New dynamic protection against exploits to stop attacks at the very early stage of exploitation of vulnerabilities

The main innovation of the new version 2.4 of the Panda Adaptive Defense family of solutions for protection against unknown threats was the new dynamic anti-exploit technology, which allows detecting and stopping known and unknown attacks at the very early stage.
The new version 2.4 of the Adaptive Defense solution family will delight its users with the following improvements:
')
1. Detection / mitigation of consequences at the stage of exploitation (infection) in the life cycle of cyber attacks - Dynamic anti-exploitation technology
2. Detection of attacks that do not use malicious programs or any files, and monitoring via the management console
3. Identification of computers used to spread attacks within the network
4. Export detailed information about the status of the workstation and the server for its integration into operational applications
5. Increased flexibility for integration with a local client SIEM solution
6. Advanced features of expert analysis: the ability to export detailed information about the life cycle of one or more threats, as well as display information about the command line parameters (version 2.4.1)
Let's look at these improvements in more detail.
Detection and mitigation of consequences at the stage of exploitation (infection) in the life cycle of cyber attacks - Dynamic anti-exploitation technology
An exploit is a sequence of commands that allows you to exploit an error or vulnerability in legitimate software. Modern attackers use executable and non-executable files (or fileless attacks based on scripts) to gain access to and operate systems installed on workstations and servers in order to carry out their attacks.
In a typical attack scenario, a hacker manipulates a legitimate program to run code, trying to avoid detection by security systems. This code then downloads the malware, i.e. malicious executable file, or uses a legitimate system utility to perform malicious actions without using any executable file (an attack without using malware or file-free attacks).
In the latter case, and to gain complete control over the required computer, the hacker must perform a set of actions that become possible during the exploitation of a software vulnerability. In such a scenario, blocking attempts to exploit a vulnerability will be able to completely stop the attack.
Adaptive Defense and Adaptive Defense 360 include a new dynamic anti-exploit technology that prevents attempts to use exploits by continuously monitoring the activity of devices, as well as identifying known and unknown (zero-day) exploits.
Why is it important to stop attacks at the stage of exploitation (infection)?
A cyber attack consists of a chain of actions that various techniques use to penetrate systems and bypass existing detection mechanisms.
Many malicious attacks involve the exploitation of vulnerabilities found in legitimate applications in order to carry out the required actions without arousing suspicion from installed security systems. Hackers take advantage of software vulnerabilities due to which they are able to compromise the entire system. As a result, such vulnerabilities could allow attackers full access to the required device, as well as to each computer on the network.
The purpose of advanced protection systems, like Panda Adaptive Defense, is to identify and stop such a sequence of actions, preventing the launch of malicious code and the compromise of the application, system, and any workstation or server.
The actions or steps that make up the cyber attack are known as the “Cyber Kill Chain” (CKC), while its enhanced version from the perimeter to the target workstations and servers is known as the “Extended Cyber Kill Chain”. If you want to know more about Cyber-Kill Chain, we recommend that you read our article about it .

