"The letter of the law": A little about the protection of personal data
On May 10, President Vladimir Putin approved the Strategy for the Development of the Information Society in the Russian Federation for the period from 2017 to 2030. The document outlined a plan for import substitution, according to which it is necessary to replace foreign software and electronic databases with Russian counterparts, as well as to ensure the use of domestic encryption in the electronic interaction of federal authorities.
 / photo by Charles Dyer CC
/ photo by Charles Dyer CC
According to the designated strategy, it is necessary to improve the mechanisms for restricting access to information, the dissemination of which is prohibited in the Russian Federation by law. The document also states that it is necessary to improve the mechanisms of legislative regulation of media activities and sources of information, which in many respects can be attributed to such - social networks, news aggregators, instant messengers and Internet TV.
')
All this is related to the law on information and the law on the storage of personal data (PD). They oblige the sites to notify Roskomnadzor of the start of their activities, take responsibility for storing personal data of citizens of the Russian Federation, as well as organize and configure the connection to the SORM equipment (a system of technical means to ensure the functions of operational search activities), providing the data necessary for to the register of information dissemination organizers (ARIs).
Participants in this registry are required to store data on user actions and transfer them at the request of government agencies and special services. At the same time, according to the law, Roskomnadzor is obliged to block the websites of companies that have refused to provide the information necessary for entering into the register.
For example, in mid-April, the federal service blocked the sites and servers of the Zello mobile radio. Also, in early May, access to the websites and servers of Line, Imo, Vchat and BlackBerry Messenger messengers was limited . And on May 4, Roskomnadzor blocked a large Chinese service WeChat, but later the department still canceled the lock - the issue with the data was resolved.
According to the current legislation, the organizers of the dissemination of information are obliged to store metadata about all actions of the service participants for six months. At the same time, from July 2018, when the new provision of the Spring Package comes into force, companies will have to keep on their servers information about the messages sent over the year (both voice, text and multimedia).
All this is a peculiar consequence of the Law “On Personal Data”, which seriously tightened the requirements for all private and public companies and organizations, as well as individuals who store, collect, transmit or process personal data. At the same time, the task of protecting information fell on the shoulders of organizations that process this personal data.
By processing personal data we mean any operation, action, set of actions performed with or without the use of automation tools, which includes collecting, recording, organizing, storing, modifying, using, distributing, blocking, deleting, and destroying personal data.
According to Article 18.1 of the Federal Law-152, operators (state and municipal bodies, as well as legal entities or individuals who process personal data) fall into the definition of an “operator” of personal data, a number of organizational, legal and technical measures are required. First, appoint a responsible person to organize the processing of personal data. Secondly, to exercise internal control and (or) audit of the compliance of personal data processing with the requirements of the federal law and regulations adopted in accordance with it.
Third, to assess the damage that may be caused to personal data subjects in the event of violation of this federal law, as well as to familiarize employees who directly process personal data with the provisions of the Russian legislation on personal data. And this is not a complete list of requirements (the full list can be found here ).
If an organization does not fulfill the requirements of the Law on Personal Data, it may face the following risks: civil claims from customers or employees, suspension or termination of PD processing in an organization, bringing the organization to administrative, criminal, civil, disciplinary and other types of responsibility , suspension or revocation of licenses for the main activity of the organization, reputational risks and risks of unfair competition.
To be clean before the law, companies have several ways. The first one is to independently organize the protection of personal data with or without the assistance of third-party legal consulting. This scenario is acceptable, as its server or data center provides precise control of access to equipment processing personal data. All this allows you to limit the potential leak of information area of protected and inaccessible from the outside machines. Also, its own infrastructure makes it easy to install additional monitoring and protection tools.
However, this method has disadvantages. It is rather complicated for implementation and can be costly, since for this it is necessary to acquire expensive equipment, to set up and maintain infrastructure. In addition, not all companies are able to provide the appropriate level of reliability and security of personal data of users.
As an alternative to self-deployment of the infrastructure - since it is quite difficult to fulfill all the requirements of the Federal Law 152 independently, the personal data operator may engage on a contractual basis a third-party organization that will provide both organizational and technical data protection measures. This is a so-called cloud hosting service, which is offered by many IaaS providers ( including IT-GRAD) when a client leases infrastructure with a full set of certified information security tools as part of the IaaS model.
