Security threats in electronic postage stamp systems
Hi% username!
The habr for the Postal Form is about to close for an indefinite period, and we really want to have time to release at least a small part of the long-term construction. The article will discuss the main vulnerabilities of the two-dimensional code, which is more and more often used in the world of postal operators as a sign of payment for mailings. Yes, there is a lot of confusion in the article, but we have only 20 minutes to block and very, very much collected useful information.
So.
Light, camera, motor!
')
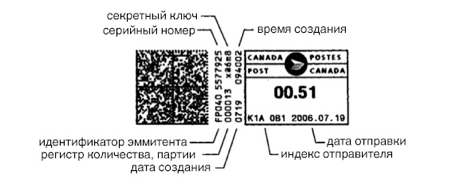
The main task of e-postage systems is to provide the sender with the opportunity to use the services of postal operators, correctly determine the amount of postage for each service used and transfer the appropriate funds from the sender to the postal operator safely and in a timely manner. The second most important tasks are to provide postal operators with accurate data on the use of postal services, additional information to the user when tracking a postal item, as well as protecting the confidentiality of information about senders and recipients ("communication secret").
In order to develop and start using such a system, at the design stage it is important to anticipate possible security risks to which it will be exposed during the entire lifetime, and after deployment, regularly re-evaluate the residual risks. For any considered EPM system, all actions must be planned in advance, organized and carried out within the framework of the so-called “risk management process”. This is a recurring cycle of taking measures to reduce the identified risks to an acceptable level and maintain it further.
At the risk assessment stage, it is necessary to determine the relevant data held by the system and to evaluate them. The following indicates a possible threat of damage to the established data. Threats include an emergency or malfunction, as well as hacker attacks. In order to understand the resilience of the system to attacks, it is useful to develop their model describing which parts of the system may be vulnerable to an attacker, what methods of attacks he has and what resources he has.
Unintentional threats can be measured by the degree of their likelihood. Hacker attacks can be judged on the basis of the expected benefits that attackers can help out. The greater the value of the target asset, the higher the risk of security breach; the more likely or cheaper to launch an attack, the more serious or critical the expected breach of the security system or the damage to the relevant data will be.
The risk assessment phase usually consists of a security audit, which examines all active and operational components. The final system security report provides a framework with which you can determine the current level and compare it with the results of the previous audit. In the case of detection of new vulnerabilities or security threats, as well as if existing protection measures are considered ineffective, a new phase is introduced in which additional protection measures are identified and established with a corresponding update of the system documentation.
In this article, we will look at the systems of electronic postal prepayments from the point of view of the postal operator, the main requirement of which is the protection of legitimate income. Next, we will develop a catalog of security threats common to most EMP systems. We will also give examples of threats to mechanical and electromechanical franking machines.

Typical modern franking machine
We agree that in the commercial sector there are 3 classes of intruders:
■ Attackers of class 1 : people from the side, often very intellectually developed, but lacking sufficient knowledge of the system. They may have access only to equipment of medium complexity and often try to take advantage of an existing vulnerability in the system, without trying to find new ones.
■ Attacking 2 classes : internal specialists with relevant technical education and significant experience. To varying degrees, they have an understanding of how the components of the system work. Most often they own modern tools and tools for analysis.
■ Attackers 3 classes : funded by organizations able to organize teams of specialists with related and complementary skills, provided with large financial resources. They are capable of in-depth analysis of the system, the development of complex attacks using the most advanced analysis tools, and can use attacking class 2 as part of a team.
In the EMP systems, it is necessary to clearly distinguish the areas of potential attacks: the mail delivery domain and the backoffice domain.
The sender is always identified at the time of registration of the EMP generation devices, and companies using closed EPM devices (franking machines), under certain circumstances, are obliged to deal with postal inspections. Otherwise, the replenishment processes remain virtually uncontrolled by the postal operator, which creates various opportunities for attacks.
In traditional mail transport and processing systems, where mail is not protected by cryptography, attackers can directly access the mail transport system by bribing or blackmailing postal employees who work in logistics centers handling mail. Thus, attackers, without great risk of detection, can illegally throw bags with unpaid mail into the mail channel and delivery system after the blanking stage of the prints and before the address recognition stage. It can be assumed that these methods of attack can be used by attacking class 1.