Fig. 1. Model enhanced Cyber Kill Chain. Actions designed to access and target servers and devices by the hacker
According to the expanded Cyber Kill Chain model, while attackers must successfully go through each phase of this model to achieve their goals, we, as defenders of our clients' networks, must be able to stop the attack at any stage before the hacker can access to the assets of its victim. Thus, at each stage of the attack life cycle, we must apply the appropriate technology in order to stop the threats as quickly as possible.
Dynamic anti-exploit technology, included in version 2.4, is designed to detect and interrupt attacks before they can compromise legitimate applications.
What does anti-exploit technology provide in Adaptive Defense?
Adaptive Defense contains new anti-explosive technologies developed by our information security experts in the PandaLabs anti-virus laboratory of Panda Security. These technologies are based on continuously updated knowledge of Panda Security (this information comes in real time from various sensors, including those installed on millions of devices), and continuous monitoring of processes and their activity on end devices with continuous analysis of the causal relationship between various processes.
Key benefits of this technology:
- Provides an extra level of protection for blocking exploits in real time. With an exploit, this technology prevents the launch of malicious code that infects a computer and spreads to other devices in the company.
- Controls the internal behavior of compromised processes by searching for anomalies that may indicate known or unknown (zero-day) exploits.
- Detects threats regardless of the exploit used in the attack. Adaptive Defense provides effective protection against all types of exploits, especially unknown exploits (zero day), which take advantage of vulnerabilities in web browsers (Internet Explorer, Firefox, Chrome, Opera and others), in commonly used applications (Java, Adobe Reader, Adobe Flash, Microsoft Office, multimedia players ...) and on unsupported operating systems (Microsoft XP and others).
- Provides end users with continuous protection and does not slow down systems.
Unlike most other products currently on the market, Adaptive Defense is able to neutralize not only known vulnerabilities, but also the most dangerous threats - unknown vulnerabilities (zero day). Therefore, the solution is largely focused on the detection of all types of anomalies and unusual behavior in the context of their implementation, including the detection and blocking of attacks that exploit techniques use, at any stage of their life cycle.
As a result, the solution can stop exploits and prevent legitimate applications from being compromised at the earliest stages of attacks that exploit vulnerabilities, all of which is done transparently to the user of the protected device.
Key Differences in Adaptive Defense Anti-Exploit Technology
Most of the anti-exploit solutions on the market today rely either on performing morphological analysis of files and / or their execution context, or on introducing various protection functions missing in Windows: ASR, DEP, EAF, as well as specific detection of known vulnerabilities (Common Vulnerabilities and Exposures, CVE).
However, these techniques are not effective enough to stop attacks, which, due to known and unknown vulnerabilities, create “entry points”.
Considering all these factors, let us highlight the key differences between the anti-exploit technology that is now implemented in the Adaptive Defense product family:
- Its globality: discovers exploits of known and unknown (zero day) vulnerabilities.
- Unlike most other solutions on the market, Panda’s new anti-exploit technology was not just designed to fix security holes in Windows systems. It is based on continuous monitoring of all processes running on devices and cloud-based correlation of the data collected using artificial intelligence algorithms. This allows you to automatically analyze the context of attack direction and exploitation of vulnerabilities.