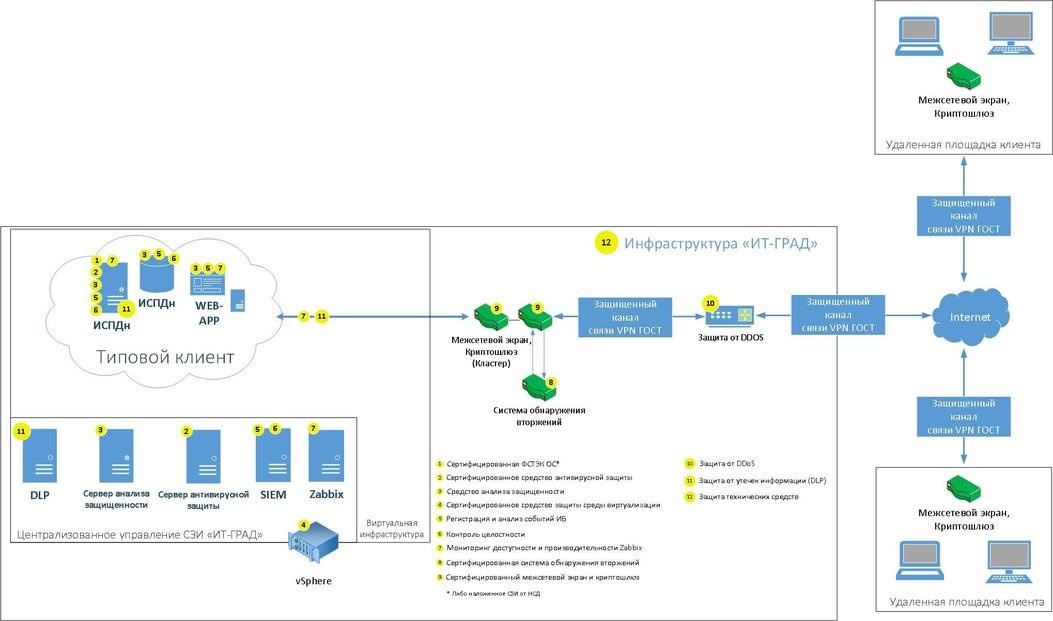 Infrastructure scheme "IT-GRAD"
Infrastructure scheme "IT-GRAD"
In this case , the supplier’s customers get rid of the need to certify their own information system, the costs of creating and owning a secure IT infrastructure, and legal liability. Customers additionally receive secure hosting using certified hardware from world manufacturers of hardware (NetApp, Cisco, IBM, etc.), as well as the use of software and hardware encryption.
However, there are some peculiarities that need to be remembered. When concluding a contract with a service provider, a client should carefully read all the points provided for in it. Particular attention should be paid to the issue of differentiation of access rights by employees of the provider to the data placed in the cloud.
Do not forget about the agreement on the level of services (SLA). Hosting PDS, like any other service provided in the context of the stipulated conditions, must be accompanied by an agreement on the level of services provided. Since the integrity and availability of data is an important aspect, it is necessary to discuss the details and find out what responsibility the supplier will bear in case of non-fulfillment of certain conditions.
Note that in both cases - when creating your own infrastructure or renting it - customers who want to fully comply with the requirements of personal data protection legislation and have no problems with regulatory bodies, you must carefully consider the choice of a hosting provider or consulting organization. In order not to encounter unscrupulous companies that claim to be able to conduct an audit, or to bring the information structure in full compliance with the law, but they do not follow their promises.
PS Selection of materials on the topic from the First Corporate IaaS blog:
 / photo by Charles Dyer CC
/ photo by Charles Dyer CCAccording to the designated strategy, it is necessary to improve the mechanisms for restricting access to information, the dissemination of which is prohibited in the Russian Federation by law. The document also states that it is necessary to improve the mechanisms of legislative regulation of media activities and sources of information, which in many respects can be attributed to such - social networks, news aggregators, instant messengers and Internet TV.
')
All this is related to the law on information and the law on the storage of personal data (PD). They oblige the sites to notify Roskomnadzor of the start of their activities, take responsibility for storing personal data of citizens of the Russian Federation, as well as organize and configure the connection to the SORM equipment (a system of technical means to ensure the functions of operational search activities), providing the data necessary for to the register of information dissemination organizers (ARIs).
Participants in this registry are required to store data on user actions and transfer them at the request of government agencies and special services. At the same time, according to the law, Roskomnadzor is obliged to block the websites of companies that have refused to provide the information necessary for entering into the register.