E-mail stamp processing center
In ePM systems, mail processing centers are designed in such a way that the franc verification process includes a snapshot of each mail item. Then, the resulting digital image is divided into the lower part, which contains the recipient's address, and the upper part, which contains payment information. If the verification of payment fails, the shipment is automatically sorted and delivered to the recipient, subject to payment of a penalty, or otherwise returned to the sender. This higher degree of automation and system integration effectively prevents access to the first-class attacking mail delivery system, which used methods of bribing or blackmailing postal workers. However, an attacker may attempt to misuse the EPR devices to obtain valid stamps on mail items that will be freely passed through processing centers. It is important to remember that EPM devices are used in unsupervised environments. Attackers can explore one or more devices to analyze their defense mechanisms before planning a complex attack on new ones.
Social engineering, collusion - deliberate collaboration between several fraud members pursuing fraudulent goals. Parties may collude across security areas, for example, senders cooperating with corrupt employees of an EMF provider and / or postal operator. Another type of collusion is an example where an attacker “hires” a former employee of the manufacturer of an EPM device to access inside information and tools to control this type of device, as well as to obtain seals or replaceable plastic seals to eliminate traces of intrusion.
Unauthorized access to the system - a general definition for any type of attack that interferes with the integrity or accountability of financial transaction systems. Most of them are still guided by the principle of security, which provides narrowly limited access for unauthorized persons if they do not have the necessary powers, and full access rights for internal specialists. Thus, persons with unrestricted access to confidential information, by virtue of their official position, may incorrectly use their access rights to databases or application servers to create hidden accounts and launch malware. As a result, outsiders may gain access to confidential information after they have calculated passwords or otherwise captured one of the privileged user accounts.
The actions of the offender under the guise of a legitimate user are a fraud, as a result of which personal data of the sender who did not actually send anything is displayed on the stamp of the postal item. This can occur as a result of using lost or stolen EPM devices without re-registering them with the postal service operator. For example, in 1996, only 0.6% of all registered franking machines were lost or stolen in the US market.
Refunds - an attempt to replenish the electronic mass storage device from the electronic mass media provider, which will later be canceled (for example, using a rejected check or refusing to debit funds from an account). The attacker will try to replenish the franking machine, before the provider can find out that in fact the payment failed.
Illegal modification of EPM devices is a fraud scheme as well. For example, in mechanical franking machines, locks and seals were neutralized in order to replace printed clichés, which, for example, were taken from the lost or stolen machines of this or a similar model. Another type of attack is a way to bypass the blocking mechanism, which aims to prevent the franking process after the remainder in the downstream DR register has been expended (for more information on the registers of frankmashins, see our first article ). Such “jackpot” machines could be tuned to the maximum number of available mailings, which in some cases amounted to $ 99,999,999.
Bypassing the control of the printing mechanism occurs by replacing the control system of the printing mechanism with its own software running from a PC in the EPM device. This attack can theoretically produce any stamps and print them with postal ink.
Print reuse is a type of attack in which the print control unit of a legitimate EPM device is connected to printers of two or more EPMs. As a result, the attacker collects one or more free copies of each legitimate stamp on mailings, each of which is printed with mail (fluorescent) ink. This attack leads to the manufacture of higher quality duplicate stamps than in the manufacture of its photocopies.

Special module of the franking machine that stores all existing registers
Physical attacks include drilling, cutting, sand blasting, exposure to heat or cold, or certain chemicals such as acids or solvents on devices. These attacks are aimed at identifying certain electrical access points, which are usually protected by a mail security device.
Other attacks are aimed at extracting the cryptographic keys of individual users from the mail security devices necessary to obtain correct prints.
For example, replacing the original cryptographic keys with false ones or launching man-in-the-middle attacks with the further introduction of a fake key into the mail security device. This attack can lead to the actions of the offender under the guise of a legitimate user, if the attacker uses the cryptographic keys of other clients.
There are attacks aimed at replaying a replenishment transaction without the fact of a repayment. If the received messages are checked at the level of the EPM provider using cryptographic tools, then the attacker may not be able to calculate the actual checksum for a randomly selected message, but he can reuse the previously intercepted message along with its checksum.