- The effectiveness of the new anti-exploit technology Adaptive Defense is due to the careful synchronization of the following components:
- Anti-exploit protection on workstations and servers, fully integrated with advanced protection. No updates or additional processing functions are required, since The security model is based on monitoring all actions performed by any process and application running on the end device.
- Specialized machine learning algorithms operating in a cloud environment. These algorithms are an integral part of the managed service, and as such, are always adapted to new systems, applications, and advanced circumvention techniques used to exploit attacks.
- Managed service maintained by our team of threat hunters (threat hunters), specialized in the detection of advanced explosive techniques.
The introduction of new anti-explosive technology in Panda Adaptive Defense
Anti-exploit technology settings. Modes of operation
Starting with version 2.4, the web management console allows you to configure this technology at the security profile level. Anti-exploit technology is enabled and disabled independently of any other protection module in Adaptive Defense, including Extended Protection.
In the new version, this technology is disabled by default, although it is strongly recommended to enable it in all security profiles configured to protect your corporate network.
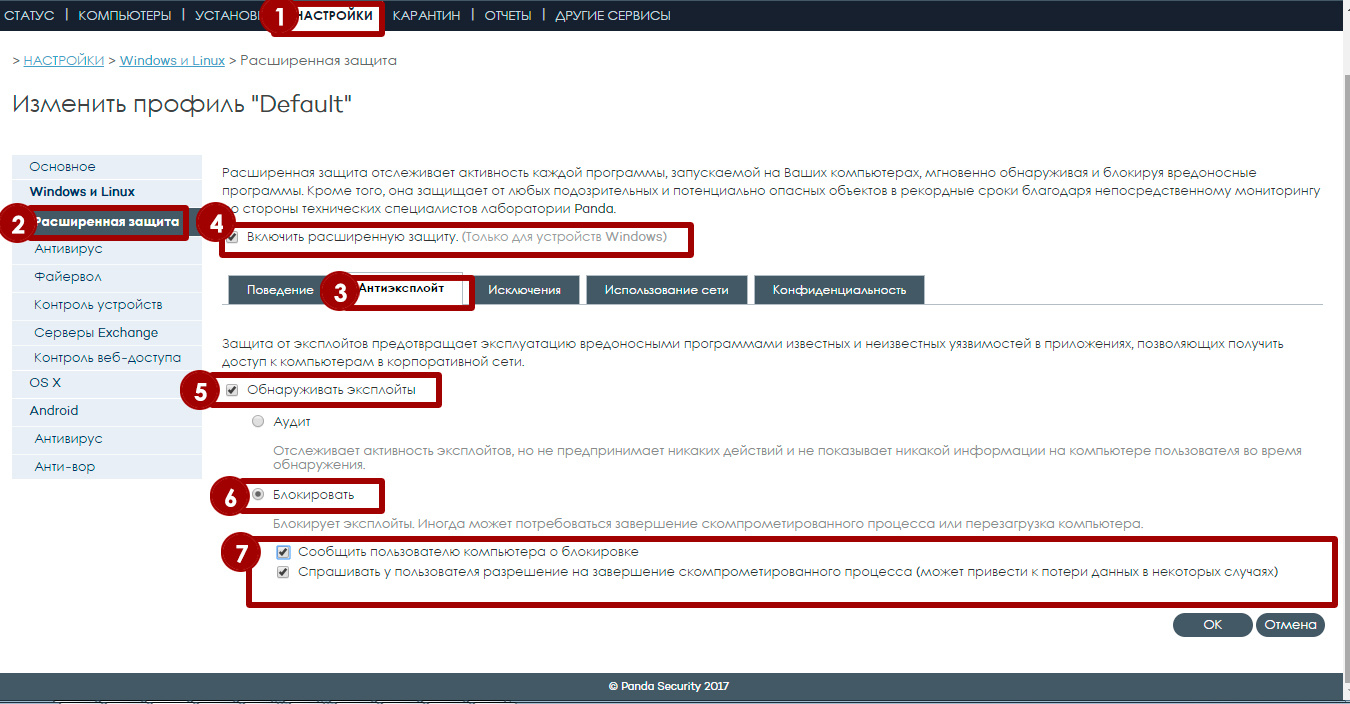
Fig. 2. Configure anti-exploit technology in security profiles
Audit Mode: Console Detection Only notification
In this mode of operation, Adaptive Defense will not take any action when it detects an attempt to use an exploit. The solution will only register the event in the web management console, display the relevant information in the integrated Advanced Reporting Tool (ART) SIEM system and / or send logs to a third-party SIEM system as part of the SIEMFeeder service.
Block mode: Console notification of detections and action against them.
In this mode of operation, Adaptive Defense will not only notify the administrator via the management console and e-mail about each attempt to exploit the exploit, but will also take the required actions on the compromised workstation and server, blocking the attack without interference from the end user .
However, since Since most exploits "live" in the memory of a compromised application, it will often be necessary to complete the process and clear the memory.
Under such circumstances, if the compromised process is a critical system process , stopping the attack may require restarting the required computer.
Notify the user of the compromised computer if action is required
Due to the inconvenience that a compromised computer user may encounter in the event of an unintentional stopping of a legitimate application or restarting the system, the solution provides administrators with options that allow end users to voluntarily stop the compromised process or restart the computer. This approach allows them, for example, to pre-save changes in their user files.
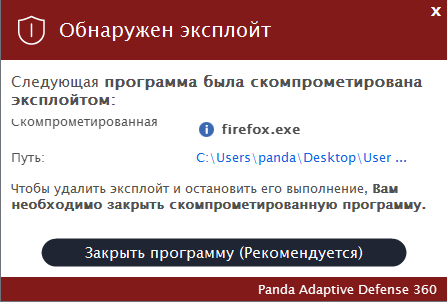
Fig. 3. An exploit has been detected, the compromised program must be shut down.
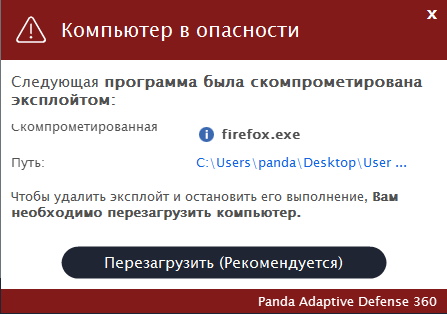
Fig. 4. An exploit is detected, a computer restart is required. This notification will be displayed periodically until the end device is rebooted.
However, it is worth noting that since the discovery of a compromised process until it is completed or until the computer is restarted, the exploit remains loaded in memory, trying to run malicious code. To remind users of this potentially dangerous situation, the local console will display a warning, prompting the user to shut down a compromised application or restart the computer.
Monitoring exploit detection in the management console
The Adaptive Defense web-based management console notifies you of exploit detections in the following ways:
Block "Activity". Panel "Classification of all running and tested programs"
The number of exploits detected is added to the total number of programs classified as malware and exploits.