For example, in mid-April, the federal service blocked the sites and servers of the Zello mobile radio. Also, in early May, access to the websites and servers of Line, Imo, Vchat and BlackBerry Messenger messengers was limited . And on May 4, Roskomnadzor blocked a large Chinese service WeChat, but later the department still canceled the lock - the issue with the data was resolved.
According to the current legislation, the organizers of the dissemination of information are obliged to store metadata about all actions of the service participants for six months. At the same time, from July 2018, when the new provision of the Spring Package comes into force, companies will have to keep on their servers information about the messages sent over the year (both voice, text and multimedia).
Personal data protection
All this is a peculiar consequence of the Law “On Personal Data”, which seriously tightened the requirements for all private and public companies and organizations, as well as individuals who store, collect, transmit or process personal data. At the same time, the task of protecting information fell on the shoulders of organizations that process this personal data.
By processing personal data we mean any operation, action, set of actions performed with or without the use of automation tools, which includes collecting, recording, organizing, storing, modifying, using, distributing, blocking, deleting, and destroying personal data.
According to Article 18.1 of the Federal Law-152, operators (state and municipal bodies, as well as legal entities or individuals who process personal data) fall into the definition of an “operator” of personal data, a number of organizational, legal and technical measures are required. First, appoint a responsible person to organize the processing of personal data. Secondly, to exercise internal control and (or) audit of the compliance of personal data processing with the requirements of the federal law and regulations adopted in accordance with it.
Third, to assess the damage that may be caused to personal data subjects in the event of violation of this federal law, as well as to familiarize employees who directly process personal data with the provisions of the Russian legislation on personal data. And this is not a complete list of requirements (the full list can be found here ).
If an organization does not fulfill the requirements of the Law on Personal Data, it may face the following risks: civil claims from customers or employees, suspension or termination of PD processing in an organization, bringing the organization to administrative, criminal, civil, disciplinary and other types of responsibility , suspension or revocation of licenses for the main activity of the organization, reputational risks and risks of unfair competition.
To be clean before the law, companies have several ways. The first one is to independently organize the protection of personal data with or without the assistance of third-party legal consulting. This scenario is acceptable, as its server or data center provides precise control of access to equipment processing personal data. All this allows you to limit the potential leak of information area of protected and inaccessible from the outside machines. Also, its own infrastructure makes it easy to install additional monitoring and protection tools.
However, this method has disadvantages. It is rather complicated for implementation and can be costly, since for this it is necessary to acquire expensive equipment, to set up and maintain infrastructure. In addition, not all companies are able to provide the appropriate level of reliability and security of personal data of users.
As an alternative to self-deployment of the infrastructure - since it is quite difficult to fulfill all the requirements of the Federal Law 152 independently, the personal data operator may engage on a contractual basis a third-party organization that will provide both organizational and technical data protection measures. This is a so-called cloud hosting service, which is offered by many IaaS providers ( including IT-GRAD) when a client leases infrastructure with a full set of certified information security tools as part of the IaaS model.
 Infrastructure scheme "IT-GRAD"
Infrastructure scheme "IT-GRAD"In this case , the supplier’s customers get rid of the need to certify their own information system, the costs of creating and owning a secure IT infrastructure, and legal liability. Customers additionally receive secure hosting using certified hardware from world manufacturers of hardware (NetApp, Cisco, IBM, etc.), as well as the use of software and hardware encryption.
However, there are some peculiarities that need to be remembered. When concluding a contract with a service provider, a client should carefully read all the points provided for in it. Particular attention should be paid to the issue of differentiation of access rights by employees of the provider to the data placed in the cloud.
Do not forget about the agreement on the level of services (SLA). Hosting PDS, like any other service provided in the context of the stipulated conditions, must be accompanied by an agreement on the level of services provided. Since the integrity and availability of data is an important aspect, it is necessary to discuss the details and find out what responsibility the supplier will bear in case of non-fulfillment of certain conditions.
Note that in both cases - when creating your own infrastructure or renting it - customers who want to fully comply with the requirements of personal data protection legislation and have no problems with regulatory bodies, you must carefully consider the choice of a hosting provider or consulting organization. In order not to encounter unscrupulous companies that claim to be able to conduct an audit, or to bring the information structure in full compliance with the law, but they do not follow their promises.
PS Selection of materials on the topic from the First Corporate IaaS blog:
Source: https://habr.com/ru/post/328588/
All Articles