Typical sorting
Alteration - is a modification of the intercepted impressions, changing the value of the prepayment or identification or other data of the sender.
Copying is the illegal reproduction of prints using, for example, photocopiers or color laser printers. For EMP systems using cryptographically protected stamps, any stamps that occur twice are, by definition, invalid. However, this will not prevent criminals from creating a large number of copies, because all the “electronic traces” available to investigating authorities will only lead to original stamps of postal prepaid security devices. Another risk postal operators associated with the fact that attackers use high-speed copying machines to fill the mail network with massive copies of stamps.
Counterfeit - the creation of valid or similar to actual impressions in any way other than using a registered EPM device, for example, rubber stamps, software on personal computers or counterfeit EPM devices. This is one of the most common ways of cheating postal operators, which can only be detected through laboratory analysis.
Erroneous application - the use of electronic stamps in the postal item in such a way that the nominal value of the impression does not coincide with the postal item. If this error happens by accident, it can lead to overpayment or underpayment. But in the case where the action is intentional, in most cases this leads to incomplete payment.
Obliteration is a distortion of an imprint in order to make it impossible to read or verify them. This can be achieved by deforming, hiding, blurring the character set. All these actions are difficult to detect because they can be committed unintentionally.
Cryptanalysis is a general term for any kind of attack on a cryptographic mechanism. Each postal operator reserves the right to indicate which cryptographic algorithms are allowed to use in its EMP systems. Even if postal operators regularly review their recommendations regarding the use of new cryptographic algorithms, the old algorithms continue to work in existing systems for a long time. The average period of use of algorithms from commissioning to removal should be no more than 10 years. The advantage of these rules is that an erroneous algorithm is unlikely to be used in approved EFM systems. On the other hand, if an incorrect algorithm is already in use and turns out to be incorrect subsequently or otherwise damaged, then the entire system and potentially all electronic devices and programs are at risk.
The professional way to resolve this predicament is to additionally use instant key updates for each cryptographic mechanism so that it will take effect in an emergency situation.
Cryptanalysis of common hash functions
A hash function that is resistant to finding the second preimage must generate 80 or more bits at the output. In order to be resistant to collisions, hash values must be at least 160 bits long. Shorter output values are not recommended, since the search for second types or collisions can be performed offline, and such attacks can be highly parallelized.
Hash functions are an example of how too limited rules can threaten all electronic postal prepay systems. Not surprisingly, in 2005 (Dada, if you’ve read it up to this point, it means we can say with confidence that we are translating the book of 2005) almost all the EMP systems (and many other cryptographic systems) use SHA-1 for (a) preprocessing messages before they are digitally signed or (b) authenticated by using a message identification code, © obtaining a secret key using the session key agreement and (d) generating pseudo-random bits according to FIPS 186-2. Since the output length of the SHA-1 added extra margin to the minimum recommended output length for the hash functions, SHA-1 was considered sufficiently resistant to collisions. That all changed when, in 2004, Biham and Chen demonstrated new ways of finding possible conflicts in SHA-0 and SHA-1. All of these attacks were aimed at finding collisions, when the attacker must find any two pre-images that are matched with the same hash value for SHA-1.
When focusing on the weaknesses of the hash function, we assume that the attacker will not be able to compromise the private keys of the electronic signature of any mail security device, including his own.
How are these attacks applied to industrial EMP systems and what is the likelihood that they will be successful? In general, the data fields in an imprint fall into two categories: (a) system constants and data that are individual for an EPM client or device, and (b) data that are specific to each individual imprint. Since clients and their EPM devices are usually registered by postal operators, in the imprint the data fields of categories (a) must coincide with the record registered by the postal operator in order to be recognized as valid. The data fields by category (b) may vary, but in general must meet the basic integrity criteria. For example, a data field containing the amount of postage usually corresponds to, or is determined by, a data field containing a category of tariffs or services.
First consider the case where SHA-1 is used in combination with a digital signature algorithm, so the data in the mark is first hashed to a fixed length, and then signed using, for example, RSA, DSA or ECDSA.

USPS Electronic Brand: IBIP (Information Based Indicia Program)
Consider stamps IBIP (Information Based Indiciaia Program), which should be used to send by mail on a particular day. How many valid IBIP stamp values exist on this day?

Variables contained in IBIP
An analysis of the table above shows that 8 of the 14 data fields fall into category (a), or rather fields No. 1-6, 10, and 12. This subset of data can take on any of the 1.6 million franking machine records registered in the United States ( if the market had completely moved to IBIP). The remaining fields are in category (b). Of these, the date of dispatch (field No. 9) automatically coincides with the specified date of registration, and, as a rule, the tariff category (field No. 4) is uniquely determined by the payment amount (field No. 8). Assuming that the unused field number 11 can take any possible value, there are 17 bytes of data category (b) left, data that belongs to the contents of the stamps. Factoring in both data categories is no more than 1.6x10 ^ 6 x 256 ^ 17 ≈ 256 ^ 16.58 of the actual value of the stamps. Any restrictions on filling data fields will further reduce this figure.
So it goes.
The habr for the Postal Form is about to close for an indefinite period, and we really want to have time to release at least a small part of the long-term construction. The article will discuss the main vulnerabilities of the two-dimensional code, which is more and more often used in the world of postal operators as a sign of payment for mailings. Yes, there is a lot of confusion in the article, but we have only 20 minutes to block and very, very much collected useful information.
So.
Light, camera, motor!
')