Fig. 5. Panel "Classification of all running and tested programs"
Block "Activity". Panel "Malicious programs and exploits"
Detected exploits are displayed in real time in the management console in the panel “Malicious programs and exploits”.

Fig. 6. The panel "Malicious programs and exploits"
Details of the discovered exploit:
When you click on the panel “Malicious programs and exploits”, you are taken to a page with a list of detected malware and exploits. When you switch to the Exploits tab, you can see the following information:
- Computer name
- The path to the compromised program
- The action taken in relation to the exploit. This column can have the following values:
o Administrator Enabled: In Audit mode.
o Blocked (automatically): In the “Block” mode. The exploit was immediately blocked without the need for any intervention from the user.
o Blocked after completion of the process: In the “Block” mode. The exploit has been neutralized after the user has completed the application.
o Allowed by user. In the "Block" mode. The user was asked to complete the application, but he has not yet done so.
o Detected. Waiting for reboot. In the "Block" mode. This action appears under the following circumstances:
- When it is necessary to reboot the system to block the exploit and fix it, because This affects system processes.
- If the user is asked to terminate a compromised application, but he did not do it after a certain period of time. The status of the computer will change and it will be necessary to reboot the system.
- Risk. If the exploit was not immediately blocked, the Risk column will indicate that the computer was in danger from the moment the exploit was discovered and until the moment of its blocking (if it was actually blocked).
- Discovery date

Fig. 7. Notifications about malware and exploits found
The details of the notification contain additional information necessary for expert analysis of the attack: the life cycle of the exploit and the activity chart detailing the evolution of the exploit to the moment it was stopped (if it was stopped), as well as access to the URL until the attack was detected, since There is a high probability that some of these addresses are associated with this attack.
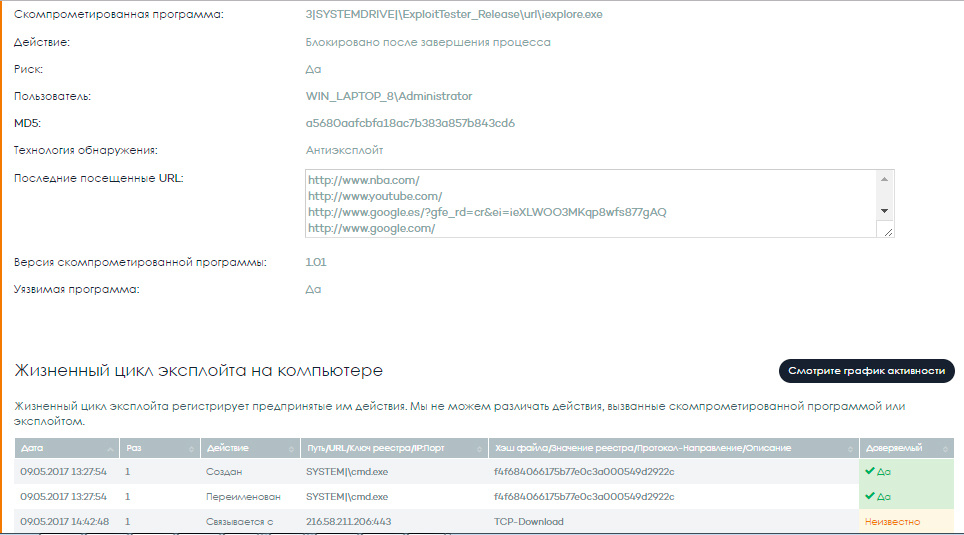
Fig. 8. Details of the exploit, including visited URLs
to the moment of detection, and the life cycle of the exploit

Fig. 9. The life cycle of the exploit over time
Predefined filters for an exploit section allow you to search for specific computers, compromised applications, etc. In exactly the same way as it is implemented with pre-installed filters for partitions with malicious programs, potentially unwanted programs and blocked objects.
Pre-configured reports
Reports for management, advanced reports for management and reports on threats include information on exploits discovered.
Email Alerts
In addition, if the option to send email notifications when malware is detected is enabled, the network administrator or the information security manager can quickly receive an email immediately after an exploit is detected.

