Controlling external URLs allows you to protect each VM and its users from Internet resources that do not comply with security policies or carry high risk. The control of launching programs and their privileges controls the activity of users, so that only trusted applications can run on the VM.
Mail and web traffic protection protects data exchange and communications of corporate users with the “outside world”, while device control ensures protection of each virtual desktop when virtualized USB devices and network printers are connected to it.


There are additional requirements for data centers. One of the most important is the high degree of infrastructure security. Reliable data center protection is a critical factor for data center owners as well as for any large enterprise.

Changes in data centers require a review of security policy. IB must become as flexible and dynamic as a modern IT infrastructure, be able to adapt to its changes, and at the same time not have a negative impact on the performance of IT systems.
')
According to experts of Kaspersky Lab, traditional protection has no place in a modern data center, the existing security concept can no longer be applicable and should be revised. New interaction scenarios have appeared, the virtual environment establishes new connections between the infrastructure components.

With all the new trends, the principles of building the infrastructure of corporate data centers are still quite traditional. It includes a storage, data processing and network infrastructure.
What and how to protect (and how not to)?
Modern data center combines:
- Data center infrastructure with virtualization platforms (VMware vSphere, Microsoft Hyper-V, Citrix XenServer, or KVM).
- Storage infrastructure - file servers, storage systems of different types.
- Network infrastructure that provides data center interoperability as well as virtual networks (for example, based on VMware NSX).
All of these components are critical for the work of the data center and require protection, taking into account the characteristics of specific technologies. For example, in a virtual environment, traditional security solutions that are not adapted to its specificity are too “resource-intensive”, inhibit the operation of critical business applications, and create inconvenience for users.

According to a survey of companies from 25 countries conducted by Kaspersky Lab, 44% of respondents use traditional solutions to protect virtual environments.
Virtual machines perform redundant tasks. VM locally stores and updates anti-virus databases, performs scans for malicious code, protects itself from network attacks. This creates a significant additional load on the host system, reducing the efficiency of the IT infrastructure and its users, which is especially noticeable during the “update storm” and “inspection storm”.
If a VM is not used for a long time, its anti-virus databases become obsolete, a “window of vulnerability” appears, and these are threats to the security of the entire corporate data center. In the traditional approach, it is also not possible to ensure the security of all file operations.

If traditional solutions are deployed to protect virtual infrastructures, their impact may be almost worse than the penetration of malware. They can seriously slow down the work of IT systems, preventing them from functioning normally, as well as creating problems for the execution of business tasks by company employees.
If the organization of information security issues is poorly or not worked out at all, then many of the existing threats will be dangerous even for the most modern data centers, where the best infrastructure security is implemented using, for example, micro-segmentation. Therefore, in any case, specialized solutions designed specifically for virtual environments should be used to protect the data center from cyber attacks and malware.
Software-defined data centers combine a large number of systems aimed at solving different tasks. Security technologies must work in the right place at the right time, regardless of the complexity and scale of the infrastructure.
There are problems of uncontrolled growth of the number of VMs, network interaction in virtualized infrastructures, when network traffic bypasses the physical equipment installed to protect the corporate network and its perimeter. As a result, network protection devices do not provide complete control. A permanently turned off VM is no longer updated and becomes a weak link in information security. In the VDI infrastructure, the damage or infection of the “golden image” can lead to the emergence of hundreds of dangerous virtual machines.
Network storage devices (NAS) also require an additional solution specifically designed to protect critical data without compromising system performance.

Kaspersky Lab offers a specialized solution to protect modern data centers, which has a minimal impact on its performance and speed of systems. It provides for integration with technological solutions used in the data center and management from a single console.
Let's see what Kaspersky Lab offers to protect corporate data centers.
NSX integration and agentless protection
The VMware vSphere platform with NSX technology allows you to quickly create or reconfigure your network topology and quickly implement a security strategy using a joint solution from Kaspersky Lab and VMware. It was specifically designed to protect software-defined data centers built on VMware technology.

Features agentless protection in Kaspersky Security for virtual environments.
The Kaspersky Security for Virtual Environments solution does not require the installation of an additional agent on protected VMs, and the “extra” processes for the virtualized environment are transferred to dedicated security devices that scan files and network traffic without degrading the performance of key data center systems. Each VM is protected immediately after power on.

Kaspersky Security interacts with the VMware infrastructure through an API, which allows not only to protect each VM, block network threats and integrate deeply with system processes.
Automatic deployment simplifies the work of staff, each VM receives a level of protection according to the corporate information security policy. The data center can react to IS incidents in real time by reconfiguring the network topology. The entire corporate data center is protected 24x7.