Management of risks
The main task of e-postage systems is to provide the sender with the opportunity to use the services of postal operators, correctly determine the amount of postage for each service used and transfer the appropriate funds from the sender to the postal operator safely and in a timely manner. The second most important tasks are to provide postal operators with accurate data on the use of postal services, additional information to the user when tracking a postal item, as well as protecting the confidentiality of information about senders and recipients ("communication secret").
In order to develop and start using such a system, at the design stage it is important to anticipate possible security risks to which it will be exposed during the entire lifetime, and after deployment, regularly re-evaluate the residual risks. For any considered EPM system, all actions must be planned in advance, organized and carried out within the framework of the so-called “risk management process”. This is a recurring cycle of taking measures to reduce the identified risks to an acceptable level and maintain it further.
At the risk assessment stage, it is necessary to determine the relevant data held by the system and to evaluate them. The following indicates a possible threat of damage to the established data. Threats include an emergency or malfunction, as well as hacker attacks. In order to understand the resilience of the system to attacks, it is useful to develop their model describing which parts of the system may be vulnerable to an attacker, what methods of attacks he has and what resources he has.
Unintentional threats can be measured by the degree of their likelihood. Hacker attacks can be judged on the basis of the expected benefits that attackers can help out. The greater the value of the target asset, the higher the risk of security breach; the more likely or cheaper to launch an attack, the more serious or critical the expected breach of the security system or the damage to the relevant data will be.
The risk assessment phase usually consists of a security audit, which examines all active and operational components. The final system security report provides a framework with which you can determine the current level and compare it with the results of the previous audit. In the case of detection of new vulnerabilities or security threats, as well as if existing protection measures are considered ineffective, a new phase is introduced in which additional protection measures are identified and established with a corresponding update of the system documentation.
In this article, we will look at the systems of electronic postal prepayments from the point of view of the postal operator, the main requirement of which is the protection of legitimate income. Next, we will develop a catalog of security threats common to most EMP systems. We will also give examples of threats to mechanical and electromechanical franking machines.

Typical modern franking machine
Attacker model
We agree that in the commercial sector there are 3 classes of intruders:
■ Attackers of class 1 : people from the side, often very intellectually developed, but lacking sufficient knowledge of the system. They may have access only to equipment of medium complexity and often try to take advantage of an existing vulnerability in the system, without trying to find new ones.
■ Attacking 2 classes : internal specialists with relevant technical education and significant experience. To varying degrees, they have an understanding of how the components of the system work. Most often they own modern tools and tools for analysis.
■ Attackers 3 classes : funded by organizations able to organize teams of specialists with related and complementary skills, provided with large financial resources. They are capable of in-depth analysis of the system, the development of complex attacks using the most advanced analysis tools, and can use attacking class 2 as part of a team.
In the EMP systems, it is necessary to clearly distinguish the areas of potential attacks: the mail delivery domain and the backoffice domain.
The sender is always identified at the time of registration of the EMP generation devices, and companies using closed EPM devices (franking machines), under certain circumstances, are obliged to deal with postal inspections. Otherwise, the replenishment processes remain virtually uncontrolled by the postal operator, which creates various opportunities for attacks.
In traditional mail transport and processing systems, where mail is not protected by cryptography, attackers can directly access the mail transport system by bribing or blackmailing postal employees who work in logistics centers handling mail. Thus, attackers, without great risk of detection, can illegally throw bags with unpaid mail into the mail channel and delivery system after the blanking stage of the prints and before the address recognition stage. It can be assumed that these methods of attack can be used by attacking class 1.