Fig. 10. Real-time email notification settings,
including notifications on detected exploits

Fig. 11. Email notification of an exploit detected that compromised Internet Explorer. The end user has not completed the application, so the risk status is high
Information Available in Advanced Reporting Tool
Every time an attempt to exploit a vulnerability on a client’s network is detected, the Advanced Reporting Tool (ART) receives a notification just as it does when it detects malware or a PUP, only in this case the value of “Exploit” will be displayed in the AlertType column.

Fig. 12. Notification Table with Exploit Detections
Therefore, in the case of detections of this type, they will be shown in Security Incidents.

Fig. 13. Security Incidents with exploit information
Information available in the client SIEM solution
If a third-party SIEM system is implemented in the enterprise, then information about each detection of an attempt to exploit a vulnerability, regardless of the technology used, is reported to this SIEM solution in the form of a specific notification. This is implemented in the same way as in the case of malware and PUP detection, only in this case such notifications are transmitted with the event type “Exploit”.
Detection of fileless and non-malware attacks
Attacks that do not use malicious programs are based on the use of non-executable files, vulnerabilities in legitimate applications such as Chrome, Firefox, Internet Explorer, Microsoft Office (Word, Excel, etc.), Java VM and Adobe products. They compromise workstations and servers by distributing and executing code in memory when the attacked user opens files, for example, with macros. Attacks using non-executable files manipulate the stack of legitimate applications and they achieve their goals without downloading malicious executables.
In addition to this, fileless or “script” attacks are based on a sequence of commands written in scripting languages (such as Java or PowerShell). These malicious scripts run without writing files to disk. That is why such attacks are called fileless.
Finally, many attacks use a combination of macros and PowerShell arguments for the command line. For example, we saw attacks that opened a Word document with a macro using circumvention techniques to hide and launch an attack using PowerShell scripts from remote management servers.
Fileless attacks and attacks based on non-executable files do not constitute something new, but they are becoming more common and remain undetectable by traditional antivirus solutions.
Adaptive Defense and Adaptive Defense 360 include techniques that determine this type of attack by monitoring processes, analyzing their interconnections and the ability of the solution to identify the malicious behavior of legitimate applications. These techniques are additionally enhanced in the new version 2.4. Starting from this version, the detection of such attacks can be controlled the same way as it does for other detections, i.e. they are displayed in the control console panel and appear in the reports as malware detection. This allows administrators to monitor their life cycle and receive email notifications whenever this type of attack is detected.
Computers used as a launching pad for a network attack (source of infection)
It is a well-known fact that intruders penetrate corporate networks through their weak points, and then they use empowerment techniques, circumvention techniques and horizontal promotion between computers and servers to achieve their goals. In many cases, certain computers on the network turn into “zombies” through which external management servers send the required commands. Such "zombies" computers can be used as a launching pad for launching cyber attacks on other computers in the corporate network.
In such and other cases, it is imperative to find out as early as possible which workstations and servers are sources of infection.
Starting from version 2.4, whenever a malware / PNP is detected or an unknown object is blocked, Adaptive Defense shows the network computer from which the infection spread, its IP address, and even data on the connected user. All this information is part of the threat life cycle data.
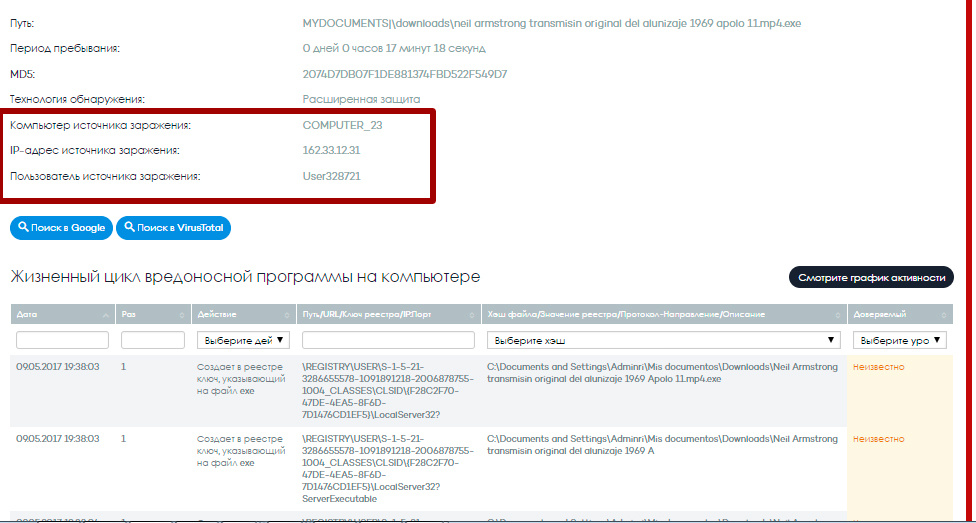
Fig. 14. Data on the life cycle of the exploit, indicating the source of infection
and the currently connected user
Computer Status Report
In many cases, especially from medium and large companies that manage the security of their end devices and that have systems, applications, processes and tools managed by the IT department of an enterprise or third-party organizations (outsourcing), information is required on the status of workstations and servers, which integrated into these processes or tools. Such an example is the corporate system of management of user requests (internal technical support).
For this reason, the new version 2.4 includes a new report type (in CSV format) with information on the status of all protected workstations and servers. The administrator can export this report or schedule it to be sent automatically.