The solution architecture was originally designed to minimally impact the operation of business-critical servers.
If Kaspersky sees malicious activity, then the VMware NSX platform immediately receives information about it, and then the configuration of the IT infrastructure can be rebuilt by the VMware NSX platform completely automatically.
Light agents
Some virtual environments do not include an API that allows the integration of the infrastructure itself and the solution to protect it. And the VDI infrastructure, for example, requires reliable protection of the user regardless of his level of awareness of current threats and methods to prevent them.

Kaspersky Security solution with light agents provides additional levels of protection.
Kaspersky Security with light agents supports the most popular virtualization platforms, including VMware vSphere, Microsoft Hyper-V, Citrix XenServer and KVM, while in a VDI environment such as VMware Horizon and Citrix XenDesktop, performance is maintained.

A light agent controls the launch of programs and protects virtual jobs.
A dedicated virtual machine (SVM, Security Virtual Machine) performs a centralized scan of all VMs, a lightweight agent that is installed on each VM, allows you to not only check files, but also scan memory and processes.

Deploying a light agent in a VDI environment enables you to use advanced security features, including launch control of applications, devices and URLs, as well as heuristic e-mail and Internet traffic analysis modules.
Application launch control means the following:
- Only trusted applications can run.
- New applications are checked by the administrator.
- You can dynamically update the list.
- Run everything except the blacklist.
- Works for all users of the system.

Protection features with a light agent in Kaspersky Security for virtual environments.
Application Privilege Control manages application activity within each individual VDI machine, restricts access to resources based on rules and policies. Virtual workplaces are also protected from complex attacks, including encryption viruses.
An intrusion prevention system combines a network attack blocker (NAB) and a firewall. It detects and blocks the latest network attacks, monitors network traffic for malicious activity. And device control manages access to storage devices, network devices, printing devices, and system buses, providing privacy and protection against data leakage.
It also provides protection for incoming and outgoing traffic (HTTP, FTP). Each link (URL) is checked by a light agent to make sure that it is not malicious and / or phishing. POP3, SMTP, IMAP, and NNTP protocol protection intercepts and scans each email message with an incident notification about each VDI user.
How difficult is protection with a light agent, how to install it correctly? The process involves several steps. Need to:
- Install the KSV control plugin on the KSC.
- Deploy security servers to hypervisors.
- Define security policies and settings.
- Create update tasks and key distribution.
- Distribute light agent installation packages to the VM.
- At KSC, set up a policy of light agents.
Storage Security
Kaspersky Securtiy for storage systems integrates with a variety of enterprise-level network storage systems using ICAP and RPC protocols, ensuring protection of every file operation and eliminating the risk of malware infecting important corporate files. The antivirus engine scans every file when it is launched or modified, and heuristic analysis can even detect new and unknown threats.
Scan configuration allows you to create so-called "trusted zones", which can be excluded from the scan, along with certain file formats and processes, such as backup.
Conclusion
Installing a “heavy” solution for VM protection creates a high load, significantly increases the use of resources on hypervisors and can negate all the advantages of the software-defined data center. The use of old approaches or insufficient attention to the organization of the protection of the data center can lead to its failure and cause serious damage to business and reputation. It is important that the security solution be designed specifically for such infrastructures, provide for effective integration with the core technologies and do not adversely affect the performance and performance of the systems.
Equally important is security in the cloud area when deploying virtual servers. For example, providers, owners of commercial data centers, offer their customers anti-virus protection of virtual servers (VPS / VDS) running under Windows Server and Linux. The lightweight agent is installed on the client's virtual machine, and its deployment allows you to activate advanced security features. Thus, RUVDS offers Kaspersky Security for Virtualization 4.0 Light Agent (Kaspersky Anti-Virus light agent for virtual environments). Peaks in resource consumption are smoothed using an intelligent task distribution system that automatically groups and prioritizes VPS verification tasks.
The security system controls the behavior of programs running on the VM, rolls back malicious actions and protects against encryption programs. Protection technology against network attacks and intrusion prevention system protects the virtual infrastructure from network threats. Controlling external URLs allows you to protect each VM and its users from Internet resources that do not comply with security policies or carry high risk. The control of launching programs and their privileges controls the activity of users, so that only trusted applications can run on the VM.
Mail and web traffic protection protects data exchange and communications of corporate users with the “outside world”, while device control ensures protection of each virtual desktop when virtualized USB devices and network printers are connected to it.

Source: https://habr.com/ru/post/328794/
All Articles