E-mail stamp processing center
In ePM systems, mail processing centers are designed in such a way that the franc verification process includes a snapshot of each mail item. Then, the resulting digital image is divided into the lower part, which contains the recipient's address, and the upper part, which contains payment information. If the verification of payment fails, the shipment is automatically sorted and delivered to the recipient, subject to payment of a penalty, or otherwise returned to the sender. This higher degree of automation and system integration effectively prevents access to the first-class attacking mail delivery system, which used methods of bribing or blackmailing postal workers. However, an attacker may attempt to misuse the EPR devices to obtain valid stamps on mail items that will be freely passed through processing centers. It is important to remember that EPM devices are used in unsupervised environments. Attackers can explore one or more devices to analyze their defense mechanisms before planning a complex attack on new ones.
Social engineering, collusion - deliberate collaboration between several fraud members pursuing fraudulent goals. Parties may collude across security areas, for example, senders cooperating with corrupt employees of an EMF provider and / or postal operator. Another type of collusion is an example where an attacker “hires” a former employee of the manufacturer of an EPM device to access inside information and tools to control this type of device, as well as to obtain seals or replaceable plastic seals to eliminate traces of intrusion.
Unauthorized access to the system - a general definition for any type of attack that interferes with the integrity or accountability of financial transaction systems. Most of them are still guided by the principle of security, which provides narrowly limited access for unauthorized persons if they do not have the necessary powers, and full access rights for internal specialists. Thus, persons with unrestricted access to confidential information, by virtue of their official position, may incorrectly use their access rights to databases or application servers to create hidden accounts and launch malware. As a result, outsiders may gain access to confidential information after they have calculated passwords or otherwise captured one of the privileged user accounts.
The actions of the offender under the guise of a legitimate user are a fraud, as a result of which personal data of the sender who did not actually send anything is displayed on the stamp of the postal item. This can occur as a result of using lost or stolen EPM devices without re-registering them with the postal service operator. For example, in 1996, only 0.6% of all registered franking machines were lost or stolen in the US market.
Refunds - an attempt to replenish the electronic mass storage device from the electronic mass media provider, which will later be canceled (for example, using a rejected check or refusing to debit funds from an account). The attacker will try to replenish the franking machine, before the provider can find out that in fact the payment failed.
EPM device
Illegal modification of EPM devices is a fraud scheme as well. For example, in mechanical franking machines, locks and seals were neutralized in order to replace printed clichés, which, for example, were taken from the lost or stolen machines of this or a similar model. Another type of attack is a way to bypass the blocking mechanism, which aims to prevent the franking process after the remainder in the downstream DR register has been expended (for more information on the registers of frankmashins, see our first article ). Such “jackpot” machines could be tuned to the maximum number of available mailings, which in some cases amounted to $ 99,999,999.
Bypassing the control of the printing mechanism occurs by replacing the control system of the printing mechanism with its own software running from a PC in the EPM device. This attack can theoretically produce any stamps and print them with postal ink.
Print reuse is a type of attack in which the print control unit of a legitimate EPM device is connected to printers of two or more EPMs. As a result, the attacker collects one or more free copies of each legitimate stamp on mailings, each of which is printed with mail (fluorescent) ink. This attack leads to the manufacture of higher quality duplicate stamps than in the manufacture of its photocopies.
Postal Security Device

Special module of the franking machine that stores all existing registers
Physical attacks include drilling, cutting, sand blasting, exposure to heat or cold, or certain chemicals such as acids or solvents on devices. These attacks are aimed at identifying certain electrical access points, which are usually protected by a mail security device.
Other attacks are aimed at extracting the cryptographic keys of individual users from the mail security devices necessary to obtain correct prints.
For example, replacing the original cryptographic keys with false ones or launching man-in-the-middle attacks with the further introduction of a fake key into the mail security device. This attack can lead to the actions of the offender under the guise of a legitimate user, if the attacker uses the cryptographic keys of other clients.
There are attacks aimed at replaying a replenishment transaction without the fact of a repayment. If the received messages are checked at the level of the EPM provider using cryptographic tools, then the attacker may not be able to calculate the actual checksum for a randomly selected message, but he can reuse the previously intercepted message along with its checksum.
Mail processing area