Fig. 15. Report on the status of computers, which allows you to integrate this data into the operational software of the organization, for example, in the system of management of user requests
Improvements in the service Advanced Reporting Tool
This functionality is available only for those customers who have licenses for the Advanced Reporting Tool (ART) .
New data in existing tables
- The OPS table now shows the command line argument used to launch the application, including its parameters.
- Table ALERTS :
- This table now shows events of the type “Exploit”, as well as the most recently visited URLs (up to 10 URLs, separated by the “*” symbol, in the UrlList field).
- When malware is detected, if it occurred when a malicious file was transferred from one computer on the network to another, the table will show the IP address of the source computer and the user connected to it.
- Previously, the SOCKETS table showed only network protocols (TCP, UDP, ICMP). The new version additionally shows information about connections at the application level for RDP traffic (remote desktop). This allows you to identify RDP attacks (the “Protocol” key will show the value “TCP-RDP”).
New widget in Security Incidents
Two new widgets appeared with information about the computers that are the source of the infection from which attempts were made to copy or transfer the malware to other computers.
The first widget is a nodal graph displaying the relationship established between two computers for a selected period of time. With it, you can look at the dynamics over time, from which computer and on which computer they tried to transfer malware.
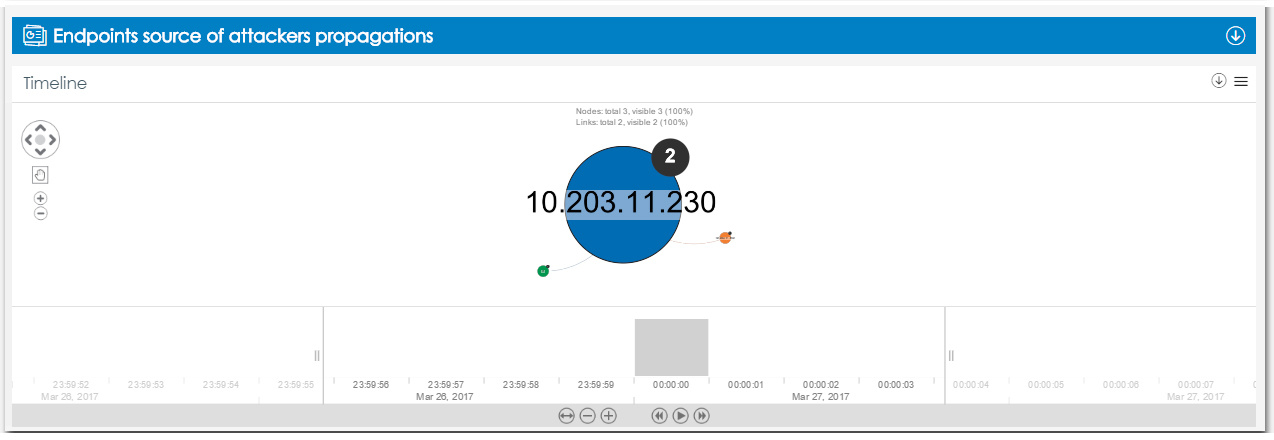
Fig. 16. A new widget in ART with a time diagram of end devices,
being sources and victims of infections
The second widget is an affinity graph. It shows how many times attempts were made to transfer malware from one computer (source of infection) to other computers.

Fig. 17. A new widget in ART linking end devices
being sources and victims of infections
Information about current categories of hashes related to events
All tables showing the categories associated with the hash of the parent and child processes now show the category at the moment the event occurred, and the current category (with a maximum update rate of 4 hours).
Improvements in the service SIEMFeeder
This functionality is available only to those Adaptive Defense users who are licensed to SIEMFeeder to integrate the solution with a third-party SIEM system.
More information about events
- OPS events now show the command line argument used to launch an application, including its parameters.
- ALERTS events:
- Now they show events like “Exploit”, as well as the most recently visited URLs (up to 10 URLs, separated by the “*” symbol, in the UrlList field). In the case of exploits arising from the document, the Doclist field will be filled.

Fig. 18. Format of Alerts event in SIEMFeeder
- When malware is detected, if it occurred when a malicious file was transferred from one computer on the network to another, the table will show the IP address of the source computer and the user connected to it.
- Previously, SOCKETS events showed only network protocols (TCP, UDP, ICMP). The new version additionally shows information about connections at the application level for RDP traffic (remote desktop). This allows you to identify RDP attacks (the “Protocol” key will show the value “TCP-RDP”).

Fig. 19. Format of Sockets event in SIEMFeeder
Increased flexibility for integration with a local client SIEM solution
In addition to transferring activity logs from workstations and servers via sFTP or FTP, the new version 2.4 also allows you to send logs via the Syslog protocol. If necessary, the transmitted data can be encrypted using SSL / TLS encryption. In order to use the Syslog protocol, a Syslog server, ready for receiving logs from our side, which is in most cases already built into the SIEM solution, must be implemented in the network.
Please note that you will need preliminary configuration information and time to configure the service parameters: the number of parallel connections, the number of attempts (3 by default), etc.
Finally, this version implements a VPN service to increase the level of security when sending logs via FTP / sFTP.
Other improvements in version 2.4
Version 2.4 of Adaptive Defense and Adaptive Defense 360 solutions with protection version 7.70 and agent version 7.71 contain the following additional improvements:
1. Exception management:
- Exceptions at the profile level will also affect extended protection.
- Higher consistency between notifications on detections and exceptions: if an object is excluded from extended protection, the solution will no longer send email notifications for this object until the exception is removed.
2. Lock : , , , . Those. , .
3. , Exchange, .
4. : , , , , , .
5. : , , , . , , . , , .
Other improvements:
- , Adaptive Defense/Adaptive Defense 360.
- - SIEMFeeder .

Fig. 20. SIEMFeeder
, , :
— , Windows Terminal Server.
— . .
— , Panda Security . , .
, 2.4, .
2.4 :
- Server Core 2008 (32 64 ), 2008 R2 (64 ), 2012 2012 R2, GUI . Since GUI, :
— , , .. - , .
- Windows MultiPoint Server 2012
- Mac Virus Barrier X9
( 2.4.1)
2.4.1 ( 2017 .) CSV. , Excel, .
, , 24 , , .
, , .
, , , .
, 2.4.1 , PowerShell.
2.4
2.4 8 2017 , - .
- Adaptive Defense 360, 2.4.
, Adaptive Defense 360
Adaptive Defense:
- 2.4, , .
- , , 2.4 . :
— 101 : 17.05.2017
— 101 501 : 29.05.2017
— 501 : 12.06.2017
- 2.4, 7.71
- 7.70 , , . , .
2.4.1
2.4.1 2017 , - .

2.4, 2.4.1 .
Conclusion
, , Adaptive Defense.
, , , , . , , , , , , , , / , ..
Cyber Kill Chain, 2.4 – ().
Adaptive Defense :
—
— - : , ,
— .
.
- Adaptive Defense 360
To familiarize yourself with the management console, just a regular browser (Chrome or Firefox is recommended) and some free time are sufficient.
Console: demologin.pandasecurity.com
Login: DRUSSIAN_FEDERATION_C14@panda.com
Password: DRUSSIAN # 123
Trial licenses Adaptive Defense 360
You can register free full-featured licenses for 1 month.
Source: https://habr.com/ru/post/328682/
All Articles