Typical sorting
Alteration - is a modification of the intercepted impressions, changing the value of the prepayment or identification or other data of the sender.
Copying is the illegal reproduction of prints using, for example, photocopiers or color laser printers. For EMP systems using cryptographically protected stamps, any stamps that occur twice are, by definition, invalid. However, this will not prevent criminals from creating a large number of copies, because all the “electronic traces” available to investigating authorities will only lead to original stamps of postal prepaid security devices. Another risk postal operators associated with the fact that attackers use high-speed copying machines to fill the mail network with massive copies of stamps.
Counterfeit - the creation of valid or similar to actual impressions in any way other than using a registered EPM device, for example, rubber stamps, software on personal computers or counterfeit EPM devices. This is one of the most common ways of cheating postal operators, which can only be detected through laboratory analysis.
Erroneous application - the use of electronic stamps in the postal item in such a way that the nominal value of the impression does not coincide with the postal item. If this error happens by accident, it can lead to overpayment or underpayment. But in the case where the action is intentional, in most cases this leads to incomplete payment.
Obliteration is a distortion of an imprint in order to make it impossible to read or verify them. This can be achieved by deforming, hiding, blurring the character set. All these actions are difficult to detect because they can be committed unintentionally.
Algorithmic level
Cryptanalysis is a general term for any kind of attack on a cryptographic mechanism. Each postal operator reserves the right to indicate which cryptographic algorithms are allowed to use in its EMP systems. Even if postal operators regularly review their recommendations regarding the use of new cryptographic algorithms, the old algorithms continue to work in existing systems for a long time. The average period of use of algorithms from commissioning to removal should be no more than 10 years. The advantage of these rules is that an erroneous algorithm is unlikely to be used in approved EFM systems. On the other hand, if an incorrect algorithm is already in use and turns out to be incorrect subsequently or otherwise damaged, then the entire system and potentially all electronic devices and programs are at risk.
The professional way to resolve this predicament is to additionally use instant key updates for each cryptographic mechanism so that it will take effect in an emergency situation.
Cryptanalysis of common hash functions
A hash function that is resistant to finding the second preimage must generate 80 or more bits at the output. In order to be resistant to collisions, hash values must be at least 160 bits long. Shorter output values are not recommended, since the search for second types or collisions can be performed offline, and such attacks can be highly parallelized.
Hash functions are an example of how too limited rules can threaten all electronic postal prepay systems. Not surprisingly, in 2005 (Dada, if you’ve read it up to this point, it means we can say with confidence that we are translating the book of 2005) almost all the EMP systems (and many other cryptographic systems) use SHA-1 for (a) preprocessing messages before they are digitally signed or (b) authenticated by using a message identification code, © obtaining a secret key using the session key agreement and (d) generating pseudo-random bits according to FIPS 186-2. Since the output length of the SHA-1 added extra margin to the minimum recommended output length for the hash functions, SHA-1 was considered sufficiently resistant to collisions. That all changed when, in 2004, Biham and Chen demonstrated new ways of finding possible conflicts in SHA-0 and SHA-1. All of these attacks were aimed at finding collisions, when the attacker must find any two pre-images that are matched with the same hash value for SHA-1.
When focusing on the weaknesses of the hash function, we assume that the attacker will not be able to compromise the private keys of the electronic signature of any mail security device, including his own.
How are these attacks applied to industrial EMP systems and what is the likelihood that they will be successful? In general, the data fields in an imprint fall into two categories: (a) system constants and data that are individual for an EPM client or device, and (b) data that are specific to each individual imprint. Since clients and their EPM devices are usually registered by postal operators, in the imprint the data fields of categories (a) must coincide with the record registered by the postal operator in order to be recognized as valid. The data fields by category (b) may vary, but in general must meet the basic integrity criteria. For example, a data field containing the amount of postage usually corresponds to, or is determined by, a data field containing a category of tariffs or services.
First consider the case where SHA-1 is used in combination with a digital signature algorithm, so the data in the mark is first hashed to a fixed length, and then signed using, for example, RSA, DSA or ECDSA.

USPS Electronic Brand: IBIP (Information Based Indicia Program)
Consider stamps IBIP (Information Based Indiciaia Program), which should be used to send by mail on a particular day. How many valid IBIP stamp values exist on this day?

Variables contained in IBIP
An analysis of the table above shows that 8 of the 14 data fields fall into category (a), or rather fields No. 1-6, 10, and 12. This subset of data can take on any of the 1.6 million franking machine records registered in the United States ( if the market had completely moved to IBIP). The remaining fields are in category (b). Of these, the date of dispatch (field No. 9) automatically coincides with the specified date of registration, and, as a rule, the tariff category (field No. 4) is uniquely determined by the payment amount (field No. 8). Assuming that the unused field number 11 can take any possible value, there are 17 bytes of data category (b) left, data that belongs to the contents of the stamps. Factoring in both data categories is no more than 1.6x10 ^ 6 x 256 ^ 17 ≈ 256 ^ 16.58 of the actual value of the stamps. Any restrictions on filling data fields will further reduce this figure.
So it goes.
Source: https://habr.com/ru/post/328748/
All Articles